Chapter 5. Managing user passwords in IdM
5.1. Who can change IdM user passwords and how
Regular users without the permission to change other users' passwords can change only their own personal password. The new password must meet the IdM password policies applicable to the groups of which the user is a member. For details on configuring password policies, see Defining IdM password policies.
Administrators and users with password change rights can set initial passwords for new users and reset passwords for existing users. These passwords:
- Do not have to meet the IdM password policies.
- Expire after the first successful login. When this happens, IdM prompts the user to change the expired password immediately. To disable this behavior, see Enabling password reset in IdM without prompting the user for a password change at the next login.
The LDAP Directory Manager (DM) user can change user passwords using LDAP tools. The new password can override any IdM password policies. Passwords set by DM do not expire after the first login.
5.2. Changing your user password in the IdM Web UI
As an Identity Management (IdM) user, you can change your user password in the IdM Web UI.
Prerequisites
- You are logged in to the IdM Web UI.
Procedure
In the upper right corner, click User name → Change password.
Figure 5.1. Resetting Password
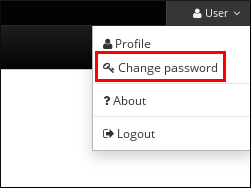
- Enter the current and new passwords.
5.3. Resetting another user’s password in the IdM Web UI
As an administrative user of Identity Management (IdM), you can change passwords for other users in the IdM Web UI.
Prerequisites
- You are logged in to the IdM Web UI as an administrative user.
Procedure
-
Select Identity →
Users. - Click the name of the user to edit.
Click Actions →
Reset password.Figure 5.2. Resetting Password
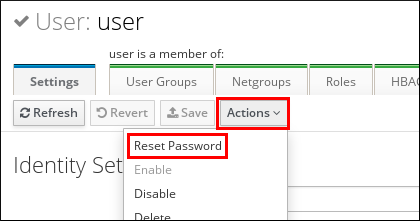
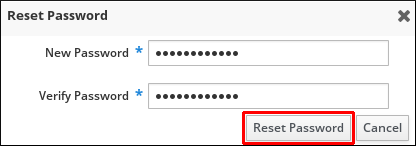
Enter the new password, and click Reset Password.
Figure 5.3. Confirming New Password
5.4. Resetting the Directory Manager user password
If you lose the Identity Management (IdM) Directory Manager password, you can reset it.
Prerequisites
-
You have
rootaccess to an IdM server.
Procedure
Generate a new password hash by using the
pwdhashcommand. For example:# pwdhash -D /etc/dirsrv/slapd-IDM-EXAMPLE-COM password {PBKDF2_SHA256}AAAgABU0bKhyjY53NcxY33ueoPjOUWtl4iyYN5uW...By specifying the path to the Directory Server configuration, you automatically use the password storage scheme set in the
nsslapd-rootpwstorageschemeattribute to encrypt the new password.On every IdM server in your topology, execute the following steps:
Stop all IdM services installed on the server:
# ipactl stopEdit the
/etc/dirsrv/IDM-EXAMPLE-COM/dse.ldiffile and set thensslapd-rootpwattribute to the value generated by thepwdhashcommand:nsslapd-rootpw: {PBKDF2_SHA256}AAAgABU0bKhyjY53NcxY33ueoPjOUWtl4iyYN5uW...- Start all IdM services installed on the server:
# ipactl start
5.5. Changing your user password or resetting another user’s password in IdM CLI
You can change your user password using the Identity Management (IdM) command-line interface (CLI). If you are an administrative user, you can use the CLI to reset another user’s password.
Prerequisites
- You have obtained a ticket-granting ticket (TGT) for an IdM user.
- If you are resetting another user’s password, you must have obtained a TGT for an administrative user in IdM.
Procedure
Enter the
ipa user-modcommand with the name of the user and the--passwordoption. The command will prompt you for the new password.$ ipa user-mod idm_user --password Password: Enter Password again to verify: -------------------- Modified user "idm_user" -------------------- ...
You can also use the ipa passwd idm_user command instead of ipa user-mod.
5.6. Enabling password reset in IdM without prompting the user for a password change at the next login
By default, when an administrator resets another user’s password, the password expires after the first successful login. As IdM Directory Manager, you can specify the following privileges for individual IdM administrators:
- They can perform password change operations without requiring users to change their passwords subsequently on their first login.
- They can bypass the password policy so that no strength or history enforcement is applied.
Bypassing the password policy can be a security threat. Exercise caution when selecting users to whom you grant these additional privileges.
Prerequisites
- You know the Directory Manager password.
Procedure
On every Identity Management (IdM) server in the domain, make the following changes:
Enter the
ldapmodifycommand to modify LDAP entries. Specify the name of the IdM server and the 389 port and press Enter:$ ldapmodify -x -D "cn=Directory Manager" -W -h server.idm.example.com -p 389 Enter LDAP Password:
- Enter the Directory Manager password.
Enter the distinguished name for the
ipa_pwd_extoppassword synchronization entry and press Enter:dn: cn=ipa_pwd_extop,cn=plugins,cn=config
Specify the
modifytype of change and press Enter:changetype: modify
Specify what type of modification you want LDAP to execute and to which attribute. Press Enter:
add: passSyncManagersDNs
Specify the administrative user accounts in the
passSyncManagersDNsattribute. The attribute is multi-valued. For example, to grant theadminuser the password resetting powers of Directory Manager:passSyncManagersDNs: \ uid=admin,cn=users,cn=accounts,dc=example,dc=com
- Press Enter twice to stop editing the entry.
The whole procedure looks as follows:
$ ldapmodify -x -D "cn=Directory Manager" -W -h server.idm.example.com -p 389 Enter LDAP Password: dn: cn=ipa_pwd_extop,cn=plugins,cn=config changetype: modify add: passSyncManagersDNs passSyncManagersDNs: uid=admin,cn=users,cn=accounts,dc=example,dc=com
The admin user, listed under passSyncManagerDNs, now has the additional privileges.
5.7. Checking if an IdM user’s account is locked
As an Identity Management (IdM) administrator, you can check if an IdM user’s account is locked. For that, you must compare a user’s maximum allowed number of failed login attempts with the number of the user’s actual failed logins.
Prerequisites
- You have obtained the ticket-granting ticket (TGT) of an administrative user in IdM.
Procedure
Display the status of the user account to see the number of failed logins:
$ ipa user-status example_user ----------------------- Account disabled: False ----------------------- Server: idm.example.com Failed logins: 8 Last successful authentication: N/A Last failed authentication: 20220229080317Z Time now: 2022-02-29T08:04:46Z ---------------------------- Number of entries returned 1 ----------------------------
Display the number of allowed login attempts for a particular user:
- Log in to the IdM Web UI as IdM administrator.
- Open the Identity → Users → Active users tab.

- Click the user name to open the user settings.
- In the Password policy section, locate the Max failures item.
-
Compare the number of failed logins as displayed in the output of the
ipa user-statuscommand with the Max failures number displayed in the IdM Web UI. If the number of failed logins equals that of maximum allowed login attempts, the user account is locked.
Additional resources
5.8. Unlocking user accounts after password failures in IdM
If a user attempts to log in using an incorrect password a certain number of times, Identity Management (IdM) locks the user account, which prevents the user from logging in. For security reasons, IdM does not display any warning message that the user account has been locked. Instead, the CLI prompt might continue asking the user for a password again and again.
IdM automatically unlocks the user account after a specified amount of time has passed. Alternatively, you can unlock the user account manually with the following procedure.
Prerequisites
- You have obtained the ticket-granting ticket of an IdM administrative user.
Procedure
To unlock a user account, use the
ipa user-unlockcommand.$ ipa user-unlock idm_user ----------------------- Unlocked account "idm_user" -----------------------After this, the user can log in again.
Additional resources
5.9. Enabling the tracking of last successful Kerberos authentication for users in IdM
For performance reasons, Identity Management (IdM) running in Red Hat Enterprise Linux 8 does not store the time stamp of the last successful Kerberos authentication of a user. As a consequence, certain commands, such as ipa user-status, do not display the time stamp.
Prerequisites
- You have obtained the ticket-granting ticket (TGT) of an administrative user in IdM.
-
You have
rootaccess to the IdM server on which you are executing the procedure.
Procedure
Display the currently enabled password plug-in features:
# ipa config-show | grep "Password plugin features" Password plugin features: AllowNThash, KDC:Disable Last Success
The output shows that the
KDC:Disable Last Successplug-in is enabled. The plug-in hides the last successful Kerberos authentication attempt from being visible in the ipa user-status output.Add the
--ipaconfigstring=featureparameter for every feature to theipa config-modcommand that is currently enabled, except forKDC:Disable Last Success:# ipa config-mod --ipaconfigstring='AllowNThash'This command enables only the
AllowNThashplug-in. To enable multiple features, specify the--ipaconfigstring=featureparameter separately for each feature.Restart IdM:
# ipactl restart

