Red Hat Training
A Red Hat training course is available for Red Hat Enterprise Linux
Chapter 6. Applying patches with kernel live patching
You can use the Red Hat Enterprise Linux kernel live patching solution to patch a running kernel without rebooting or restarting any processes.
With this solution, system administrators:
- Can immediately apply critical security patches to the kernel.
- Do not have to wait for long-running tasks to complete, for users to log off, or for scheduled downtime.
- Control the system’s uptime more and do not sacrifice security or stability.
Note that not every critical or important CVE will be resolved using the kernel live patching solution. Our goal is to reduce the required reboots for security-related patches, not to eliminate them entirely. For more details about the scope of live patching, see the Customer Portal Solutions article.
Some incompatibilities exist between kernel live patching and other kernel subcomponents. Read the Section 6.1, “Limitations of kpatch” section carefully before using kernel live patching.
6.1. Limitations of kpatch
-
The
kpatchfeature is not a general-purpose kernel upgrade mechanism. It is used for applying simple security and bug fix updates when rebooting the system is not immediately possible. -
Do not use the
SystemTaporkprobetools during or after loading a patch. The patch could fail to take effect until after such probes have been removed.
6.2. Support for third-party live patching
The kpatch utility is the only kernel live patching utility supported by Red Hat with the RPM modules provided by Red Hat repositories. Red Hat will not support any live patches which were not provided by Red Hat itself.
For support of a third-party live patch, contact the vendor that provided the patch.
For any system running with third-party live patches, Red Hat reserves the right to ask for reproduction with Red Hat shipped and supported software. In the event that this is not possible, we require a similar system and workload be deployed on your test environment without live patches applied, to confirm if the same behavior is observed.
For more information about third-party software support policies, see How does Red Hat Global Support Services handle third-party software, drivers, and/or uncertified hardware/hypervisors or guest operating systems?
6.3. Access to kernel live patches
Kernel live patching capability is implemented as a kernel module (.ko file) that is delivered as an RPM package.
All customers have access to kernel live patches, which are delivered through the usual channels. However, customers who do not subscribe to an extended support offering will lose access to new patches for the current minor release once the next minor release becomes available. For example, customers with standard subscriptions will only be able to live patch RHEL 8.2 kernels until RHEL 8.3 is released.
6.4. Components of kernel live patching
The components of kernel live patching are as follows:
- Kernel patch module
- The delivery mechanism for kernel live patches.
- A kernel module which is built specifically for the kernel being patched.
- The patch module contains the code of the desired fixes for the kernel.
-
The patch modules register with the
livepatchkernel subsystem and provide information about original functions to be replaced, with corresponding pointers to the replacement functions. Kernel patch modules are delivered as RPMs. -
The naming convention is
kpatch_<kernel version>_<kpatch version>_<kpatch release>. The "kernel version" part of the name has dots and dashes replaced with underscores.
- The
kpatchutility - A command-line utility for managing patch modules.
- The
kpatchservice -
A
systemdservice required bymultiuser.target. This target loads the kernel patch module at boot time.
6.5. How kernel live patching works
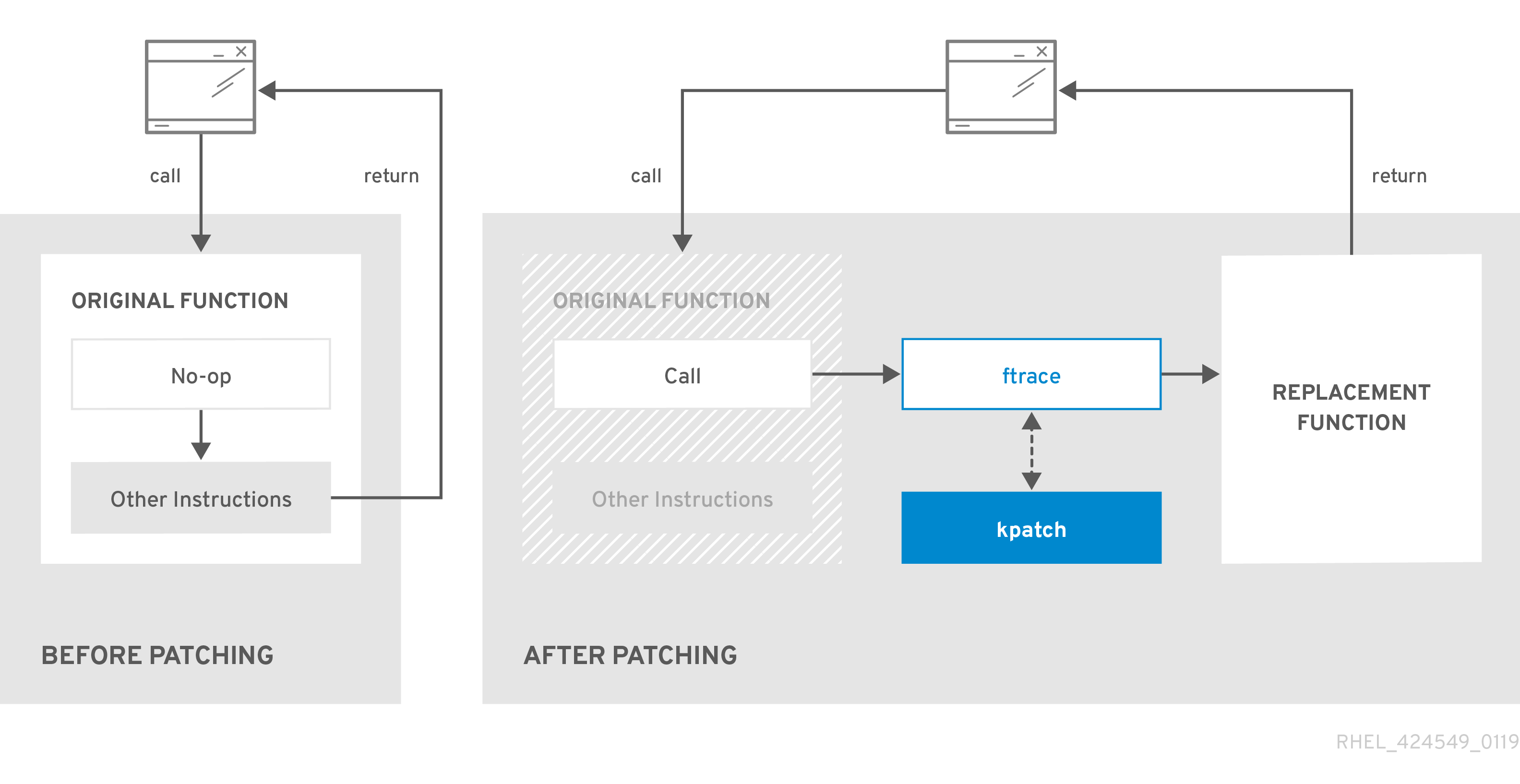
The kpatch kernel patching solution uses the livepatch kernel subsystem to redirect old functions to new ones. When a live kernel patch is applied to a system, the following things happen:
-
The kernel patch module is copied to the
/var/lib/kpatch/directory and registered for re-application to the kernel bysystemdon next boot. -
The kpatch module is loaded into the running kernel and the patched functions are registered to the
ftracemechanism with a pointer to the location in memory of the new code. -
When the kernel accesses the patched function, it is redirected by the
ftracemechanism which bypasses the original functions and redirects the kernel to patched version of the function.
Figure 6.1. How kernel live patching works
6.6. Enabling kernel live patching
A kernel patch module is delivered in an RPM package, specific to the version of the kernel being patched. Each RPM package will be cumulatively updated over time.
The following subsections describe how to ensure you receive all future cumulative live patching updates for a given kernel.
Red Hat does not support any third party live patches applied to a Red Hat supported system.
6.6.1. Subscribing to the live patching stream
This procedure describes installing a particular live patching package. By doing so, you subscribe to the live patching stream for a given kernel and ensure that you receive all future cumulative live patching updates for that kernel.
Because live patches are cumulative, you cannot select which individual patches are deployed for a given kernel.
Prerequisites
- Root permissions
Procedure
Optionally, check your kernel version:
# uname -r 3.10.0-1062.el7.x86_64
Search for a live patching package that corresponds to the version of your kernel:
# yum search $(uname -r)
Install the live patching package:
# yum install "kpatch-patch = $(uname -r)"
The command above installs and applies the latest cumulative live patches for that specific kernel only.
The live patching package contains a patch module, if the package’s version is 1-1 or higher. In that case the kernel will be automatically patched during the installation of the live patching package.
The kernel patch module is also installed into the
/var/lib/kpatch/directory to be loaded by thesystemdsystem and service manager during the future reboots.NoteIf there are not yet any live patches available for the given kernel, an empty live patching package will be installed. An empty live patching package will have a kpatch_version-kpatch_release of 0-0, for example
kpatch-patch-3_10_0-1062-0-0.el7.x86_64.rpm. The installation of the empty RPM subscribes the system to all future live patches for the given kernel.Optionally, verify that the kernel is patched:
# kpatch list Loaded patch modules: kpatch_3_10_0_1062_1_1 [enabled] Installed patch modules: kpatch_3_10_0_1062_1_1 (3.10.0-1062.el7.x86_64) …
The output shows that the kernel patch module has been loaded into the kernel, which is now patched with the latest fixes from the
kpatch-patch-3_10_0-1062-1-1.el7.x86_64.rpmpackage.
Additional resources
-
For more information about the
kpatchcommand-line utility, see thekpatch(1)manual page. - Refer to the relevant sections of the System Administrator’s Guide for further information about software packages in RHEL 7.
6.7. Updating kernel patch modules
Since kernel patch modules are delivered and applied through RPM packages, updating a cumulative kernel patch module is like updating any other RPM package.
Prerequisites
- Root permissions
- The system is subscribed to the live patching stream, as described in Section 6.6.1, “Subscribing to the live patching stream”.
Procedure
Update to a new cumulative version for the current kernel:
# yum update "kpatch-patch = $(uname -r)"
The command above automatically installs and applies any updates that are available for the currently running kernel. Including any future released cumulative live patches.
Alternatively, update all installed kernel patch modules:
# yum update "kpatch-patch*"
When the system reboots into the same kernel, the kernel is automatically live patched again by the kpatch.service service.
Additional resources
- For further information about updating software packages, see the relevant sections of System Administrator’s Guide.
6.8. Disabling kernel live patching
In case system administrators encountered some unanticipated negative effects connected with the Red Hat Enterprise Linux kernel live patching solution they have a choice to disable the mechanism. The following sections describe the ways how to disable the live patching solution.
Currently, Red Hat does not support reverting live patches without rebooting your system. In case of any issues, contact our support team.
6.8.1. Removing the live patching package
The following procedure describes how to disable the Red Hat Enterprise Linux kernel live patching solution by removing the live patching package.
Prerequisites
- Root permissions
- The live patching package is installed.
Procedure
Select the live patching package:
# yum list installed | grep kpatch-patch kpatch-patch-3_10_0-1062.x86_64 1-1.el7 @@commandline …
The example output above lists live patching packages that you installed.
Remove the live patching package:
# yum remove kpatch-patch-3_10_0-1062.x86_64
When a live patching package is removed, the kernel remains patched until the next reboot, but the kernel patch module is removed from disk. After the next reboot, the corresponding kernel will no longer be patched.
- Reboot your system.
Verify that the live patching package has been removed:
# yum list installed | grep kpatch-patch
The command displays no output if the package has been successfully removed.
Optionally, verify that the kernel live patching solution is disabled:
# kpatch list Loaded patch modules:
The example output shows that the kernel is not patched and the live patching solution is not active because there are no patch modules that are currently loaded.
Additional resources
-
For more information about the
kpatchcommand-line utility, see thekpatch(1)manual page. - For further information about working with software packages, see the relevant sections of System Administrator’s Guide.
6.8.2. Uninstalling the kernel patch module
The following procedure describes how to prevent the Red Hat Enterprise Linux kernel live patching solution from applying a kernel patch module on subsequent boots.
Prerequisites
- Root permissions
- A live patching package is installed.
- A kernel patch module is installed and loaded.
Procedure
Select a kernel patch module:
# kpatch list Loaded patch modules: kpatch_3_10_0_1062_1_1 [enabled] Installed patch modules: kpatch_3_10_0_1062_1_1 (3.10.0-1062.el7.x86_64) …
Uninstall the selected kernel patch module:
# kpatch uninstall kpatch_3_10_0_1062_1_1 uninstalling kpatch_3_10_0_1062_1_1 (3.10.0-1062.el7.x86_64)
Note that the uninstalled kernel patch module is still loaded:
# kpatch list Loaded patch modules: kpatch_3_10_0_1062_1_1 [enabled] Installed patch modules: <NO_RESULT>When the selected module is uninstalled, the kernel remains patched until the next reboot, but the kernel patch module is removed from disk.
- Reboot your system.
Optionally, verify that the kernel patch module has been uninstalled:
# kpatch list Loaded patch modules:
The example output above shows no loaded or installed kernel patch modules, therefore the kernel is not patched and the kernel live patching solution is not active.
Additional resources
-
For more information about the
kpatchcommand-line utility, refer to thekpatch(1)manual page.
6.8.3. Disabling kpatch.service
The following procedure describes how to prevent the Red Hat Enterprise Linux kernel live patching solution from applying all kernel patch modules globally on subsequent boots.
Prerequisites
- Root permissions
- A live patching package is installed.
- A kernel patch module is installed and loaded.
Procedure
Verify
kpatch.serviceis enabled:# systemctl is-enabled kpatch.service enabled
Disable
kpatch.service:# systemctl disable kpatch.service Removed /etc/systemd/system/multi-user.target.wants/kpatch.service.
Note that the applied kernel patch module is still loaded:
# kpatch list Loaded patch modules: kpatch_3_10_0_1062_1_1 [enabled] Installed patch modules: kpatch_3_10_0_1062_1_1 (3.10.0-1062.el7.x86_64)
- Reboot your system.
Optionally, verify the status of
kpatch.service:# systemctl status kpatch.service ● kpatch.service - "Apply kpatch kernel patches" Loaded: loaded (/usr/lib/systemd/system/kpatch.service; disabled; vendor preset: disabled) Active: inactive (dead)
The example output testifies that
kpatch.servicehas been disabled and is not running. Thereby, the kernel live patching solution is not active.Verify that the kernel patch module has been unloaded:
# kpatch list Loaded patch modules: Installed patch modules: kpatch_3_10_0_1062_1_1 (3.10.0-1062.el7.x86_64)
The example output above shows that the kernel patch module is still installed but the kernel is not patched.
Additional resources
-
For more information about the
kpatchcommand-line utility, see thekpatch(1)manual page. -
For more information about the
systemdsystem and service manager, unit configuration files, their locations, as well as a complete list ofsystemdunit types, see the relevant sections in System Administrator’s Guide.

