Release Notes
Highlighted features and updates related to Red Hat Certificate System 9 (9.0 - 9.7)
Marc Muehlfeld
Petr Bokoč
Filip Hanzelka
Tomáš Čapek
Abstract
Chapter 1. Red Hat Certificate System 9.7
1.1. Hardware Requirements
Minimal Requirements
- CPU: 2 threads
- RAM: 2 GB
- Disk space: 20 GB
Recommended Requirements
- CPU: 4 or more threads, AES-NI support
- RAM: 4 GB or more
- Disk space: 80 GB or more
1.2. Supported Platforms
1.2.1. Server Support
Note
1.2.2. Client Support
- Red Hat Enterprise Linux 7.
- The latest versions of Red Hat Enterprise Linux 5 and 6.Although these platforms do not support Red Hat Certificate System 9.7, those clients can be used with the Token Management System (TMS) system in Red Hat Certificate System 9.7.
1.2.3. Supported Web Browsers
Table 1.1. Supported Web Browsers by Platform
| Platform | Agent Services | End User Pages |
|---|---|---|
| Red Hat Enterprise Linux | Firefox 60 and later [a] | Firefox 60 and later [a] |
| Windows 7 | Firefox 60 and later [a] |
Firefox 60 and later
[a] |
[a]
This Firefox version no longer supports the crypto web object used to generate and archive keys from the browser. As a result, expect limited functionality in this area.
| ||
Note
1.2.4. Supported Smart Cards
- Gemalto TOP IM FIPS CY2 64K token (SCP01)
- Giesecke & Devrient (G&D) SmartCafe Expert 7.0 (SCP03)
- SafeNet Assured Technologies SC-650 (SCP01)
1.2.5. Supported Hardware Security Modules
| HSM | Firmware | Appliance Software | Client Software |
|---|---|---|---|
| nCipher nShield Connect 6000 | 2.61.2 | CipherTools-linux64-dev-12.30.00 | CipherTools-linux64-dev-12.30.00 |
|
Gemalto SafeNet Luna SA 1700 / 7000 (limited)
(Limited support [a] )
| 6.24.0 | 6.2.0-15 | libcryptoki-6.2.x86_64 |
[a]
For details about supported features, see Section 1.2.5.1, “Gemalto SafeNet Luna SA 1700 / 7000 (limited)”.
| |||
1.2.5.1. Gemalto SafeNet Luna SA 1700 / 7000 (limited)
- CL - Cloning Model
- Cloning of symmetric keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Cloning of asymmetric (private) keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Replication of symmetric keys and objects: All symmetric keys and objects are replicated when configured in an HA group
- Replication of asymmetric keys and objects: All asymmetric keys and objects are replicated when configured in an HA group
- Wrapping private (asymmetric) keys off the HSM: Not possible

Figure 1.1. Example of a Cloning Model
- CKE - Key Export Model
- Cloning of symmetric keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Cloning of asymmetric (private) keys and objects: Not possible
- Replication of symmetric keys and objects: All symmetric keys and objects are replicated when configured in an HA group
- Replication of asymmetric keys and objects: Not possible
- Wrapping private (asymmetric) keys off the HSM: Possible
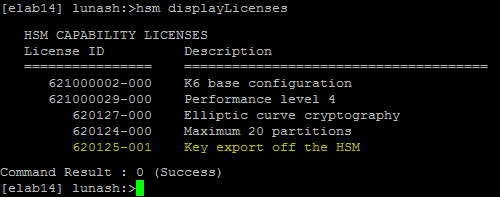
Figure 1.2. Example of a Key Export Model
1.3. Highlighted Updates and New Features
Certificate System packages rebased to version 10.5.18
Highlighted Updates and New Features in the pki-core Package
1.4. Bug Fixes
Missing TPS Auditor group on existing TPS installations
ldapmodify to connect to the LDAP server in question and add the missing object:
$ ldapmodify -x -D "cn=Directory Manager" -w $PASSWORD << EOF
dn: cn=Auditors,ou=Groups,{rootSuffix}
changeType: add
objectClass: top
objectClass: groupOfUniqueNames
cn: Auditors
description: People who can read the signed audit logs for TPS
EOF
{rootSuffix} with the base DN (pki_ds_base_dn) from the TPS configuration file. For example dc=tks,dc=pki,dc={DOMAIN...},dc={TLD}.
Bug Fixes in the pki-core Package
1.5. Deprecated Functionality
SCP01 support in Certificate System has been deprecated
Chapter 2. Red Hat Certificate System 9.6
2.1. Hardware Requirements
Minimal Requirements
- CPU: 2 threads
- RAM: 2 GB
- Disk space: 20 GB
Recommended Requirements
- CPU: 4 or more threads, AES-NI support
- RAM: 4 GB or more
- Disk space: 80 GB or more
2.2. Supported Platforms
2.2.1. Server Support
Note
2.2.2. Client Support
- Red Hat Enterprise Linux 7.
- The latest versions of Red Hat Enterprise Linux 5 and 6.Although these platforms do not support Red Hat Certificate System 9.6, those clients can be used with the Token Management System (TMS) system in Red Hat Certificate System 9.6.
2.2.3. Supported Web Browsers
Table 2.1. Supported Web Browsers by Platform
| Platform | Agent Services | End User Pages |
|---|---|---|
| Red Hat Enterprise Linux | Firefox 60 and later [a] | Firefox 60 and later [a] |
| Windows 7 | Firefox 60 and later [a] |
Firefox 60 and later
[a] |
[a]
This Firefox version no longer supports the crypto web object used to generate and archive keys from the browser. As a result, expect limited functionality in this area.
| ||
Note
2.2.4. Supported Smart Cards
- Gemalto TOP IM FIPS CY2 64K token (SCP01)
- Giesecke & Devrient (G&D) SmartCafe Expert 7.0 (SCP03)
- SafeNet Assured Technologies SC-650 (SCP01)
2.2.5. Supported Hardware Security Modules
| HSM | Firmware | Appliance Software | Client Software |
|---|---|---|---|
| Thales nCipher nShield Connect 6000 | 2.61.2 | CipherTools-linux64-dev-12.30.00 | CipherTools-linux64-dev-12.30.00 |
|
Gemalto SafeNet Luna SA 1700 / 7000 (limited)
(Limited support [a] )
| 6.24.0 | 6.2.0-15 | libcryptoki-6.2.x86_64 |
[a]
For details about supported features, see Section 2.2.5.1, “Gemalto SafeNet Luna SA 1700 / 7000 (limited)”.
| |||
2.2.5.1. Gemalto SafeNet Luna SA 1700 / 7000 (limited)
- CL - Cloning Model
- Cloning of symmetric keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Cloning of asymmetric (private) keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Replication of symmetric keys and objects: All symmetric keys and objects are replicated when configured in an HA group
- Replication of asymmetric keys and objects: All asymmetric keys and objects are replicated when configured in an HA group
- Wrapping private (asymmetric) keys off the HSM: Not possible

Figure 2.1. Example of a Cloning Model
- CKE - Key Export Model
- Cloning of symmetric keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Cloning of asymmetric (private) keys and objects: Not possible
- Replication of symmetric keys and objects: All symmetric keys and objects are replicated when configured in an HA group
- Replication of asymmetric keys and objects: Not possible
- Wrapping private (asymmetric) keys off the HSM: Possible

Figure 2.2. Example of a Key Export Model
2.3. Highlighted Updates and New Features
Certificate System packages rebased to version 10.5.17
2.4. Bug Fixes
Certificate System now fully supports AES key derivation for SCP03
Bug Fixes in the pki-core Package
2.5. Deprecated Functionality
SCP01 support in Certificate System has been deprecated
Chapter 3. Red Hat Certificate System 9.5
3.1. Hardware Requirements
Minimal Requirements
- CPU: 2 threads
- RAM: 2 GB
- Disk space: 20 GB
Recommended Requirements
- CPU: 4 or more threads, AES-NI support
- RAM: 4 GB or more
- Disk space: 80 GB or more
3.2. Supported Platforms
3.2.1. Server Support
Note
3.2.2. Client Support
- Red Hat Enterprise Linux 7.
- The latest versions of Red Hat Enterprise Linux 5 and 6.Although these platforms do not support Red Hat Certificate System 9.5, those clients can be used with the Token Management System (TMS) system in Red Hat Certificate System 9.5.
3.2.3. Supported Web Browsers
Table 3.1. Supported Web Browsers by Platform
| Platform | Agent Services | End User Pages |
|---|---|---|
| Red Hat Enterprise Linux | Firefox 60 and later [a] | Firefox 60 and later [a] |
| Windows 7 | Firefox 60 and later [a] |
Firefox 60 and later
[a] |
[a]
This Firefox version no longer supports the crypto web object used to generate and archive keys from the browser. As a result, expect limited functionality in this area.
| ||
Note
3.2.4. Supported Smart Cards
- Gemalto TOP IM FIPS CY2 64K token (SCP01)
- Giesecke & Devrient (G&D) SmartCafe Expert 7.0 (SCP03)
- SafeNet Assured Technologies SC-650 (SCP01)
3.2.5. Supported Hardware Security Modules
| HSM | Firmware | Appliance Software | Client Software |
|---|---|---|---|
| Thales nCipher nShield Connect 6000 | 2.61.2 | CipherTools-linux64-dev-12.30.00 | CipherTools-linux64-dev-12.30.00 |
|
Gemalto SafeNet Luna SA 1700 / 7000 (limited)
(Limited support [a] )
| 6.24.0 | 6.2.0-15 | libcryptoki-6.2.x86_64 |
[a]
For details about supported features, see Section 3.2.5.1, “Gemalto SafeNet Luna SA 1700 / 7000 (limited)”.
| |||
3.2.5.1. Gemalto SafeNet Luna SA 1700 / 7000 (limited)
- CL - Cloning Model
- Cloning of symmetric keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Cloning of asymmetric (private) keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Replication of symmetric keys and objects: All symmetric keys and objects are replicated when configured in an HA group
- Replication of asymmetric keys and objects: All asymmetric keys and objects are replicated when configured in an HA group
- Wrapping private (asymmetric) keys off the HSM: Not possible

Figure 3.1. Example of a Cloning Model
- CKE - Key Export Model
- Cloning of symmetric keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Cloning of asymmetric (private) keys and objects: Not possible
- Replication of symmetric keys and objects: All symmetric keys and objects are replicated when configured in an HA group
- Replication of asymmetric keys and objects: Not possible
- Wrapping private (asymmetric) keys off the HSM: Possible

Figure 3.2. Example of a Key Export Model
3.3. Highlighted Updates and New Features
Certificate System packages rebased to version 10.5.16
Highlighted Updates and New Features in the pki-core Package
3.4. Bug Fixes
Bug Fixes in the pki-core Package
3.5. Deprecated Functionality
SCP01 support in Certificate System has been deprecated
Chapter 4. Red Hat Certificate System 9.4
4.1. Hardware Requirements
Minimal Requirements
- CPU: 2 threads
- RAM: 2 GB
- Disk space: 20 GB
Recommended Requirements
- CPU: 4 or more threads, AES-NI support
- RAM: 4 GB or more
- Disk space: 80 GB or more
4.2. Supported Platforms
4.2.1. Server Support
Note
4.2.2. Client Support
- Red Hat Enterprise Linux 7.
- The latest versions of Red Hat Enterprise Linux 5 and 6.Although these platforms do not support Red Hat Certificate System 9.4, those clients can be used with the Token Management System (TMS) system in Red Hat Certificate System 9.4.
4.2.3. Supported Web Browsers
Table 4.1. Supported Web Browsers by Platform
| Platform | Agent Services | End User Pages |
|---|---|---|
| Red Hat Enterprise Linux | Firefox 60 and later [a] | Firefox 60 and later [a] |
| Windows 7 | Firefox 60 and later [a] |
Firefox 60 and later
Internet Explorer 10 [b]
|
[a]
This Firefox version no longer supports the crypto web object used to generate and archive keys from the browser. As a result, expect limited functionality in this area.
[b]
Internet Explorer 11 is currently not supported by Red Hat Certificate System 9 because the enrollment code for this web browser depends upon Visual Basic Script, which has been deprecated in Internet Explorer 11.
| ||
Note
4.2.4. Supported Smart Cards
- Gemalto TOP IM FIPS CY2 64K token (SCP01)
- Giesecke & Devrient (G&D) SmartCafe Expert 7.0 (SCP03)
- SafeNet Assured Technologies SC-650 (SCP01)
4.2.5. Supported Hardware Security Modules
| HSM | Firmware | Appliance Software | Client Software |
|---|---|---|---|
| Thales nCipher nShield Connect 6000 | 2.61.2 | CipherTools-linux64-dev-12.30.00 | CipherTools-linux64-dev-12.30.00 |
|
Gemalto SafeNet Luna SA 1700 / 7000 (limited)
(Limited support [a] )
| 6.24.0 | 6.2.0-15 | libcryptoki-6.2.x86_64 |
[a]
For details about supported features, see Section 4.2.5.1, “Gemalto SafeNet Luna SA 1700 / 7000 (limited)”.
| |||
4.2.5.1. Gemalto SafeNet Luna SA 1700 / 7000 (limited)
- CL - Cloning Model
- Cloning of symmetric keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Cloning of asymmetric (private) keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Replication of symmetric keys and objects: All symmetric keys and objects are replicated when configured in an HA group
- Replication of asymmetric keys and objects: All asymmetric keys and objects are replicated when configured in an HA group
- Wrapping private (asymmetric) keys off the HSM: Not possible

Figure 4.1. Example of a Cloning Model
- CKE - Key Export Model
- Cloning of symmetric keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Cloning of asymmetric (private) keys and objects: Not possible
- Replication of symmetric keys and objects: All symmetric keys and objects are replicated when configured in an HA group
- Replication of asymmetric keys and objects: Not possible
- Wrapping private (asymmetric) keys off the HSM: Possible

Figure 4.2. Example of a Key Export Model
4.3. Highlighted Updates and New Features
Certificate System packages rebased to version 10.5.9
Highlighted Updates and New Features in the pki-core Package
4.4. Bug Fixes
Server-side key generation succeeds with only one identity type certificate
Bug Fixes in the pki-core Package
4.5. Deprecated Functionality
SCP01 support in Certificate System has been deprecated
Chapter 5. Red Hat Certificate System 9.3
5.1. Supported Platforms
5.1.1. Server Support
Note
5.1.2. Client Support
- Red Hat Enterprise Linux 7.
- The latest versions of Red Hat Enterprise Linux 5 and 6.Although these platforms do not support Red Hat Certificate System 9.3, those clients can be used with the Token Management System (TMS) system in Red Hat Certificate System 9.3.
5.1.3. Supported Web Browsers
Table 5.1. Supported Web Browsers by Platform
| Platform | Agent Services | End User Pages |
|---|---|---|
| Red Hat Enterprise Linux | Firefox 52 and later [a] | Firefox 52 and later [a] |
| Windows 7 | Firefox 52 and later [a] |
Firefox 52 and later
Internet Explorer 10 [b]
|
[a]
This Firefox version no longer supports the crypto web object used to generate and archive keys from the browser. As a result, expect limited functionality in this area.
[b]
Internet Explorer 11 is currently not supported by Red Hat Certificate System 9 because the enrollment code for this web browser depends upon Visual Basic Script, which has been deprecated in Internet Explorer 11.
| ||
Note
5.1.4. Supported Smart Cards
- Gemalto TOP IM FIPS CY2 64K token (SCP01)
- Giesecke & Devrient (G&D) SmartCafe Expert 6.0 (SCP03)
- SafeNet Assured Technologies SC-650 (SCP01)
5.1.5. Supported Hardware Security Modules
| HSM | Firmware | Appliance Software | Client Software |
|---|---|---|---|
| Thales nCipher nShield Connect 6000 | 2.61.2 | CipherTools-linux64-dev-12.30.00 | CipherTools-linux64-dev-12.30.00 |
|
Gemalto SafeNet Luna SA 1700 / 7000 (limited)
(Limited support [a] )
| 6.24.0 | 6.2.0-15 | libcryptoki-6.2.x86_64 |
[a]
For details about supported features, see Section 5.1.5.1, “Gemalto SafeNet Luna SA 1700 / 7000 (limited)”.
| |||
5.1.5.1. Gemalto SafeNet Luna SA 1700 / 7000 (limited)
- CL - Cloning Model
- Cloning of symmetric keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Cloning of asymmetric (private) keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Replication of symmetric keys and objects: All symmetric keys and objects are replicated when configured in an HA group
- Replication of asymmetric keys and objects: All asymmetric keys and objects are replicated when configured in an HA group
- Wrapping private (asymmetric) keys off the HSM: Not possible

Figure 5.1. Example of a Cloning Model
- CKE - Key Export Model
- Cloning of symmetric keys and objects: Possible to other Luna SAs/G5 or Luna Backup HSM
- Cloning of asymmetric (private) keys and objects: Not possible
- Replication of symmetric keys and objects: All symmetric keys and objects are replicated when configured in an HA group
- Replication of asymmetric keys and objects: Not possible
- Wrapping private (asymmetric) keys off the HSM: Possible

Figure 5.2. Example of a Key Export Model
5.2. Highlighted Updates and New Features
Certificate System packages rebased to version 10.5.1
Certificate System is now RFC 5272-compliant
- The identity proof by signing with another certificate owned by the same entity to support enrollment, renewal, and revocation
- The
IdentityProof V2control with Shared Secret for both enrollment and revocation - The identification control to support Shared Secret
- The
EncryptedPOPandDecryptedPOPcontrols for non-signing certificates - The
POPLinkWitnessV2control - The TLS client authentication enforcement for user-signed CMC requests
- The
CMCStatusInfoV2response
CMCRequest and CMCResponse utilities have been updated to support these new features, and the CMCSharedToken utility has been introduced to support the CMC Shared Secret feature.
Highlighted Updates and New Features in the pki-core Package
5.3. Bug Fixes
In-place update of the TPS subsystem now adds the externalRegISEtoken profile to the CS.cfg file
externalRegISEtoken Token Processing System (TPS) profile to the default /usr/share/pki/tps/conf/CS.cfg TPS configuration file. However, the new configuration was not added to the /var/lib/pki/pki-instance_name/tps/conf/CS.cfg file when an administrator performed an in-place upgrade of an older TPS system. Consequently, upgraded TPS systems did not use the new configuration. This update fixes the problem. As a result, the token profile is now added automatically to the TPS configuration when performing an in-place upgrade.
Bug Fixes in the pki-core Package
5.4. Known Issues
Known Issues in the pki-core Package
Chapter 6. Red Hat Certificate System 9.2
6.1. Supported Platforms
6.1.1. Server and Client Support
6.1.2. Supported Web Browsers
Note
Table 6.1. Supported Web Browsers by Platform
| Platform | Agent Services | End User Pages |
|---|---|---|
| Red Hat Enterprise Linux | Firefox 38 and later | Firefox 38 and later |
| Windows 7 | Firefox 40 and later |
Firefox 40 and later
Internet Explorer 10
|
| Windows Server 2012 | Firefox 40 and later |
Firefox 40 and later
|
Warning
crypto web object used to generate and archive keys from the browser. As a result, expect limited functionality in this area.
Note
6.1.3. Supported Smart Cards
- Gemalto TOP IM FIPS CY2 64K token, both as a smart card and GemPCKey USB form factor key
- SafeNet Assured Technologies Smart Card 650 (SC-650), with support for SCP01
- G&D Smart Cafe 6.0 for SCP03
6.1.4. Supported HSM
| HSM | Firmware | Appliance Software | Client Software |
|---|---|---|---|
| nCipher nShield connect 6000 | 0.4.11cam2 | CipherTools-linux64-dev-11.70.00 | CipherTools-linux64-dev-11.70.00 |
| Gemalto SafeNet Luna SA 1700 | 6.22.0 | 6.0.0-41 | libcryptoki-5.4.1-2.x86_64 |
6.2. Highlighted Updates and New Features
Important
New audit events have been added for SSL/TLS session events on Red Hat Certificate System servers
SSL and TLS session events, namely successful and unsuccessful connection establishments and connection terminations.
- ACCESS_SESSION_ESTABLISH_SUCCESS for successful connections
- ACCESS_SESSION_ESTABLISH_FAILURE for failed connections
- ACCESS_SESSION_TERMINATED for terminated connections
CS.cfg file to further configure these settings. (BZ#1404080)
Red Hat Certificate System can now display a custom banner at the start of a secure connection
SSL or TLS connection. The connecting user will be prompted to confirm they read the banner before resuming normal client operation.
/etc/pki/pki-tomcat/banner.txt and place the message you want to display into this file. Make sure the file is encoded as UTF-8 and readable by the pkiuser user account. To remove the banner, delete the aforementioned file. No server restart is required to add, change, or remove the banner. (BZ#1404085)
New tools to retrieve audit logs from Red Hat Certificate System server
pki <subsystem>-audit-file-find
pki <subsystem>-audit-file-retrieve <filename>
grep to search for specific log entries, and the AuditVerify tool to verify their authenticity. For more information on these tools, see their respective man pages. (BZ#1417307)
New session timeout parameter for PKI Console
keepAliveTimeout, has been added to Certificate System's server configuration file. This parameter controls the session timeout period for PKI Console. PKI Console will be automatically disconnected from the server after it has been idle for a time period specified in this parameter; the Console will then display an error message and terminate.
server.xml file, and accepts an integer which specifies the timeout period in miliseconds. The default value is 300000, which is 5 minutes. (BZ#1446877)
Certificate System now supports SCP03-enabled tokens
6.3. Bug Fixes
Important
Token memory is now cleaned after the deletion of keys and certificates
Chapter 7. Red Hat Certificate System 9.1
7.1. Supported Platforms
7.1.1. Server and Client Support
7.1.2. Supported Web Browsers
Note
Table 7.1. Supported Web Browsers by Platform
| Platform | Agent Services | End User Pages |
|---|---|---|
| Red Hat Enterprise Linux | Firefox 38 and later | Firefox 38 and later |
| Windows 7 | Firefox 40 and later |
Firefox 40 and later
Internet Explorer 10
|
| Windows Server 2012 | Firefox 40 and later |
Firefox 40 and later
|
Warning
crypto web object used to generate and archive keys from the browser. As a result, expect limited functionality in this area.
Note
7.1.3. Supported Smart Cards
- Gemalto TOP IM FIPS CY2 64K token, both as a smart card and GemPCKey USB form factor key
- SafeNet Assured Technologies Smart Card 650 (SC-650), with support for both SCP01 and SCP02
7.1.4. Supported HSM
| HSM | Firmware | Appliance Software | Client Software |
|---|---|---|---|
| nCipher nShield connect 6000 | 0.4.11cam2 | CipherTools-linux64-dev-11.70.00 | CipherTools-linux64-dev-11.70.00 |
| Gemalto SafeNet Luna SA 1700 | 6.22.0 | 6.0.0-41 | libcryptoki-5.4.1-2.x86_64 |
7.2. Note on Token Processing System Upgrades
7.3. Highlighted Updates and New Features
Important
New Java-based Token Processing System
Note
Global Platform 2.1.1 in the Token Processing System
gp211 applet has been introduced that provides support for Secure Channel Protocol 02 (SCP02). SCP02 has been tested with SafeNet Assured Technologies Smart Card 650.
Note
Certificate System now supports setting SSL ciphers for individual installation
SSL cipher using a two-step installation, which avoids this problem.
- Prepare a deployment configuration file that includes the
pki_skip_configuration=Trueoption. - Pass the deployment configuration file to the
pkispawncommand to start the initial part of the installation. - Set the ciphers in the
sslRangeCiphersoption in the/var/lib/pki/instance/conf/server.xmlfile. Replace instance with the instance name. - Replace the
pki_skip_configuration=Trueoption set in the first step withpki_skip_installation=Truein the deployment configuration file. - Run the same
pkispawncommand to complete the installation.
Man pages updates
Certificate System now uses a specific JDK and version and no longer supports alternatives
/usr/sbin/alternatives mechanism. Instead, Red Hat Certificate System 9.1 always uses its own specified JDK and version. For Red Hat Certificate System 9.1, this JDK is java-1.8.0-openjdk, and the version is 1:1.8.0.
7.4. Bug Fixes
Important
Installing the redhat-pki package no longer requires the Server-optional repository
Server-optional repository. Therefore, installation failed on systems where this repository was not enabled.
Server-optional repository is not required in order to install redhat-pki. The jss-javadoc package is still only provided by Server-optional, which must be enabled using Subscription Manager before you can install the package.
7.5. Known Issues
Important
CRL cannot be configured in console to update after every revocation or release from hold unless grace period is set
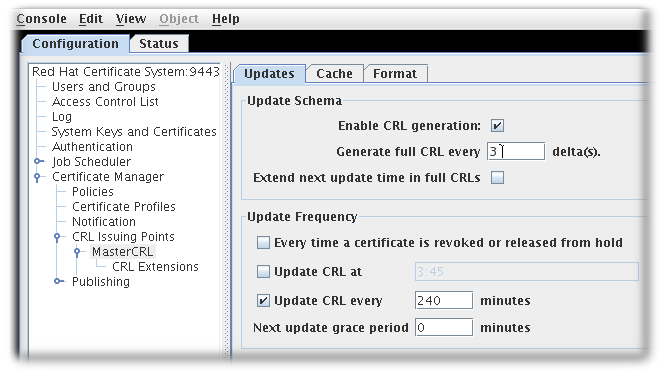
Firefox can no longer enroll a signing and an archival certificate at the same time
caDualCert.cfg profile previously used the Mozilla cryptographic object to create two requests, one for a signing certificate and the other for an encryption certificate, with private key archival specified for the encryption certificate. Since Mozilla has removed the generateCRMFRequest() object, Red Hat Certificate System can no longer support this type of enrollment within the browser.
pki command line interface (CLI) tools. It describes manual user signing and encryption certificates enrollment.
- Enroll for the signing-only certificate:
- Create the certificate signing request (CSR) using
certutil:certutil -R -k rsa -g 2048 -s "CN=John Smith,O=Example Corp,L=Mountain View,ST=California,C=US" -d ./ -a -o cert.cer
- Send the request to the Certificate Authority (CA) using the
caSigningUserCertprofile:pki ca cert-request-submit --csr-file ./cert.cer --profile caSigningUserCert --subject "CN=John Smith,O=Example Corp,L=Mountain View,ST=California,C=US"
- The final certificate can be retrieved using the standard end entity (EE) graphical user interface of the product:
- Enroll for the encryption-only certificate:
- Obtain the transport certificate from the Key Recovery Authority (KRA):
pki -C "" -U 'https://localhost:8443/ca' cert-show 0x07 --encoded --output transport.pem
- One can make sure that certificate
0x07is actually the transport certificate for the KRA by consulting the end entity interface of the product. If the certificate happens to have a different ID, use that one instead of0x07. - Use the
CRMFPopClientcommand to create the CSR for the encryption certificate that will have the private key archived to the KRA.Here we use thecaEncUserCertprofile to obtain this certificate:CRMFPopClient -d . -p password "secret123" -o csr -a rsa -l 2048 -n "UID=username" -f caEncUserCert -b transport.pem
- Get the enrollment template for the
caEncUserCertprofile:pki -v -C "secret123" -U https://localhost:8443/ca cert-request-profile-show caEncUserCert --output encuser.xml
- Sanitize the line endings in the
csrfile you just created:dos2unix csr
- Fill in the enrollment template as follows:
cert_request_type = crmf cert_request = <copied certificate request blob from the file csr> sn_cn = <your cn value>
- Submit the final request to the CA:
pki -v -C "secret123" -U https://localhost.localdomain:8443/ca cert-request-submit encuser.xml
caUserCert profile request using Internet Explorer 10 results in an Invalid request error
caUserCert profile using Internet Explorer 10 from Windows 7, the request results in the "Invalid request" error. The following procedure specifies how to work around this problem.
- Go to the Internet Options/Advanced/Security section and uncheck the TLS 1.2 box to connect to the SSL port.
- Go to the End Entity page which allows downloading and importing the CA certificate chain. Add the CA certificate to the Trusted CAs list.
- Go to Internet Options and enter the Security tab. Add the SSL url to the Trusted Sites list. Set the security slider to medium high or, alternatively, choose medium or below if trying to troubleshoot problems.
- Go to the Compatibility View Settings settings by clicking the Tools dropdown menu on the right and add the site to the list. Alternatively, enable the view for intranet sites or all sites.
- Go to the usual dual use profile enrollment page. The browser will probably issue a warning that a cryptographic operation is about to occur. Accept that by clickign OK. At this point the display should have a drop down list next to the key size list that contains the Communication Service Providers (CSPs). If this list is not empty, attempt an enrollment.
The console does not enable a separate ticking of the Update CRL every time a certificate is revoked or released from hold option

Additional steps needed when uninstalling TPS
pkidestroy(8) man page for instructions.
Chapter 8. Red Hat Certificate System 9.0
8.1. Supported Platforms
8.1.1. Server and Client Support
8.1.2. Supported Web Browsers
Note
Table 8.1. Supported Web Browsers by Platform
| Platform | Agent Services | End User Pages |
|---|---|---|
| Red Hat Enterprise Linux | Firefox 38 and later | Firefox 38 and later |
| Windows 7 | Firefox 40 and later |
Firefox 40 and later
Internet Explorer 10
|
| Windows Server 2012 | Firefox 40 and later |
Firefox 40 and later
|
Warning
crypto web object used to generate and archive keys from the browser. As a result, expect limited functionality in this area.
Note
8.1.3. Supported Smart Cards
- Gemalto TOP IM FIPS CY2 64K token, both as a smart card and GemPCKey USB form factor key
- SafeNet Assured Technologies Smart Card 650 (SC-650), with support for both SCP01 and SCP02
8.1.4. Supported HSM
| HSM | Firmware | Appliance Software | Client Software |
|---|---|---|---|
| nCipher nShield connect 6000 | 0.4.11cam2 | CipherTools-linux64-dev-11.70.00 | CipherTools-linux64-dev-11.70.00 |
| Gemalto SafeNet Luna SA 1700 | 6.22.0 | 6.0.0-41 | libcryptoki-5.4.1-2.x86_64 |
8.2. Installing Red Hat Certificate System Subsystems
- Install a Red Hat Enterprise Linux 7.1 server with an active network connection.
Note
While not required, for most real-world deployments, the recommended approach is to install the Red Hat Directory Server and the Red Hat Certificate System on separate machines with Red Hat Enterprise Linux 7.1 installed. If separate machines are used in the deployment, unless otherwise noted, execute the following command sequences on both machines. - Subscribe the system using Red Hat Subscription Manager and attach the subscription providing Red Hat Certificate System:
# subscription-manager register # subscription-manager list --available --all
Make note of the pool ID providing Red Hat Certificate System. In addition, all certificate subsystems also require access to Red Hat Directory Server:# subscription-manager attach --pool=POOL_ID_CERT_SYSTEM # subscription-manager attach --pool=POOL_ID_DIR_SERVER
For the machine where the certificate system resides, also make sure to attach the subscription for the Red Hat Enterprise Linux Server, and then enable the Red Hat Enterprise Linux Optional repository:# subscription-manager attach --pool=POOL_ID_Red_Hat_Enterprise_Linux_Server # subscription-manager repos --enable rhel-7-server-optional-rpms
- Enable the certificate system and directory server repositories.
- Enable the certificate server repository on the machine where it will reside:
# subscription-manager repos --enable=rhel-7-server-rhcs-9-rpms
- Enable the directory server repository on the machine where it will reside:
# subscription-manager repos --enable=rhel-7-server-rhds-10-rpms
- Before continuing, make sure that the latest updates have been applied to each Red Hat Enterprise Linux 7.1 system you use:
# yum update
- On the machine where it will reside, install the directory server packages:
# yum install redhat-ds
- Ensure that a real domain name is specified in each
/etc/resolv.conffile and that a host name is set within each/etc/hostsfile. - On the machine where it will reside, run the directory server installation script, selecting the defaults or customizing as required:
# /usr/sbin/setup-ds-admin.pl
- On the machine where it will reside, install the certificate system packages:
# yum install redhat-pki
- On the machine where the certificate server resides, run the
pkispawnscript to create and configure the subsystem instances. At least one CA subsystem must be installed and fully configured before any other type of subsystem can be configured. For details, see the pkispawn man page. - To access the agent interface of various Red Hat Certificate System subsystems, use a properly configured local or remote Mozilla Firefox web browser.
8.2.1. Verifying JDK Version
yum or by downloading the packages directly from http://openjdk.java.net/install/. For example:
# yum install java-1.7.0-openjdk
/usr/sbin/alternatives as root to ensure that the proper JDK is available and selected in order to use Red Hat Certificate System 9:
# /usr/sbin/alternatives --config java There are 3 programs which provide 'java'. Selection Command ----------------------------------------------- 1 /usr/lib/jvm/jre-1.4.2-gcj/bin/java + 2 /usr/lib/jvm/jre-1.7.0-openjdk/bin/java * 3 /usr/lib/jvm/jre-1.6.0-sun.x86_64/bin/java
/usr/sbin/alternatives command to configure the appropriate selection if it has not already been selected.
8.2.2. Installing through yum
# yum install pki-subsystem
cafor the Certificate Manager.krafor the Key Recovery Authority.ocspfor the Online Certificate Status Protocol Responder.tksfor the Token Key System.tpsfor the Token Processing System.consolefor the Java console.
# yum install redhat-pki
8.2.3. Installing from an ISO image
RPMS/ directory which can be used as a local yum repository.
# subscription-manager attach --pool=POOL_ID_Red_Hat_Enterprise_Linux_Server # subscription-manager repos --enable rhel-7-server-optional-rpms
RPMS/ directory on a web server and then configure yum to use that location as a repository. After that, install Red Hat Certificate System as described in Section 8.2.2, “Installing through yum”.
8.3. Highlighted Updates and New Features
Red Hat Certificate System 9.0 on Red Hat Enterprise Linux 7.1 requires packages from the Optional repository
Optional repository. These are the required packages:
resteasy-base-client >= 3.0.6-1 is needed by pki-base-10.2.4-2.el7.noarch resteasy-base-jackson-provider >= 3.0.6-1 is needed by pki-base-10.2.4-2.el7.noarch libsvrcore.so.0()(64bit) is needed by pki-tps-10.2.4-2.el7.x86_64 jss-javadoc >= 4.2.6-35 is needed by redhat-pki-10.2.4-1.el7.noarch nuxwdog-client-java >= 1.0.1-11 is needed by pki-server-10.2.4-2.el7.noarch
Note
Optional repository.
A New pki Command-line Utility
pki command-line utility that provides an interface to access PKI services on a PKI server. The main purpose of the utility is to:
- allow commonly used CA and KRA functionality to be usable from the command line for end users and for simple scripting and automation purposes.
- allow use of the new REST API operations from the command line.
pki utility, see the pki man page.
Simplified Installation and Deployment
- Simplify silent installation by using INI-like configuration files instead of command-line arguments
- Instance creation and configuration can be performed in a single automated operation
- Multiple subsystems can be deployed in a single Tomcat instance.
Technology Preview: Global Platform 2.1.1 in TPS
Note
gp211 applet has been introduced that provides support for Secure Channel Protocol 02 (SCP02). SCP02 has been tested with SafeNet Assured Technologies Smart Card 650.
REST Web Service APIs
Technology Preview: New Java-based Token Processing System
Note
KRA Enhancements
Support for KRA Transport Key Rotation
External Authorization LDAP Server
Adding SAN to a Server Certificate during Installation
pkispawn configuration.
Common Criteria Evaluation
The PKI Configuration Has Been Removed from the GUI-based Installation Wizard
pkispawn utility.
8.4. Known Issues
- BZ#1041414
- Due to a bug, Certificate System sets an incorrect CA profile ID when you install a TPS. To work around the problem, manually set the
op.enroll.delegateISEtoken.keyGen.encryption.ca.profileIdparameter in the/var/lib/pki/instance_name/tps/conf/CS.cfgfile tocaTokenUserDelegateAuthKeyEnrollment:op.enroll.delegateISEtoken.keyGen.encryption.ca.profileId=caTokenUserDelegateAuthKeyEnrollment
- BZ#1256901
- When certain HSMs are used while
TLS_ECDHE_RSA_*ciphers are enabled, subsystems experience communication problems. The issue occurs in the following scenarios:- When a CA has been installed and a second subsystem is being installed and tries to contact the CA as a security domain, thus preventing the installation from succeeding.
- While performing a certificate enrollment on the CA, when archival is required, the CA encounters the same communication problem with the KRA. This scenario can only occur if the offending ciphers were temporarily disabled for the installation.
To work around this problem, keep theTLS_ECDHE_RSA_*ciphers turned off if possible. Note that while the Perfect Forward Secrecy provides added security by using theTLS_ECDHE_RSA_*ciphers, each SSL session takes about three times longer to establish. Also, the defaultTLS_RSA_*ciphers are adequate for the Certificate System operations. - issue tracked upstream
- Red Hat Certificate System 9 provides SCEP enrollment using RSA transport certificates only. If ECC certificates are required to be issued using SCEP, the administrator should set up an RSA system certificate to be used for transporting purposes, instead of the CA signing certificate.
- BZ#1202527
- If a CUID provided by a client is not properly converted in format, the
tokenTypeandkeySetmapping resolver framework sometimes fails to evaluate properly the mapping filter for the CUID range (tokenCUID.start / tokenCUID.end). - BZ#1256984
- Currently, the External Registration Recovery does not calculate the size of each key to recover individually and only works properly for 1024-bit keys by default. For example, at attempt to recover a certificate with a 2048-bit private key will fail.To work around this problem, add the following setting to the
externalRegAddToTokenprofile in theCS.cfgfile:op.enroll.externalRegAddToToken.keyGen.encryption.keySize=2048
This configuration will work if all the requiredcertificates to add have keys of the same size. - BZ#1255963
- When using the latest TPS applet version that supports
scp01smart cards, format operations fail on the SafeNet 330 Java (330J) smart card.Note that the TPS server is currently offered as a Technology Preview and is not yet fully supported under subscription agreements. - BZ#1202526
- Token terminations force revocation of all certificates on the token and previously, there was little ability to customize that process. Red Hat Certificate System adds granular control over operations performed on certificates. However, in order to work properly, this feature requires the following list of parameters to be added to the TPS
CS.cfgfile for all token types:op.enroll.tokenType.keyGen.keyType.recovery.terminated.revokeCert op.enroll.tokenType.keyGen.keyType.recovery.terminated.revokeCert.reason op.enroll.tokenType.keyGen.keyType.recovery.terminated.scheme
The above parameters ensure that theterminatedandkeyCompromisestates can be configured to have different revocation reasons.op.enroll.tokenType.keyGen.keyType.recovery.endState.holdRevocationUntilLastCredential = true/false
The above set of new parameters for each token allows to set behavior so that if a certificate is shared by multiple tokens, then that certificate is not revoked until the last token containing that certificate is terminated or lost. If the certificate is finally revoked on the last token, then the status of all the other tokens is set torevokedas well.op.enroll.tokenType.keyGen.keyType.recovery.state.revokeExpiredCerts = true/false
The above set of new parameters for each token type allows to set behavior so that expired certificates do not get revoked. - BZ#1255192
- In Certificate Manager - Certificate Profiles, if you select a Profile instance that is disabled and click Edit/View to get the Certificate Profile Rule Editor window, changes to the inputs are not applied as they should.
- BZ#1253502
- When a
caDirUserCertcertificate is issued, the job notification email is not sent when the job notification for issued certificates is enabled. - BZ#1252952
- When using a SCP02 token with the
gp211Coolkey applet, which is currently offered as a technology preview, attempting a re-enroll operation results in a failure near the end of the process.To work around this problem, perform a format operation before re-enrolling. - BZ#1254804
- CRMF key generation request types are no longer supported in Firefox 33, 35 or later. As a consequence, it is no longer possible to perform browser-based enrollments, particularly in the key archival functionality. Note that limited support for simple keygen-based enrollments now exists for the profiles not performing key archival.To work around this problem, perform enrollments through the
pkiCLI utility. In Red Hat Certificate System 9, theclient-cert-requestcommand supports both PKCS #10 and CRMF certificate requests. To generate and submit a CRMF certificate request with key archival, first download the transport certificate:# pki cert-find --name "<KRA Transport certificate's subject common name>" # pki cert-show serial_number --output transport.pem
Then, submit the certificate request:# pki -c password client-init # pki -c password client-cert-request subject_DN --profile caDualCert --type crmf --transport transport.pem
- BZ#1257670
- When a CA with KRA is installed and an archival attempt through archival-enabled CA profile is made, if the connection between CA and KRA was attempted with the user
pkidbuserinstead of the subsystem user, the archival attempt fails.To work around this problem, add thepkidbuseruser to the Trusted Managers group. - BZ#1244965
- The synchronous key recovery mechanism has been deprecated in Red Hat Certificate System 9. Red Hat recommends to use asynchronous key recovery instead.
- BZ#1250741
- When cloning a CA and the master CA having
serialCloneTransferNumber=0set, thepkispawnutility currently does not return a proper error message as it should. - BZ#1255431
- An incompatibility with the authentication plug-in interface protocol has resulted in the
UdnPwdDirAuthplug-in not working properly in Red Hat Certificate System 9.0, so that this plug-in cannot be placed in any profile at this time. - BZ#1250734
- When cloning a CA, if the serial number range is less than the value of
serialCloneTransferNumber, thepkispawnutility terminates with an exception rather than returning a proper error message. - BZ#1252621
- The
pkispawnutility uses the following default ports as defined in/etc/pki/default.cfg:pki_https_port=8443 pki_http_port=8080
Whilepkispawnallows for highly flexible customizations, any attempt to override the default port values using ports that have been pre-allocated for other uses may cause installation or configuration to fail with error messages similar to the following:pkispawn : DEBUG ....... Error Type: Exception pkispawn : DEBUG ....... Error Message: port 9180 has invalid selinux context pki_ca_port_t
The availability of a given port can be checked by running the following commands:# semanage port -l | grep 9180 pki_ca_port_t tcp 829, 9180, 9701, 9443-9447 # semanage port -l | grep 18443 (if the port is unused, nothing will be displayed)
Note
Red Hat Certificate System 9 primarily uses thehttp_port_tSELinux context, even though the default HTTP port 8080 useshttp_cache_port_t. The following ports and their SELinux contexts were added to the system policy for previous versions of Red Hat Certificate System, and as such, cannot be used for Red Hat Certificate System 9:# semanage port -l | grep pki pki_ca_port_t tcp 829, 9180, 9701, 9443-9447 pki_kra_port_t tcp 10180, 10701, 10443-10446 pki_ocsp_port_t tcp 11180, 11701, 11443-11446 pki_ra_port_t tcp 12888-12889 pki_tks_port_t tcp 13180, 13701, 13443-13446 pki_tps_port_t tcp 7888-7889
- BZ#1246635
- The
pki user-cert-addcommand provides an option to import the user certificate directly from CA. However, this option does not work properly if the command is executed over SSL port due to incorrect client library initialization. Consequently, the command fails with the following error message:javax.net.ssl.SSLPeerUnverifiedException: peer not authenticated.
To work around this problem, download the certificate from CA into a file using thepki cert-showcommand, then upload the certificate from a file using thepki user-cert-addcommand. - BZ#1247410
- Currently, the
ocspResponderURLconfiguration parameter does not work when it uses a HTTPS secure port. Consequently, trying to enable OCSP checking from the KRA (Key Recovery Authority) subsystem using CA's secure port causes self tests to fail during KRA restart.To work around this problem, you can safely use an insecure HTTP port because the response is signed and time-stamped. - BZ#1251581
- When an enrollment request is submitted using the End-Entity page using the
Manual User Signing & Encryption Certificates Enrollmentprofile, the CA will generate both encryption and signing certificates. However, when the request is submitted using theCRMFPopClientorpkiutilities, the CA only generates the encryption certificate.To work around this problem, the signing certificate can be requested separately. - BZ#1231261
- The
pkispawnutility has an interactive mode to primarily help users deploy the most straightforward configurations, and become familiar with Red Hat Certificate System. Therefore,pkispawndoes not currently provide an interactive session for HSM, cloning subsystems, sub-CA, and externally signed CA.As a temporary relief, the user is properly informed during the interactivepkispawnsession as to which functionality is not yet supported, to prevent any confusion from other related error messages. - BZ#753311
- When restarting the CA, SELinux returns AVC denied error messages.The CA ultimately restarts properly, so these errors can be ignored.
- BZ#699456
- If an administrator creates a custom log type, any modifications made to the file or to the log file configuration is not recorded in the audit log. This means that the log file is not secure .
- BZ#693412
- Using the KRA agent's page to search for pending recovery requests does not return the list of pending requests.Search for the specific recovery request by using the reference number given when the recovery request was submitted. Searching by the reference number successfully returns the recovery request record. From there, the request can be approved by clicking the Grant button.
- BZ#678320
- Resetting the password on a token with an applet upgrade operation does not work properly. Both the password reset operation and the applet upgrade operation fail.To work around this problem, disable applet upgrade in the PIN reset profile.
- BZ#673182
- ECC keys are not supported for signing audit logs. Neither the servers nor the
AuditVerifyutility support ECC keys for signed audit log files.To work around this problem, use RSA keys for signing audit logs. - BZ#664594
- After a key recovery request is approved and complete, the recovery request page should display a list of which KRA agents approved the recovery. Instead, the Recovery Approving Agents field remains blank.The recovering page used by agents to approve the request is updated with the list of approving agents. That page can be referenced.
- BZ#616532
- When attempting to recover keys, if you search for pending requests based on the key identifier and click the Recover button, it returns an error that it had a problem processing the request. The form used to submit the search request sends a malformed request, which results in an invalid X.509 certificate error.To work around this problem, search for the recovery certificate by pasting in the full certificate blob in the search criteria form.
- BZ#512029
- If the same HSM partition is used to multiple Red Hat Certificate System subsystem instances, the instance names cannot be used more than once, even if the instances are on different hosts. If the user tries to configure a new instance with the same name (including the default options) as an existing instance, then configuration process stops at the key generation step with an error that the certificate subject name already exists.To work around this problem, when using an HSM, always specify a distinct
pki_XYZ_subject_dnindividually. - BZ#226823
- An error in the
<Connector>entry in theserver.xmlfile causes the server to start and listen on that connector port, but does not provide any services. This problem occurs if the system is configured to use an HSM, not the internal token, and can be recognized by the following JSS configuration error returned by the Tomcat server:Failed to create jss service: java.lang.SecurityException: Unable to initialize security library
- BZ#454559
- Attempting to connect to the Online Certificate Status Manager using the
wgetutility or HTTP POST to send OCSP requests times out.To work around this problem, use theOCSPClientutility to send status requests.
Appendix A. Revision History
| Revision History | |||
|---|---|---|---|
| Revision 9.7-0 | Tue Sep 29 2020 | Florian Delehaye | |
| |||
| Revision 9.6-0 | Wed Apr 01 2020 | Florian Delehaye | |
| |||
| Revision 9.5-0 | Tue Aug 06 2019 | Marc Muehlfeld | |
| |||
| Revision 9.4-0 | Thu Oct 25 2018 | Marc Muehlfeld | |
| |||
| Revision 9.3-1 | Tue Apr 10 2018 | Marc Muehlfeld | |
| |||
| Revision 9.2-1 | Tue Dec 12 2017 | Petr Bokoč | |
| |||
| Revision 9.2-0 | Tue Aug 01 2017 | Petr Bokoč | |
| |||
| Revision 9.1-1 | Thu Mar 09 2017 | Petr Bokoč | |
| |||
| Revision 9.1-0 | Tue Nov 01 2016 | Petr Bokoč | |
| |||
| Revision 9.0-1 | Fri Sep 04 2015 | Tomáš Čapek | |
| |||
| Revision 9.0-0 | Fri Aug 28 2015 | Tomáš Čapek | |
| |||

