Chapter 20. Setting access control on the Directory Manager account
Having an unconstrained administrative user makes sense from a maintenance perspective. The Directory Manager requires a high level of access in order to perform maintenance tasks and to respond to incidents.
However, because of the power of the Directory Manager user, a certain level of access control can be advisable to prevent damages from attacks being performed as the administrative user.
20.1. About access controls on the Directory Manager account
Directory Server applies regular access control instructions only to the directory tree. The privileges of the Directory Manager account are hard-coded, and you cannot use this account in bind rules. To limit access to the Directory Manager account, use the RootDN Access Control plug-in.
This plug-in’s features are different from standard access control instructions (ACI). For example, certain information, such as the target (the Directory Manager entry) and the allowed permissions (all of them) is implied. The purpose of the RootDN Access Control plug-in is to provide a level of security by limiting who can log in as Directory Manager based on their location or time, not to restrict what this user can do.
For this reason, the settings of the plug-in only support:
- Time-based access controls, to allow or deny access on certain days and specific time ranges
- IP address rules, to allow or deny access from defined IP addresses, subnets, and domains
- Host access rules, to allow or deny access from specific hosts, domains, and subdomains
There is only one access control rule you can set for the Directory Manager. It is in the plug-in entry, and it applies to the entire directory.
Same as in regular ACIs, deny rules have a higher priority than allow rules.
Ensure that the Directory Manager account has an appropriate level of access. This administrative user might need to perform maintenance operations in off-hours or to respond to failures. In this case, setting a too restrictive time or day rule can prevent the Directory Manager user from adequately manage the directory.
20.2. Configuring the RootDN access control plug-in using the command line
By default, the RootDN Access Control plug-in is disabled. To limit permissions of the Directory Manager account, enable and configure the plug-in.
Procedure
Enable the
RootDN Access Controlplug-in:# dsconf -D "cn=Directory Manager" ldap://server.example.com plugin root-dn enableSet the bind rules. For example, to allow the Directory Manager account to only log in between 6am and 9pm from the host with IP address
192.0.2.1, enter:# dsconf -D "cn=Directory Manager" ldap://server.example.com plugin root-dn set --open-time=0600 --close-time=2100 --allow-ip="192.0.2.1"For the full list of parameters you can set and their descriptions, enter:
# dsconf -D "cn=Directory Manager" ldap://server.example.com plugin root-dn set --helpRestart the instance:
#
dsctl instance_name restart
Verification
Perform a query as
cn=Directory Managerfrom a host that is not allowed or outside of the allowed time range:[user@192.0.2.2]$ ldapsearch -D "cn=Directory Manager" -W -H ldap://server.example.com -x -b "dc=example,dc=com" Enter LDAP Password: ldap_bind: Server is unwilling to perform (53) additional info: RootDN access control violationIf Directory Server denies access, the plug-in works as expected.
20.3. Configuring the RootDN access control plug-in using the web console
By default, the RootDN Access Control plug-in is disabled. To limit permissions of the Directory Manager account, enable and configure the plug-in.
Prerequisites
- You are logged in to the instance in the web console.
Procedure
- Navigate to Plugins → RootDN Access Control.
- Enable the plug-in.
Fill the fields according to your requirements.
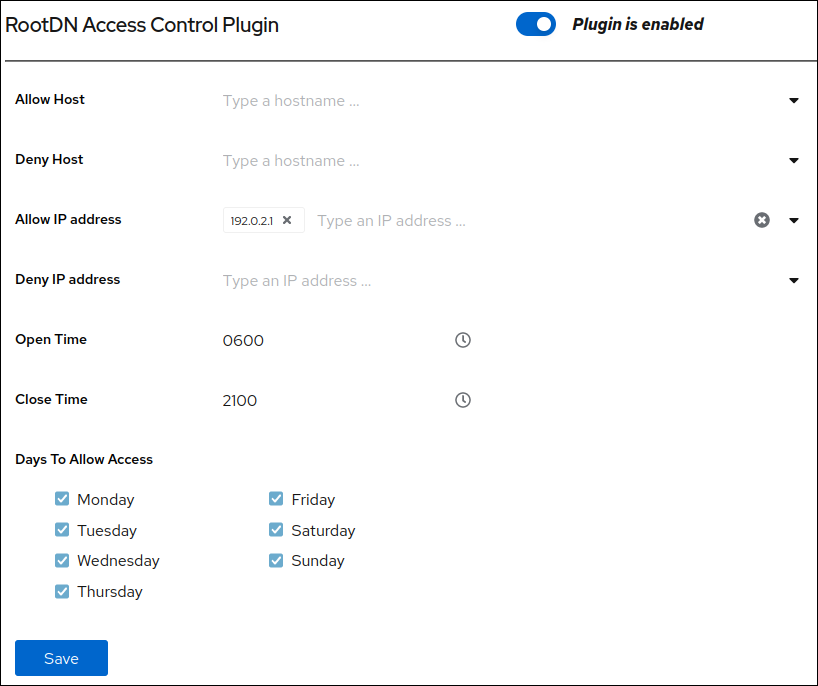
- Click Save.
-
Click Actions in the top right corner, and select
Restart Instance.
Verification
Perform a query as
cn=Directory Managerfrom a host that is not allowed or outside of the allowed time range:[user@192.0.2.2]$ ldapsearch -D "cn=Directory Manager" -W -H ldap://server.example.com -x -b "dc=example,dc=com" Enter LDAP Password: ldap_bind: Server is unwilling to perform (53) additional info: RootDN access control violationIf Directory Server denies access, the plug-in works as expected.

