Free access to proftpd service on WAN port
Regards
It is with great pleasure that I come here to inform you that I am studying RedHat-based system administration, but I am starting with CentOS-7.
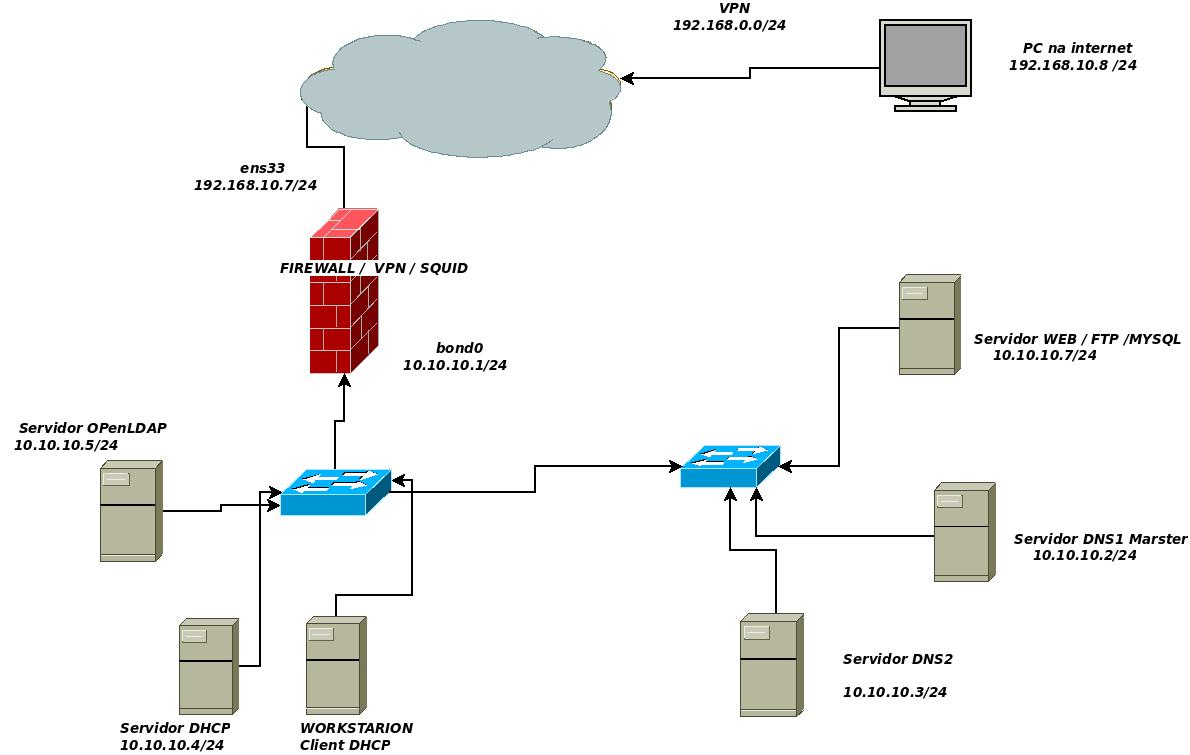
In a laboratory for study I created the infra as shown in the attached image, where all servers and firewall are CentOS.
I need to know how should I create a rule in Firewalld to allow external access to ftp service, I have a rule set to walk external access from port 21 to FTP server port, but by the time I access the browser web and access ftp://10.10.10.7 the web browser prompts me for the username and password, but even using the correct credentials I do not have the connection fully established.
A small note, I have access to the ftp service over the internal network without problems.
So I believe it is a rule that I should add to the firewall that manages my entire network.
Could you please help me with this task?
root@web ~]# cat /etc/proftpd.conf
ServerName " FTP do curso CentOS Server "
ServerType standalone
ServerAdmin root@empresa.com.br
AccessGrantMsg " O Usuário %u logou com sucesso "
UseReverseDNS off
DefaultAddress 10.10.10.7
Port 21
PassivePorts 5000 61000
User ftp
Group ftp
MaxInstances 20
MultilineRFC2228 on
ShowSymlinks off
UseIPv6 off
DefaultTransferMode binary
WtmpLog off
TransferLog /var/log/proftpd/xferlog
SystemLog /var/log/proftpd/proftpd.log
RootLogin off
AuthPAM on
DefaultRoot /home/ftp
Below is the ftp server firewall configuration
[root@web ~]# firewall-cmd --zone=public --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: ens32
sources:
services: ftp http dhcpv6-client ssh https mysql
ports: 22/tcp 21/tcp
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
[root@web ~]#
2: ens32: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:32:8b:e3 brd ff:ff:ff:ff:ff:ff
inet 10.10.10.7/24 brd 10.10.10.255 scope global noprefixroute ens32
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe32:8be3/64 scope link
valid_lft forever preferred_lft forever
[root@web ~]#
Below is the firewall configuration, dedicated server only for firewall where I think I should have to create some more rules.
I am working with only two zones the external for the "interfaces: ens33" WAN and the internal for the LAN "interfaces: bond0 ens34 ens35"
[root@firewall ~]# firewall-cmd --zone=internal --list-all
internal (active)
target: DROP
icmp-block-inversion: no
interfaces: bond0 ens34 ens35
sources:
services: ssh mdns samba-client dhcpv6-client
ports: 3128/tcp 3128/udp
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
[root@firewall ~]# firewall-cmd --zone=external --list-all
external (active)
target: default
icmp-block-inversion: no
interfaces: ens33
sources:
services: ssh openvpn
ports:
protocols:
masquerade: yes
forward-ports: port=80:proto=tcp:toport=80:toaddr=10.10.10.7
port=2222:proto=tcp:toport=22:toaddr=10.10.10.7
port=2220:proto=tcp:toport=22:toaddr=10.10.10.2
port=2221:proto=tcp:toport=22:toaddr=10.10.10.3
port=2223:proto=tcp:toport=22:toaddr=10.10.10.4
port=2224:proto=tcp:toport=22:toaddr=10.10.10.5
port=2228:proto=tcp:toport=22:toaddr=10.10.10.8
port=9090:proto=tcp:toport=9090:toaddr=10.10.10.8
port=21:proto=tcp:toport=21:toaddr=10.10.10.7
source-ports:
icmp-blocks:
rich rules:
[root@firewall ~]#
----------------------------------------------------------------------------------------------