Chapter 3. About Clair
The content in this section highlights Clair releases, official Clair containers, and information about CVSS enrichment data.
3.1. Clair releases
New versions of Clair are regularly released. The source code needed to build Clair is packaged as an archive and attached to each release. Clair releases can be found at Clair releases.
Release artifacts also include the clairctl command line interface tool, which obtains updater data from the internet by using an open host.
3.2. Clair supported languages
Clair supports the following languages: * Python * Java (CRDA must be enabled)
3.3. Clair containers
Official downstream Clair containers bundled with Red Hat Quay can be found on the Red Hat Ecosystem Catalog.
Official upstream containers are packaged and released as a container at Quay.io/projectquay/clair. The latest tag tracks the Git development branch. Version tags are built from the corresponding release.
3.4. CVE ratings from the National Vulnerability Database
As of Clair v4.2, Common Vulnerability Scoring System (CVSS) enrichment data is now viewable in the Red Hat Quay UI. Additionally, Clair v4.2 adds CVSS scores from the National Vulnerability Database for detected vulnerabilities.
With this change, if the vulnerability has a CVSS score that is within 2 levels of the distribution score, the Red Hat Quay UI present’s the distribution’s score by default. For example:
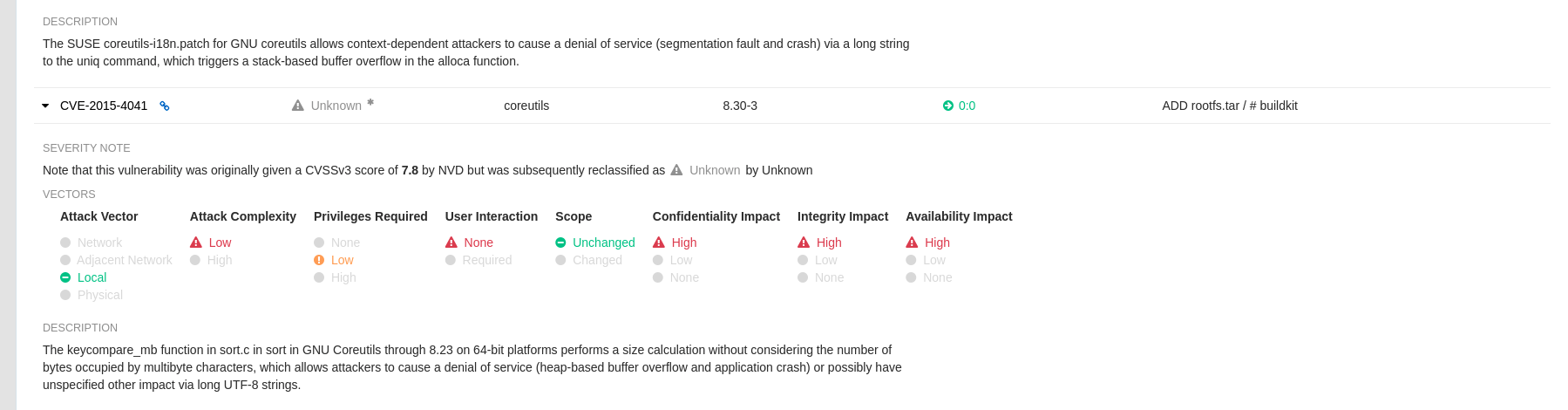
This differs from the previous interface, which would only display the following information:

3.5. Federal Information Processing Standard (FIPS) readiness and compliance
The Federal Information Processing Standard (FIPS) developed by the National Institute of Standards and Technology (NIST) is regarded as the highly regarded for securing and encrypting sensitive data, notably in highly regulated areas such as banking, healthcare, and the public sector. Red Hat Enterprise Linux (RHEL) and OpenShift Container Platform support the FIPS standard by providing a FIPS mode, in which the system only allows usage of specific FIPS-validated cryptographic modules like openssl. This ensures FIPS compliance.
Red Hat Quay supports running on FIPS-enabled RHEL and OpenShift Container Platform environments from Red Hat Quay version 3.5.0.

