Joining new server to multiple AD domains
builtt 3 new RHEL 8.9 servers currently on the network but only had root access via console:
for each server I first executed
realm discover
and updated the /etc/sssd/sssd.conf
[root@arccdb11 ~]# cat /etc/sssd/sssd.conf
[sssd]
domains = ad.laker.local, rxoptions.local
config_file_version = 2
services = nss, pam
[domain/ad.laker.local]
ad_domain = ad.laker.local
krb5_realm = AD.LAKER.LOCAL
realmd_tags = manages-system joined-with-adcli
cache_credentials = True
id_provider = ad
krb5_store_password_if_offline = True
default_shell = /bin/bash
ldap_id_mapping = True
use_fully_qualified_names = True
full_name_format = $u
fallback_homedir = /home/%u
access_provider = ad
[domain/ad.laker.local/rxoptions.local]
ad_domain = rxoptions.local
krb5_realm = RXOPTIONS.LOCAL
realmd_tags = manages-system joined-with-adcli
cache_credentials = True
id_provider = ad
krb5_store_password_if_offline = True
default_shell = /bin/bash
ldap_id_mapping = True
use_fully_qualified_names = True
full_name_format = %u
fallback_homedir = /home/%u
access_provider = ad
executed join to first domain: ad.laker.local
[root@arccdb11 ~]# realm join -U bstolp-a -v ad.laker.local
* Resolving: _ldap._tcp.ad.laker.local
* Performing LDAP DSE lookup on: 10.2.6.4
* Performing LDAP DSE lookup on: 10.10.60.6
* Performing LDAP DSE lookup on: 10.2.6.6
* Successfully discovered: ad.laker.local
Password for bstolp-a:
* Required files: /usr/sbin/oddjobd, /usr/libexec/oddjob/mkhomedir, /usr/sbin/sssd, /usr/sbin/adcli
* LANG=C /usr/sbin/adcli join --verbose --domain ad.laker.local --domain-realm AD.LAKER.LOCAL --domain-controller 10.10.60.6 --login-type user --login-user bstolp-a --stdin-password
* Using domain name: ad.laker.local
* Calculated computer account name from fqdn: ARCCDB11
* Using domain realm: ad.laker.local
* Sending NetLogon ping to domain controller: 10.10.60.6
* Received NetLogon info from: CLEADS02.ad.laker.local
* Wrote out krb5.conf snippet to /var/cache/realmd/adcli-krb5-Vbaxi7/krb5.d/adcli-krb5-conf-RMg4u5
* Authenticated as user: bstolp-a@AD.LAKER.LOCAL
* Using GSS-SPNEGO for SASL bind
* Looked up short domain name: LAKERAD
* Looked up domain SID: S-1-5-21-4056373416-2870543786-2149594862
* Received NetLogon info from: CLEADS02.ad.laker.local
* Using fully qualified name: arccdb11.ad.laker.local
* Using domain name: ad.laker.local
* Using computer account name: ARCCDB11
* Using domain realm: ad.laker.local
* Calculated computer account name from fqdn: ARCCDB11
* Generated 120 character computer password
* Using keytab: FILE:/etc/krb5.keytab
* Found computer account for ARCCDB11$ at: CN=ARCCDB11,CN=Computers,DC=ad,DC=laker,DC=local
* Trying to set computer password with Kerberos
* Set computer password
* Retrieved kvno '3' for computer account in directory: CN=ARCCDB11,CN=Computers,DC=ad,DC=laker,DC=local
* Checking RestrictedKrbHost/arccdb11.ad.laker.local
* Added RestrictedKrbHost/arccdb11.ad.laker.local
* Checking RestrictedKrbHost/ARCCDB11
* Added RestrictedKrbHost/ARCCDB11
* Checking host/arccdb11.ad.laker.local
* Added host/arccdb11.ad.laker.local
* Checking host/ARCCDB11
* Added host/ARCCDB11
* Discovered which keytab salt to use
* Added the entries to the keytab: ARCCDB11$@AD.LAKER.LOCAL: FILE:/etc/krb5.keytab
* Added the entries to the keytab: host/ARCCDB11@AD.LAKER.LOCAL: FILE:/etc/krb5.keytab
* Added the entries to the keytab: host/arccdb11.ad.laker.local@AD.LAKER.LOCAL: FILE:/etc/krb5.keytab
* Added the entries to the keytab: RestrictedKrbHost/ARCCDB11@AD.LAKER.LOCAL: FILE:/etc/krb5.keytab
* Added the entries to the keytab: RestrictedKrbHost/arccdb11.ad.laker.local@AD.LAKER.LOCAL: FILE:/etc/krb5.keytab
* /usr/bin/systemctl enable sssd.service
* /usr/bin/systemctl restart sssd.service
* /usr/bin/sh -c /usr/bin/authselect select sssd with-mkhomedir --force && /usr/bin/systemctl enable oddjobd.service && /usr/bin/systemctl start oddjobd.service
Backup stored at /var/lib/authselect/backups/2024-01-18-17-26-45.4eurqd
Profile "sssd" was selected.
The following nsswitch maps are overwritten by the profile:
- passwd
- group
- netgroup
- automount
- services
Make sure that SSSD service is configured and enabled. See SSSD documentation for more information.
-
with-mkhomedir is selected, make sure pam_oddjob_mkhomedir module
is present and oddjobd service is enabled and active-
systemctl enable --now oddjobd.service
-
Successfully enrolled machine in realm
[root@arccdb11 ~]#
-
that seems to work flawlessly
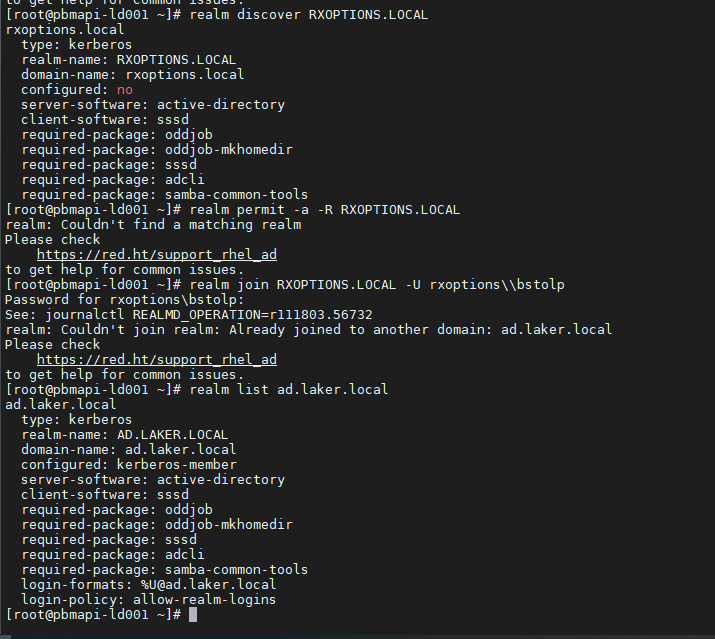
However when attempting to join second realm/domain
RXOPTIONS.LOCAL/rxoptions.local
[root@arccdb11 ~]# realm join -U RXOPTIONS\bstolp-a -v rxoptions.local
* Resolving: _ldap._tcp.rxoptions.local
* Performing LDAP DSE lookup on: 192.168.128.51
* Successfully discovered: rxoptions.local
Password for RXOPTIONS\bstolp-a:
realm: Couldn't join realm: Already joined to another domain: ad.laker.local
Please check
https://red.ht/support_rhel_ad
to get help for common issues.
[root@arccdb11 ~]#