The dynamic Kerberos PAC ticket signature enforcement mechanism fixes cross-version incompatibility in IdM
Summary
If your Identity Management (IdM) environment has IdM servers running on both RHEL 8 and RHEL 9, specifically RHEL 9.2 or earlier, an incompatibility due to the upstream implementation of the MS-PAC ticket signature support may cause certain operations to fail. However, in RHEL 9.2.z and RHEL 9.3, the implementation of the dynamic ticket signature enforcement mechanism feature fixes this cross-version incompatibility between RHEL 8 and RHEL 9 IdM servers.
Details
Over the past years, Microsoft introduced two new types of Privilege Attribute Certificate (PAC) signatures, or "checksums" in MIT Kerberos terminology:
- Ticket signature
- Released in KB4598347
- Meant to fix CVE-2020-17049, also known as the "Bronze-Bit" attack
- Extended KDC signature
- Released in KB5020805
- Meant to fix CVE-2022-37967
Support for both these signatures was implemented in upstream MIT Kerberos and backported to RHEL 9. But on RHEL 8, only the PAC extended KDC signature could be supported because of application binary interface (ABI) stability constraints.
| RHEL version | Signature type | Bugzilla bug | Advisory | Package version |
|---|---|---|---|---|
| RHEL 9 | Ticket signature, extended KDC signature | BZ#2165827 | RHSA-2023:2570 | krb5-1.20.1-6.el9 |
| RHEL 8 | Extended KDC signature | BZ#2211390 | RHEA-2023:3850 | krb5-1.18.2-25.el8_8 |
| RHEL 8.8 | Extended KDC signature | BZ#2211387 | RHEA-2023:3831 | ipa-4.9.11-6.el8_8 |
| RHEL 8.9+ | Extended KDC signature | BZ#2176406 | RHBA-2023:6977 | ipa-4.9.12-8.el8 |
In case of a gradual migration environment, that is a domain with IdM servers running on both RHEL 9 and RHEL 8, an incompatibility due to the upstream implementation of the PAC ticket signature support may cause certain operations to fail. This cross-versions incompatibility has been fixed with the introduction of the dynamic ticket signature enforcement mechanism in the following updates:
| RHEL version | Bugzilla bug | Advisory | Package version |
|---|---|---|---|
| RHEL 9.2 | BZ#2211388 | RHBA-2023:3731 | krb5-1.20.1-9.el9_2 |
| RHEL 9.3+ | BZ#2178298 | RHSA-2023:6699 | krb5-1.21.1-1.el9 |
| RHEL 9.2 | BZ#2211389 | RHBA-2023:3719 | ipa-4.10.1-7.el9_2 |
| RHEL 9.3+ | BZ#2182683 | RHBA-2023:6477 | ipa-4.10.2-4.el9 |
For the dynamic ticket signature enforcement mechanism to actually take effect, you must:
- Update all the servers in the domain.
- Restart all the IdM Kerberos Distribution Center (KDC) services.
The order of these two actions is important. When starting, the KDCs query the metadata of all the other servers in the domain to check if they all support the PAC ticket signature. If this is not the case, the signature will not be enforced.
Below is an image portraying a constrained delegation request in a gradual upgrade environment without the fix described above:
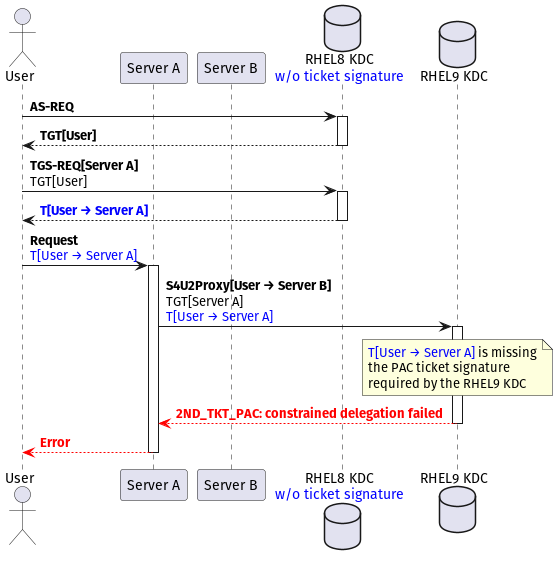 |
|---|
| Missing PAC ticket signature in a constrained delegation request |
Compare this to a setup where this fix is deployed:
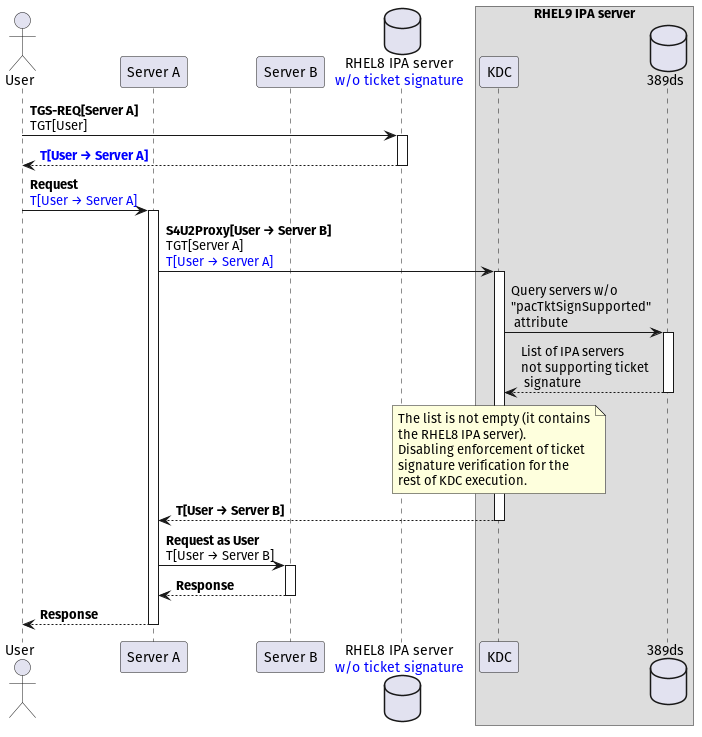 |
|---|
| Dynamic PAC ticket signature enforcement for a constrained delegation request |


Comments