Chapter 30. Managing remote systems in the web console
Connect to the remote systems and manage them in the RHEL 9 web console.
The following chapter describes:
- The optimal topology of connected systems.
- How to add and remove remote systems.
- When, why, and how to use SSH keys for remote system authentication.
-
How to configure a web console client to allow a user authenticated with a smart card to
SSHto a remote host and access services on it.
Prerequisites
- Opened the SSH service on remote systems.
30.1. Remote system manager in the web console
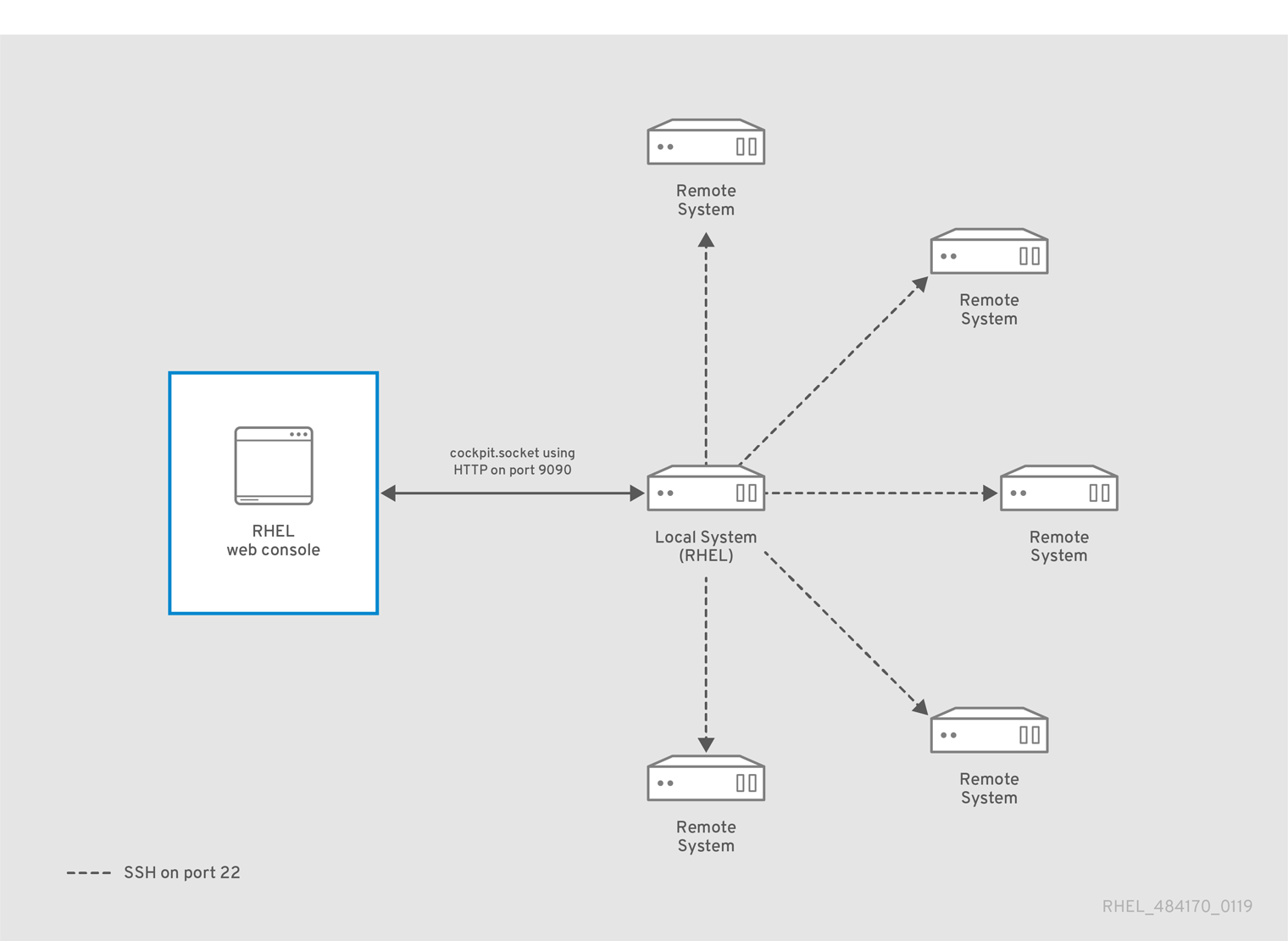
Using the RHEL 9 web console to manage remote systems in the network requires considering the topology of connected servers.
For optimal security, Red Hat recommends the following connection setup:
- Use one system with the web console as a bastion host. The bastion host is a system with opened HTTPS port.
- All other systems communicate through SSH.
With the web interface running on the bastion host, you can reach all other systems through the SSH protocol using port 22 in the default configuration.
30.2. Adding remote hosts to the web console
You can connect other systems with a user name and password.
Prerequisites
- You need to be logged into the web console with administration privileges. For details, see Logging in to the web console.
Procedure
In the RHEL 9 web console, click on your
username@hostnamein the top left corner of the Overview page.
In the drop down menu, click the Add new host button.
- In the Add new host dialog box, specify the host you want to add.
(Optional) Add the user name for the account to which you want to connect.
You can use any user account of the remote system. However, if you use credentials of a user account without administration privileges, you will not be able to perform administration tasks.
If you use the same credentials as for your local system, the web console will authenticate remote systems automatically every time you log in. However, using the same credentials on more machines could be a potential security risk.
- (Optional) Click the Color field to change the color of the system.
Click Add.
The new host will appear in the list of hosts in the
username@hostnamedrop down menu.
The web console does not save passwords used to log in to remote systems which means that you have to log in again after each system restart. Next time you log in, click the Log in button placed on the main screen of the disconnected remote system to open the login dialog.
30.3. Removing remote hosts from the web console
You can remove other systems from the web console.
Prerequisites
Remote systems added.
For details, see Adding remote hosts to the web console.
You must be logged into the web console with administrator privileges.
For details, see Logging in to the web console.
Procedure
- Log in to the RHEL 9 web console.
Click on your
username@hostnamein the top left corner of the Overview page.
Click the Edit hosts icon.
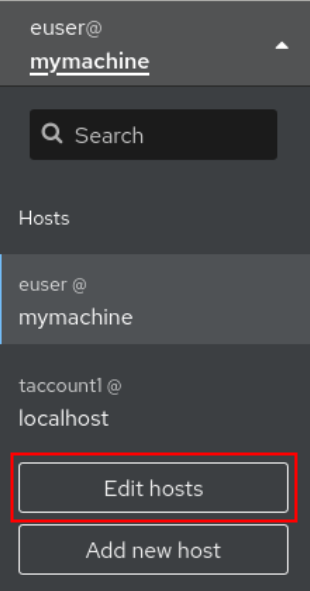
To remove a host from web console, click the red minus sign - button next to its host name. Note that you cannot remove a host you are currently connected to.
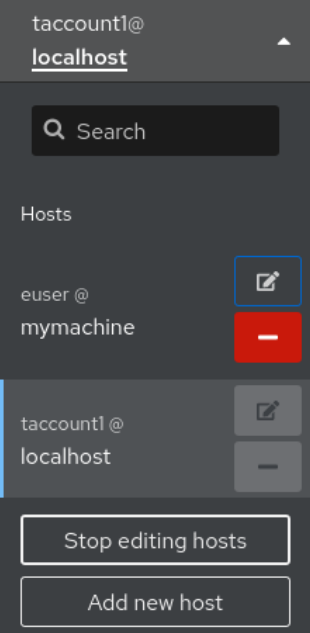
As a result, the server is removed from your web console.
30.4. Enabling SSH login for a new host
When you add a new host you can also log into it with an SSH key. If you already have an SSH key on your system, the web console will use the existing one; otherwise, the web console can create a key.
Prerequisites
You need to be logged into the web console with administration privileges.
For details, see Logging in to the web console.
Procedure
In the RHEL 9 web console, click on your
username@hostnamein the top left corner of the Overview page.
In the drop down menu, click the Add new host button.

- In the Add new host dialog box, specify the host you want to add.
Add the user name for the account to which you want to connect.
You can use any user account of the remote system. However, if you use credentials of a user account without administration privileges, you will not be able to perform administration tasks.
- (Optional) Click the Color field to change the color of the system.
Click Add.
A new dialog window will appear asking for a password.
- Enter the user account password.
Check Authorize ssh key if you already have an SSH key.
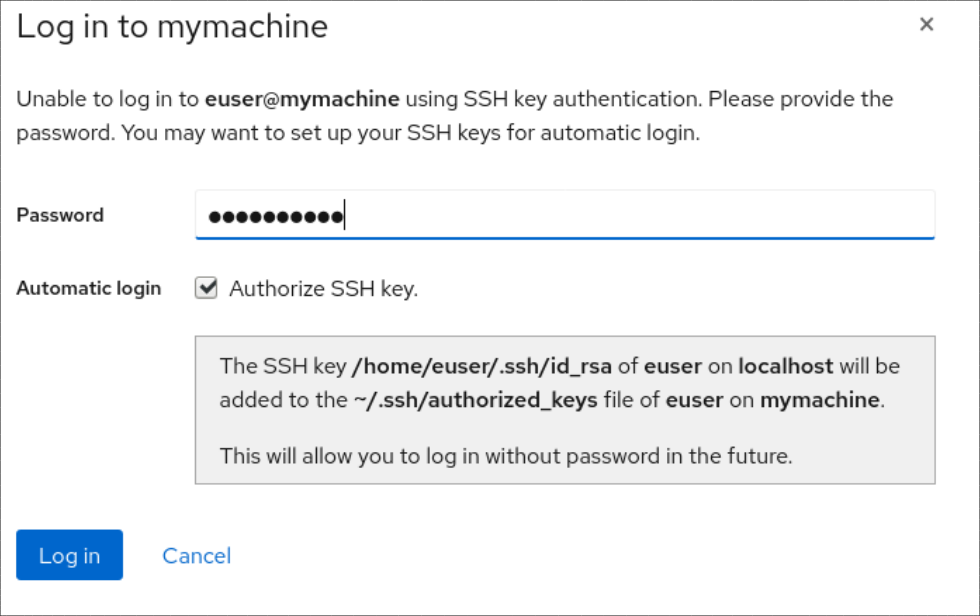
Check Create a new SSH key and authorize it if you do not have an SSH key. The web console will create it for you.

- Add a password for the SSH key.
- Confirm the password.
Click Log in
The new host will appear in the list of hosts in the
username@hostnamedrop down menu.
Verification steps
- Log out.
- Log back in.
- Click Log in in the Not connected to host screen.
Select SSH key as your authentication option.

- Enter your key password.
- Click Log in.
Additional resources
30.5. Constrained delegation in Identity Management
The Service for User to Proxy (S4U2proxy) extension provides a service that obtains a service ticket to another service on behalf of a user. This feature is known as constrained delegation. The second service is typically a proxy performing some work on behalf of the first service, under the authorization context of the user. Using constrained delegation eliminates the need for the user to delegate their full ticket-granting ticket (TGT).
Identity Management (IdM) traditionally uses the Kerberos S4U2proxy feature to allow the web server framework to obtain an LDAP service ticket on the user’s behalf. The IdM-AD trust system also uses constrained delegation to obtain a cifs principal.
You can use the S4U2proxy feature to configure a web console client to allow an IdM user that has authenticated with a smart card to achieve the following:
- Run commands with superuser privileges on the RHEL host on which the web console service is running without being asked to authenticate again.
-
Access a remote host using
SSHand access services on the host without being asked to authenticate again.
Additional resources
30.6. Configuring a web console to allow a user authenticated with a smart card to SSH to a remote host without being asked to authenticate again
After you have logged in to a user account on the RHEL web console, as an Identity Management (IdM) system administrator you might need to connect to remote machines by using the SSH protocol. You can use the constrained delegation feature to use SSH without being asked to authenticate again.
Follow this procedure to configure the web console to use constrained delegation. In the example below, the web console session runs on the myhost.idm.example.com host and it is being configured to access the remote.idm.example.com host by using SSH on behalf of the authenticated user.
Prerequisites
-
You have obtained an IdM
adminticket-granting ticket (TGT). -
You have
rootaccess to remote.idm.example.com. - The web console service is present in IdM.
- The remote.idm.example.com host is present in IdM.
The web console has created an
S4U2ProxyKerberos ticket in the user session. To verify that this is the case, log in to the web console as an IdM user, open theTerminalpage, and enter:$ klist Ticket cache: FILE:/run/user/1894000001/cockpit-session-3692.ccache Default principal: user@IDM.EXAMPLE.COM Valid starting Expires Service principal 07/30/21 09:19:06 07/31/21 09:19:06 HTTP/myhost.idm.example.com@IDM.EXAMPLE.COM 07/30/21 09:19:06 07/31/21 09:19:06 krbtgt/IDM.EXAMPLE.COM@IDM.EXAMPLE.COM for client HTTP/myhost.idm.example.com@IDM.EXAMPLE.COM
Procedure
Create a list of the target hosts that can be accessed by the delegation rule:
Create a service delegation target:
$ ipa servicedelegationtarget-add cockpit-targetAdd the target host to the delegation target:
$ ipa servicedelegationtarget-add-member cockpit-target \ --principals=host/remote.idm.example.com@IDM.EXAMPLE.COM
Allow
cockpitsessions to access the target host list by creating a service delegation rule and adding theHTTPservice Kerberos principal to it:Create a service delegation rule:
$ ipa servicedelegationrule-add cockpit-delegationAdd the web console client to the delegation rule:
$ ipa servicedelegationrule-add-member cockpit-delegation \ --principals=HTTP/myhost.idm.example.com@IDM.EXAMPLE.COMAdd the delegation target to the delegation rule:
$ ipa servicedelegationrule-add-target cockpit-delegation \ --servicedelegationtargets=cockpit-target
Enable Kerberos authentication on the remote.idm.example.com host:
-
SSHto remote.idm.example.com asroot. -
Open the
/etc/ssh/sshd_configfile for editing. -
Enable
GSSAPIAuthenticationby uncommenting theGSSAPIAuthentication noline and replacing it withGSSAPIAuthentication yes.
-
Restart the
SSHservice on remote.idm.example.com so that the above changes take effect immediately:$ systemctl try-restart sshd.service
30.7. Using Ansible to configure a web console to allow a user authenticated with a smart card to SSH to a remote host without being asked to authenticate again
After you have logged in to a user account on the RHEL web console, as an Identity Management (IdM) system administrator you might need to connect to remote machines by using the SSH protocol. You can use the constrained delegation feature to use SSH without being asked to authenticate again.
Follow this procedure to use the servicedelegationrule and servicedelegationtarget ansible-freeipa modules to configure a web console to use constrained delegation. In the example below, the web console session runs on the myhost.idm.example.com host and it is being configured to access the remote.idm.example.com host by using SSH on behalf of the authenticated user.
Prerequisites
-
The IdM
adminpassword. -
rootaccess to remote.idm.example.com. - The web console service is present in IdM.
- The remote.idm.example.com host is present in IdM.
The web console has created an
S4U2ProxyKerberos ticket in the user session. To verify that this is the case, log in to the web console as an IdM user, open theTerminalpage, and enter:$ klist Ticket cache: FILE:/run/user/1894000001/cockpit-session-3692.ccache Default principal: user@IDM.EXAMPLE.COM Valid starting Expires Service principal 07/30/21 09:19:06 07/31/21 09:19:06 HTTP/myhost.idm.example.com@IDM.EXAMPLE.COM 07/30/21 09:19:06 07/31/21 09:19:06 krbtgt/IDM.EXAMPLE.COM@IDM.EXAMPLE.COM for client HTTP/myhost.idm.example.com@IDM.EXAMPLE.COM
You have configured your Ansible control node to meet the following requirements:
- You are using Ansible version 2.14 or later.
-
You have installed the
ansible-freeipapackage on the Ansible controller. - The example assumes that in the ~/MyPlaybooks/ directory, you have created an Ansible inventory file with the fully-qualified domain name (FQDN) of the IdM server.
-
The example assumes that the secret.yml Ansible vault stores your
ipaadmin_password.
Procedure
Navigate to your ~/MyPlaybooks/ directory:
$ cd ~/MyPlaybooks/Create a
web-console-smart-card-ssh.ymlplaybook with the following content:Create a task that ensures the presence of a delegation target:
--- - name: Playbook to create a constrained delegation target hosts: ipaserver vars_files: - /home/user_name/MyPlaybooks/secret.yml tasks: - name: Ensure servicedelegationtarget web-console-delegation-target is present ipaservicedelegationtarget: ipaadmin_password: "{{ ipaadmin_password }}" name: web-console-delegation-targetAdd a task that adds the target host to the delegation target:
- name: Ensure servicedelegationtarget web-console-delegation-target member principal host/remote.idm.example.com@IDM.EXAMPLE.COM is present ipaservicedelegationtarget: ipaadmin_password: "{{ ipaadmin_password }}" name: web-console-delegation-target principal: host/remote.idm.example.com@IDM.EXAMPLE.COM action: memberAdd a task that ensures the presence of a delegation rule:
- name: Ensure servicedelegationrule delegation-rule is present ipaservicedelegationrule: ipaadmin_password: "{{ ipaadmin_password }}" name: web-console-delegation-ruleAdd a task that ensures that the Kerberos principal of the web console client service is a member of the constrained delegation rule:
- name: Ensure the Kerberos principal of the web console client service is added to the servicedelegationrule web-console-delegation-rule ipaservicedelegationrule: ipaadmin_password: "{{ ipaadmin_password }}" name: web-console-delegation-rule principal: HTTP/myhost.idm.example.com action: memberAdd a task that ensures that the constrained delegation rule is associated with the web-console-delegation-target delegation target:
- name: Ensure a constrained delegation rule is associated with a specific delegation target ipaservicedelegationrule: ipaadmin_password: "{{ ipaadmin_password }}" name: web-console-delegation-rule target: web-console-delegation-target action: member
- Save the file.
Run the Ansible playbook. Specify the playbook file, the file storing the password protecting the secret.yml file, and the inventory file:
$ ansible-playbook --vault-password-file=password_file -v -i inventory web-console-smart-card-ssh.ymlEnable Kerberos authentication on remote.idm.example.com:
-
SSHto remote.idm.example.com asroot. -
Open the
/etc/ssh/sshd_configfile for editing. -
Enable
GSSAPIAuthenticationby uncommenting theGSSAPIAuthentication noline and replacing it withGSSAPIAuthentication yes.
-
Additional resources
- Logging in to the web console with smart cards
- Constrained delegation in Identity Management
-
README-servicedelegationrule.mdandREADME-servicedelegationtarget.mdin the/usr/share/doc/ansible-freeipa/directory -
Sample playbooks in the
/usr/share/doc/ansible-freeipa/playbooks/servicedelegationtargetand/usr/share/doc/ansible-freeipa/playbooks/servicedelegationruledirectories

