Enabling and Disabling CloudWatch Audit Log Forwarding for ROSA HCP cluster
Environment
- Red Hat OpenShift Service on AWS Hosted Control Planes (ROSA HCP)
- 4
Issue
- How to enable Audit Log forwarding to CloudWatch for Red Hat OpenShift Service on AWS Hosted Control Planes (ROSA HCP)?
- How to disable Audit Log forwarding to CloudWatch for Red Hat OpenShift Service on AWS Hosted Control Planes (ROSA HCP)?
- Is it possible to enable the audit log forwarding to CloudWatch for ROSA HCP clusters?
- Is it supported to enable cross-account audit log forwarding to CloudWatch (to a different AWS Account)?
Resolution
It is possible to enable Audit Log Forwarding to CloudWatch for ROSA HCP clusters after the cluster is installed.
IMPORTANT: As of OpenShift version 4.17.2, OAuth log files are included in audit logs for all Managed OpenShift clusters. Because OAuth logs are large and detailed, including these log files in audit logs substantially increases the typical size of audit logs for a cluster.
You may need to increase available log storage on your cluster and allow additional time when gathering audit logs. This behavior is enabled by default and cannot be disabled for any Managed OpenShift cluster using the following OpenShift versions:
- 4.17.2 or later
- 4.16.19 or later minor versions
- 4.15.43 or later minor versions
Note: Enabling the audit log forwarding to CloudWatch to a different AWS Account is not supported.
Steps
-
Set the
CLUSTER_IDvariable to the ID of your ROSA HCP cluster:$ oc get clusterversion version -o jsonpath='{.spec.clusterID}{"\n"}' [...] $ CLUSTER_ID=<some ocm cluster id> -
Get the OIDC Endpoint URL by using rosa cli:
$ OIDC_ENDPOINT_URL=$(rosa describe cluster -c $CLUSTER_ID -o yaml | grep "oidc_endpoint_url" | sed -E 's|^.*oidc_endpoint_url: https://(.*)|\1|') -
Get the AWS Account ID:
$ rosa describe cluster -c $CLUSTER_ID | grep "AWS Account:" $ AWS_ACCOUNT_ID=<AWS Account result number> -
Create the Trust Relationship file
trust-relationship.json:$ cat << EOF > trust-relationship.json { "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "Federated": "arn:aws:iam::${AWS_ACCOUNT_ID}:oidc-provider/${OIDC_ENDPOINT_URL}" }, "Action": "sts:AssumeRoleWithWebIdentity", "Condition": { "StringEquals": { "${OIDC_ENDPOINT_URL}:sub": "system:serviceaccount:openshift-config-managed:cloudwatch-audit-exporter" } } } ] } EOF -
Create the CloudWatch IAM Policy file
iam-policy.json:$ cat << EOF > iam-policy.json { "Version": "2012-10-17", "Statement": [ { "Action": [ "logs:PutLogEvents", "logs:CreateLogGroup", "logs:PutRetentionPolicy", "logs:CreateLogStream", "logs:DescribeLogGroups", "logs:DescribeLogStreams" ], "Effect": "Allow", "Resource": "arn:aws:logs:*:*:*" } ] } EOF -
Create the IAM Policy and Role:
$ IAM_POLICY_NAME = <Enter_preferred_policy_name> $ IAM_ROLE_NAME = <Enter_preferred_role_name> $ IAM_POLICY_ARN=$(aws iam create-policy --policy-name $IAM_POLICY_NAME --policy-document file://iam-policy.json | jq -r '.Policy.Arn') $ IAM_ROLE_ARN=$(aws iam create-role --role-name $IAM_ROLE_NAME --assume-role-policy-document file://trust-relationship.json | jq -r '.Role.Arn') $ aws iam attach-role-policy --policy-arn ${IAM_POLICY_ARN} --role-name ${IAM_ROLE_NAME} -
To enable the CloudWatch Audit Logs Forwarding, patch the
role_arnusing the following command:$ ocm describe cluster <CLUSTER_ID> ID: <Internal_CLUSTER_ID>$ ocm patch /api/clusters_mgmt/v1/clusters/<Internal_CLUSTER_ID> << EOM { "aws": {"audit_log": {"role_arn":"$IAM_ROLE_ARN"}} } EOM -
To disable the Cloud Watch Audit Log Forwarding, please use
rosa editcommand and follow the prompts:rosa edit cluster -c <cluster_name or id> --audit-log-arn "" -
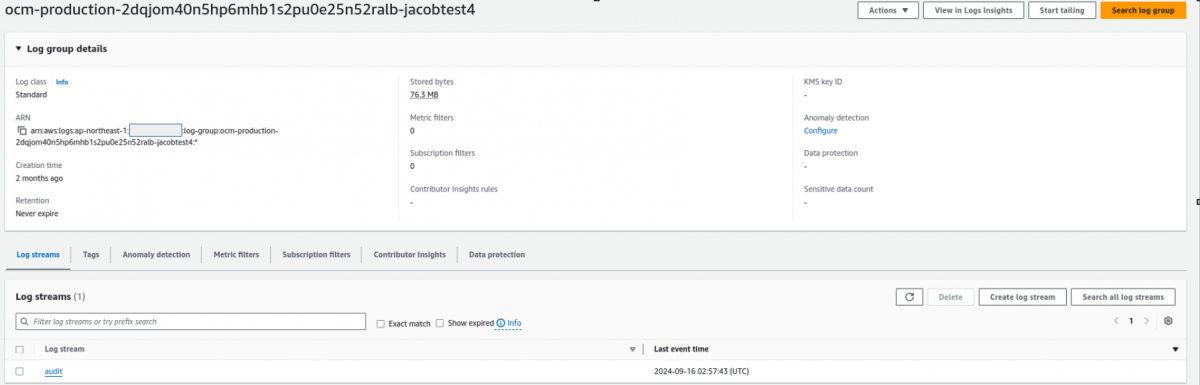
The audit log will be inside ocm-production-Internal_CLUSTER_ID-ClusterName Log Groups of cloud watch
(please check the below sample)
Root Cause
For enabling or disabling the Cloud Watch Audit Log Forwarding, additional permissions needs to be added.
Diagnostic Steps
Refer to Failed to configure audit log forwarding in ROSA HCP clusters in case the ocm patch command is failing.
This solution is part of Red Hat’s fast-track publication program, providing a huge library of solutions that Red Hat engineers have created while supporting our customers. To give you the knowledge you need the instant it becomes available, these articles may be presented in a raw and unedited form.


Comments