Red Hat JBoss EAP XP 2.0.0 Release Notes
For Use with JBoss EAP XP 2.0.0
Abstract
Chapter 1. New Features and Enhancements
1.1. JBoss EAP XP manager
The JBoss EAP XP manager has been enhanced in JBoss EAP XP 2.0.0.
Improved status command
The status command now provides information about the following:
- Version of the server.
- Enabled patch streams and their cumulative patch IDs.
The command also provides the upgrade prompt if you have an old JBoss EAP XP server installed.
New patch-apply command
JBoss EAP XP manager 2.0 provides a patch-apply command. The command is similar to the patch apply management CLI command, but takes fewer arguments than the management CLI command.
You can use the patch-apply command to apply patches to any patch stream that is enabled on the server. Therefore, you can apply both the base server patches as well as the JBoss EAP XP patches to a server that has JBoss EAP XP patch stream enabled.
New upgrade command
JBoss EAP XP manager 2.0 provides an upgrade command.
Use this command to upgrade your JBoss EAP XP 1.0.x to JBoss EAP XP 2.0.0.
Additional resources
- For more information about JBoss EAP XP manager commands, see JBoss EAP XP manager 2.0 commands in Using Eclipse MicroProfile with JBoss EAP XP 2.0.0.
1.2. Eclipse MicroProfile
Support for readiness probes in MicroProfile Health
JBoss EAP XP 2.0.0 supports the following readiness probes to determine server health and readiness:
-
server-status- returnsUPwhen the server state isrunning. -
boot-errors- returnsUPwhen the probe detects no boot errors. -
deployment-status- returnsUPwhen the status for all deployments isOK.
For more information about the readiness probes, see Readiness probes that determine server health and readiness in Using Eclipse MicroProfile with JBoss EAP XP 2.0.0.
1.3. Bootable JAR
You can now package your application as a bootable JAR or as a hollow bootable JAR in JBoss EAP XP 2.0.0.
Ability to package applications as a bootable JAR
A bootable JAR contains a server, a packaged application, and the runtime required to launch the server.
You can build and package a microservices application as a bootable JAR with the JBoss EAP Maven plug-in. You can then run the application on a JBoss EAP bare-metal platform or a JBoss EAP for OpenShift platform.
The bootable JAR Maven plug-in uses Galleon trimming capability to reduce the size and memory footprint of the server. Thus, you can configure the server according to your requirements, including only the Galleon layers that provide the capabilities that you need.
For more information about packaging your application as a bootable JAR, see The bootable JAR in Using Eclipse MicroProfile with JBoss EAP XP 2.0.0.
Ability to package applications as a hollow bootable JAR
You can provision a hollow bootable JAR. This JAR contains only the server, so that the server can be reused to run a different application.
For more information about packaging your application as a hollow bootable JAR, see Using a bootable JAR on a JBoss EAP bare-metal platform in Using Eclipse MicroProfile with JBoss EAP XP 2.0.0.
Secure your application with Red Hat Single Sign-On
You can use the Galleon keycloak-client-oidc layer to install a version of a server that is provisioned with Red Hat Single Sign-On OpenID Connect client adapters.
The keycloak-client-oidc layer provides Red Hat Single Sign-On OpenID Connect client adapters to your Maven project. This layer is included with the keycloak-adapter-galleon-pack Red Hat Single Sign-On feature pack.
You can add the keycloak-adapter-galleon-pack feature pack to your Maven project by specifying the org.jboss.sso:keycloak-adapter-galleon-pack:9.0.10.redhat-00001 feature pack in your project.
For more information about using the keycloak-client-oidc layer, see Securing your JBoss EAP bootable JAR application with Red Hat Single Sign-On in Using Eclipse MicroProfile with JBoss EAP XP 2.0.0.
For information about configuring the Red Hat Single Sign-On adapter subsystem, see JBoss EAP Adapter in the Securing Applications and Services Guide.
The Maven feature-pack location
In JBoss EAP XP 2.0.0, the JBoss EAP feature-pack location is org.jboss.eap:wildfly-galleon-pack:2.0.0.GA-redhat-00002. You must reference this feature-pack location in the <plugin> element in the pom.xml file of your Maven project.
For more information about the JBoss EAP JAR Maven plug-in supported in JBoss EAP XP 2.0.0, see JBoss EAP Maven plug-in in Using Eclipse MicroProfile with JBoss EAP XP 2.0.0.
Additional resources
- For more information about packaging your application as a bootable JAR, see The bootable JAR in Using Eclipse MicroProfile with JBoss EAP XP 2.0.0.
1.4. Content trimming
Content trimming added to JBoss EAP XP
The content trimming capability introduced to support JBoss EAP on OpenShift is now supported when using JBoss EAP XP. For more information, see Capability trimming in Using Eclipse MicroProfile with JBoss EAP XP 2.0.0.
New Galleon layers
Several new Galleon layers have been added, including a layer that supports Eclipse MicroProfile capabilities. For more information see Decorator layers in Using Eclipse MicroProfile with JBoss EAP XP 2.0.0.
1.5. Quickstarts
OpenShift quickstarts
Quickstarts released in JBoss EAP XP 1.0.0 to support OpenShift were Tech Preview.
As of JBoss EAP XP 2.0.0, these quickstarts are fully supported.
Eclipse MicroProfile quickstarts for the bootable JAR
JBoss EAP XP 2.0.0 provides Eclipse MicroProfile quickstarts that you can use to understand the bootable JAR feature.
Each quickstart provides a small, specific, working bootable JAR example. Use the quickstarts to run and test bootable JAR examples on your chosen platform.
Eclipse MicroProfile quickstarts cannot be used to build and test a hollow bootable JAR.
Use the following Eclipse MicroProfile quickstarts to test the bootable JAR on either a bare-metal platform or an OpenShift platform:
- Eclipse MicroProfile Config
- Eclipse MicroProfile Fault Tolerance
- Eclipse MicroProfile Health
- Eclipse MicroProfile JWT
- Eclipse MicroProfile Metrics
- Eclipse MicroProfile OpenAPI
- Eclipse MicroProfile OpenTracing
- Eclipse MicroProfile REST Client
1.6. CodeReady support
CodeReady support for bootable JAR
You can now use CodeReady Studio and CodeReady Workspaces to create a bootable JAR for baremetal platforms.
Support for building a bootable JAR for OpenShift in CodeReady Studio is pending the release of CodeReady Studio 12.18.0.
Support for building a bootable JAR for OpenShift in CodeReady Workspaces is pending the release of CodeReady Workspaces 2.6.0.
These releases add support for devfiles, which are required to build a bootable JAR for OpenShift.
Chapter 2. Maintenance support
2.1. Maintenance support for JBoss EAP XP
When a new JBoss EAP XP major version is released, maintenance support for the previous major version begins. Maintenance support usually lasts for 12 weeks.
If you use a JBoss EAP XP major version that is outside of its maintenance support length, you might experience issues as the development of security patches and bug fixes no longer apply. To avoid such issues, upgrade to the newest JBoss EAP XP major version release that is compatible with your JBoss EAP version.
Additional resources
- For information about maintenance support, see the Red Hat JBoss Enterprise Application Platform expansion pack (JBoss EAP XP or EAP XP) Life Cycle and Support Policies located on the Red Hat Customer Portal.
Chapter 3. Unsupported features and deprecated features
3.1. Unsupported features
Support for some technologies is removed due to the high maintenance cost, low community interest, and better alternative solutions. The following features are not supported in JBoss EAP XP 2.0.0:
EAP Operator automated transaction recovery with your bootable JAR
On OpenShift, you cannot use the EAP Operator automated transaction recovery feature with your bootable JAR. A fix for this technical limitation is planned for a future JBoss EAP XP 2.0.0 patch release.
3.2. Deprecated features
Some features have been deprecated with this release. This means that no enhancements are made to these features, and they might be removed in the future, usually the next major release.
Red Hat continues to provide full support and bug fixes under our standard support terms and conditions. For more information about the Red Hat support policy for JBoss EAP XP, see the Red Hat JBoss Enterprise Application Platform expansion pack life cycle and support policies located on the Red Hat Customer Portal.
OpenJDK 8 images and imagestreams on OpenShift
On OpenShift, the following OpenJDK 8 images are deprecated:
- eap-xp2-openjdk8-openshift-rhel7
- eap-xp2-openjdk8-runtime-openshift-rhel7
On OpenShift, the following OpenJDK 8 imagestreams are deprecated:
- jboss-eap-xp2-openjdk8-openshift
- jboss-eap-xp2-openjdk8-runtime-openshift
These images and imagestreams are still supported on OpenShift. However, no enhancements are made to these images and imagestreams and they might be removed in the future. Red Hat continues to provide full support and bug fixes for OpenJDK 8 images and imagestreams under its standard support terms and conditions.
Chapter 4. Resolved issues and known issues
4.1. Resolved issues
See Resolved Issues for JBoss EAP XP 2.0.0 to view the list of issues that have been resolved for this release.
4.2. Known issues
See Known Issues for JBoss EAP XP 2.0.0 to view the list of known issues for this release.
The server installation directory on a bare-metal Windows platform
After you exit a bootable JAR that is running on a bare-metal Windows platform, the %userprofile%\AppData\Local\Temp\wildfly-bootable-server_XXX_ server installation directory, where XXX is the unique identifier of your bootable JAR server, is not automatically deleted, so you must delete the directory manually. If you set an installation directory with the --install-dir=<install dir> argument, you must delete the specified <install dir> installation directory instead of the TEMP directory.
Hot deploy and OpenShift server adapter
Hot deploy does not currently work with OpenShift server adapter. Red Hat is working on a fix.
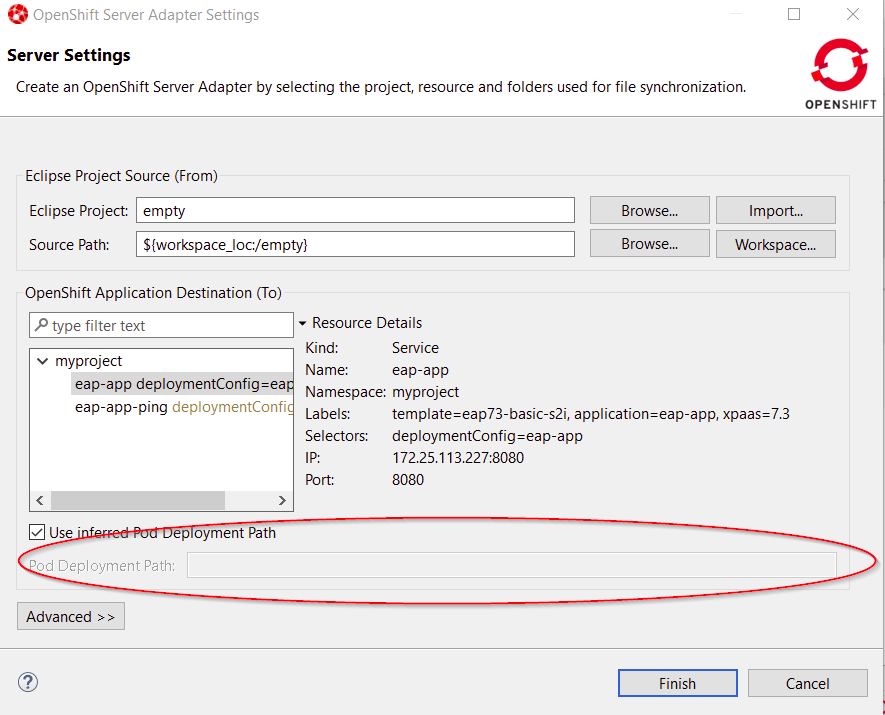
To work around this issue, in the OpenShift Server Adapter Settings Server Settings window, clear Use inferred Pod Deployment Path and set the Pod Deployment Path field to /opt/eap/standalone/deployments/, as illustrated in the accompanying image.
Figure 4.1. Pod deployment fields
For further information, see https://issues.redhat.com/browse/JBIDE-27591.

