Chapter 2. Automating Network Intrusion Detection and Prevention Systems (IDPS) with Ansible
You can use Ansible to automate your Intrusion Detection and Prevention System (IDPS). For the purpose of this guide, we use Snort as the IDPS. Use Ansible automation hub to consume content collections, such as tasks, roles, and modules to create automated workflows.
2.1. Requirements and prerequisites
Before you begin automating your IDPS with Ansible, ensure that you have the proper installations and configurations necessary to successfully manage your IDPS.
- You have installed Ansible 2.9 or later.
- SSH connection and keys are configured.
- IDPS software (Snort) is installed and configured.
- You have access to the IDPS server (Snort) to enforce new policies.
2.1.1. Verifying your IDPS installation
Additional resources
To verify that Snort has been configured successfully, call it via sudo and ask for the version:
$ sudo snort --version
,,_ -*> Snort! <*-
o" )~ Version 2.9.13 GRE (Build 15013)
"" By Martin Roesch & The Snort Team: http://www.snort.org/contact#team
Copyright (C) 2014-2019 Cisco and/or its affiliates. All rights reserved.
Copyright (C) 1998-2013 Sourcefire, Inc., et al.
Using libpcap version 1.5.3
Using PCRE version: 8.32 2012-11-30
Using ZLIB version: 1.2.7
Verify that the service is actively running via sudo systemctl:
$ sudo systemctl status snort
● snort.service - Snort service
Loaded: loaded (/etc/systemd/system/snort.service; enabled; vendor preset: disabled)
Active: active (running) since Mon 2019-08-26 17:06:10 UTC; 1s ago
Main PID: 17217 (snort)
CGroup: /system.slice/snort.service
└─17217 /usr/sbin/snort -u root -g root -c /etc/snort/snort.conf -i eth0 -p -R 1 --pid-path=/var/run/snort --no-interface-pidfile --nolock-pidfile
[...]
If the Snort service is not actively running, restart it with systemctl restart snort and recheck the status.
Once you confirm the service is actively running, exit the Snort server by simultaneously pressing CTRL and D, or by typing exit on the command line. All further interaction will be done through Ansible from the Ansible control host.
2.2. Automating your IDPS rules with Ansible
To automate your IDPS, use the ids_rule role to create and change Snort rules. Snort uses rule-based language that analyzes your network traffic and compares it against the given rule set.
The following lab environment demonstrates what an Ansible security automation integration would look like. A machine called “Attacker” simulates a potential attack pattern on the target machine on which the IDPS is running.
Keep in mind that a real world setup will feature other vendors and technologies.
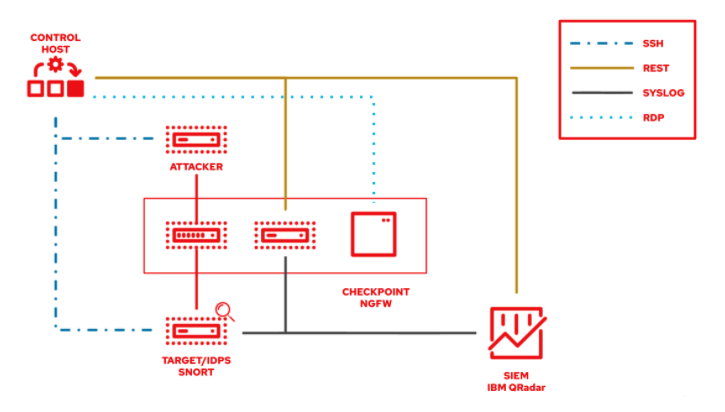
2.2.1. Creating a new IDPS rule
Additional resources
Use the ids_rule role to manage your rules and signatures for IDPS. For example, you can set a new rule that looks for a certain pattern aligning with a previous attack on your firewall.
Currently, the ids_rule role only supports Snort IDPS.
Prerequisites
-
You need
rootprivileges to make any changes on the Snort server.
Procedure
Install the
ids_rulerole using the ansible-galaxy command:$ ansible-galaxy install ansible_security.ids_rule
Create a new playbook file titled
add_snort_rule.yml. Set the following parameters:- name: Add Snort rule hosts: snort
Add the
becomeflag to ensure that Ansible handles privilege escalation.- name: Add Snort rule hosts: snort become: true
Specify the name of your IDPS provider by adding the following variables:
- name: Add Snort rule hosts: snort become: true vars: ids_provider: snortAdd the following tasks and task-specific variables (e.g., rules, Snort rules file, and the state of the rule - present or absent) to the playbook:
- name: Add Snort rule hosts: snort become: true vars: ids_provider: snort tasks: - name: Add snort password attack rule include_role: name: "ansible_security.ids_rule" vars: ids_rule: 'alert tcp any any -> any any (msg:"Attempted /etc/passwd Attack"; uricontent:"/etc/passwd"; classtype:attempted-user; sid:99000004; priority:1; rev:1;)' ids_rules_file: '/etc/snort/rules/local.rules' ids_rule_state: presentTasks are components that make changes on the target machine. Since you are using a role that defines these tasks, the
include_roleis the only entry you need.The
ids_rules_filevariable specifies a defined location for thelocal.rulesfile, while theids_rule_statevariable indicates that the rule should be created if it does not already exist.Run the playbook by executing the following command:
$ ansible-navigator run add_snort_rule.ym --mode stdout
Once you run the playbook, all of your tasks will be executed in addition to your newly created rules. Your playbook output will confirm your PLAY, TASK, RUNNING HANDLER, and PLAY RECAP.
Verification
To verify that your IDPS rules were successfully created, SSH to the Snort server and view the content of the /etc/snort/rules/local.rules file.

