-
Language:
English
-
Language:
English
6.2.3 Release Notes
JBoss Enterprise Application Platform 6.2
For Use with Red Hat JBoss Enterprise Application Platform 6.2
Nidhi Chaudhary
Lucas Costi
Russell Dickenson
Sande Gilda
Vikram Goyal
Eamon Logue
Darrin Mison
Scott Mumford
David Ryan
Misty Stanley-Jones
Keerat Verma
Tom Wells
Abstract
These release notes contain important information related to Red Hat JBoss Enterprise Application Platform 6.2.3. Read these Release Notes in their entirety before installing the product.
1. About Maintenance Releases
In order to better meet customer expectations, micro releases for JBoss EAP 6 have been discontinued upon the 6.2 release and replaced with patch updates delivered on a repeating schedule, targeting a new release every 6 weeks. The patch updates will be delivered for both ZIP and RPM based installations of JBoss EAP.
- For installations originating from a ZIP file, a Cumulative Patch managed by a new EAP feature for applying patches, removing patches, and viewing patch state will be delivered.
- For installations originating from RPMs, updated RPMs containing the identical fixes included in the Cumulative Patch will be delivered through Red Hat Network on the same repeating schedule.
Each new patch update will contain a number of bug fixes for customer reported issues and potentially a number of security fixes. We expect that the patch updates will substantially reduce the number of individual patches that we produce and that customers must manage to keep their installations up to date.
For more information see the following Red Hat Knowledgebase articles: Maintenance Release Changes in EAP 6.2+ (https://access.redhat.com/site/articles/547663) and Updated Patch Management with EAP 6.2+ (https://access.redhat.com/site/articles/547673).
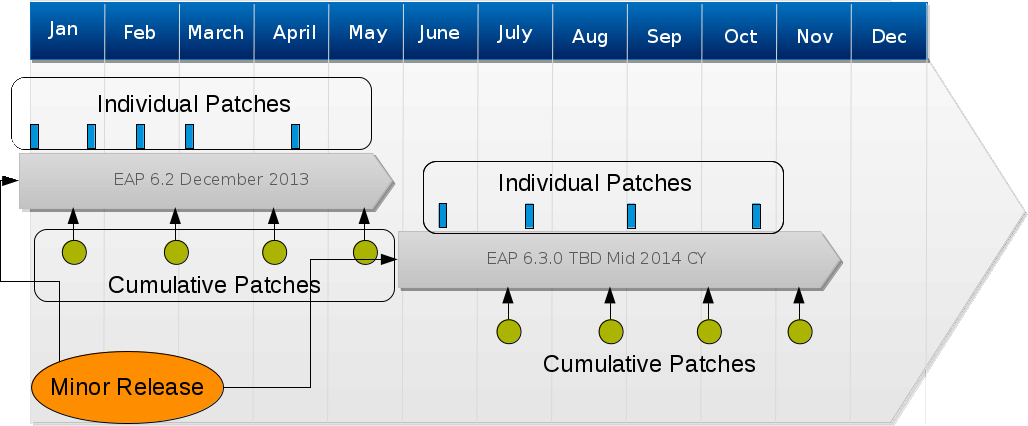
Figure 1. JBoss EAP Patching Schedule
2. Apply a Patch Update
The method of applying a patch update varies according to the installation method used to install JBoss EAP. See Patching and Upgrading JBoss EAP in the Installation Guide for further details.
For information about how to apply an incremental patch to a local Maven repository, see Apply a Patch to the Local Maven Repository in the Development Guide for JBoss EAP.
3. Security Advisories
- Zip
- JBoss Watch List archives - https://www.redhat.com/archives/jboss-watch-list/
- RPMs/Red Hat Enterprise Linux
- JBoss Enterprise Application Platform 6 EL5 Security Advisories - https://rhn.redhat.com/errata/rhel5-jbeap-6-errata-security.htmlJBoss Enterprise Application Platform 6 EL6 Security Advisories - https://rhn.redhat.com/errata/rhel6-jbeap-6-errata-security.html
4. Changes in this release
4.1. Bug Fixes
CDI/Weld
- 1088791 - Timed out conversation unexpectedly alive on next request
- In a JSF application, a conversation was unexpectedly activated and associated with a request even after the conversation had expired, resulting in a NonExistentConversationException error. The root cause of this issue was that Weld did not properly check the state of conversation when initiating requests. To resolve this issue the conversation context activation and invalidation procedure has been amended to check conversation state more thoroughly. As a result, expired conversations are no longer mistakenly associated with requests.
Domain Management
- 1075082 - management authorization throws an exception when an LDAP group contains a slash character
- Cause : Previous versions of JBoss EAP were found to contain a bug that prevented the backslash (/) character from being escaped correctly when it was used in an LDAP group on a Windows Active Directory LDAP server. Consequence : The bug would cause EAP management authorization to throw a NamingException. Fix : This release included an update that ensures the character is escaped correctly and the exception no longer presents.
- 1089616 - High CPU usage by JMX monitoring client, RBAC seems the hotspot
- A performance issue affecting JMX Query was identified, where the CPU load was much higher than expected in previous JBoss EAP releases. The cause of the issue was that role-based access control (RBAC) was checking the address of every query, regardless of whether that address was relevant to JMX Query. To resolve this issue the processing of querie was changed to first check if the address is relevant to JMX Query and if not, avoid the processing involved. The result of this change is that CPU load of JMX monitoring is again at a normal level.
- 1082478 - Can't promote --backup slave HC to master and reload without moving domain.cached-remote.xml
- Consequence : A bug prevents a slave Host Controller that has been reconfigured to act as Master from loading the cached domain configuration upon restart.Cause: The newly promoted Master loads the configuration from the domain/configuration/domain.xml instead of the domain/configuration/domain.cached-remote.xml file.If a domain.xml file exists, its content will be used for the domain wide config, even though that content may be out of date. If a domain.xml file does not exist, restarting the Host Controller will fail with a
FileNotFoundException.Fix: If a slave HostController started with --backup is reconfigured to act as master and is then reloaded to pick up that change, the domain.cached-remote.xml file it was maintaining when running as a backup will automatically be detected and used. - 1072949 - slaves cannot reconnect to a restarted master if RBAC is enabled
EJB
- 1084872 - ArrayIndexOutOfBoundsException during periodic recovery on EJBTransactionRecoveryService
- An intermittent issue between the periodic recovery and EJBTransactionRecoveryService resulted in an ArrayIndexOutOfBoundsException.
[com.arjuna.ats.jta] (Periodic Recovery) ARJUNA016009: Caught:: java.lang.ArrayIndexOutOfBoundsException: 0 at org.jboss.as.ejb3.remote.EJBTransactionRecoveryService.getXAResources(EJBTransactionRecoveryService.java:112) ....
The root cause of the issue was that the creation of an XAResource element was not contained within the associated logic loop and this led to the array index error. This element has now been moved so that it is within the logic loop and so the periodic recovery no longer conflicts with the EJBTransactionRecoveryService. - 1082880 - Cannot get exception as pass-by-reference
- A bug that prevented servlets from getting EJB exceptions as a pass-by reference even it was configured to do so has been corrected in this release.
Hibernate
- 1073082 - HHH-8983 Database drivers may attach warnings to statement handles and these may accumulate and consume significant memory
- When using
java.sql.Timestamptypes against a Sybasedatetimetype, Sybase attaches warning objects to the statement handles used byinsert,update, andquery. In situations where inserts or updates are batched, the accumulation of the warning objects can be significant, and if these statements remained cached, the memory usage can grow significantly. This issue was fixed modifying the JDBC coordinator implementation to log and clear the warnings so they are not retained in memory. - 1085976 - NPE while query.list on a Native SQL, using cache
- Cause : An NPE error is thrown when executing a native SQL query in Hibernate with level 1 and/or 2 cache enabled.Fix :The issue is fixed by correcting the Loader returnTypes.
- 1073118 - HHH-3482: UnsupportedOperationException with StatelessSession
- Instances of an
UnsupportedOperationErrorerror message being thrown when using StatelessSession and saving a ManyToOne have been addressed in this release of JBoss EAP 6. The error was caused by a call togetTimestamp()method which was not implemented for StatelessSession. This method has since been implemented and as a result, theUnsupportedOperationErrorerror message no longer occurs.
HornetQ
- 1088606 - All methods in ClientSessionImpl which implement XAResource can potentially throw a non-XAException to the TM
- If an XA transaction involving HornetQ timed out, it was possible that HornetQ might throw a
non-XAExceptionto the Transaction Manager. The implementation ofjavax.transaction.xa.XAResourcein HornetQ was modified to eliminate this possibility. - 1088599 - ClientConsumer max rate not taking effect if ServerLocator's consumerMaxRate <=0
- The Core API method
createConsumer(String queueName, String filter, int windowSize, int maxRate, boolean browseOnly)ignored the parametermaxRateif the ConnectionFactory (or ServerLocator) had setmaxRateto its default value. This issue has been fixed in this release of JBoss EAP 6, and thecreateConsumermethod now correctly uses themaxRateparameter even if it is set to its default value. - 1088604 - Policy Fail may drop messages before it sends the exception to the client
- Consequence : The "FAIL" address-full-policy might drop messages and not send an exception to the client. Fix : This was resolved so that blocking sends always result in an exception on the client when the address is full and non-blocking sends will result in an exception on the client when additional credits are requested from the server.
- 1088603 - Spurious WARN messages after XmlDataImporter deletes temp file
- When the
XmlDataImporterwas importing large messages, spurious WARN messages were logged. The root cause of this issue was that when importing sufficiently large messages, theXmlDataImportercreated a temporary file and deleted it when the import task was complete. When importing another large message, theXmlDataImporterfunction tried to delete the temporary file, which no longer existed, and so logged the WARN message. The handling of temporary files in theXmlDataImporterfunction has now been modified and as a result, spurious WARN messages are no longer logged. - 1088602 - listMessagesAsJSON method fails to list messages if the filter property contians \n character.
- Filter parsing would fail if you used
\ninside a String or any other property. We fixed it accordingly to accept\non the filter property. - 1088601 - Fix order of totalIterator()
- Any management operations that listed messages would incorrectly list paged messages before previously sent messages. Other possible out of order issues were also identified in cases after redeliveries. This issue was fixed by rectifying the order where the Iterator takes messages before sending them to management operations.
- 1088600 - Full scheduledReferences traversal in every call to ScheduledDeliveryHandlerImpl$ScheduledDeliveryRunnable.run()
- HornetQ would consume a lot of CPU if lots of messages were scheduled with a small interval between each message because it would transverse the whole list of messages at every scheduled time.
- 1088609 - Implement sync of counters for non transactional sends
- When sending non-TX messages persistently, the page counter could get out of sync between paged messages and what was stored on the journal, and this could had led to negative delivering numbers. In this release, extra checks were added to guarantee the page counter is synced properly.
- 1088617 - Avoiding possible NPE during the depage process
- A NullPointerException (NPE) was possible during message delivery and paging process. In this release of JBoss EAP 6, checks were added in order to avoid NPEs during message delivery and paging.
- 1087632 - Change initial connection behavior for cluster connection
- Consequence : HornetQ could get in an infinite loop when trying to connect to a cluster node if it was disconnected during its initial connection attempt.Cause :This could be an issue in two cases: Using a static cluster configuration, any initial connect attempt would be done infinitely ignoring the number of retries parameter.Using a dynamic cluster configuration, if the node was disconnected between the time it received a notification about the node being part of the cluster topology and the initial connection.In any of these cases an infinite loop trying to connect would be in place wasting CPU resources.Fix: Cluster connection bridge should use the "reconnect-attempts" value for both the initial connection attempts and reconnection attempts.Result: HornetQ infinite loop avoided.
- 1088616 - Messages always acked individually after certain reconnection scenarios
- The client consumer would always ack messages individually in certain scenarios, for example after failures. This process was very inefficient. In this release of JBoss EAP 6, optimizations were added to the client consumer implementation to address this inefficiency.
IIOP
- 1072747 - StackOverflowError when org.jboss.as.jacorb.rmi.InterfaceAnalysis is analyzing javax.ejb.EJBObject
- In previous versions of JBoss EAP 6, it was found that, depending on the timing of a thread context switch, IIOP-enabled EJBs could fail to deploy correctly, causing a StackOverflowError.This issue was traced to improper thread synchronization in org.jboss.as.jacorb.rmi.WorkCacheManager.The issue has been corrected in this release and the StackOverflowError no longer presents.
Logging
- 1070453 - System.out.println() doesn't work when using per-deployment logging
- In previous versions of JBoss EAP 6, a bug prevented the System.out.println() method from printing to the console, server.log, or test.log files when per-deployment logging was in use.This bug was resolved with an upstream patch.
- 1087630 - Cache string representation of throwable info
- The stack trace information was not guaranteed to be stored correctly. As a result, data could be lost upon serialization of Log4J logging events.To fix this, Log4J has been amended to cache the stack trace (i.e. throwable information) upon deserialization. This ensures that stack trace information will not be lost upon serialization.
Other
- 1078665 - Cleanup deploy directories
- In previous versions of JBoss EAP 6, the temporary deployment directory ( /tmp/vfs), created while the server was running, would remain if the server stopped unexpectedly or was forcibly stopped. The directory and its contents would not be removed on a later startup. This could have serious consequences as accumulated temporary files could eventually use all available disk space. The root cause of this issue has now been resolved by adding a test on startup for temporary files. If /tmp/vfs is found, the directory and its contents are removed and as a result, temporary files can no longer accumulate.
PicketLink
- 1084600 - Backport PLINK-396
- In previous verions of JBoss Enterprise Application Platform 6, it was found that PicketLink’s
IDPWebBrowserSSOValveandIDPFilterwere decoding the relaystate, which was contrary to the SAML specification. This has been addressed in this release of the product.
RESTEasy
- 1063653 - Chosen variant is not always the best match
- In previous versions of JBoss EAP 6, it was found that RESTEasy, while adhering to specification RFC 2616, did not always return the most appropriate media handler in instances where specificity and quality factors were equal.For instance, when given an Accept header of
application/json,*/*and variant values of["application/xml","application/json"], RESTEasy’sRequest.selectVariant()would chooseapplication/xmloverapplication/json.
Security
- 1069886 - SecureIdentityLoginModule (and ConfiguredIdentityLoginModule) results are not cached by the JAAS cache
- Cause: The JAAS cache did not cache the login information when the principal was null.Consequence: If an application was not secured and used a datasource that was configured to use the
SecureIdentityLoginModule, the principal comes into JAAS cache as a null. As a result, nothing was cached. This meant that each time the application used the datasource, a call to the login-module was triggered.Fix: Modify the JAAS cache logic to cache the login info when the principal is null.Result: The login module is not called each time the datasource is used. - 1085504 - The NegotiationAuthenticator loses post data
- When using negotiation with PicketLink, if the Service Provider (SP) was using HTTP-POST binding, then the
NegotiationAuthenticatorwould lose the SAMLRequest post parameter. This meant that after a user was successfully authenticated, the Identity Provider (IDP) would not know to where to redirect the user. As a result, the user would be left at the IDP index page.This issue was fixed by altering theNegotiationAuthenticatorto check if there was a re-submission of the original request URI, and if so, would forward the original request instead. As a result, using HTTP-POST binding when using negotiation should redirect the user successfully after authentication. - 1085503 - JBoss Negotiation should fallback to form authentication instead of returning 401
- Cause: Invalid entry in KDC returns 401 instead of form.Consequence: JBoss negotiation returns 401 on fallback.Fix: Code updated to capture invalid entries and return a form.
- 1085506 - Upgrade negotiation from 2.2.7 to 2.2.8
Server
- 1076507 - Usage of vault for system-properties throws java.lang.SecurityException
- Previous versions of JBoss EAP 6 could fail to start if a system property was used that contained a vault expression in its value attribute.This was because the system property resources in the XML configuration were processed before the security vault resources. This meant that the security vault was not available as a source for resolving expressions. Any resources using a vault attribute would result in the following error:
java.lang.SecurityException: JBAS013322: Vault is not initialized
In this release, if a system property value expression fails to resolve, a second attempt is made later in the boot process at a point after the vault (if one is configured) is installed. This resolves the issue and systems using vault expressions now boot as expected.
Web
- 1036977 - JBoss EAP 6.x/JBOSSWEB_7.2.x APR connector does not allow adding system property org.apache.tomcat.util.ENABLE_MODELER=true
- When enabled, the system property
org.apache.tomcat.util.ENABLE_MODELERwas causing an error that prevented JBoss Enterprise Application Platform 6 from booting. This was because the name of the connector was not consistent with JMX naming requirements. The name of the connector has been changed, and the property now performs as expected.
Web Services
- 1079085 - Webservices DUP is not scanning all visible classes for @WebService annotation
- It was discovered that the Webservices DUP in previous versions of JBoss EAP 6 carried a bug that prevented it from scanning all visible classes with the
@WebServiceannotation. The error presented when a war archive that contained a web.xml with a <servlet-class> that refers to a JAX-WS endpoint (so the class is annotated with@WebService) was located within an ear archive and the jar containing the class was located in the ear archive’s lib/ directory. The relevant code has been amended in this release to scan more thoroughly for@WebServiceclasses and the error no longer presents.
4.2. Enhancements
JSF
- 1087781 - Upgrade to Mojarra 2.1.28 (from 2.1.27)
- In this release of JBoss EAP 6, the JSF component has been upgraded from 2.1.27 to the latest upstream bugfix version; 2.1.28.
PicketLink
- 1084595 - Backport PLINK-313
- A new feature has been introduced into the PicketLink component in this version of JBoss EAP 6. In this release IDP is now configurable to sign assertions.
- 1085539 - Backport PLINK-407
- An update to this release of JBoss EAP 6 introduces an upstream PicketLink feature that allows the
FormAuthenticatorcharacterEncodingparameter to be used for requests inIDPWebBrowserSSOValve. - 1084597 - Backport PLINK-405
- A new feature has been incorporated into the PicketLink component of this version of JBoss EAP 6. In this release the the principal that gets sent to the AttributeManager has been made configurable.When using PicketLink with JBoss Negotiation, the principal that is sent to the AttributeManager is a hashed string and not the username. This can result failed lookups if the mapping provider uses the principal to look up any attributes.The ability to configure the principle ameliorates this issue.
- 1084587 - Backport PLINK-146
- A new feature has been introduced into the PicketLink component in this version of JBoss EAP 6. The
XMLSignatureUtilcan now allow KeyInfo to use X509 if desired.
4.3. Known Issues
Hibernate
- 1094756 - HHH-9170 HHH-9174 ORM Performance regression
- A regression that can cause performance degradation is present in this release of JBoss EAP 6. It has been traced to the
Statement.getWarnings()method (which was negatively impacted by changes made to resolve an earlier memory leak caused by a bug in the Sybase JDBC drivers).To address the performance issues, new code has been added to check the log level of warnings and ignore any messages below WARN level. These messages are cleared and not written to theserver.logfile. While this measure mitigates much of the performance degradation, the issue may still present to varying degrees, depending on the JDBC implementation being used.To avoid the performance issue completely, users can raise this threshold by setting theorg.hibernatelogging category to ERROR. Care should be taken before making this change, however, as ignoring warnings below the ERROR level can obfuscate possible problems in the database.
Patching
- 1065830 - patch conflict with pure EAP 6.2 installed using the jar installer
- If you used the JAR installer to install JBoss EAP, you may encounter conflicts when applying a cumulative patch. Due to differences in some files included with the JAR installer distribution, the patch tool can mistakenly identify these differences as user modifications.See Applying Cumulative Patches to Installer Installations for information about how to resolve these conflicts. This issue is expected to be fixed in a future release.
Scripts and Commands
- 1072227 - Wrong handling of --debug argument by standalone.[sh|bat] scripts
- This release of JBoss EAP 6 carries a bug where-in the shell script for running EAP in standalone mode (standalone.sh|bat) does not use the default port (port 8787) when the script is used with "debug" argument without a port number.As a result execution of the script (standalone.sh|bat) with "debug" argument results in an error and does not start the server.A possible workaround for this issue is to specify a port number when the script (standalone.sh|bat) is used with "debug" argument:standalone.[sh|bat] --debug [port number]This issue is expected to be resolved in a future release of the product.
A. Revision History
| Revision History | |||
|---|---|---|---|
| Revision 6.2.3-16 | Tuesday May 27 2014 | Tom Wells | |
| |||
Legal Notice
Copyright © 2014 Red Hat, Inc..
This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed.
Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law.
Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries.
Linux® is the registered trademark of Linus Torvalds in the United States and other countries.
Java® is a registered trademark of Oracle and/or its affiliates.
XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries.
MySQL® is a registered trademark of MySQL AB in the United States, the European Union and other countries.
Node.js® is an official trademark of Joyent. Red Hat Software Collections is not formally related to or endorsed by the official Joyent Node.js open source or commercial project.
The OpenStack® Word Mark and OpenStack logo are either registered trademarks/service marks or trademarks/service marks of the OpenStack Foundation, in the United States and other countries and are used with the OpenStack Foundation's permission. We are not affiliated with, endorsed or sponsored by the OpenStack Foundation, or the OpenStack community.
All other trademarks are the property of their respective owners.

