How to Enable Groups Claim on Azure Active Directory for OpenID Connect
Environment
- Red Hat OpenShift Container Platform (RHOCP)
- 4.10+
- Red Hat OpenShift on AWS (ROSA)
- 4.10+
- Red Hat OpenShift Dedicated (OSD)
- 4.10+
- Azure Red Hat OpenShift (ARO)
- 4.10+
Issue
- Enable the
groups claimon Azure Active Directory for use with Openshift OAuth OIDC provider.
Resolution
Disclaimer: Links contained herein to external website(s) are provided for convenience only. Red Hat has not reviewed the links and is not responsible for the content or its availability. The inclusion of any link to an external website does not imply endorsement by Red Hat of the website or their entities, products or services. You agree that Red Hat is not responsible or liable for any loss or expenses that may result due to your use of (or reliance on) the external site or content.
-
Sign in to the Azure portal
Navigate to https://portal.azure.com and sign in with your Azure account credentials. -
Navigate to Azure Active Directory
From the left-hand menu, select "Azure Active Directory". -
Select App registrations
Within the Azure Active Directory page, select "App registrations" from the menu. -
Select the relevant application
From the list of applications, select the application for which you want to enable the groups claim. -
Open Token Configuration
From the left-hand menu of the application page, select "Token configuration". -
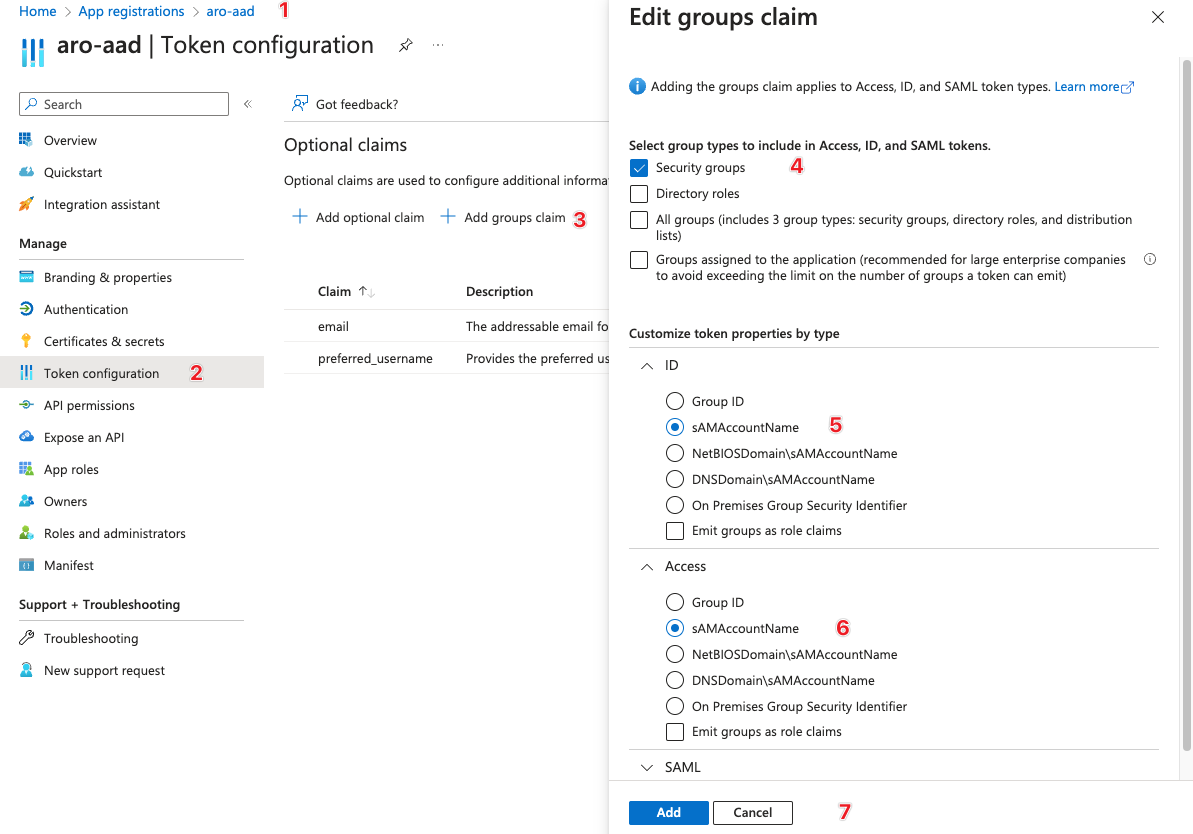
Add groups claim
Click on the "+ Add groups claim" button. -
Configure groups claim
In the "Add groups claim" page:- Select the types of groups (security groups, distribution lists, etc.) you want to include in the groups claim.
- Select the ID type (group ID or group name).
- Select the source (user’s groups or groups assigned to the application).
- Configure any advanced settings as required.
-
Save the changes
Click on "Add" to save the changes. -
Create AAD client secret
# create AAD client secret
oc create secret generic aad-secret --from-literal=clientSecret=zCS8Q~qS8.xxxxxxxxxxxxxxxxxB6l5DOfcw. -n openshift-config
- Configure Oauth OIDC on Openshift with groups claim, e.g.:
apiVersion: config.openshift.io/v1
kind: OAuth
metadata:
name: cluster
spec:
identityProviders:
- name: HTPasswd
mappingMethod: claim
type: HTPasswd
htpasswd:
fileData:
name: htpass-secret
- name: AAD
mappingMethod: claim
type: OpenID
openID:
clientID: 171169eb-xxxx-xxxx-xxxx-d36c6c6824d8
clientSecret:
name: aad-secret
extraScopes:
- email
- profile
claims:
preferredUsername:
- preferred_username
name:
- name
email:
- email
groups:
- groups
issuer: https://login.microsoftonline.com/64dc69e4-xxxx-xxxx-xxxx-ebece1dd1408/v2.0
The supported formats for group claims are:
- Microsoft Entra group ObjectId: Available for all groups.
- sAMAccountName: Available for groups synchronized from Active Directory.
- NetbiosDomain\sAMAccountName: Available for groups synchronized from Active Directory.
- DNSDomainName\sAMAccountName: Available for groups synchronized from Active Directory.
- On-premises group security identifier: Available for groups synchronized from Active Directory.
Note:
sAMAccountNameand on-premisesGroupSIDattributes are available only on group objects synced from Active Directory. They aren’t available on groups created in Microsoft Entra ID or Office 365. Applications configured in Microsoft Entra ID to get synced on-premises group attributes get them for synced groups only.
For more details, check Microsoft Document:
Configure group claims for applications by using Microsoft Entra ID
Root Cause
By default, Azure Active Directory does not include the groups claim in tokens for OpenID Connect. This can limit the information available for authorization decisions.
This solution is part of Red Hat’s fast-track publication program, providing a huge library of solutions that Red Hat engineers have created while supporting our customers. To give you the knowledge you need the instant it becomes available, these articles may be presented in a raw and unedited form.


Comments