How to configure Active Directory authentication with TLS on Red Hat Satellite 6?
Environment
- Red Hat Satellite 6
- Active Directory
Issue
- How to configure Active Directory authentication with TLS on Satellite 6?
- Active Directory authentication with Red Hat Satellite 6
-
Logging in with an LDAP account results in an SSL error:
SSL_connect returned=1 errno=0 state=SSLv3 read server certificate B: certificate verify failed OpenSSL::SSL::SSLError SSL_connect returned=1 errno=0 state=SSLv3 read server certificate B: certificate verify failed app/models/auth_sources/auth_source_ldap.rb:50:in `authenticate' app/models/user.rb:190:in `try_to_login' app/controllers/users_controller.rb:71:in `login' app/models/concerns/foreman/thread_session.rb:33:in `clear_thread' lib/middleware/catch_json_parse_errors.rb:9:in `call'
Resolution
This solution is for creating a certificate in Active Directory, which can then be installed on the Satellite Servers base system, to enable secure LDAP (LDAPS).
The procedure to configure Red Hat Satellite to use AD as an LDAP server is Using LDAP. This procedure is only required if you are using AD as an LDAP server. This method does not provide single-sign on.
Note that when the use of AD is required, Red Hat recommends using AD directly as described in Using Active Directory. This method uses Kerberos for authentication, which allows for single sign-on, and does not require the certificate described here.
If secure LDAP(Lightweight Directory Access Protocol) to an Active Directory server is required, the following solution is available.
-
Install the Active Directory Certificate services role:
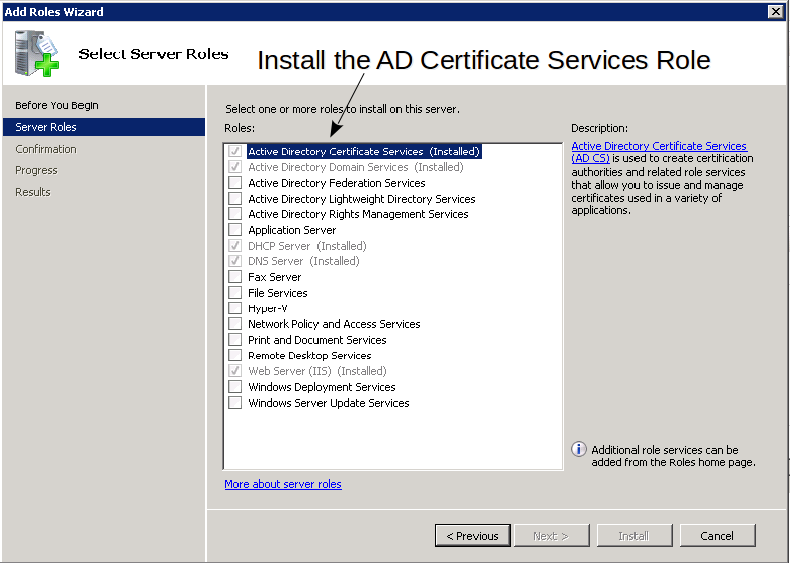
-
Select the Root CA server from the Active Directory Certificate Services console:
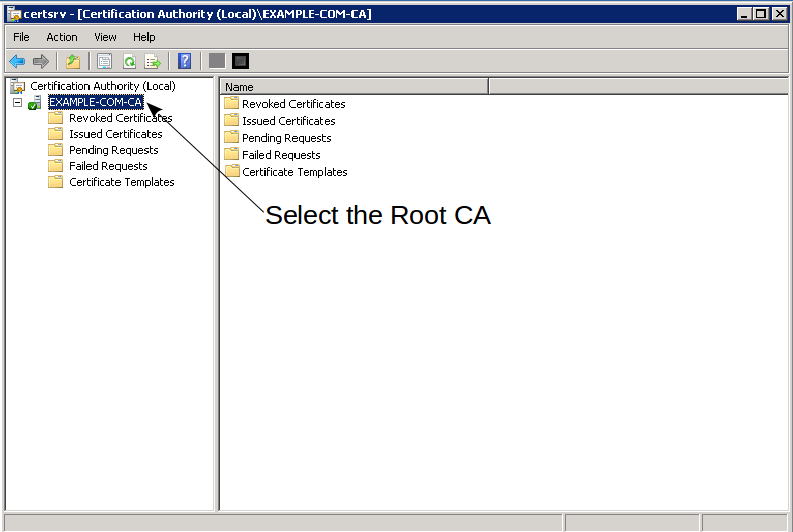
-
Right click on the Root CA server and click on its properties:
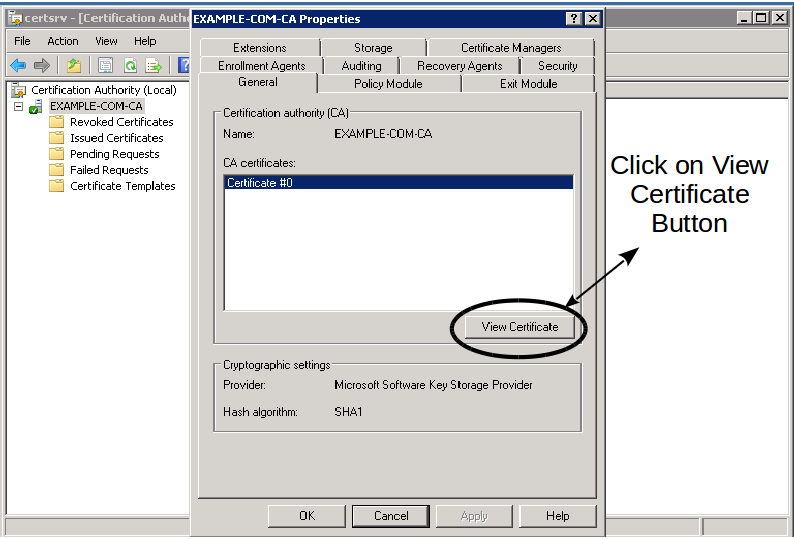
-
Click the Details tab and then click on Copy to File Button to export Active Directory CA certificate:
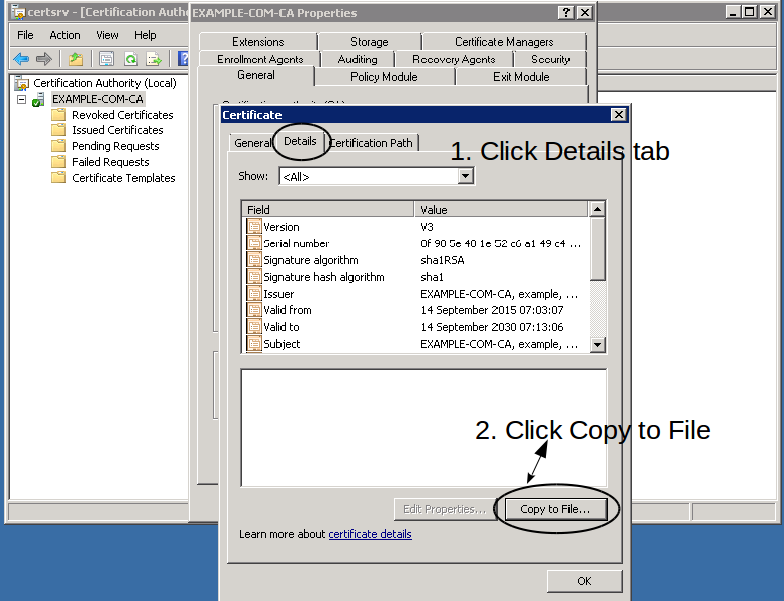
-
Select Next on the CA Certificate export wizard:
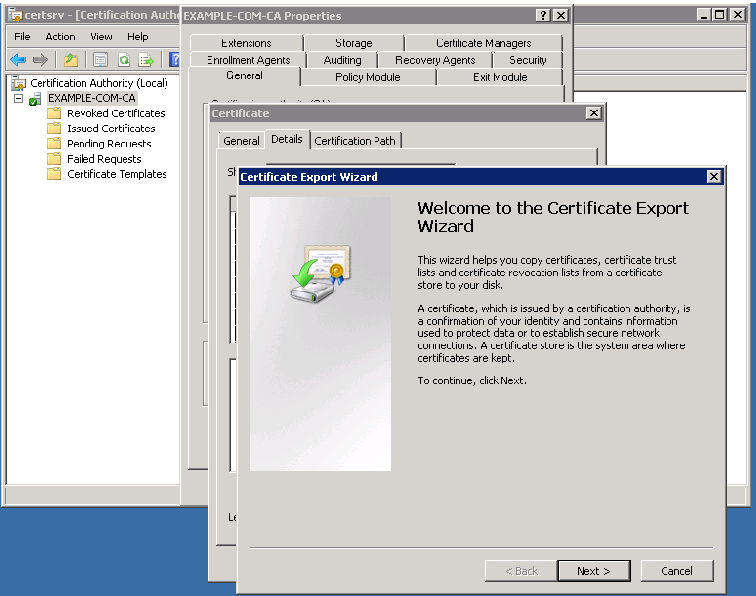
-
Select Base-64 encoded X.509 option to export the CA certificate in ASCII mode:
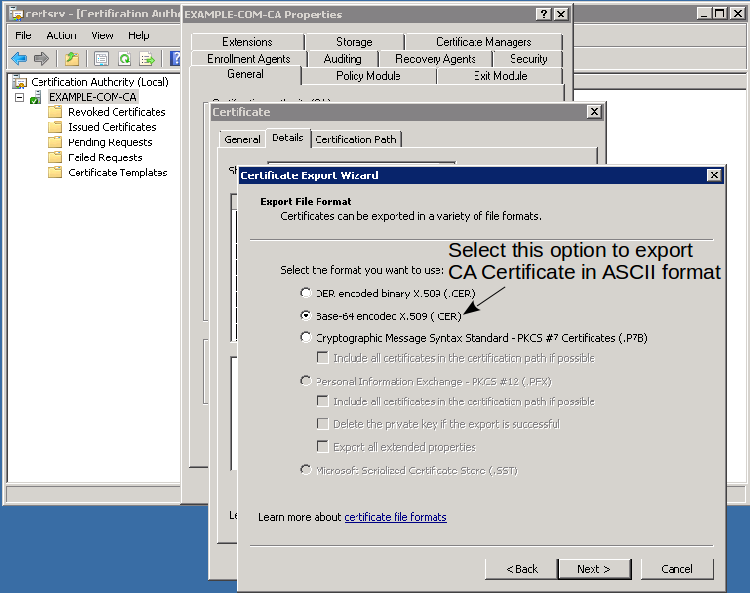
-
Specify the path and file name of the CA certificate to export:
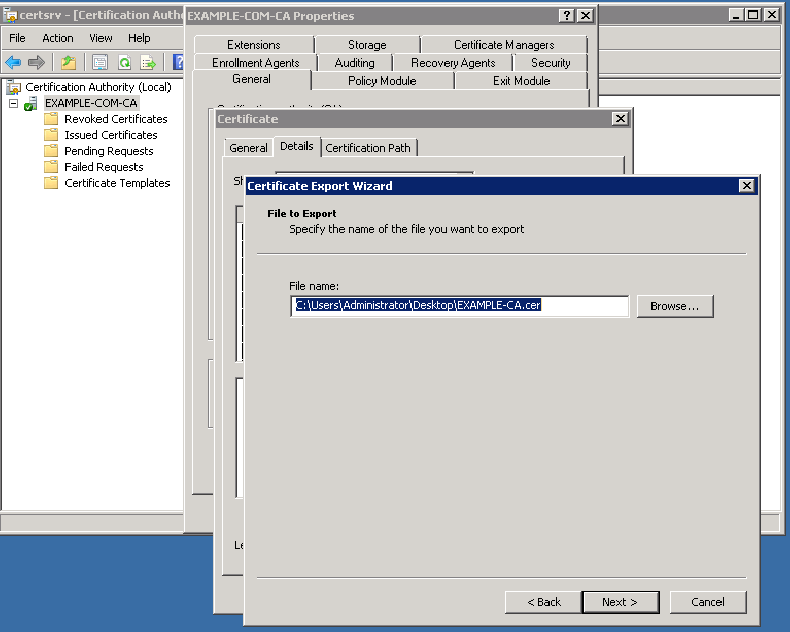
-
Review the details of the CA certificate export wizard and click on Finish to complete the export process:
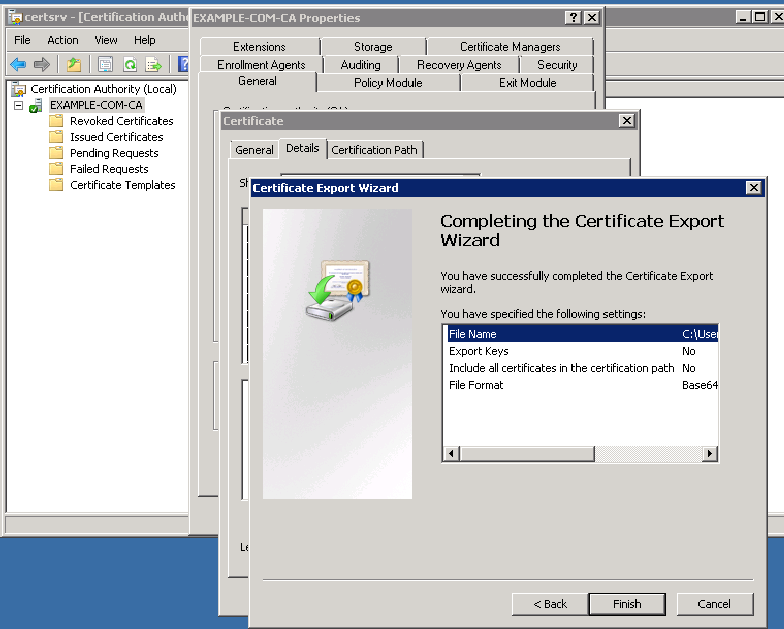
-
Alternatively, Active Directory CA certificates can be generated from the Windows Command Prompt seen here:
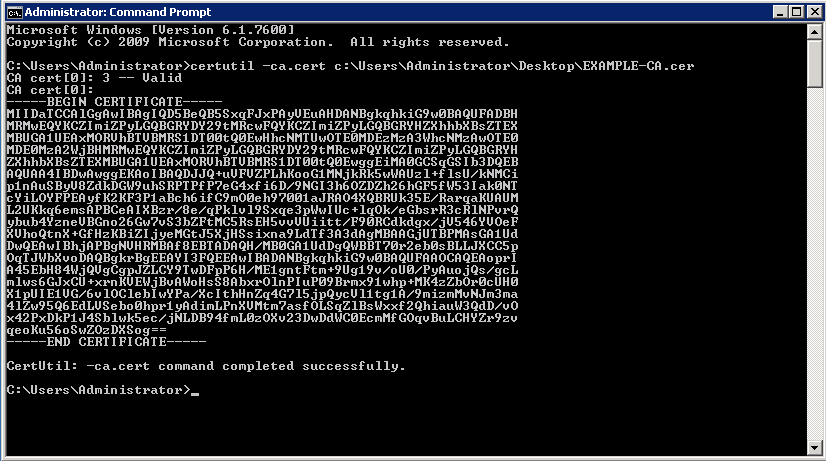
-
Copy over the exported CA Certificate file to the Red Hat Satellite 6.3 or later server and execute the following commands:
# openssl x509 -inform DER -in EXAMPLE-CA.cer -out example.crt # install example.crt /etc/pki/tls/certs/ # ln -s example.crt /etc/pki/tls/certs/$(openssl x509 -noout -hash -in /etc/pki/tls/certs/example.crt).0- Note: Make sure the certificate is in PEM format (Example:
example.crt).
Ensure the CA chain is complete and has all the required Certificate Authorities inside the bundle. ( Root + Intermediate CAs).
# openssl s_client -connect <FQDN_AD>:636 -CAfile example.crt -showcerts -state - Note: Make sure the certificate is in PEM format (Example:
-
Restart the satellite services:
[root@satellite ~]# satellite-maintain service restart -
Configure LDAP Authentication on Red Hat Satellite 6. Click Administer ---> LDAP authentication and configure it as per the following screenshots:
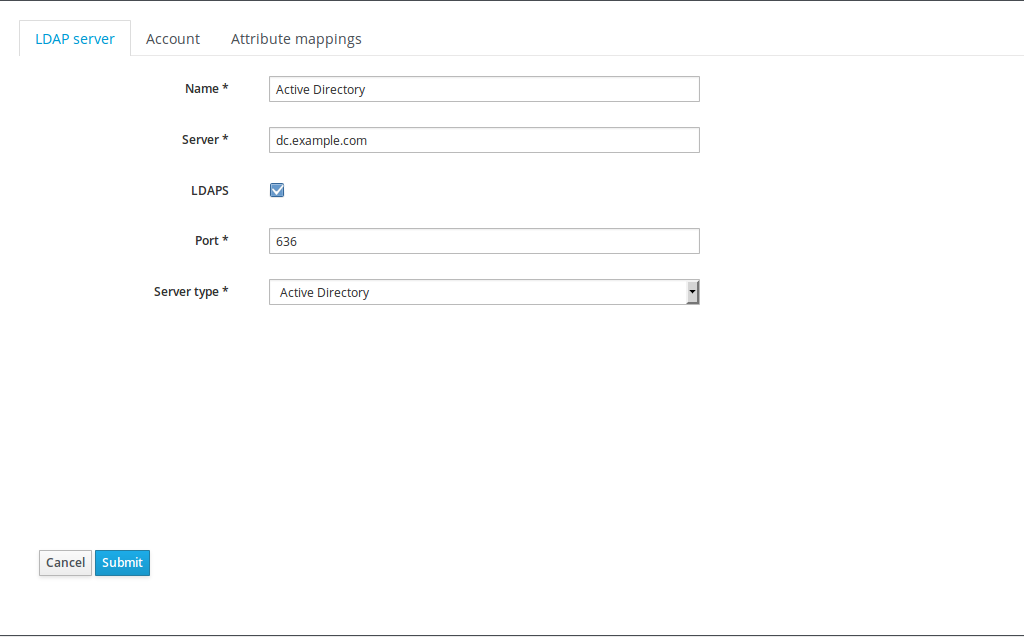


-
Log in to Red Hat Satellite 6 with Active Directory user which should authenticate successfully:
-
If the SSLv3 read server certificate B: certificate verify failed issue still persists, try adding exported CA Certificate to the
ca-bundlecertificate.# cp /etc/pki/tls/certs/ca-bundle.crt /etc/pki/tls/certs/ca-bundle.crt.bkp # cat example.crt >> /etc/pki/tls/certs/ca-bundle.crt - Copy the new ca-bundle.crt file to /etc/pki/ca-trust/source/anchors:
-
# cp -v ca-bundle.crt /etc/pki/ca-trust/source/anchors/
- Run the update-ca-trust commands below to extract and add the newly copied ca- bundle.crt file to the system-wide trust:
# update-ca-trust extract
# update-ca-trust
-
Restart satellite services:
# satellite-maintain service restart
Note: Make sure that the AD user has the email field specified in the Active Directory, which is mandatory to login to Red Hat Satellite 6 server.
For more KB articles/solutions related to Red Hat Satellite 6.x Authentication Issues, please refer to the Red Hat Satellite Consolidated Troubleshooting Article for Red Hat Satellite 6.x Authentication Issues
Attachments
This solution is part of Red Hat’s fast-track publication program, providing a huge library of solutions that Red Hat engineers have created while supporting our customers. To give you the knowledge you need the instant it becomes available, these articles may be presented in a raw and unedited form.


Comments