Resolution for POODLE SSLv3.0 vulnerability (CVE-2014-3566) in Firefox and Chromium
Environment
- Red Hat Enterprise Linux 5, 6, 7
Issue
- How to prevent Firefox and Chromium from being impacted by CVE-2014-3566
Resolution
Firefox
You can disable SSLv3 or enable TLS 1.1/1.2 by editing preferences. At initiation of a secure connection, the highest selected version (maximum supported protocol) will be attempted first. If support by the server isn't indicated or the attempt fails, the next lower version will be attempted until the lowest allowed version (minimum required protocol) is reached. To edit preferences:
1. Open a new browser window and enter 'about:config' in the URL panel, accept the warning to continue:
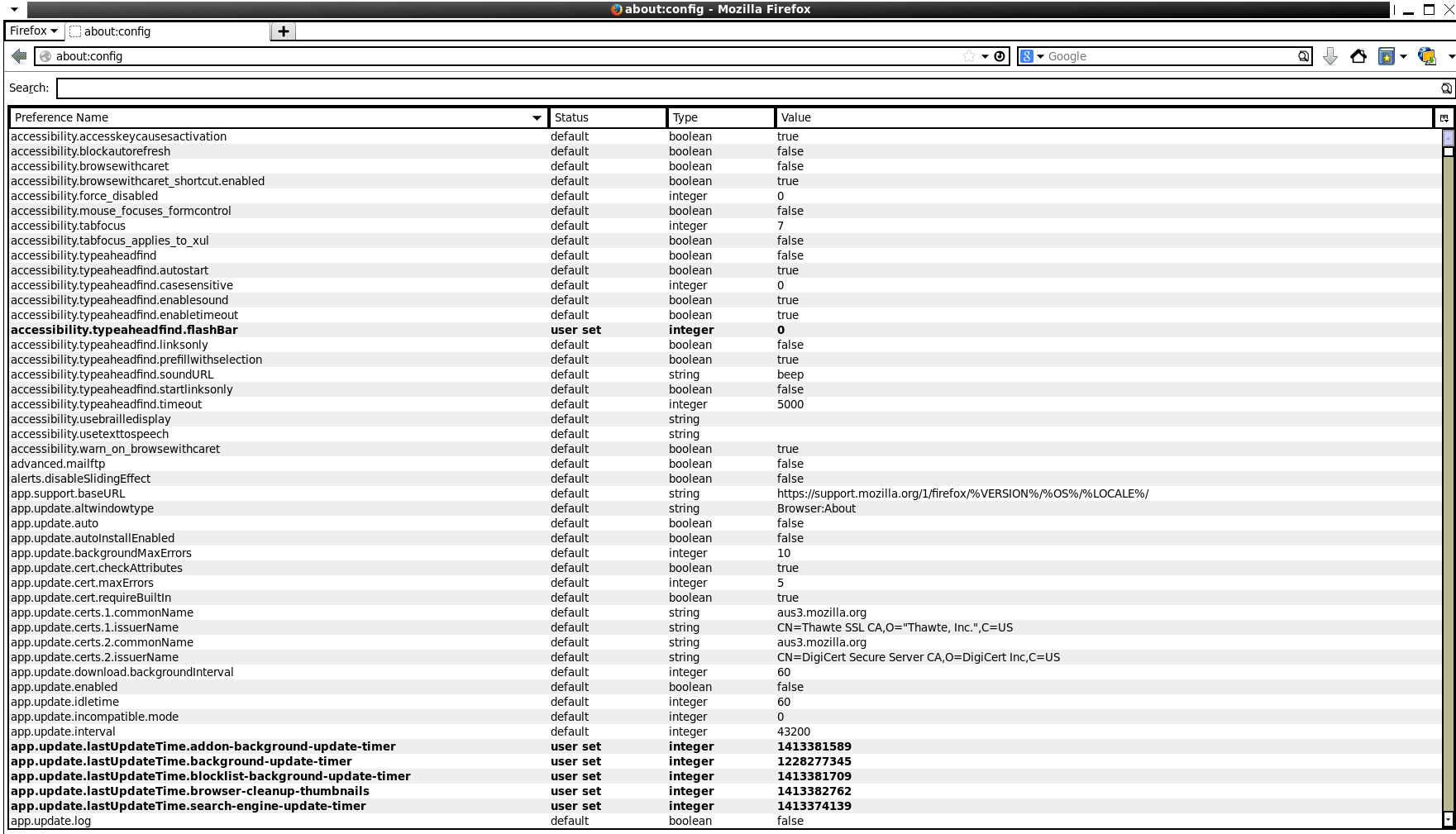
2. Enter security.tls.version.min to filter the variable responsible for setting SSL or TLS. A value of 0 indicates SSL can be used:
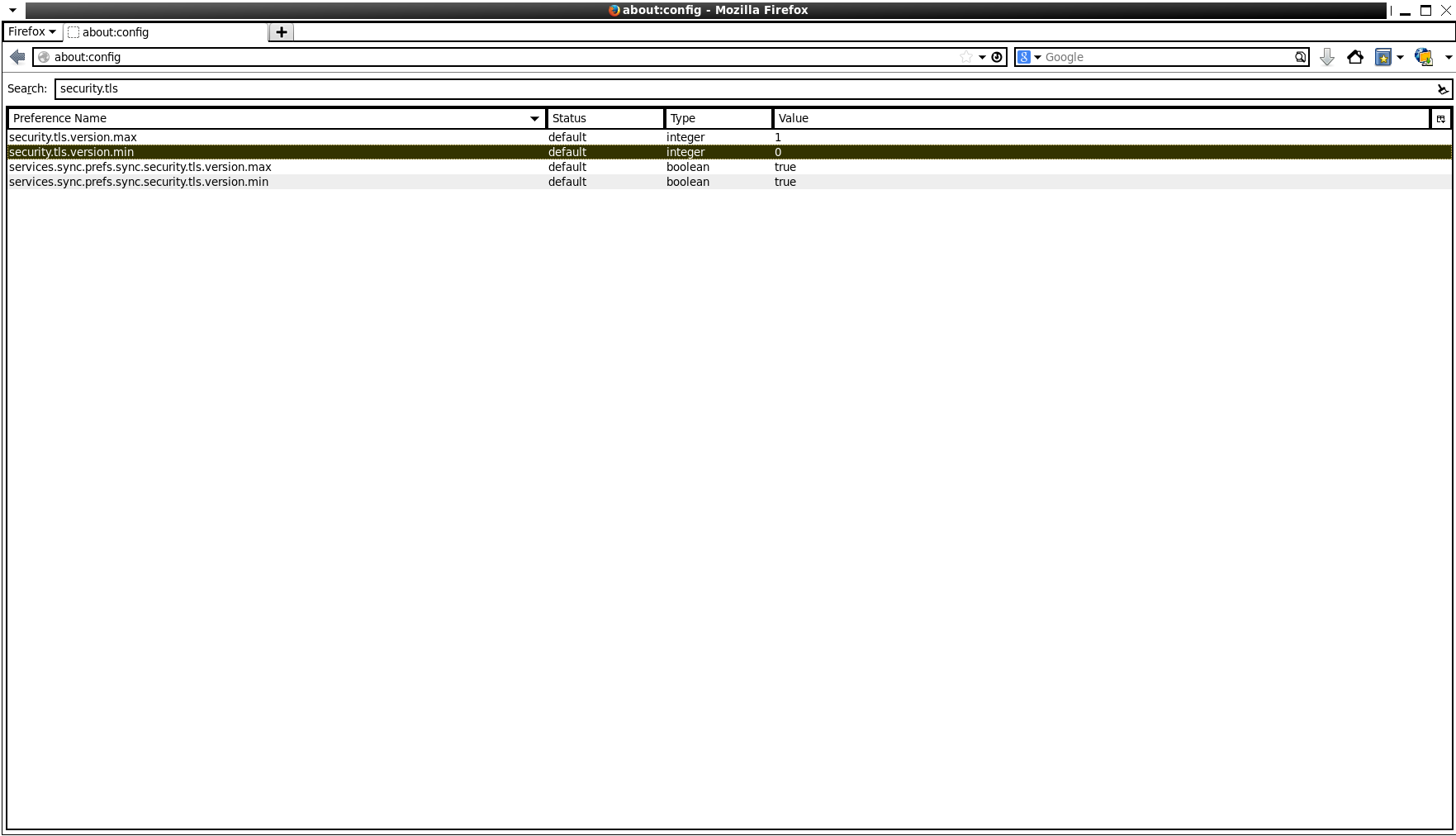
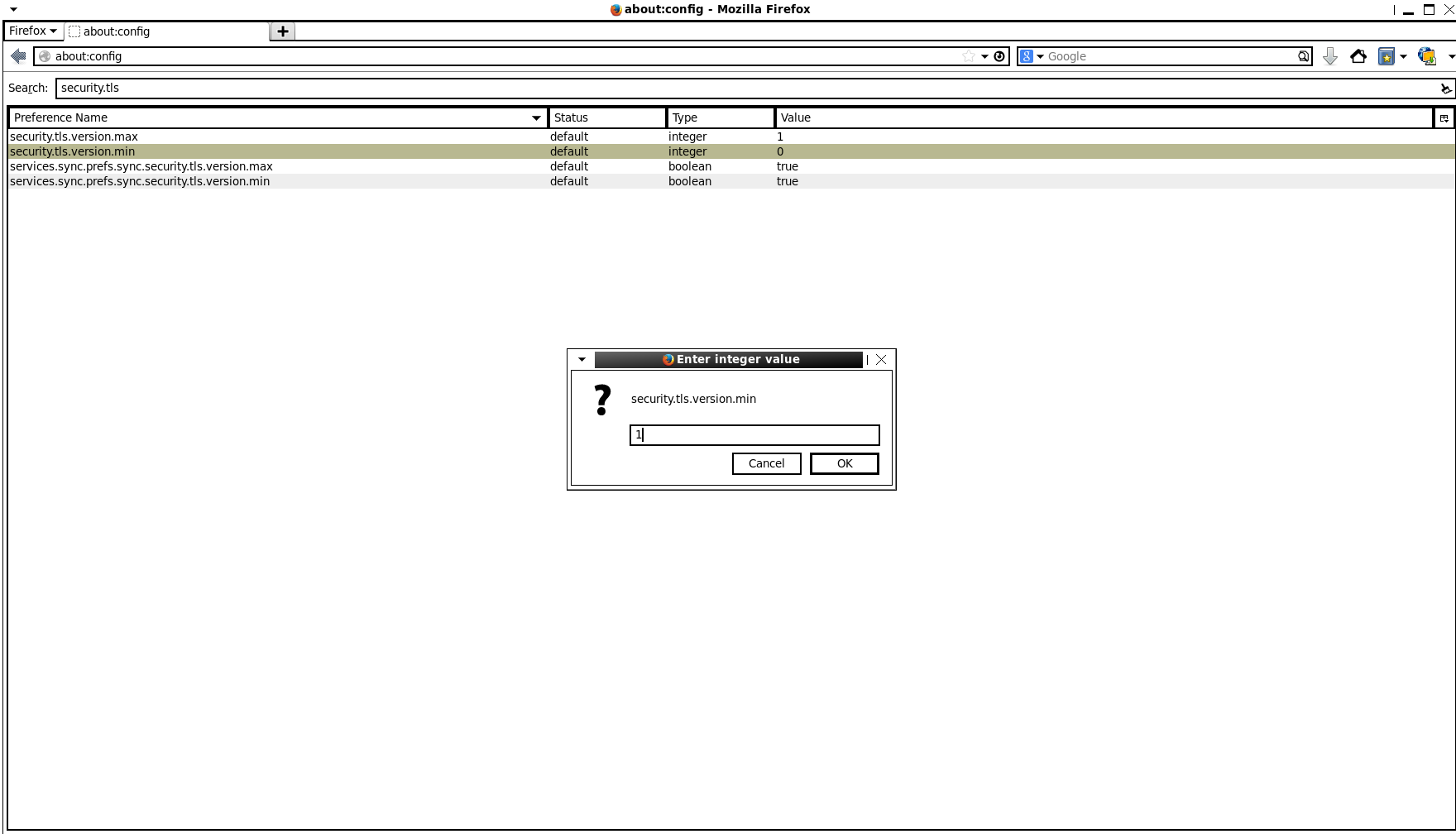
3. Double-click the variable to change the value from 0 to 1:
For more information, see this Mozilla blog post.
Chromium
Pass the following command line option to the chromium command:
--ssl-version-min=tls1
Root Cause
A vulnerability was found in the SSLv3.0 protocol. This vulnerability allows a man-in-the-middle attacker to decrypt ciphertext using a padding oracle side-channel attack. For more information about this vulnerability, refer to the following article: POODLE: SSLv3.0 vulnerability (CVE-2014-3566)
Diagnostic Steps
Red Hat Support subscribers can use the browser check in the POODLE Detector Lab
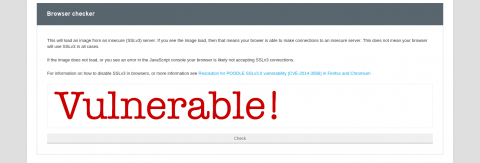
Those who do not have an active subscription can refer to the following article: POODLE: SSLv3.0 vulnerability (CVE-2014-3566)
This solution has been reviewed for technical accuracy, optimized for search, and integrated with Product Documentation and/or Red Hat Access Labs. Much like when a software package is accepted upstream, this content has moved from the general KCS editing workflow into the responsibility of Customer Content Services as maintainers.


Comments