Red Hat Training
A Red Hat training course is available for RHEL 8
Chapter 43. Adding host entries from IdM Web UI
This chapter introduces hosts in Identity Management (IdM) and the operation of adding a host entry in the IdM Web UI.
43.1. Hosts in IdM
Identity Management (IdM) manages these identities:
- Users
- Services
- Hosts
A host represents a machine. As an IdM identity, a host has an entry in the IdM LDAP, that is the 389 Directory Server instance of the IdM server.
The host entry in IdM LDAP is used to establish relationships between other hosts and even services within the domain. These relationships are part of delegating authorization and control to hosts within the domain. Any host can be used in host-based access control (HBAC) rules.
IdM domain establishes a commonality between machines, with common identity information, common policies, and shared services. Any machine that belongs to a domain functions as a client of the domain, which means it uses the services that the domain provides. IdM domain provides three main services specifically for machines:
- DNS
- Kerberos
- Certificate management
Hosts in IdM are closely connected with the services running on them:
- Service entries are associated with a host.
- A host stores both the host and the service Kerberos principals.
43.2. Host enrollment
This section describes enrolling hosts as IdM clients and what happens during and after the enrollment. The section compares the enrollment of IdM hosts and IdM users. The section also outlines alternative types of authentication available to hosts.
Enrolling a host consists of:
-
Creating a host entry in IdM LDAP: possibly using the
ipa host-addcommand in IdM CLI, or the equivalent IdM Web UI operation. - Configuring IdM services on the host, for example the System Security Services Daemon (SSSD), Kerberos, and certmonger, and joining the host to the IdM domain.
The two actions can be performed separately or together.
If performed separately, they allow for dividing the two tasks between two users with different levels of privilege. This is useful for bulk deployments.
The ipa-client-install command can perform the two actions together. The command creates a host entry in IdM LDAP if that entry does not exist yet, and configures both the Kerberos and SSSD services for the host. The command brings the host within the IdM domain and allows it to identify the IdM server it will connect to. If the host belongs to a DNS zone managed by IdM, ipa-client-install adds DNS records for the host too. The command must be run on the client.
43.3. User privileges required for host enrollment
The host enrollment operation requires authentication to prevent an unprivileged user from adding unwanted machines to the IdM domain. The privileges required depend on several factors, for example:
-
If a host entry is created separately from running
ipa-client-install - If a one-time password (OTP) is used for enrollment
User privileges for optionally manually creating a host entry in IdM LDAP
The user privilege required for creating a host entry in IdM LDAP using the ipa host-add CLI command or the IdM Web UI is Host Administrators. The Host Administrators privilege can be obtained through the IT Specialist role.
User privileges for joining the client to the IdM domain
Hosts are configured as IdM clients during the execution of the ipa-client-install command. The level of credentials required for executing the ipa-client-install command depends on which of the following enrolling scenarios you find yourself in:
-
The host entry in IdM LDAP does not exist. For this scenario, you need a full administrator’s credentials or the
Host Administratorsrole. A full administrator is a member of theadminsgroup. TheHost Administratorsrole provides privileges to add hosts and enroll hosts. For details about this scenario, see Installing a client using user credentials: interactive installation. -
The host entry in IdM LDAP exists. For this scenario, you need a limited administrator’s credentials to execute
ipa-client-installsuccessfully. The limited administrator in this case has theEnrollment Administratorrole, which provides theHost Enrollmentprivilege. For details, Installing a client using user credentials: interactive installation. -
The host entry in IdM LDAP exists, and an OTP has been generated for the host by a full or limited administrator. For this scenario, you can install an IdM client as an ordinary user if you run the
ipa-client-installcommand with the--passwordoption, supplying the correct OTP. For details, see Installing a client by using a one-time password: Interactive installation.
After enrollment, IdM hosts authenticate every new session to be able to access IdM resources. Machine authentication is required for the IdM server to trust the machine and to accept IdM connections from the client software installed on that machine. After authenticating the client, the IdM server can respond to its requests.
43.4. Enrollment and authentication of IdM hosts and users: comparison
There are many similarities between users and hosts in IdM, some of which can be observed during the enrollment stage as well as those that concern authentication during the deployment stage.
The enrollment stage (User and host enrollment):
-
An administrator can create an LDAP entry for both a user and a host before the user or host actually join IdM: for the stage user, the command is
ipa stageuser-add; for the host, the command isipa host-add. -
A file containing a key table or, abbreviated, keytab, a symmetric key resembling to some extent a user password, is created during the execution of the
ipa-client-installcommand on the host, resulting in the host joining the IdM realm. Analogically, a user is asked to create a password when they activate their account, therefore joining the IdM realm. - While the user password is the default authentication method for a user, the keytab is the default authentication method for a host. The keytab is stored in a file on the host.
Table 43.1. User and host enrollment
Action User Host Pre-enrollment
$ ipa stageuser-add user_name [--password]
$ ipa host-add host_name [--random]
Activating the account
$ ipa stageuser-activate user_name
$ ipa-client install [--password] (must be run on the host itself)
-
An administrator can create an LDAP entry for both a user and a host before the user or host actually join IdM: for the stage user, the command is
The deployment stage (User and host session authentication):
- When a user starts a new session, the user authenticates using a password; similarly, every time it is switched on, the host authenticates by presenting its keytab file. The System Security Services Daemon (SSSD) manages this process in the background.
- If the authentication is successful, the user or host obtains a Kerberos ticket granting ticket (TGT).
- The TGT is then used to obtain specific tickets for specific services.
Table 43.2. User and host session authentication
User Host Default means of authentication
Password
Keytabs
Starting a session (ordinary user)
$ kinit user_name
[switch on the host]
The result of successful authentication
TGT to be used to obtain access to specific services
TGT to be used to obtain access to specific services
TGTs and other Kerberos tickets are generated as part of the Kerberos services and policies defined by the server. The initial granting of a Kerberos ticket, the renewing of the Kerberos credentials, and even the destroying of the Kerberos session are all handled automatically by the IdM services.
Alternative authentication options for IdM hosts
Apart from keytabs, IdM supports two other types of machine authentication:
- SSH keys. The SSH public key for the host is created and uploaded to the host entry. From there, the System Security Services Daemon (SSSD) uses IdM as an identity provider and can work in conjunction with OpenSSH and other services to reference the public keys located centrally in IdM.
- Machine certificates. In this case, the machine uses an SSL certificate that is issued by the IdM server’s certificate authority and then stored in IdM’s Directory Server. The certificate is then sent to the machine to present when it authenticates to the server. On the client, certificates are managed by a service called certmonger.
43.5. Host entry in IdM LDAP
An Identity Management (IdM) host entry contains information about the host and what attributes it can contain.
An LDAP host entry contains all relevant information about the client within IdM:
- Service entries associated with the host
- The host and service principal
- Access control rules
- Machine information, such as its physical location and operating system
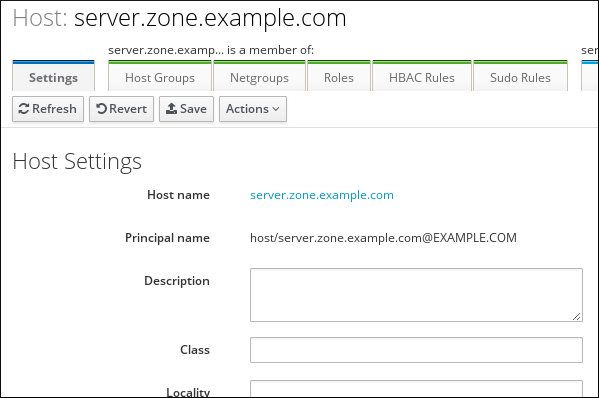
Note that the IdM Web UI Identity → Hosts tab does not show all the information about a particular host stored in the IdM LDAP.
Host entry configuration properties
A host entry can contain information about the host that is outside its system configuration, such as its physical location, MAC address, keys, and certificates.
This information can be set when the host entry is created if it is created manually. Alternatively, most of this information can be added to the host entry after the host is enrolled in the domain.
Table 43.3. Host Configuration Properties
| UI Field | Command-Line Option | Description |
|---|---|---|
| Description |
| A description of the host. |
| Locality |
| The geographic location of the host. |
| Location |
| The physical location of the host, such as its data center rack. |
| Platform |
| The host hardware or architecture. |
| Operating system |
| The operating system and version for the host. |
| MAC address |
|
The MAC address for the host. This is a multi-valued attribute. The MAC address is used by the NIS plug-in to create a NIS |
| SSH public keys |
| The full SSH public key for the host. This is a multi-valued attribute, so multiple keys can be set. |
| Principal name (not editable) |
|
The Kerberos principal name for the host. This defaults to the host name during the client installation, unless a different principal is explicitly set in the |
| Set One-Time Password |
| This option sets a password for the host which can be used in bulk enrollment. |
| - |
| This option generates a random password to be used in bulk enrollment. |
| - |
| A certificate blob for the host. |
| - |
| This sets whether the host can dynamically update its DNS entries if its IP address changes. |
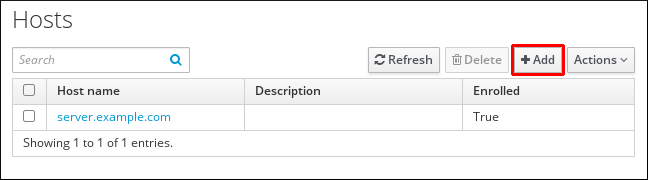
43.6. Adding host entries from the Web UI
-
Open the
Identitytab, and select theHostssubtab. Click Add at the top of the hosts list.
Figure 43.1. Adding Host Entries
Enter the machine name and select the domain from the configured zones in the drop-down list. If the host has already been assigned a static IP address, then include that with the host entry so that the DNS entry is fully created.
The
Classfield has no specific purpose at the moment.Figure 43.2. Add Host Wizard

DNS zones can be created in IdM. If the IdM server does not manage the DNS server, the zone can be entered manually in the menu area, like a regular text field.
NoteSelect the
Forcecheck box if you want to skip checking whether the host is resolvable via DNS.Click the
Add and Editbutton to go directly to the expanded entry page and enter more attribute information. Information about the host hardware and physical location can be included with the host entry.Figure 43.3. Expanded Entry Page