What is UEFI Secure Boot and how it works?
Secure Boot is a UEFI firmware security feature developed by the UEFI Consortium that ensures only immutable and signed software are loaded during the boot time. Secure Boot leverages digital signatures to validate the authenticity, source, and integrity of the code that is loaded. These validation steps are taken to prevent malicious code from being loaded and to prevent attacks, such as the installation of certain types of rootkits.
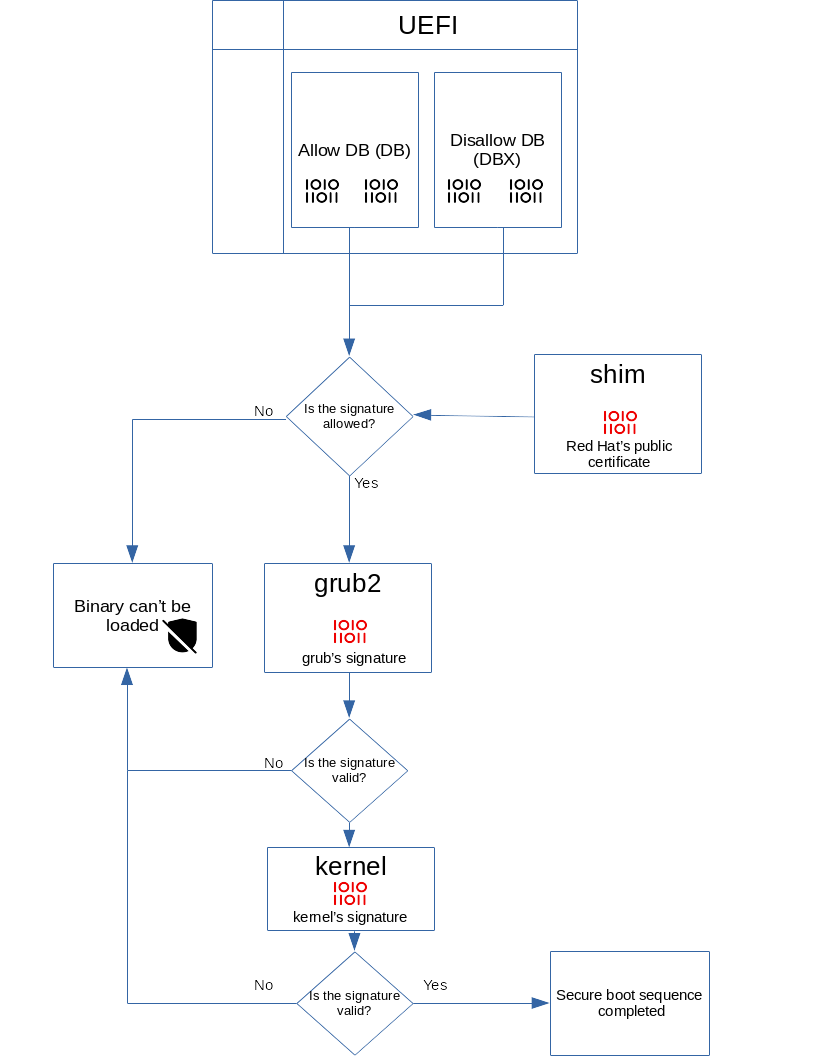
Secure Boot is split into several pieces and stages. The first important concept is the Allow DB (DB) and Disallow DB (DBX) databases. The Allow DB (DB) database stores the hashes and keys for trusted loaders and EFI applications that are allowed to be loaded by the machine’s firmware. The Disallow DB (DBX) database stores revoked, compromised, and non-trusted hashes and keys. Any attempt to load signed code using the Disallow DB keys or in the case where the hash matches a Disallow DB entry will lead to boot failure.
Trusted applications are signed by a central Certificate Authority. The public certificate is stored in the hardware, allowing third-party EFI applications signed by this certificate to load successfully.
On Red Hat Enterprise Linux versions which support Secure Boot, the signed and trusted application is the shim package which is the first application loaded by the machine’s firmware. The shim package itself holds Red Hat’s certificate and its own databases of trusted keys and code hashes that are allowed to be loaded. This data is used to verify the boot loader signature, which is GRUB 2, making sure it has not been compromised or tampered by a malicious actor. Once the verification succeeds, GRUB is loaded and verifies the kernel signature and confirms that it matches with Red Hat’s certificate or any hash enrolled by the user itself into the Allow DB. If there is a match, GRUB will load the kernel, which finishes the boot load process.
For more information on UEFI and Secure Boot see UEFI Secure Boot in Modern Computer Security Solutions.


Comments