How to update device firmware using fwupd on RHEL system?
Environment
- Red Hat Enterprise Linux 7.4 and later
- Red Hat Enterprise Linux 8
- Red Hat Enterprise Linux 9
- Red Hat Enterprise Linux 10
- fwupd utility
Issue
- How to update device firmware using
fwupdon RHEL system? - What is
fwupdand how does it works ?
Resolution
Disclaimer: Links contained herein to an external website(s) are provided for convenience only. Red Hat has not reviewed the links and is not responsible for the content or its availability. The inclusion of any link to an external website does not imply endorsement by Red Hat of the website or their entities, products or services. You agree that Red Hat is not responsible or liable for any loss or expenses that may result due to your use of (or reliance on) the external site or content.
-
fwupd is a system daemon that connects to Linux Vendor Firmware Service (LVFS) to collect firmware updates hosted by supported OEM vendors for the hardware devices connected to the system.
-
Users can either use a GUI software manager like GNOME Software or the command-line tool
fwupdmgrto view and apply firmware updates. -
The LVFS is a secure web service that allows hardware vendors to upload firmware updates. The metadata and files provided by LVFS are used by all major Linux distributions to provide metadata for clients such as GNOME software and
fwupdmgr. There is also no charge to vendors for LVFS to host or distribute content.
How to use fwupd?
1. Install fwupd package
# yum install -y fwupd
# systemctl start fwupd.service
- Users can check
fwupdservice status by running following command:
# systemctl status fwupd.service
● fwupd.service - Firmware update daemon
Loaded: loaded (/usr/lib/systemd/system/fwupd.service; static; vendor preset: disabled)
Active: active (running) since Mon 2020-09-28 14:00:22 IST; 53min ago
Docs: https://fwupd.org/
Main PID: 19250 (fwupd)
Tasks: 5
CGroup: /system.slice/fwupd.service
└─19250 /usr/libexec/fwupd/fwupd
- There is no need to explicitly
enablethefwupd.serviceas its static in nature which gets invoked automatically whenfwupdagentorfwupdmgrcommands are ran, the service will start automatically.
2. Updating firmware using fwupdmgr
- Use fwupdmgr to download the latest metadata from the LVFS:
NOTE: by default LVFS is not enabled on RHEL systems. After executing the fwupdmgr refresh command system asks user to enable LVFS so as to fetch latest device firmware metadata from LVFS.
# fwupdmgr refresh
No remotes are currently enabled so no metadata is available.
Metadata can be obtained from the Linux Vendor Firmware Service.
Enable this remote? [Y|n]: Y ⇐
The LVFS is a free service that operates as an independent legal entity and has no connection with Red Hat Enterprise Linux Workstation. Your distributor may not have verified any of the firmware updates for compatibility with your system or connected devices. All firmware is provided only by the original equipment manufacturer.
Enabling this functionality is done at your own risk, which means you have to contact your original equipment manufacturer regarding any problems caused by these updates. Only problems with the update process itself should be filed at https://bugzilla.redhat.com/.
Agree and enable the remote? [Y|n]: Y ⇐
Fetching metadata https://cdn.fwupd.org/downloads/firmware.xml.gz
Downloading… [***************************************]
Fetching signature https://cdn.fwupd.org/downloads/firmware.xml.gz.asc
Authenticating… [***************************************]
- List out available updates for any devices on the system:
# fwupdmgr get-updates
- Before proceeding with update, use below command to list out hardware devices for which
fwupddo not support firmware updates:
# fwupdmgr get-devices --show-all-devices
Intel AMT [unprovisioned]
DeviceId: 088df415cdee883ec89563e41e6d495924250174
Guid: 2800f812-b7b4-2d4b-aca8-46e0ff65814c
Summary: Hardware and firmware technology for remote out-of-band management
Plugin: amt
Flags: internal|registered
Vendor: Intel Corporation
Version: 11.8.65
VersionBootloader: 11.8.65
Icon: computer
Created: 2020-09-29
UHD Graphics 620
DeviceId: 8de6c7959053fd5798006dcc63590d33fa5e51cb
Guid: 8eb8bd2e-0fca-5aba-9aa8-f341e0aa4482
Plugin: udev
Flags: internal|registered
Vendor: Intel Corporation
VendorId: PCI:0x8086
Icon: audio-card
Created: 2020-09-29
- Install available updates with the help of below command:
# fwupdmgr update
3. Updating firmware using GNOME Software
- Users can also use the GNOME Software application to update device firmwares. Enable LVFS from
Software Repositoriesmenu available in GNOME Software.
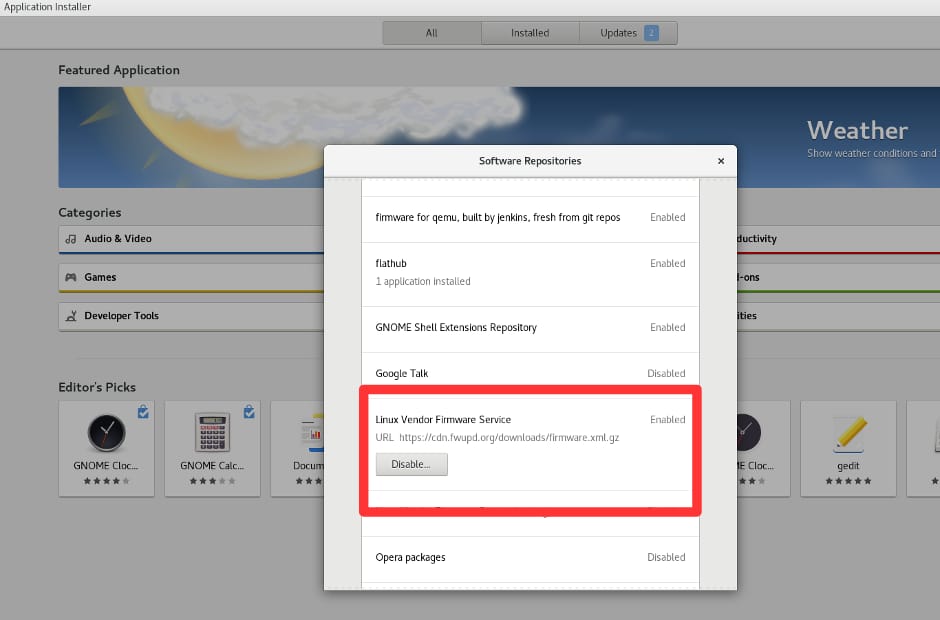
- Since required metadata files are automatically downloaded from the LVFS and submitted into fwupd over D-Bus,
if there are updates that need applying then they are downloaded and the user is notified and the update details are shown. The user has to explicitly agree to the firmware update action before the update is performed.

NOTE:
- Updates that can be applied live will be done immediately.
- Updates that run at bootup will be staged for the next reboot.
- The root user may be required to perform certain device updates.
Limitations of fwupd
-
fwupd uses firmware metadata to fetch firmware updates for hardware devices running on systems. With access to LVFS, customers will get firmware updates directly from the hardware vendor. Although it must be noted that such updates will not be verified by Red Hat QA as they are directly shared by hardware vendors through LVFS in the same way customers use to download and install the updates from OEM’s Support Portal .
-
As there are a significant number of legal problems with the redistribution of firmware, many hardware vendors are still finding acceptable methods of redistribution whilst ensuring confidentiality throughout the process.
References:
Check list of Hardware Vendors providing firmware updates through LVFS
Check available firmware updates for your devices at LVFS site
Related Articles
This solution is part of Red Hat’s fast-track publication program, providing a huge library of solutions that Red Hat engineers have created while supporting our customers. To give you the knowledge you need the instant it becomes available, these articles may be presented in a raw and unedited form.


Comments