Configuring IDP Mapping Method as lookup with GitHub
Environment
- Red Hat OpenShift Service on AWS [ROSA]
- 4.x
- Red Hat OpenShift Dedicated [OSD]
- 4.x
- Azure Red Hat OpenShift [ARO]
- 4.x
- Red Hat OpenShift Container Platform [RHOCP]
- 4.x
Issue
- How to permit a few users from my GitHub Organisation to get access to my cluster either by using the Web Console or the API Server via command line?
Resolution
Disclaimer: Links contained herein to external website(s) are provided for convenience only. Red Hat has not reviewed the links and is not responsible for the content or its availability. The inclusion of any link to an external website does not imply endorsement by Red Hat of the website or their entities, products or services. You agree that Red Hat is not responsible or liable for any loss or expenses that may result due to your use of (or reliance on) the external site or content.
-
In order to accomplish this task, the IDP Mapping Method needs to be configured as
lookup. By definition:lookup
Looks up an existing identity, user identity mapping, and user, but does not automatically provision users or identities. This allows cluster administrators to set up identities and users manually, or using an external process. Using this method requires you to manually provision users. -
The following procedure helps with the steps and information required to successfully have this implemented:
Pre-requisite:
- Have an Organization on Github with members who would be accessing the cluster. Reference: About organizations.
Procedure:
-
Set up the GitHub IDP as per Product documentation choosing the
Mapping Methodaslookup.
For ROSA/OSD, same steps are used. The ROSA documentation brings the step by step.
For ARO/RHOCP, please find the steps from the OCP documentation. -
After setting up the IDP, the pods on the
openshift-authenticationproject will start being replaced with the new configuration. This can be monitored by using the command below:$ watch oc get pods -n openshift-authentication -
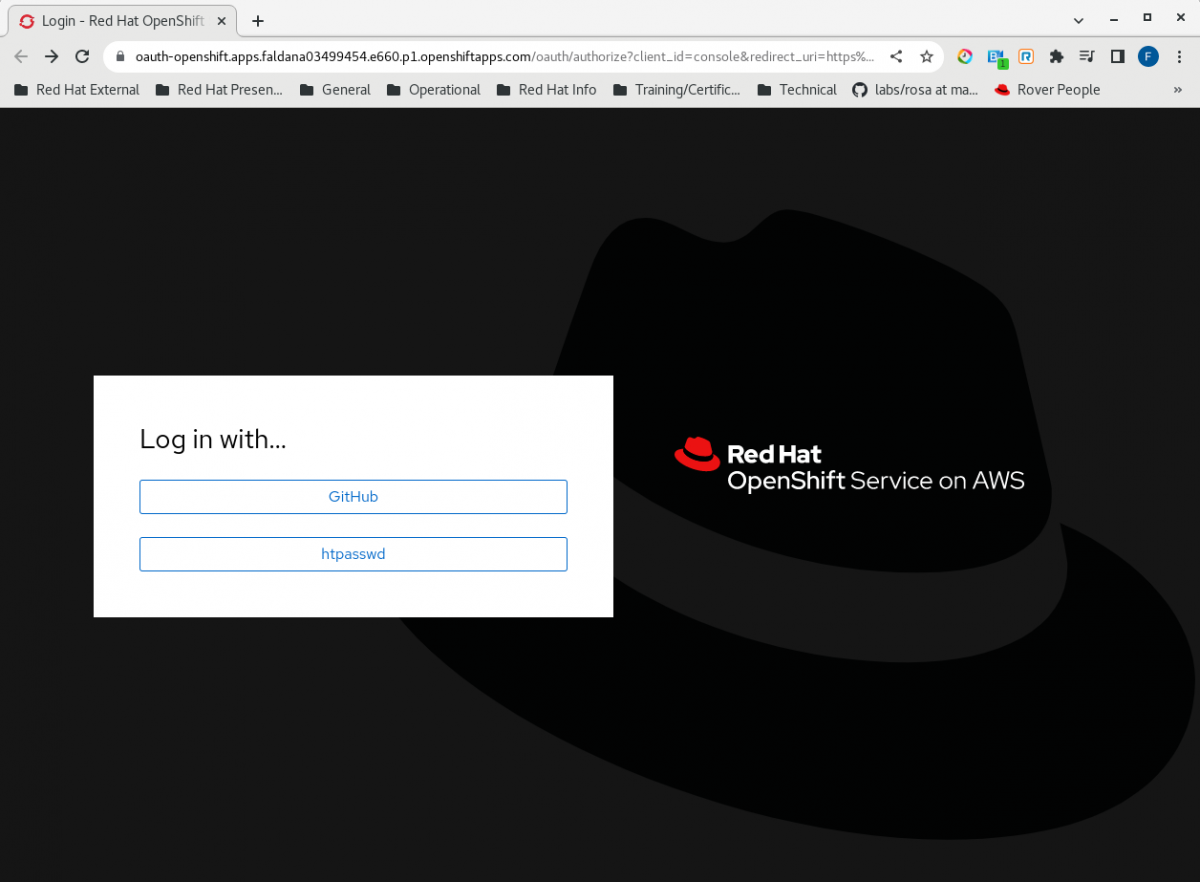
With the new configuration in place, the GitHub IDP should be ready to be used. The following OCP Login screen should be displayed on the Web Console:
- When trying to access the cluster by using the new GitHub IDP, all users will receive the error below:
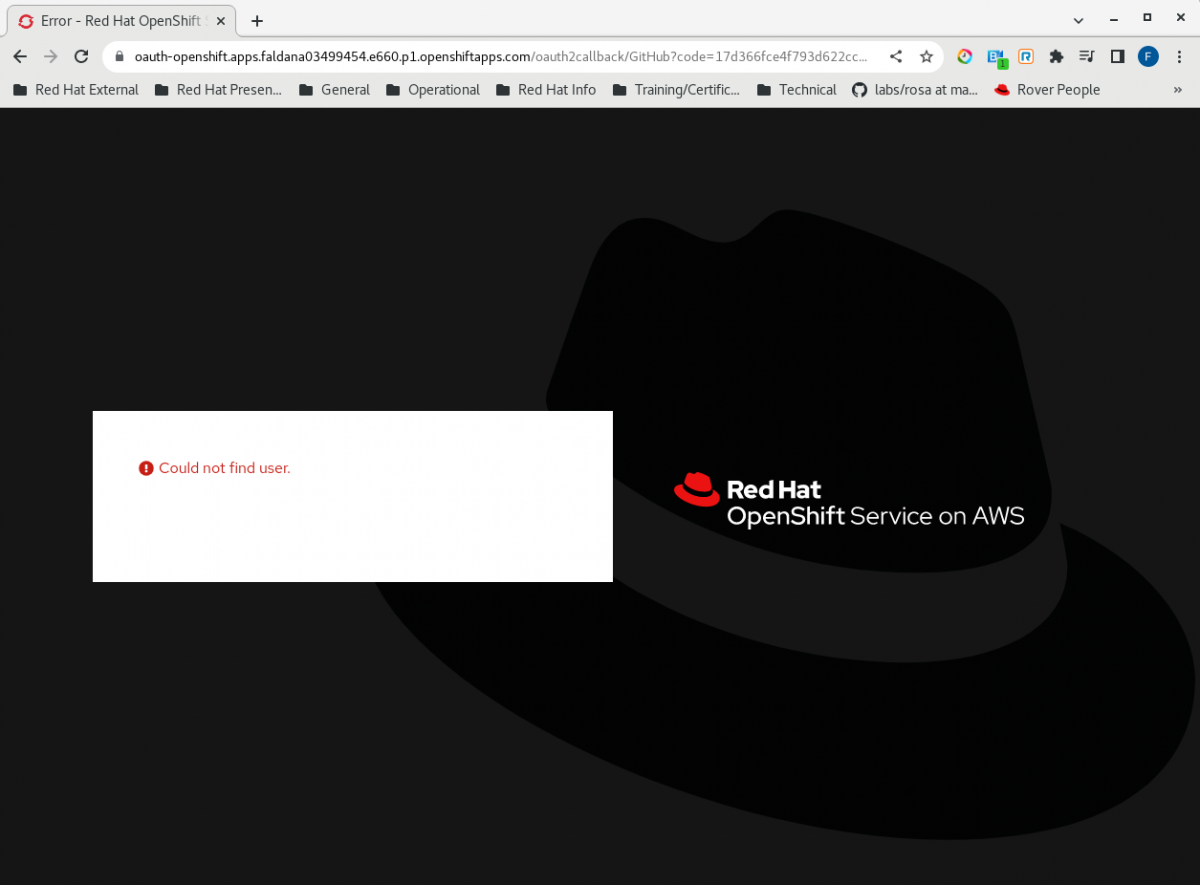
-
In order to have the GitHub members permitted to access the cluster, their user and identity need to be manually created by the Cluster Administrator:
5.1. Retrieve the GitHub user ID by using one of the methods below:
- Accessing the GitHub API: https://api.github.com/users/< username >
-
Querying the GitHub API running the
curlcommand below:$ curl -s https://api.github.com/users/<username> | jq '.id' <XXXXXXXX>
5.2. Create the OCP
user:$ oc create user <username>5.3. Create the OCP
identityby using the IDP name used on step 1 and the user ID retrieved on step 5.1:$ oc create identity <idpName:userID>5.4. Create the OCP
useridentitymapping:$ oc create useridentitymapping <idpName:userID> <username> -
Once completed all the steps above, the users will be able to access the cluster successfully.
NOTE: For other IDP methods, the same configuration applies. However, it is required to identify how to retrieve the user ID provided by the IDP method which will form the identities.
This solution is part of Red Hat’s fast-track publication program, providing a huge library of solutions that Red Hat engineers have created while supporting our customers. To give you the knowledge you need the instant it becomes available, these articles may be presented in a raw and unedited form.


Comments