Red Hat Training
A Red Hat training course is available for Red Hat Enterprise Linux
23.2. Configuring Certificate Mapping Rules in Identity Management
23.2.1. Certificate Mapping Rules for Configuring Authentication on Smart Cards
Subject and Issuer values, and if the new certificate has the same subject and issuer as the old one, the mapping still applies. If, in contrast, the full certificate was used, then the administrator would have to upload the new certificate to the user entry to replace the old one.
- An administrator has to load the certificate mapping data (typically the issuer and subject) or the full certificate into a user account.
- An administrator has to create a certificate mapping rule to allow successful logging into IdM for a user:
- whose account contains a certificate mapping data entry
- whose certificate mapping data entry matches the information on the certificate
For details on the individual components that make up a mapping rule and how to obtain and use them, see Components of an identity mapping rule in IdM and Obtaining the issuer from a certificate for use in a matching rule.
23.2.1.1. Certificate Mapping Rules for Trusts with Active Directory Domains
- If the certificate is issued by AD but the user and the certificate are stored in IdM, the mapping and the whole processing of the authentication request takes place on the IdM side. For details of configuring this scenario, see Section 23.2.2, “Configuring Certificate Mapping for Users Stored in IdM”.
- If the user is stored in AD, the processing of the authentication request takes place in AD. There are three different subcases:
- The AD user entry contains the whole certificate. For details how to configure IdM in this scenario, see Section 23.2.3, “Configuring Certificate Mapping for Users Whose AD User Entry Contains the Whole Certificate”.
- AD is configured to map user certificates to user accounts. In this case, the AD user entry does not contain the whole certificate but instead contains an attribute called
altSecurityIdentities. For details how to configure IdM in this scenario, see Section 23.2.4, “Configuring Certificate Mapping if AD is Configured to Map User Certificates to User Accounts”. - The AD user entry contains neither the whole certificate nor the mapping data. In this case, the only solution is to use the ipa idoverrideuser-add command to add the whole certificate to the AD user’s ID override in IdM. For details, see Section 23.2.5, “Configuring Certificate Mapping if the AD User Entry Contains no Certificate or Mapping Data”.
23.2.1.2. Components of an Identity Mapping Rule in IdM
- Mapping Rule
- The mapping rule component associates (or maps) a certificate with one or more user accounts. The rule defines an LDAP search filter that associates a certificate with the intended user account.Certificates issued by different certificate authorities (CAs) might have different properties and might be used in different domains. Therefore, IdM does not apply mapping rules unconditionally, but only to the appropriate certificates. The appropriate certificates are defined using matching rules.Note that if you leave the mapping rule option empty, the certificates are searched in the
userCertificateattribute as a DER encoded binary file.Define the mapping rule in the command line using the--mapruleoption. - Matching Rule
- The domain list specifies the identity domains in which you want IdM to search the users when processing identity mapping rules. If you leave the option unspecified, IdM searches the users only in the local domain to which the IdM client belongs.Define the domain in the command line using the
--domainoption. - Priority
- When multiple rules are applicable to a certificate, the rule with the highest priority takes precedence. All other rules are ignored.
- The lower the numerical value, the higher the priority of the identity mapping rule. For example, a rule with a priority 1 has higher priority than a rule with a priority 2.
- If a rule has no priority value defined, it has the lowest priority.
Define the mapping rule priority in the command line using the--priorityoption.
Example 23.1. Certificate Mapping Rule Example
simple_rule that allows authentication for a certificate issued by the Smart Card CA of the EXAMPLE.ORG organisation as long as the Subject on that certificate matches a certmapdata entry in a user account in IdM:
# ipa certmaprule-add simple_rule --matchrule '<ISSUER>CN=Smart Card CA,O=EXAMPLE.ORG' --maprule '(ipacertmapdata=X509:<I>{issuer_dn!nss_x500}<S>{subject_dn!nss_x500})'23.2.1.3. Obtaining the Issuer from a Certificate for Use in a Matching Rule
Prerequisites
- You have the user certificate in a
.pemor.crtformat.
Procedure
- Obtain the user information from the certificate. Use the openssl certificate display and signing utility with:
- the
-nooutoption to prevent the output of an encoded version of the request - the
-issueroption to output the issuer name - the
-inoption to specify the input file name to read the certificate from - the
-nameoptoption with the RFC2253 value to display the output with the most specific relative distinguished name (RDN) first
If the input file contains an Identity Management certificate, the output of the command shows that the Issuer is defined using theOrganisationinformation:# openssl x509 -noout -issuer -in idm_user.crt -nameopt RFC2253 issuer=CN=Certificate Authority,O=REALM.EXAMPLE.COM
If the input file contains an Active Directory certificate, the output of the command shows that the Issuer is defined using theDomain Componentinformation:# # openssl x509 -noout -issuer -in ad_user.crt -nameopt RFC2253 issuer=CN=AD-WIN2012R2-CA,DC=AD,DC=EXAMPLE,DC=COM
- Optionally, to create a new mapping rule in the command line based on a matching rule which specifies that the certificate issuer must be the extracted
AD-WIN2012R2-CAof thead.example.comdomain and the subject on the certificate must match thecertmapdataentry in a user account in IdM:# ipa certmaprule-add simple_rule --matchrule '<ISSUER>CN=AD-WIN2012R2-CA,DC=AD,DC=EXAMPLE,DC=COM' --maprule '(ipacertmapdata=X509:<I>{issuer_dn!nss_x500}<S>{subject_dn!nss_x500})'
Additional Information
23.2.2. Configuring Certificate Mapping for Users Stored in IdM
Prerequisites
- The user has an account in IdM.
- The administrator has either the whole certificate or the certificate mapping data to add to the user entry.
23.2.2.1. Adding a Certificate Mapping Rule in IdM
23.2.2.1.1. Adding a Certificate Mapping Rule in the IdM Web UI
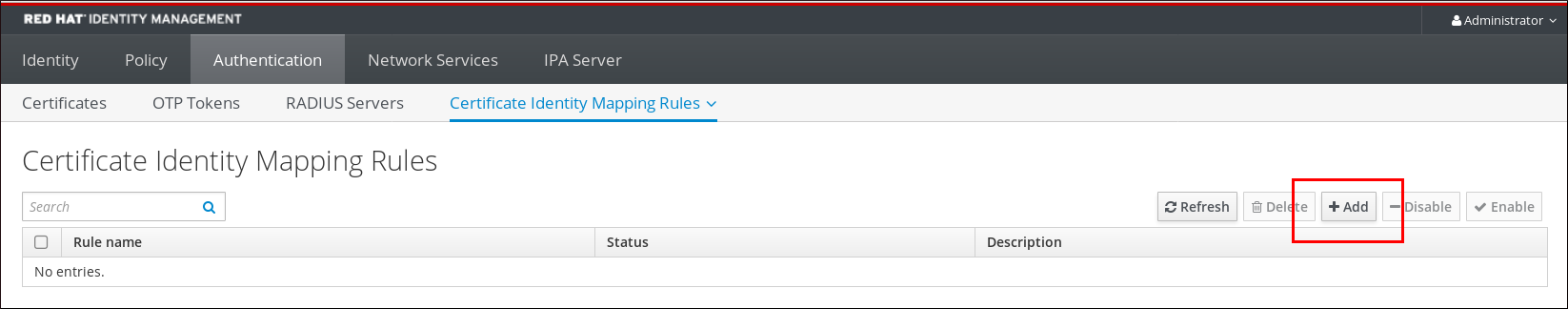
- Log in to the IdM web UI as an administrator.
- Navigate to Authentication → Certificate Identity Mapping Rules → Certificate Identity Mapping Rules.
- Click Add.
Figure 23.1. Adding a New Certificate Mapping Rule in the IdM Web UI
- Enter the rule name.
- Enter the mapping rule. For example, to make IdM search for the
IssuerandSubjectentries in any certificate presented to them, and base its decision to authenticate or not on the information found in these two entries of the presented certificate, enter:(ipacertmapdata=X509:<I>{issuer_dn!nss_x500}<S>{subject_dn!nss_x500}) - Enter the matching rule. For example, to only allow certificates issued by the
Smart Card CAof theEXAMPLE.ORGorganization to authenticate users to IdM, enter:<ISSUER>CN=Smart Card CA,O=EXAMPLE.ORG
Figure 23.2. Entering the Details for a Certificate Mapping Rule in the IdM Web UI

- Click Add at the bottom of the dialog box to add the rule and close the box.
- The System Security Services Daemon (SSSD) periodically re-reads the certificate mapping rules. To force the newly-created rule to be loaded immediately, restart SSSD:
# systemctl restart sssd
23.2.2.1.2. Adding a Certificate Mapping Rule Using the Command Line
- Obtain the administrator’s credentials:
# kinit admin
- Enter the mapping rule and the matching rule the mapping rule is based on. For example, to make IdM search for the
IssuerandSubjectentries in any certificate presented, and base its decision to authenticate or not on the information found in these two entries of the presented certificate, recognizing only certificates issued by theSmart Card CAof theEXAMPLE.ORGorganization:# ipa certmaprule-add rule_name --matchrule '<ISSUER>CN=Smart Card CA,O=EXAMPLE.ORG' --maprule '(ipacertmapdata=X509:<I>{issuer_dn!nss_x500}<S>{subject_dn!nss_x500})' ------------------------------------------------------- Added Certificate Identity Mapping Rule "rule_name" ------------------------------------------------------- Rule name: rule_name Mapping rule: (ipacertmapdata=X509:<I>{issuer_dn!nss_x500}<S>{subject_dn!nss_x500}) Matching rule: <ISSUER>CN=Smart Card CA,O=EXAMPLE.ORG Enabled: TRUE - The System Security Services Daemon (SSSD) periodically re-reads the certificate mapping rules. To force the newly-created rule to be loaded immediately, restart SSSD:
# systemctl restart sssd
23.2.2.2. Adding Certificate Mapping Data to a User Entry in IdM
23.2.2.2.1. Adding Certificate Mapping Data to a User Entry in the IdM Web UI
- Log in to the IdM web UI as an administrator.
- Navigate to Users → Active users and click the user entry.
- Find the Certificate mapping data option, and click Add.
- If you have the certificate of the user at your disposal:
- In the command-line interface, display the certificate using the
catutility or a text editor:# [root@server ~]# cat idm_user_certificate.pem -----BEGIN CERTIFICATE----- MIIFFTCCA/2gAwIBAgIBEjANBgkqhkiG9w0BAQsFADA6MRgwFgYDVQQKDA9JRE0u RVhBTVBMRS5DT00xHjAcBgNVBAMMFUNlcnRpZmljYXRlIEF1dGhvcml0eTAeFw0x ODA5MDIxODE1MzlaFw0yMDA5MDIxODE1MzlaMCwxGDAWBgNVBAoMD0lETS5FWEFN [...output truncated...]
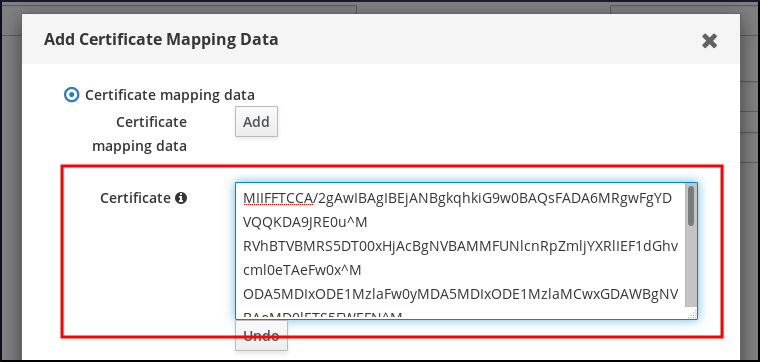
- Copy the certificate.
- In the IdM web UI, click Add next to Certificate, and paste the certificate into the window that opens up.
Figure 23.3. Adding a User's Certificate Mapping Data: Certificate
 Alternatively, if you do not have the certificate of the user at your disposal but know the
Alternatively, if you do not have the certificate of the user at your disposal but know theIssuerand theSubjectof the certificate, check the radio button of Issuer and subject and enter the values in the two respective boxes.Figure 23.4. Adding a User's Certificate Mapping Data: Issuer and Subject

- Click Add.
- Optionally, if you have access to the whole certificate in the
.pemformat, verify that the user and certificate are linked:- Use the
sss_cacheutility to invalidate the record of the user in the SSSD cache and force a reload of the user's information:# sss_cache -u user_name
- Run the ipa certmap-match command with the name of the file containing the certificate of the IdM user:
# ipa certmap-match idm_user_cert.pem -------------- 1 user matched -------------- Domain: IDM.EXAMPLE.COM User logins: idm_user ---------------------------- Number of entries returned 1 ----------------------------
The output confirms that now you have certificate mapping data added to the user and that a corresponding mapping rule defined in Section 23.2.2.1, “Adding a Certificate Mapping Rule in IdM” exists. This means that you can use any certificate that matches the defined certificate mapping data to authenticate as the user.
23.2.2.2.2. Adding Certificate Mapping Data to a User Entry Using the Command Line
- Obtain the administrator’s credentials:
# kinit admin
- If you have the certificate of the user at your disposal, add the certificate to the user account using the ipa user-add-cert command:
# CERT=`cat idm_user_cert.pem | tail -n +2 | head -n -1 | tr -d '\r\n'\` # ipa user-add-certmapdata idm_user --certificate $CERT
Alternatively, if you do not have the certificate of the user at your disposal but know theIssuerand theSubjectof the user's certificate:# ipa user-add-certmapdata idm_user --subject "O=EXAMPLE.ORG,CN=test" --issuer "CN=Smart Card CA,O=EXAMPLE.ORG" -------------------------------------------- Added certificate mappings to user "idm_user" -------------------------------------------- User login: idm_user Certificate mapping data: X509:<I>O=EXAMPLE.ORG,CN=Smart Card CA<S>CN=test,O=EXAMPLE.ORG
- Optionally, if you have access to the whole certificate in the
.pemformat, verify that the user and certificate are linked:- Use the
sss_cacheutility to invalidate the record of the user in the SSSD cache and force a reload of the user's information:# sss_cache -u user_name
- Run the ipa certmap-match command with the name of the file containing the certificate of the IdM user:
# ipa certmap-match idm_user_cert.pem -------------- 1 user matched -------------- Domain: IDM.EXAMPLE.COM User logins: idm_user ---------------------------- Number of entries returned 1 ----------------------------
23.2.3. Configuring Certificate Mapping for Users Whose AD User Entry Contains the Whole Certificate
Prerequisites
- The user does not have an account in IdM.
- The user has an account in AD which contains a certificate.
- The IdM administrator has access to data on which the IdM certificate mapping rule can be based.
23.2.3.1. Adding a Certificate Mapping Rule for Users Whose AD User Entry Contains the Whole Certificate Using the IdM Web UI
- Log in to the IdM web UI as an administrator.
- Navigate to Authentication → Certificate Identity Mapping Rules → Certificate Identity Mapping Rules.
- Click Add.
Figure 23.5. Adding a New Certificate Mapping Rule in the IdM Web UI

- Enter the rule name.
- Enter the mapping rule. To have the whole certificate that is presented to IdM for authentication compared to what is available in AD:
(userCertificate;binary={cert!bin}) - Enter the matching rule. For example, to only allow certificates issued by the
AD-ROOT-CAof theAD.EXAMPLE.COMdomain to authenticate:<ISSUER>CN=AD-ROOT-CA,DC=ad,DC=example,DC=com
Figure 23.6. Certificate Mapping Rule for a User with a Certificate Stored in AD

- Click Add.
- The System Security Services Daemon (SSSD) periodically re-reads the certificate mapping rules. To force the newly-created rule to be loaded immediately, restart SSSD:
# systemctl restart sssd
23.2.3.2. Adding a Certificate Mapping Rule for User Whose AD User Entry Contains the Whole Certificate Using the Command Line
- Obtain the administrator’s credentials:
# kinit admin
- Enter the mapping rule and the matching rule the mapping rule is based on. To have the whole certificate that is presented for authentication compared to what is available in AD, only allowing certificates issued by the
AD-ROOT-CAof theAD.EXAMPLE.COMdomain to authenticate:# ipa certmaprule-add simpleADrule --matchrule '<ISSUER>CN=AD-ROOT-CA,DC=ad,DC=example,DC=com' --maprule '(userCertificate;binary={cert!bin})' --domain ad.example.com ------------------------------------------------------- Added Certificate Identity Mapping Rule "simpleADrule" ------------------------------------------------------- Rule name: simpleADrule Mapping rule: (userCertificate;binary={cert!bin}) Matching rule: <ISSUER>CN=AD-ROOT-CA,DC=ad,DC=example,DC=com Domain name: ad.example.com Enabled: TRUE - The System Security Services Daemon (SSSD) periodically re-reads the certificate mapping rules. To force the newly-created rule to be loaded immediately, restart SSSD:
# systemctl restart sssd
23.2.4. Configuring Certificate Mapping if AD is Configured to Map User Certificates to User Accounts
Prerequisite
- The user does not have an account in IdM.
- The user has an account in AD which contains the
altSecurityIdentitiesattribute, the AD equivalent of the IdMcertmapdataattribute. - The IdM administrator has access to data on which the IdM certificate mapping rule can be based.
23.2.4.1. Adding a Certificate Mapping Rule Using the Web UI if the Trusted AD Domain is Configured to Map User Certificates
- Log in to the IdM web UI as an administrator.
- Navigate to Authentication → Certificate Identity Mapping Rules → Certificate Identity Mapping Rules.
- Click Add.
Figure 23.7. Adding a New Certificate Mapping Rule in the IdM Web UI

- Enter the rule name.
- Enter the mapping rule. For example, to make AD DC search for the
IssuerandSubjectentries in any certificate presented, and base its decision to authenticate or not on the information found in these two entries of the presented certificate:(altSecurityIdentities=X509:<I>{issuer_dn!ad_x500}<S>{subject_dn!ad_x500}) - Enter the matching rule. For example, to only allow certificates issued by the
AD-ROOT-CAof theAD.EXAMPLE.COMdomain to authenticate users to IdM:<ISSUER>CN=AD-ROOT-CA,DC=ad,DC=example,DC=com
- Enter the domain:
ad.example.com
Figure 23.8. Certificate Mapping Rule if AD is Configured for Mapping

- Click Add.
- The System Security Services Daemon (SSSD) periodically re-reads the certificate mapping rules. To force the newly-created rule to be loaded immediately, restart SSSD:
# systemctl restart sssd
23.2.4.2. Adding a Certificate Mapping Rule Using the Command Line if the Trusted AD Domain is Configured to Map User Certificates
- Obtain the administrator’s credentials:
# kinit admin
- Enter the mapping rule and the matching rule the mapping rule is based on. For example, to make AD search for the
IssuerandSubjectentries in any certificate presented, and only allow certificates issued by theAD-ROOT-CAof theAD.EXAMPLE.COMdomain:# ipa certmaprule-add ad_configured_for_mapping_rule --matchrule '<ISSUER>CN=AD-ROOT-CA,DC=ad,DC=example,DC=com' --maprule '(altSecurityIdentities=X509:<I>{issuer_dn!ad_x500}<S>{subject_dn!ad_x500})' --domain=ad.example.com ------------------------------------------------------- Added Certificate Identity Mapping Rule "ad_configured_for_mapping_rule" ------------------------------------------------------- Rule name: ad_configured_for_mapping_rule Mapping rule: (altSecurityIdentities=X509:<I>{issuer_dn!ad_x500}<S>{subject_dn!ad_x500}) Matching rule: <ISSUER>CN=AD-ROOT-CA,DC=ad,DC=example,DC=com Domain name: ad.example.com Enabled: TRUE - The System Security Services Daemon (SSSD) periodically re-reads the certificate mapping rules. To force the newly-created rule to be loaded immediately, restart SSSD:
# systemctl restart sssd
23.2.4.3. Checking Certificate Mapping Data on the AD Side
altSecurityIdentities attribute is the Active Directory (AD) equivalent of certmapdata user attribute in IdM. When configuring certificate mapping in IdM in the scenario when a trusted AD domain is configured to map user certificates to user accounts, the IdM system administrator needs to check that the altSecurityIdentities attribute is set correctly in the user entries in AD.
adserver.ad.example.com server that the altSecurityIdentities attribute is set in the user entry of ad_user and that the matchrule stipulates that the certificate that ad_user uses to authenticate to AD was issued by AD-ROOT-CA of the ad.example.com domain and that the subject is <S<>DC=com,DC=example,DC=ad,CN=Users,CN=ad_user:
$ ldapsearch -o ldif-wrap=no -LLL -h adserver.ad.example.com \ -p 389 -D cn=Administrator,cn=users,dc=ad,dc=example,dc=com \ -W -b cn=users,dc=ad,dc=example,dc=com "(cn=ad_user)" \ altSecurityIdentities Enter LDAP Password: dn: CN=ad_user,CN=Users,DC=ad,DC=example,DC=com altSecurityIdentities: X509:<I>DC=com,DC=example,DC=ad,CN=AD-ROOT-CA<S>DC=com,DC=example,DC=ad,CN=Users,CN=ad_user
23.2.5. Configuring Certificate Mapping if the AD User Entry Contains no Certificate or Mapping Data
Prerequisites
- The user does not have an account in IdM.
- The user has an account in AD which contains neither the whole certificate nor the
altSecurityIdentitiesattribute, the AD equivalent of the IdMcertmapdataattribute. - The IdM administrator has the whole AD user certificate to add to the AD user’s
user ID overridein IdM.
23.2.5.1. Adding a Certificate Mapping Rule Using the Web UI if the AD User Entry Contains no Certificate or Mapping Data
- Log in to the IdM web UI as an administrator.
- Navigate to Authentication → Certificate Identity Mapping Rules → Certificate Identity Mapping Rules.
- Click Add.
Figure 23.9. Adding a New Certificate Mapping Rule in the IdM Web UI

- Enter the rule name.
- Enter the mapping rule. To have the whole certificate that is presented to IdM for authentication compared to the certificate stored in the user ID override entry of the AD user entry in IdM:
(userCertificate;binary={cert!bin}) - Enter the matching rule. For example, to only allow certificates issued by the
AD-ROOT-CAof theAD.EXAMPLE.COMdomain to authenticate:<ISSUER>CN=AD-ROOT-CA,DC=ad,DC=example,DC=com
- Enter the domain name. For example, to search for users in the
ad.example.comdomain:Figure 23.10. Certificate Mapping Rule for a User with no Certificate or Mapping Data Stored in AD

- Click Add.
- The System Security Services Daemon (SSSD) periodically re-reads the certificate mapping rules. To force the newly-created rule to be loaded immediately, restart SSSD:
# systemctl restart sssd
23.2.5.2. Adding a Certificate Mapping Rule Using the Command Line if the AD User Entry Contains no Certificate or Mapping Data
- Obtain the administrator’s credentials:
# kinit admin
- Enter the mapping rule and the matching rule the mapping rule is based on. To have the whole certificate that is presented for authentication compared to the certificate stored in the user ID override entry of the AD user entry in IdM, only allowing certificates issued by the
AD-ROOT-CAof theAD.EXAMPLE.COMdomain to authenticate:# ipa certmaprule-add simpleADrule --matchrule '<ISSUER>CN=AD-ROOT-CA,DC=ad,DC=example,DC=com' --maprule '(userCertificate;binary={cert!bin})' --domain ad.example.com ------------------------------------------------------- Added Certificate Identity Mapping Rule "simpleADrule" ------------------------------------------------------- Rule name: simpleADrule Mapping rule: (userCertificate;binary={cert!bin}) Matching rule: <ISSUER>CN=AD-ROOT-CA,DC=ad,DC=example,DC=com Domain name: ad.example.com Enabled: TRUE - The System Security Services Daemon (SSSD) periodically re-reads the certificate mapping rules. To force the newly-created rule to be loaded immediately, restart SSSD:
# systemctl restart sssd
23.2.5.3. Adding a Certificate to an AD User’s ID Override Using the Web UI
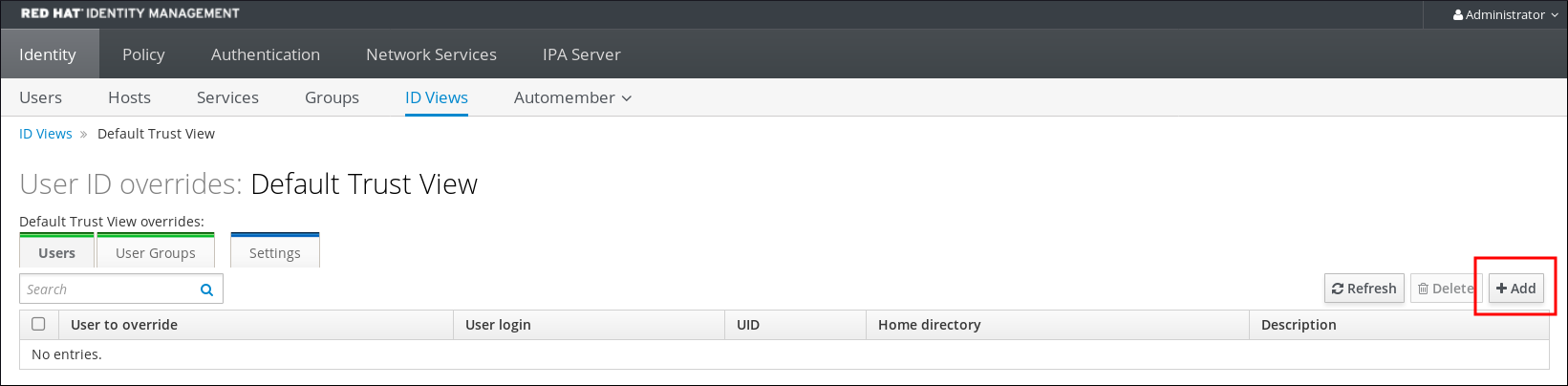
- Log in to the IdM web UI as an administrator.
- Navigate to Identity → ID Views → Default Trust View.
- Click Add.
Figure 23.11. Adding a New User ID Override in the IdM Web UI
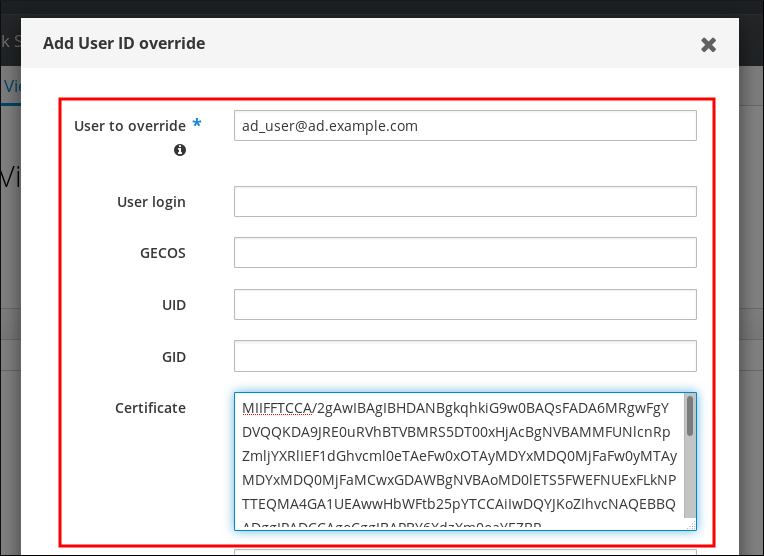
- In the User to override field, enter the user name in the following format:
user_name@domain_name - Copy and paste the certificate of the user into the Certificate field.
Figure 23.12. Configuring the User ID Override for an AD User
- Optionally, verify that the user and certificate are linked:
- Use the
sss_cacheutility to invalidate the record of the user in the SSSD cache and force a reload of the user's information:# sss_cache -u ad_user@ad.example.com
- Enter the ipa certmap-match command with the name of the file containing the certificate of the AD user:
# ipa certmap-match ad_user_cert.pem -------------- 1 user matched -------------- Domain: AD.EXAMPLE.COM User logins: ad_user@ad.example.com ---------------------------- Number of entries returned 1 ----------------------------
The output confirms that you have certificate mapping data added toad_user@ad.example.comand that a corresponding mapping rule exists. This means that you can use any certificate that matches the defined certificate mapping data to authenticate asad_user@ad.example.com.
23.2.5.4. Adding a Certificate to an AD User’s ID Override Using the Command Line
- Obtain the administrator’s credentials:
# kinit admin
- Add the certificate of the user to the user account using the ipa idoverrideuser-add-cert command:
# CERT=`cat ad_user_cert.pem | tail -n +2 | head -n -1 | tr -d '\r\n'\` # ipa idoverrideuser-add-cert ad_user@ad.example.com --certificate $CERT
- Optionally, verify that the user and certificate are linked:
- Use the
sss_cacheutility to invalidate the record of the user in the SSSD cache and force a reload of the user's information:# sss_cache -u ad_user@ad.example.com
- Enter the ipa certmap-match command with the name of the file containing the certificate of the AD user:
# ipa certmap-match ad_user_cert.pem -------------- 1 user matched -------------- Domain: AD.EXAMPLE.COM User logins: ad_user@ad.example.com ---------------------------- Number of entries returned 1 ----------------------------
The output confirms that you have certificate mapping data added toad_user@ad.example.comand that a corresponding mapping rule exists. This means that you can use any certificate that matches the defined certificate mapping data to authenticate asad_user@ad.example.com.
23.2.6. Combining Several Identity Mapping Rules Into One
$ ipa certmaprule-add ad_cert_for_ipa_and_ad_users \ --maprule='(|(ipacertmapdata=X509:<I>{issuer_dn!nss_x500}<S>{subject_dn!nss_x500})(altSecurityIdentities=X509:<I>{issuer_dn!ad_x500}<S>{subject_dn!ad_x500}))' \ --matchrule='<ISSUER>CN=AD-ROOT-CA,DC=ad,DC=example,DC=com' \ --domain=ad.example.com--maprule option includes these criteria:
ipacertmapdata=X509:<I>{issuer_dn!nss_x500}<S>{subject_dn!nss_x500}is a filter that links the subject and issuer from a smart card certificate to the value of the ipacertmapdata attribute in an IdM user account, as described in Section 23.2.2.1, “Adding a Certificate Mapping Rule in IdM”.altSecurityIdentities=X509:<I>{issuer_dn!ad_x500}<S>{subject_dn!ad_x500}is a filter that links the subject and issuer from a smart card certificate to the value of the altSecurityIdentities attribute in an AD user account, as described in Section 23.2.4, “Configuring Certificate Mapping if AD is Configured to Map User Certificates to User Accounts”.- The addition of the
--domain=ad.example.comoption means that users mapped to a given certificate are not only searched in the localidm.example.comdomain but also in thead.example.comdomain .
--maprule option accepts the logical operator | (or), so that you can specify multiple criteria. In this case, the rule maps all user accounts that meet at least one of the criteria.
$ ipa certmaprule-add ipa_cert_for_ad_users \
--maprule='(|(userCertificate;binary={cert!bin})(ipacertmapdata=X509:<I>{issuer_dn!nss_x500}<S>{subject_dn!nss_x500})(altSecurityIdentities=X509:<I>{issuer_dn!ad_x500}<S>{subject_dn!ad_x500}))' \
--matchrule='<ISSUER>CN=Certificate Authority,O=REALM.EXAMPLE.COM' \
--domain=idm.example.com --domain=ad.example.com--maprule option includes these criteria:
userCertificate;binary={cert!bin}is a filter that returns user entries that include the whole certificate. For AD users, creating this type of filter is described in detail in Section 23.2.5, “Configuring Certificate Mapping if the AD User Entry Contains no Certificate or Mapping Data”.ipacertmapdata=X509:<I>{issuer_dn!nss_x500}<S>{subject_dn!nss_x500}is a filter that links the subject and issuer from a smart card certificate to the value of theipacertmapdataattribute in an IdM user account, as described in Section 23.2.2.1, “Adding a Certificate Mapping Rule in IdM”.altSecurityIdentities=X509:<I>{issuer_dn!ad_x500}<S>{subject_dn!ad_x500}is a filter that links the subject and issuer from a smart card certificate to the value of thealtSecurityIdentitiesattribute in an AD user account, as described in Section 23.2.4, “Configuring Certificate Mapping if AD is Configured to Map User Certificates to User Accounts”.
--maprule option accepts the logical operator | (or), so that you can specify multiple criteria. In this case, the rule maps all user accounts that meet at least one of the criteria.

