Chapter 5. Upgrading CodeReady Workspaces
This chapter describes how to upgrade a CodeReady Workspaces instance from version 2.11 to CodeReady Workspaces 2.12.
The method used to install the CodeReady Workspaces instance determines the method to proceed with for the upgrade:
5.1. Upgrading CodeReady Workspaces using OperatorHub
This section describes how to upgrade from an earlier minor version using the Operator from OperatorHub in the OpenShift web console.
OperatorHub supports Automatic and Manual upgrade strategies: Automatic:: The upgrade process starts when a new version of the Operator is published. Manual:: The update must be manually approved every time the new version of the Operator is published.
5.1.1. Specifying the approval strategy of CodeReady Workspaces in OperatorHub
Prerequisites
- An administrator account on an instance of OpenShift.
- An instance of CodeReady Workspaces 2.11 or earlier that was installed by using OperatorHub.
Procedure
- Open the OpenShift web console.
- Navigate to the Operators → Installed Operators page.
- Click Red Hat CodeReady Workspaces in the list of installed Operators.
- Navigate to the Subscription tab.
Configure the approval strategy to
AutomaticorManual.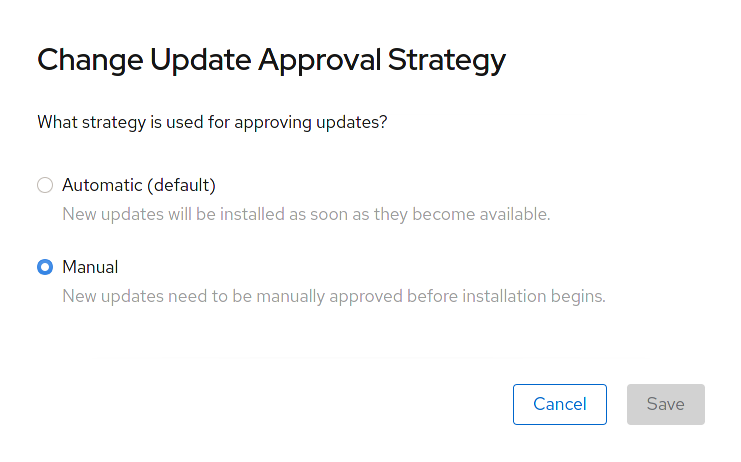
5.1.2. Manually upgrading CodeReady Workspaces in OperatorHub
OperatorHub is an assembly point for sharing Operators. The OperatorHub helps you deploy and update applications. The following section describes the process of upgrading CodeReady Workspaces by using OperatorHub and the Manual approval strategy approach. Use the Manual approval strategy to prevent automatic updates of the Operator with every release.
Prerequisites
- An administrator account on an instance of OpenShift.
- An instance of CodeReady Workspaces 2.11 or earlier that was installed by using OperatorHub.
-
The approval strategy in the subscription is
Manual.
Procedure
- Open the OpenShift web console.
- Navigate to the Operators → Installed Operators page.
- In the list of the installed Operators, click Red Hat CodeReady Workspaces.
- Navigate to the Subscription tab.
- Next to the Upgrade Status, inspect the upgrades that require approval. The expected message is 1 requires approval.
- Click 1 requires approval.
- Click Preview Install Plan.
- Review the resources that are available for upgrade and click Approve.
Verification steps
- Navigate to the Operators → Installed Operators page.
- Monitor the upgrade progress. When complete, the status changes to Succeeded and Up to date. The 2.12 version number is visible at the end of the page.
Additional resources
- Upgrading installed Operators section in the OpenShift documentation.
5.2. Upgrading CodeReady Workspaces using the CLI management tool
This section describes how to upgrade from the previous minor version using the CLI management tool.
Prerequisites
- An administrative account on OpenShift.
-
A running instance of a previous minor version of Red Hat CodeReady Workspaces, installed using the CLI management tool on the same instance of OpenShift, in the
<openshift-workspaces>project. -
crwctlis available and updated. See Section 3.3.1, “Installing the crwctl CLI management tool”.
Procedure
- Save and push changes back to the Git repositories for all running CodeReady Workspaces 2.11 workspaces.
- Shut down all workspaces in the CodeReady Workspaces 2.11 instance.
Upgrade CodeReady Workspaces:
$ crwctl server:update -n openshift-workspaces
For slow systems or internet connections, add the --k8spodwaittimeout=1800000 flag option to the crwctl server:update command to extend the Pod timeout period to 1800000 ms or longer.
Verification steps
- Navigate to the CodeReady Workspaces instance.
- The 2.12 version number is visible at the bottom of the page.
5.3. Upgrading CodeReady Workspaces using the CLI management tool in restricted environment
This section describes how to upgrade Red Hat CodeReady Workspaces using the CLI management tool in restricted environment. The upgrade path supports minor version update, from CodeReady Workspaces version 2.11 to version 2.12.
Prerequisites
- An administrative account on an instance of OpenShift.
-
A running instance version 2.11 of Red Hat CodeReady Workspaces, installed using the CLI management tool on the same instance of OpenShift, with the crwctl
--installer operatormethod, in the<openshift-workspaces>project. See Section 3.4, “Installing CodeReady Workspaces in a restricted environment”. -
The
crwctl2.12 management tool is available. See Section 3.3.1, “Installing the crwctl CLI management tool”.
5.3.1. Understanding network connectivity in restricted environments
CodeReady Workspaces requires that each OpenShift Route created for CodeReady Workspaces is accessible from inside the OpenShift cluster. These CodeReady Workspaces components have a OpenShift Route: codeready-workspaces-server, keycloak, devfile-registry, plugin-registry.
Consider the network topology of the environment to determine how best to accomplish this.
Example 5.1. Network owned by a company or an organization, disconnected from the public Internet
The network administrators must ensure that it is possible to route traffic bound from the cluster to OpenShift Route host names.
Example 5.2. Private subnetwork in a cloud provider
Create a proxy configuration allowing the traffic to leave the node to reach an external-facing Load Balancer.
5.3.2. Building offline registry images
5.3.2.1. Building an offline devfile registry image
This section describes how to build an offline devfile registry image. Starting workspaces without relying on resources from the outside Internet requires building this image. The image contains all sample projects referenced in devfiles as zip files.
Procedure
Clone the devfile registry repository and check out the version to deploy:
$ git clone git@github.com:redhat-developer/codeready-workspaces.git $ cd codeready-workspaces $ git checkout crw-2.12-rhel-8
Build an offline devfile registry image:
$ cd dependencies/che-devfile-registry $ ./build.sh --organization <my-org> \ --registry <my-registry> \ --tag <my-tag> \ --offline
NoteTo display full options for the
build.shscript, use the--helpparameter.
Additional resources
5.3.2.2. Building an offline plug-in registry image
This section describes how to build an offline plug-in registry image. Starting workspaces without relying on resources from the outside Internet requires building this image. The image contains plug-in metadata and all plug-in or extension artifacts.
Prerequisites
- Node.js 12.x
- A running version of yarn. See Installing Yarn.
-
./node_modules/.binis in thePATHenvironment variable. - A running installation of podman or docker.
Procedure
Clone the plug-in registry repository and check out the version to deploy:
$ git clone git@github.com:redhat-developer/codeready-workspaces.git $ cd codeready-workspaces $ git checkout crw-2.12-rhel-8
Build offline plug-in registry image:
$ cd dependencies/che-plugin-registry $ ./build.sh --organization <my-org> \ --registry <my-registry> \ --tag <my-tag> \ --offline \ --skip-digest-generation
NoteTo display full options for the
build.shscript, use the--helpparameter.
Additional resources
5.3.3. Preparing an private registry
Prerequisites
-
The
octool is available. -
The
skopeotool, version 0.1.40 or later, is available. -
The
podmantool is available. - An image registry accessible from the OpenShift cluster and supporting the format of the V2 image manifest, schema version 2. Ensure you can push to it from a location having, at least temporarily, access to the internet.
Table 5.1. Placeholders used in examples
|
| Full coordinates of the source image, including registry, organization, and digest. |
|
| Host name and port of the target container-image registry. |
|
| Organization in the target container-image registry |
|
| Image name and digest in the target container-image registry. |
|
| User name in the target container-image registry. |
|
| User password in the target container-image registry. |
Procedure
Log into the internal image registry:
$ podman login --username <user> --password <password> <target-registry>
NoteIf you encounter an error, like
x509: certificate signed by unknown authority, when attempting to push to the internal registry, try one of these workarounds:-
add the OpenShift cluster’s certificate to
/etc/containers/certs.d/<target-registry> -
add the registry as an insecure registry by adding the following lines to the Podman configuration file located at
/etc/containers/registries.conf:
[registries.insecure] registries = ['<target-registry>']-
add the OpenShift cluster’s certificate to
Copy images without changing their digest. Repeat this step for every image in the following table:
$ skopeo copy --all docker://<source-image> docker://<target-registry>/<target-organization>/<target-image>
NoteTable 5.2. Understanding the usage of the container-images from the prefix or keyword they include in their name
Usage Prefix or keyword Essential
not
stacks-,plugin-, or-openj9-Workspaces
stacks-,plugin-IBM Z and IBM Power Systems
-openj9-NoteImages suffixed with
openj9are theEclipse OpenJ9image equivalents of the OpenJDK images used on x86_64. IBM Power Systems and IBM Z use Eclipse OpenJ9 for better performance on those systems.Table 5.3. Images to copy in the private registry
<source-image> <target-image> registry.redhat.io/codeready-workspaces/backup-rhel8@sha256:fcf0e843868889f9125b5bee63b6456d08095004ccacb4e5c63e7a0c020e7ca3backup-rhel8@sha256:fcf0e843868889f9125b5bee63b6456d08095004ccacb4e5c63e7a0c020e7ca3registry.redhat.io/codeready-workspaces/configbump-rhel8@sha256:c833b59bdc7022883cd71f6b72e457d8a2fae9d25ac9b45eec2f9501ec89c380configbump-rhel8@sha256:c833b59bdc7022883cd71f6b72e457d8a2fae9d25ac9b45eec2f9501ec89c380registry.redhat.io/codeready-workspaces/crw-2-rhel8-operator@sha256:50bb42c6b5d38c4af5f620a44e8681656383d67a557b6a66af3ffdb51846677ecrw-2-rhel8-operator@sha256:50bb42c6b5d38c4af5f620a44e8681656383d67a557b6a66af3ffdb51846677eregistry.redhat.io/codeready-workspaces/dashboard-rhel8@sha256:4a5a51764cb7f4eb3aab8f089826738d46ed40f6ec263d0697ae9f28107af06fdashboard-rhel8@sha256:4a5a51764cb7f4eb3aab8f089826738d46ed40f6ec263d0697ae9f28107af06fregistry.redhat.io/codeready-workspaces/devfileregistry-rhel8@sha256:40448eb12f3af94efe8b78120995b204cb983f2f9b66f795cf2b68dd67e45cf7devfileregistry-rhel8@sha256:40448eb12f3af94efe8b78120995b204cb983f2f9b66f795cf2b68dd67e45cf7registry.redhat.io/codeready-workspaces/jwtproxy-rhel8@sha256:82f553706c8c809c589b4169ccb7858569e746e0f06d23e414dd47442ab119adjwtproxy-rhel8@sha256:82f553706c8c809c589b4169ccb7858569e746e0f06d23e414dd47442ab119adregistry.redhat.io/codeready-workspaces/machineexec-rhel8@sha256:93dc77a7f33171b36dbc112e7e732da4044c4c75a48b7a25907521c529170c0cmachineexec-rhel8@sha256:93dc77a7f33171b36dbc112e7e732da4044c4c75a48b7a25907521c529170c0cregistry.redhat.io/codeready-workspaces/plugin-java11-openj9-rhel8@sha256:ff81f7332ae1fed4c84fa9f47921173a754624ef3e019fcd71a5192491857866plugin-java11-openj9-rhel8@sha256:ff81f7332ae1fed4c84fa9f47921173a754624ef3e019fcd71a5192491857866registry.redhat.io/codeready-workspaces/plugin-java11-rhel8@sha256:f06f983d5e49a1ab05b9de54e449b2033688e7a38a6c57550f2ed87b3bef3fe2plugin-java11-rhel8@sha256:f06f983d5e49a1ab05b9de54e449b2033688e7a38a6c57550f2ed87b3bef3fe2registry.redhat.io/codeready-workspaces/plugin-java8-openj9-rhel8@sha256:712968392395b940f18c586ee6fe9c50037be70813e099189ff24bc0767057fbplugin-java8-openj9-rhel8@sha256:712968392395b940f18c586ee6fe9c50037be70813e099189ff24bc0767057fbregistry.redhat.io/codeready-workspaces/plugin-java8-rhel8@sha256:c451114be8be1ff012a85eae983d85216d0171dfc1376df1c410f54af0226bc2plugin-java8-rhel8@sha256:c451114be8be1ff012a85eae983d85216d0171dfc1376df1c410f54af0226bc2registry.redhat.io/codeready-workspaces/plugin-kubernetes-rhel8@sha256:3e43ffa6757980fb0f092798b76d6bbfa63768c72d2f071b666f6401b6c0df5cplugin-kubernetes-rhel8@sha256:3e43ffa6757980fb0f092798b76d6bbfa63768c72d2f071b666f6401b6c0df5cregistry.redhat.io/codeready-workspaces/plugin-openshift-rhel8@sha256:55e67c70b3b04e045230bf553e2394920d088027aad6eb5ce0a21abede138af5plugin-openshift-rhel8@sha256:55e67c70b3b04e045230bf553e2394920d088027aad6eb5ce0a21abede138af5registry.redhat.io/codeready-workspaces/pluginbroker-artifacts-rhel8@sha256:3436bacdc249e8dcc289b67e89340bdc2c5b6694304fe369af751f684a140d60pluginbroker-artifacts-rhel8@sha256:3436bacdc249e8dcc289b67e89340bdc2c5b6694304fe369af751f684a140d60registry.redhat.io/codeready-workspaces/pluginbroker-metadata-rhel8@sha256:e709e89bd1ab1612baad039ad6b824b027a070ff0a37be3395202faa55518e09pluginbroker-metadata-rhel8@sha256:e709e89bd1ab1612baad039ad6b824b027a070ff0a37be3395202faa55518e09registry.redhat.io/codeready-workspaces/pluginregistry-rhel8@sha256:7522baa5b8798bf98d9aad17d08dc34799cc5e33133af5b63179266c1b4dfb52pluginregistry-rhel8@sha256:7522baa5b8798bf98d9aad17d08dc34799cc5e33133af5b63179266c1b4dfb52registry.redhat.io/codeready-workspaces/server-rhel8@sha256:ae26042c25464990d626f2de586d47c7f8077444b48b29792bc9c2c45d739313server-rhel8@sha256:ae26042c25464990d626f2de586d47c7f8077444b48b29792bc9c2c45d739313registry.redhat.io/codeready-workspaces/stacks-cpp-rhel8@sha256:5ae3c3fcef5050ca30126d55229fe3334e887c658d6e5fbe9ef6aa8339dfc89estacks-cpp-rhel8@sha256:5ae3c3fcef5050ca30126d55229fe3334e887c658d6e5fbe9ef6aa8339dfc89eregistry.redhat.io/codeready-workspaces/stacks-dotnet-rhel8@sha256:68875b794b80d9590fceff2e35eaa8f0ac47cd9e8f183f54652a1d1703024dd8stacks-dotnet-rhel8@sha256:68875b794b80d9590fceff2e35eaa8f0ac47cd9e8f183f54652a1d1703024dd8registry.redhat.io/codeready-workspaces/stacks-golang-rhel8@sha256:a007380852029dcb01f2a00956f4e2b26c9c53d2063eca92d41d56fff4e83a27stacks-golang-rhel8@sha256:a007380852029dcb01f2a00956f4e2b26c9c53d2063eca92d41d56fff4e83a27registry.redhat.io/codeready-workspaces/stacks-php-rhel8@sha256:193b9775d58e1f7d9a45607b23bbfea4cfcba53356872da3e28de3ee9a8254e5stacks-php-rhel8@sha256:193b9775d58e1f7d9a45607b23bbfea4cfcba53356872da3e28de3ee9a8254e5registry.redhat.io/codeready-workspaces/theia-endpoint-rhel8@sha256:2eb5fd69e08e3a1a8f557fe1d41170ee9dac89d15c5947aabc477d4e2107a9eatheia-endpoint-rhel8@sha256:2eb5fd69e08e3a1a8f557fe1d41170ee9dac89d15c5947aabc477d4e2107a9earegistry.redhat.io/codeready-workspaces/theia-rhel8@sha256:7c1fcf0a972e2905a0758d53e2155534643d0fbcbb688d57b54f05bafe323582theia-rhel8@sha256:7c1fcf0a972e2905a0758d53e2155534643d0fbcbb688d57b54f05bafe323582registry.redhat.io/codeready-workspaces/traefik-rhel8@sha256:012b6d04e2c3ed30e34d95f3566a7ccdaa2e696b33d77f7622405149c21d9a6ftraefik-rhel8@sha256:012b6d04e2c3ed30e34d95f3566a7ccdaa2e696b33d77f7622405149c21d9a6fregistry.redhat.io/devworkspace/devworkspace-rhel8-operator@sha256:e68ec2fe7ac27e59641bdfc7794ae99fdfaa60e5b6d0cc0e3f20ab3f7a31bc11devworkspacedevworkspace-rhel8-operator@sha256:e68ec2fe7ac27e59641bdfc7794ae99fdfaa60e5b6d0cc0e3f20ab3f7a31bc11registry.redhat.io/jboss-eap-7/eap-xp3-openj9-11-openshift-rhel8@sha256:896c1a9baf21400e8bc75e8b7fb22fc3a829aa3fee68ca9f8373111b7c21e27deap-xp3-openj9-11-openshift-rhel8@sha256:896c1a9baf21400e8bc75e8b7fb22fc3a829aa3fee68ca9f8373111b7c21e27dregistry.redhat.io/jboss-eap-7/eap-xp3-openjdk11-openshift-rhel8@sha256:3875b2ee2826a6d8134aa3b80ac0c8b5ebc4a7f718335d76dfc3461b79f93d19eap-xp3-openjdk11-openshift-rhel8@sha256:3875b2ee2826a6d8134aa3b80ac0c8b5ebc4a7f718335d76dfc3461b79f93d19registry.redhat.io/jboss-eap-7/eap74-openjdk8-openshift-rhel7@sha256:b4a113c4d4972d142a3c350e2006a2b297dc883f8ddb29a88db19c892358632deap74-openjdk8-openshift-rhel7@sha256:b4a113c4d4972d142a3c350e2006a2b297dc883f8ddb29a88db19c892358632dregistry.redhat.io/openshift4/ose-kube-rbac-proxy@sha256:bd74f0b95ff2881faf6eb4520feecd067b69a759f09bbfecd467447ce2a2a25eopenshift4ose-kube-rbac-proxy@sha256:bd74f0b95ff2881faf6eb4520feecd067b69a759f09bbfecd467447ce2a2a25eregistry.redhat.io/openshift4/ose-oauth-proxy@sha256:7e14b5d357940f2e5e72a41f2a289c7b2757b64abf96a71f54f5829621730f84openshift4ose-oauth-proxy@sha256:7e14b5d357940f2e5e72a41f2a289c7b2757b64abf96a71f54f5829621730f84registry.redhat.io/rh-sso-7/sso74-openj9-openshift-rhel8@sha256:4ff9d6342dfd3b85234ea554b92867c649744ece9aa7f8751aae06bf9d2d324csso74-openj9-openshift-rhel8@sha256:4ff9d6342dfd3b85234ea554b92867c649744ece9aa7f8751aae06bf9d2d324cregistry.redhat.io/rh-sso-7/sso74-openshift-rhel8@sha256:b98f0b743dd406be726d8ba8c0437ed5228c7064015c1d48ef5f87eb365522bcsso74-openshift-rhel8@sha256:b98f0b743dd406be726d8ba8c0437ed5228c7064015c1d48ef5f87eb365522bcregistry.redhat.io/rhel8/postgresql-96@sha256:e8177c5de05ccdd6d12e360b65c63c889b2de725d573ffdedd8914230b118639postgresql-96@sha256:e8177c5de05ccdd6d12e360b65c63c889b2de725d573ffdedd8914230b118639registry.redhat.io/rhscl/mongodb-36-rhel7@sha256:9f799d356d7d2e442bde9d401b720600fd9059a3d8eefea6f3b2ffa721c0dc73mongodb-36-rhel7@sha256:9f799d356d7d2e442bde9d401b720600fd9059a3d8eefea6f3b2ffa721c0dc73registry.redhat.io/ubi8/ubi-minimal@sha256:54ef2173bba7384dc7609e8affbae1c36f8a3ec137cacc0866116d65dd4b9afeubi8ubi-minimal@sha256:54ef2173bba7384dc7609e8affbae1c36f8a3ec137cacc0866116d65dd4b9afe
Verification steps
Verify the images have the same digests:
$ skopeo inspect docker://<source-image> $ skopeo inspect docker://<target-registry>/<target-organization>/<target-image>
Additional resources
-
To find the sources of the images list, see the values of the
relatedImagesattribute in the link: - CodeReady Workspaces Operator ClusterServiceVersion sources.
5.3.4. Upgrading CodeReady Workspaces using the CLI management tool in restricted environment
This section describes how to upgrade Red Hat CodeReady Workspaces using the CLI management tool in restricted environment.
Prerequisites
- An administrative account on an OpenShift instance.
-
A running instance version 2.11 of Red Hat CodeReady Workspaces, installed using the CLI management tool on the same instance of OpenShift, with the crwctl
--installer operatormethod, in the<openshift-workspaces>project. See Section 3.4, “Installing CodeReady Workspaces in a restricted environment”. - Essential container images are available to the CodeReady Workspaces server running in the cluster. See Section 5.3.3, “Preparing an private registry”.
-
The
crwctl2.12 management tool is available. See Section 3.3.1, “Installing the crwctl CLI management tool”.
Procedure
- In all running workspaces in the CodeReady Workspaces 2.11 instance, save and push changes back to the Git repositories.
- Stop all workspaces in the CodeReady Workspaces 2.11 instance.
Run the following command:
$ crwctl server:update --che-operator-image=<image-registry>/<organization>/crw-2-rhel8-operator:2.12 -n openshift-workspaces
- <image-registry>: A host name and a port of the container-image registry accessible in the restricted environment.
- <organization>: An organization of the container-image registry. See: Section 5.3.3, “Preparing an private registry”.
Verification steps
- Navigate to the CodeReady Workspaces instance.
- The 2.12 version number is visible at the bottom of the page.
For slow systems or internet connections, add the --k8spodwaittimeout=1800000 flag option to the crwctl server:update command to extend the Pod timeout period to 1800000 ms or longer.
5.4. Upgrading CodeReady Workspaces that uses project strategies other than 'per user'
This section describes how to upgrade CodeReady Workspaces that uses project strategies other than 'per user'.
CodeReady Workspaces intends to use Kubernetes secrets as a storage for all sensitive user data. One project per user simplifies the design of the workspaces. This is the reason why project strategies other than per user become deprecated. The deprecation process happens in two steps. In the First Step project strategies other than per user are allowed but not recommended. In the Second Step support for project strategies other than per user is going to be removed.
No automated upgrade support exists between First Step and Second Step for the installations where project strategies other than per user are used without losing data.
Prerequisites
-
CodeReady Workspaces configured with the project strategies other than
per user. -
Intention to use CodeReady Workspaces configured with the
per usernamespace strategiesper user.
5.4.1. Upgrading CodeReady Workspaces and backing up user data
Procedure
Notify all CodeReady Workspaces users about the upcoming data wipe.
NoteTo back up the data, you can commit workspace configuration to an SCM server and use factories to restore it later.
-
Re-install CodeReady Workspaces with
per usernamespace strategy.
5.4.2. Upgrading CodeReady Workspaces and losing user data
When CodeReady Workspaces is upgraded and user data is not backed up, workspace configuration and user preferences are going to be preserved but all runtime data will be wiped out.
Procedure
- Notify all CodeReady Workspaces users about the upcoming data wipe.
-
Change project strategy to
per user.
Upgrading without backing up user data has disadvantage. Original PVs with runtime data are going to be preserved and will no longer be used. This may lead to the waste of resources.

