Chapter 1. Introduction to Ansible Automation Platform on Microsoft Azure
1.1. About Red Hat Ansible Automation Platform on Microsoft Azure
Red Hat Ansible Automation Platform on Microsoft Azure is a managed application that you can deploy from the Azure Marketplace portal to a resource group in your Azure tenant. Ansible Automation Platform on Microsoft Azure provides access to a library of Ansible content collections, and it is integrated with key Azure services, so you can start deploying, configuring, and managing infrastructure and applications quickly.
The following Red Hat Automation Platform components are available on Red Hat Ansible Automation Platform on Microsoft Azure:
- Automation Controller
- Automation Hub
- Private Automation Hub
- Automation Service Catalog
- Ansible Content Collections, including the Microsoft collection for Azure
- Automation Execution Environment
- Ansible content tools, including access to Red Hat Insights for Red Hat Ansible Automation Platform
Automation mesh is not available on Ansible Automation Platform on Microsoft Azure.
1.2. Application Architecture
Red Hat Ansible Automation Platform on Microsoft Azure is installed as a managed application. Red Hat manages both the underlying Azure resources and the software running on it while that infrastructure runs in your Azure tenant.
The managed application resource group is completely separate from other resource groups in your tenant. Red Hat only has access to the managed application resource group, with no visibility into other tenant resources.
For information about how this works and how resources and access are isolated from the rest of your Azure resources, refer to Azure managed applications overview in the Microsoft Azure managed applications guide.
Ansible Automation Platform on Microsoft Azure uses the following resource groups:
- A new or existing resource group (RG) in your tenant. This resource group includes a single resource referring to the Ansible Automation Platform on Microsoft Azure managed application deployment. Red Hat has access to the managed app to perform support, maintenance, and upgrades, but the resource group is outside of Red Hat’s management.
- A multi-tenant managed resource group (MRG) that contains most of the infrastructure needed to operate Ansible Automation Platform on Microsoft Azure. This multi-tenant resource group is shared between the Red Hat tenant and your tenant. Red Hat has full administrative control and you have read-only access to the resource group.
- An AKS node pool resource group (NPRG). Microsoft requires the NPRG for AKS deployments. It contains resources that AKS uses to function. It is created on deployment, and it is outside of Red Hat’s management. Refer to Microsoft’s AKS documentation for more information about NPRGs.
Do not interact with any resources in the node pool resource group (NPRG) unless explicitly directed to by the Red Hat Ansible Automation Platform on Microsoft Azure SRE team. Changes to resources in the NPRG cannot be protected by Red Hat and can cause irrecoverable damage to the application.
Red Hat cannot restrict your ability to change or delete resources in the NPRG.
When you install Ansible Automation Platform on Microsoft Azure, you choose whether the deployment is public or private. This affects how users can access the Ansible Automation Platform user interfaces.
Regardless of whether you choose a public or private deployment, you must configure network peering for outbound communication from Ansible Automation Platform to the private networks that contain resources that you want to automate against. You can configure network peering from Ansible Automation Platform on Microsoft Azure to your private Azure VNets and to on-premises or multi-cloud networks where transit routing with Azure exists.
1.2.1. Public deployment
Public deployments permit ingress to the Ansible Automation Platform on Microsoft Azure user interfaces over the public internet. Upon deployment, a domain name is issued to the Ansible Automation Platform on Microsoft Azure instance. No configuration is required to access Ansible Automation Platform. Users can navigate to the domain from the public internet and log in to the user interfaces.
The following diagram outlines the application resources and architecture that are deployed into the managed application resource group on a public deployment of Ansible Automation Platform on Microsoft Azure into your Azure subscription. The IP ranges change based on the networking address range you set on deployment.
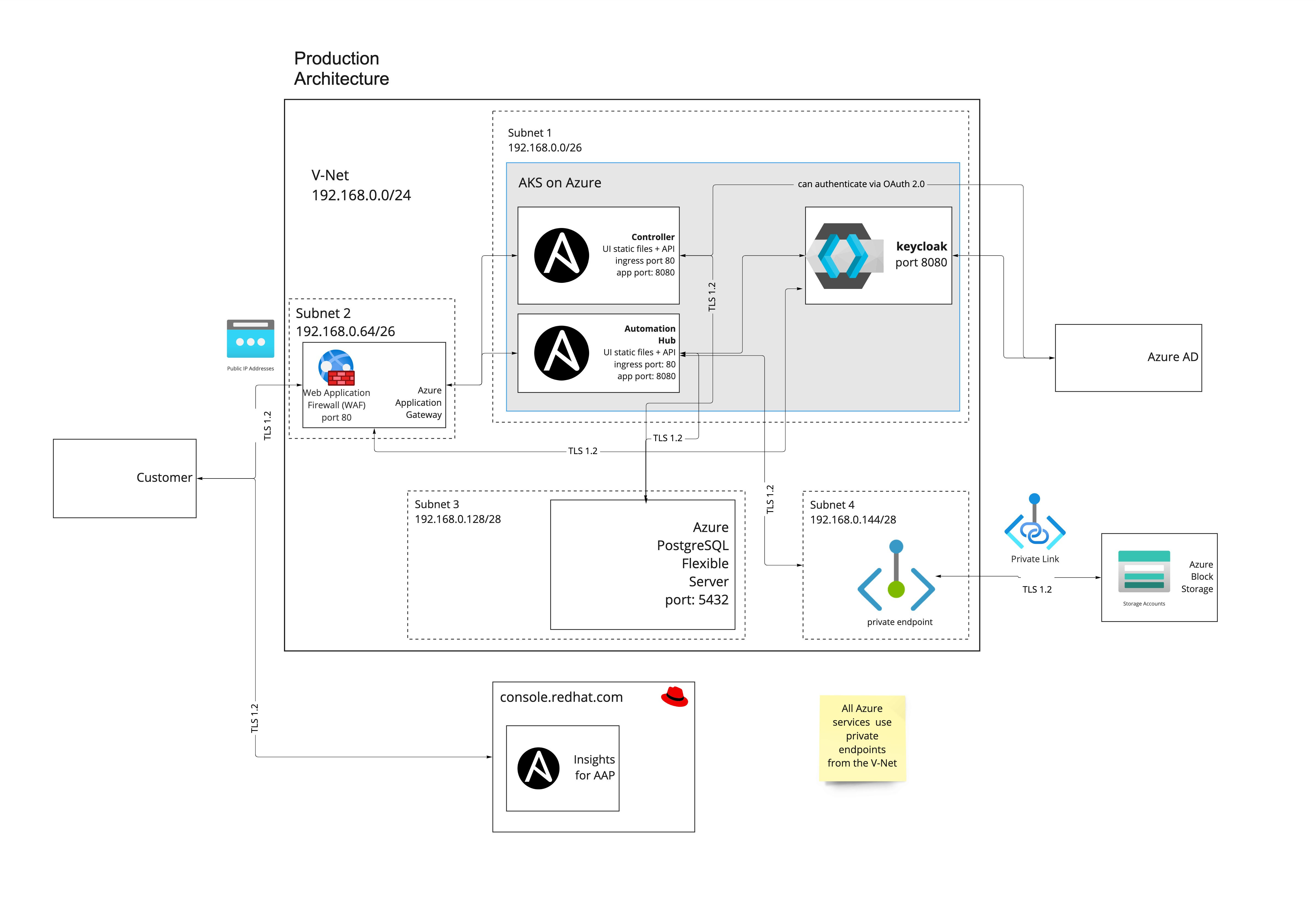
1.2.2. Private deployment
A private deployment of Ansible Automation Platform resides in an isolated Azure VNet with no access from external sources: traffic to and from the public internet and other Azure VNets and subnets is blocked.
To access the URLs for the Ansible Automation Platform user interfaces, you must configure network peering.
Once peering and routing are configured, users can access Ansible Automation Platform through a VM on a connected Azure subnet, or directly if your organization has transit routing set up between Azure and your local network.
No two Azure networking configurations are the same. To allow user access to your Ansible Automation Platform URLs, your organization will need to work with your Azure administrators to connect the private access deployment.
The following diagram outlines the application resources and architecture that are deployed into the managed application resource group on a private deployment of Ansible Automation Platform on Microsoft Azure into your Azure subscription. The IP ranges change based on the networking address range you set on deployment.
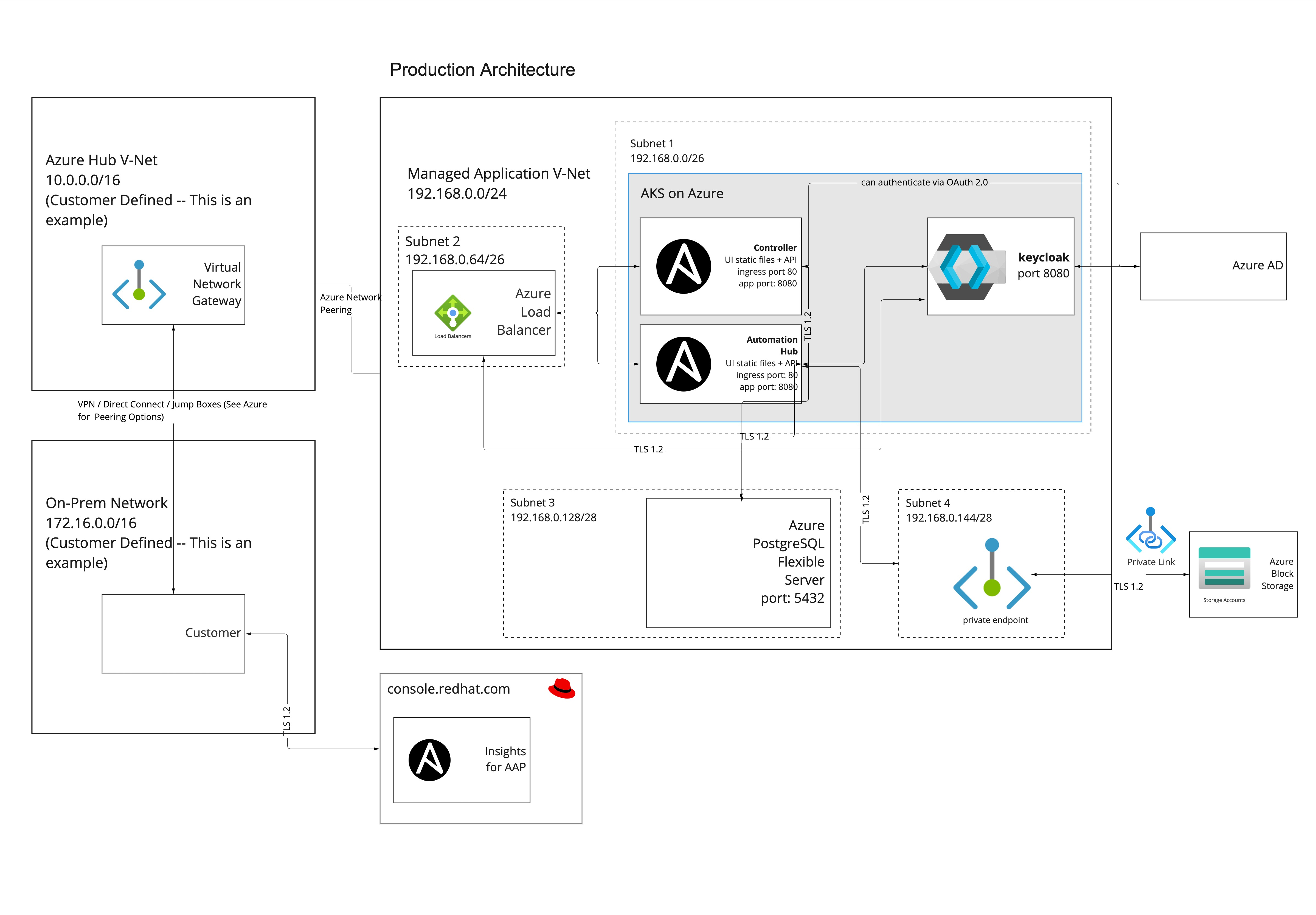
1.3. Network
You can configure the networking address range (CIDR block) for the VNet that your Ansible Automation Platform on Microsoft Azure application uses. You set the CIDR block for the application in a network configuration form when you deploy Ansible Automation Platform on Microsoft Azure. Plan your networking configuration before you deploy the Ansible Automation Platform on Microsoft Azure application, because you cannot change it after deployment.
When you are planning your network configuration, bear the following in mind:
The managed application requires at least a /24 Vnet that is divided into four subnets. The subnets have minimum address spacing.
Networking entity Minimum CIDR Block VNet
/24
Cluster subnet
/26
Gateway subnet
/28
Database subnet
/28
Private link subnet
/28
- Ensure that the VNet range you configure does not intersect with the default CIDR block for AKS clusters (10.0.0.0/16). The Azure user interface does not prevent you entering this range, but using the default AKS CIDR block for your VNet causes networking issues.
- To ensure successful network peering and communication between Ansible Automation Platform on Microsoft Azure and your existing networks, your enterprise network ranges must not overlap with the VNet network range.
- If you do not have any existing Azure VNets, the Azure user interface suggests a default CIDR block and range for the VNet. Do not accept these defaults. Instead, use the network configuration that you have planned.
For information about planning the network address range and completing the networking configuration form on deployment, refer to Red Hat Ansible Automation Platform on Microsoft Azure VNet Preparation.
1.4. Ansible Automation Platform on Microsoft Azure infrastructure usage
When you install Ansible Automation Platform on Microsoft Azure, the following infrastructure is deployed into your Azure subscription:
- Azure Kubernetes service (AKS)
The Kubernetes cluster used to deploy Ansible Automation Platform applications and services.
Service Shape:
- Compute nodes: Standard_D4s_v3 (4 vCPUs x 16 GiB)
- Autoscaling minimum nodes: 2
- Autoscaling maximum nodes: 20
- Managed identity
- An Azure service that enables Ansible Automation Platform components to communicate with other Azure services such as database, DNS, storage, and other services.
- Key vault
- A secure key vault used to store secrets that are unique to the Ansible Automation Platform deployment.
- Log Analytics Workspace
- An Azure service that enables Red Hat site reliability engineers to inspect the operations of Ansible Automation Platform on Microsoft Azure.
- Private DNS Zone
- Manages local DNS requests for the services used by Ansible Automation Platform on Microsoft Azure.
- Azure Database for PostgreSQL
An Azure database service used for Ansible Automation Platform’s PostgreSQL database.
Service Shape: 1 TB
- Storage account
The Azure service is used for file and block storage for local storage of projects, containers, etc.
Service Shape: StorageV2 - Standard_LRS
- Virtual network
The Azure service is used to manage all internal networking and dependent services such as the Azure Application Gateway.
Service Shape: Application Gateway: WAF_v2
Exact infrastructure usage depends on the length of time that the managed application is deployed in your tenancy, and the automation requirements that might cause the Kubernetes cluster to autoscale to meet the demands of your workload.
Microsoft provides a Pricing calculator to estimate your costs for Azure products and services. Red Hat has configured an example scenario in the pricing calculator: use the Red Hat Ansible Automation Platform on Azure Infrastructure Estimate to tune Kubernetes expected auto scaling variables based on your organization’s workloads.
1.5. Lifecycle management
Red Hat Ansible is responsible for the monitoring, health, and maintenance of the underlying services and Ansible Automation Platform on Microsoft Azure core systems as well as the operation of Ansible Automation Platform on Microsoft Azure itself. This includes lifecycle management of the components.
1.6. Ansible Automation Platform on Microsoft Azure scaling
Ansible Automation Platform on Microsoft Azure default configuration of Microsoft Azure cluster autoscaler for autoscaling, with the following settings to limit the number of nodes:
- Minimum Nodes: 1
- Maximum Nodes: 20
1.7. Migration
Red Hat does not provide a solution to migrate existing deployments to Ansible Automation Platform on Microsoft Azure.

