Red Hat OpenStack Platform director (TripleO) CVE-2017-2637 bug and Red Hat OpenStack Platform
Environment
- Red Hat OpenStack Platform 11 is not affected.
- Red Hat OpenStack Platform 10 is affected.
- Red Hat OpenStack Platform 9 is affected.
- Red Hat OpenStack Platform 8 is affected.
- Red Hat OpenStack Platform 7 is affected.
Issue
A design flaw issue was found in the Red Hat OpenStack Platform director use of TripleO to enable libvirtd based live-migration. TripleO did not have support for secure live migration and no additional steps were taken to lock-down the libvirtd deployment by director. Libvirtd is deployed by default (by director) listening on 0.0.0.0 (all interfaces) with no-authentication or encryption. Anyone able to make a TCP connection to any compute host IP address, including 127.0.0.1, other loopback interface addresses or in some cases possibly addresses that have been exposed beyond the management interface, could use this to open a virsh session to the libvirtd instance and gain control of virtual machine instances or possibly take over the host.
Note: Without the presence of additional flaws, this should not be accessible from tenant or external networks.
Resolution
Red Hat OpenStack Platform 11
Red Hat OpenStack Platform 11 includes:
- puppet-tripleo-6.3.0-12.el7ost
- openstack-nova-15.0.3-3.el7ost
- puppet-nova-10.4.0-5.el7ost
- openstack-tripleo-common-6.0.0-8.el7ost
- openstack-tripleo-heat-templates-6.0.0-9.el7ost
- openstack-tripleo-puppet-elements-6.0.0-3.el7ost
These updated packages resolve this issue and were made available as of Red Hat OpenStack Platform 11 general availability (2017-05-18).
If using beta or release candidate builds of Red Hat OpenStack Platform please be reminded that these are not supported for usage in production environments. It is recommended that beta or release candidate installations now be re-deployed with the generally available release of Red Hat OpenStack Platform 11.
Red Hat OpenStack Platform 10
Red Hat OpenStack Platform 10 now includes these packages, which resolve this issue:
- openstack-nova-14.0.3-9.el7ost
- puppet-nova-9.5.0-4.el7ost
- openstack-tripleo-puppet-elements-5.2.0-3.el7ost
- puppet-tripleo-5.5.0-11.el7ost
- openstack-tripleo-heat-templates-5.2.0-12.el7ost
- openstack-tripleo-common-5.4.1-5.el7ost
These updates must be applied before upgrading to Red Hat OpenStack Platform 11. These updates were released as part of erratum RHSA-2017:1242.
To apply these updates you should follow the documentation for performing updates to minor versions in the Upgrading Red Hat Openstack Platform guide.
Composable Roles Impact
If you are using custom roles, the custom roles must be updated prior to applying the OSP10 minor update. Please see Red Hat Bugzilla # 1448157 for additional details.
Red Hat OpenStack Platform 9
Red Hat OpenStack Platform 9 now includes these packages, which resolve this issue:
- openstack-tripleo-heat-templates-2.0.0-57.el7ost
- openstack-tripleo-heat-templates-liberty-2.0.0-57.el7ost
- openstack-tripleo-puppet-elements-2.0.0-6.el7ost
- python-tripleoclient-2.0.0-14.el7ost
These updates must be applied before upgrading to Red Hat OpenStack Platform 10. These updates were released as part of erratum RHSA-2017:1504.
To apply these updates you should follow the documentation for performing updates to minor versions in the Upgrading Red Hat Openstack Platform guide.
Red Hat OpenStack Platform 8
Red Hat OpenStack Platform 8 now includes these packages, which resolve this issue:
- openstack-tripleo-heat-templates-0.8.14-29.el7ost
- openstack-tripleo-heat-templates-kilo-0.8.14-29.el7ost
- openstack-tripleo-puppet-elements-0.0.5-2.el7ost
- python-tripleoclient-0.3.4-14.el7ost
These updates must be applied before upgrading to Red Hat OpenStack Platform 9. These updates were released as part of erratum RHSA-2017:1546.
To apply these updates you should follow the documentation for performing updates to minor versions in the Upgrading Red Hat Openstack Platform guide.
Red Hat OpenStack Platform 7
Red Hat OpenStack Platform 7 now includes these packages, which resolve this issue:
- openstack-tripleo-heat-templates-0.8.6-135.el7ost
- openstack-tripleo-puppet-elements-0.0.1-6.el7ost
- python-rdomanager-oscplugin-0.0.10-34.el7ost
These updates must be applied before upgrading to Red Hat OpenStack Platform 8. These updates were released as part of erratum RHSA-2017:1537.
To apply these updates you should follow the documentation for performing updates to minor versions in the Director Installation and Usage guide.
Mitigation for Red Hat OpenStack Platform 7,8,9
Red Hat OpenStack Platform 7, 8, 9 now include fixes resolving this issue. Please follow the steps listed earlier in this article to locate and apply the update for the version of Red Hat OpenStack Platform that you are using.
As a short term mitigation, packages were previously provided that allow you to “opt-in” to a mitigation for the issue.
Deployment and Update Warning Text
For users running a director version that does not currently have the full secure fix, the following text will be displayed when running the overcloud deploy or update commands.
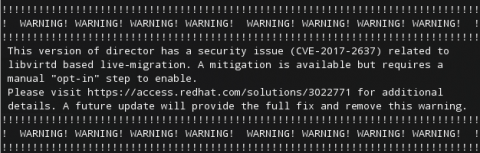
To remove this warning, follow the steps listed in this solution to apply the relevant updates for the version of Red Hat OpenStack Platform that you are using.
Root Cause
Official statement from Security Advisory CVE-2017-2637:
A design flaw issue was found in the Red Hat OpenStack Platform director use of TripleO to enable libvirtd based live-migration. Libvirtd is
deployed by default (by director) listening on 0.0.0.0 (all interfaces) with no-authentication or encryption. Anyone able to make a TCP connection to any compute host IP address, including 127.0.0.1, other loopback interface addresses, or in some cases possibly addresses that have been exposed beyond the management interface, could use this to open a virsh session to the libvirtd instance and gain control of virtual machine instances or possibly take over the host. (CVE-2017-2637)
For links to more detail, see the entry for CVE-2017-2637 in Red Hat's CVE Database.
Diagnostic Steps
Refer to the Resolution section of this document to find the instructions to apply a fix or mitigate the issue for the Red Hat OpenStack Platform release that you have installed.
This solution is part of Red Hat’s fast-track publication program, providing a huge library of solutions that Red Hat engineers have created while supporting our customers. To give you the knowledge you need the instant it becomes available, these articles may be presented in a raw and unedited form.


Comments