Creating the Developer Portal
A good developer portal is a must have to assure adoption of your API. Create yours in no time.
Abstract
Chapter 1. Developer Portal
By the end of this section you should be familiar with the Developer Portal, including its structure, use, and functionality.
You can customize the look and feel of the entire Developer Portal to match your own branding. You have complete control over every element of the portal, so you can make it as easy as possible for developers to learn how to use your API. A successful API Developer Portal will help your developers turn concepts into working apps in no time at all.
1.1. Overview of the Developer Portal
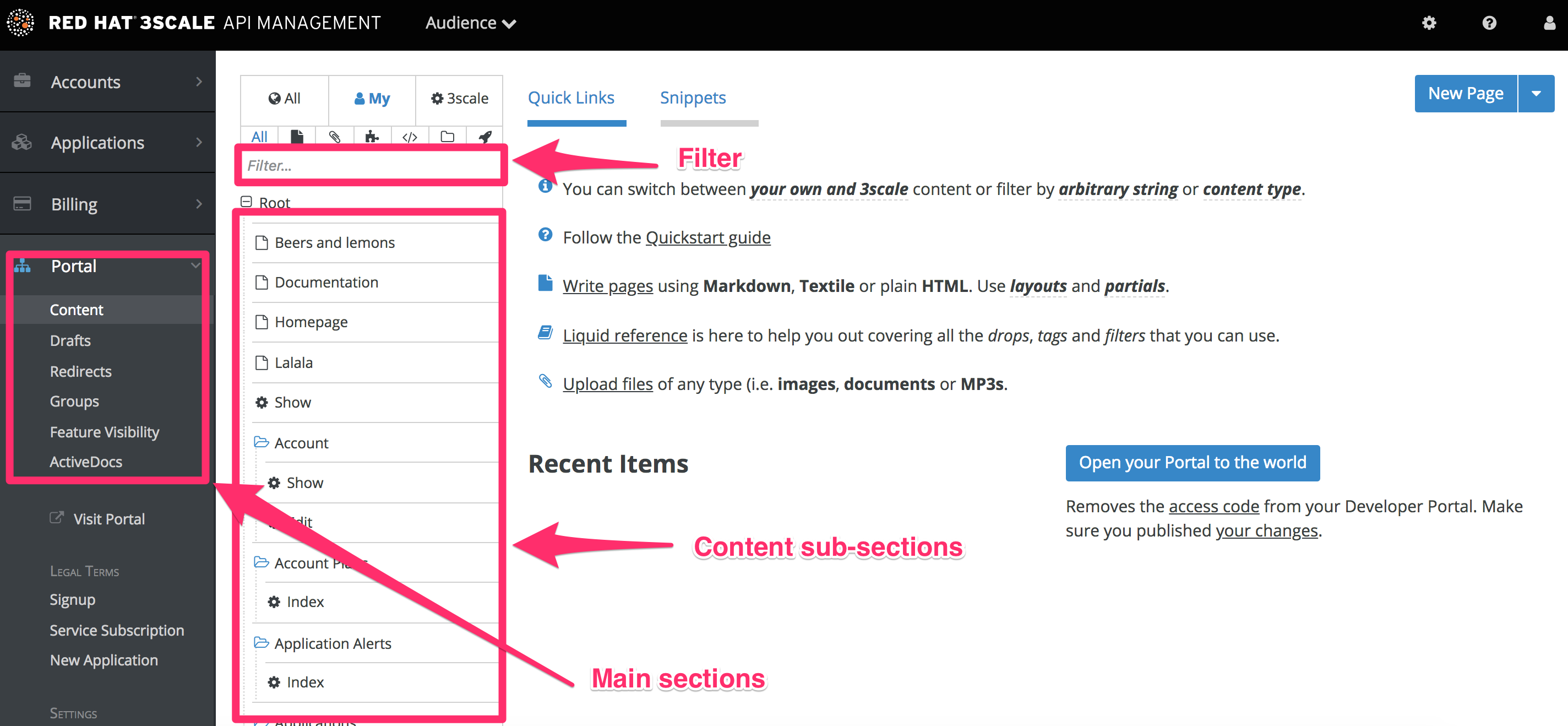
The Developer Portal consists of a few elements:
- Left menu with access to Content, Drafts, Redirects, Groups, Feature Visibility, ActiveDocs, Legal Terms, Settings and Liquid documentation.
- The main area containing details of the sections above.
1.2. Content
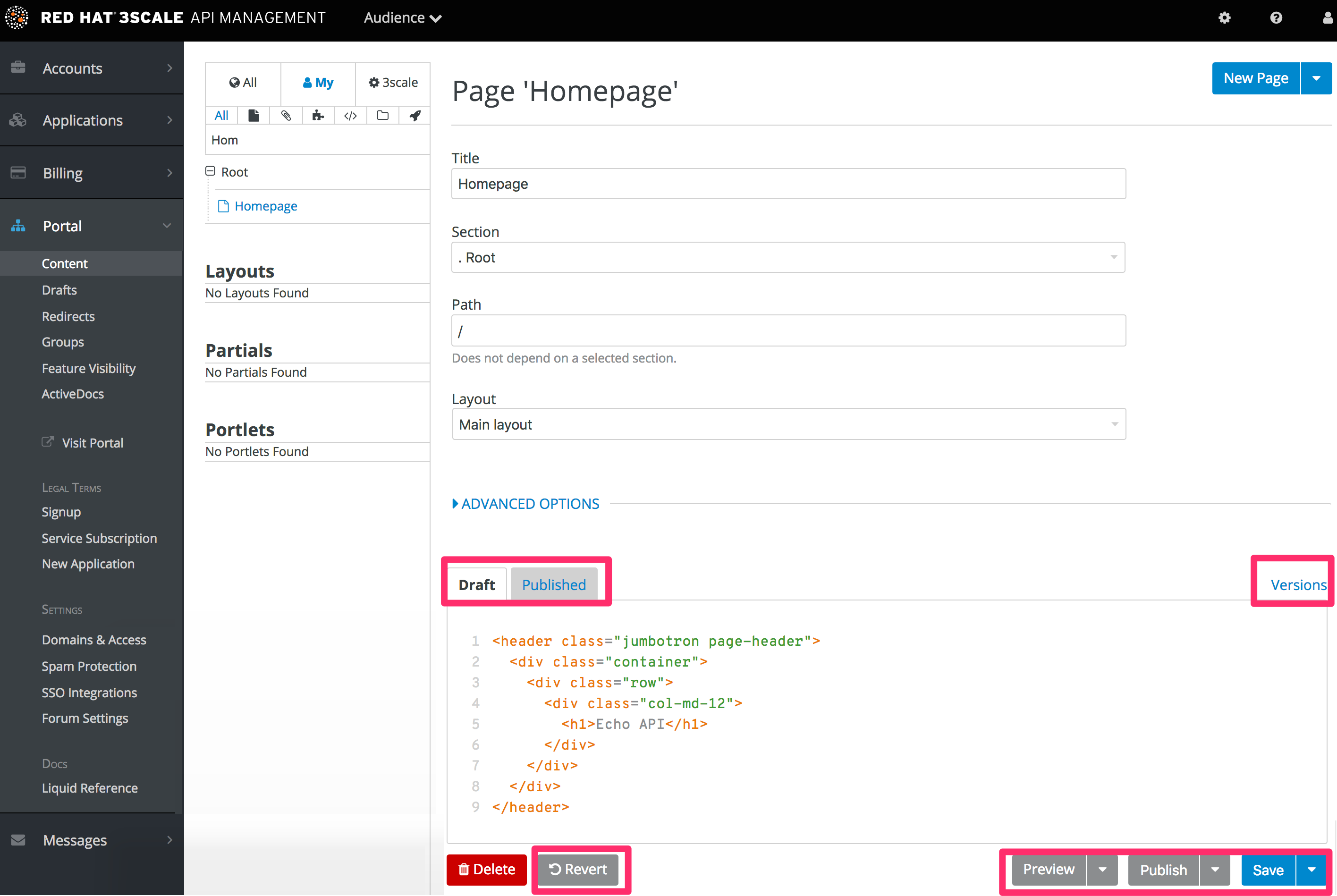
This is the most important part of your view of the Developer Portal system. The content section shows the site structure and hierarchy and provides editing functionality within the same page. This means you can manage the site structure, the pages, and other assets stored in it. The portal’s hierarchy is displayed in the form of a directory tree.
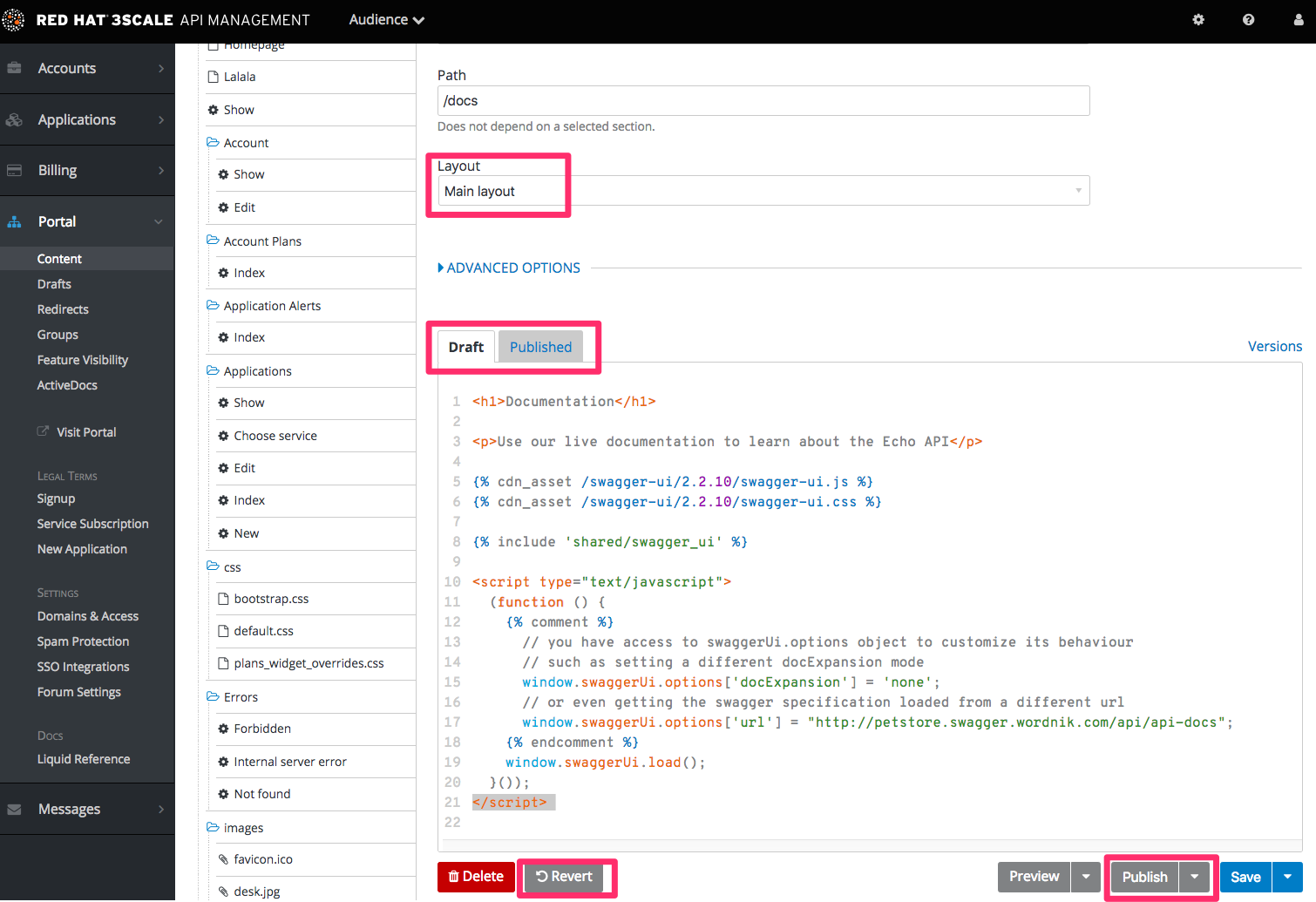
The image above shows a sample view of one of the pages inside the contents section. As you can see, it displays all the files (pages, images, stylesheets, JavaScript, etc.) preserving the site’s path hierarchy. As before, sections are functionally equal to directories.
On the right-hand side, you can see the edit page view. Here you can see the page name (which also indicates whether it’s a standard or built-in page) and a button to add a new element to the content (page, layout, partial, section, or file). Below, you can choose which layout the page will use and toggle the liquid tags functionality. The following part is the text editor, which supports code highlighting, tabulations, line numeration, and much more. The tab buttons Draft and Published switch between the draft and published versions of the edited document. The following two icons list the document’s versions and open a pop-up edit window, respectively.
To edit page content, simply choose the desired layout, set a few additional options such as content type and URL path, and then input the code in HTML, Markdown, or Textile.
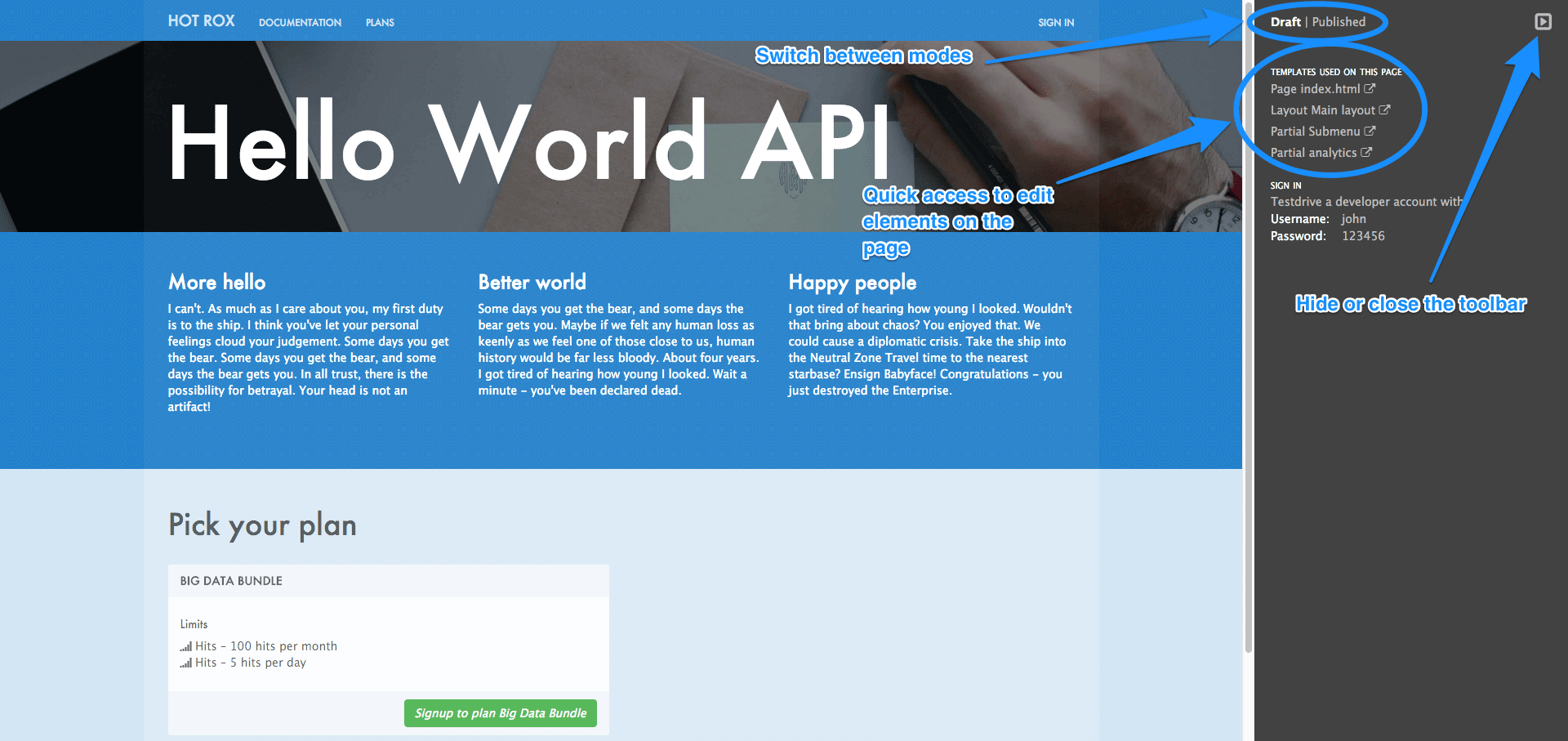
Another important feature in this view is the Preview button. You can choose whether you want to preview the published or draft version of the page. Clicking the button redirects you to Developer Portal mode, where you can see the live (or draft) rendered version of the page with a dark grey vertical bar on the right-hand side. This bar contains links to the page, layout, and partials edit views of the Developer Portal. It allows you to swtich between draft and published views.
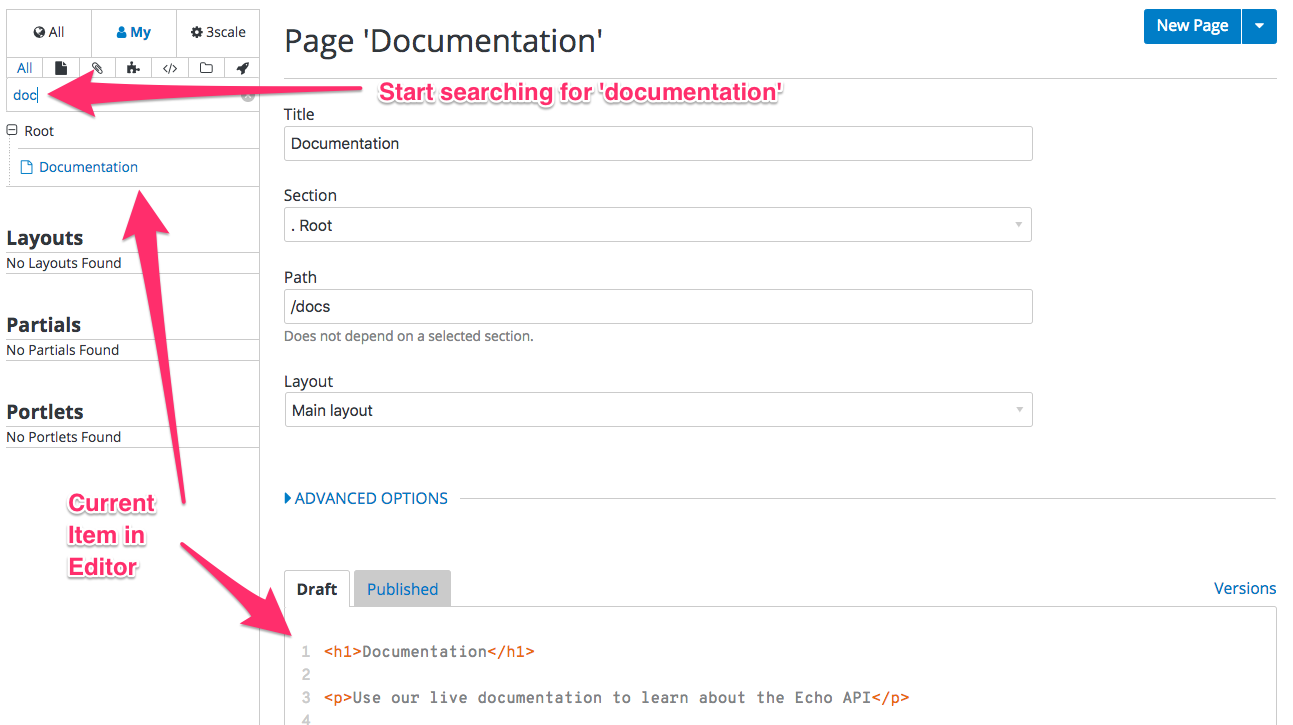
There’s also a filter feature, which serves not only as a search field but allows you to limit the elements shown to only stylesheets, JavaScript, or any other types specified.
1.3. Layouts and partials
The layouts and partials sections manage the templates and the reusable parts of the page. Their functionality is similar to that of the content section.
The layouts section consists of definitions of the templates used by pages. Layout is the main structure of the page, and the contents of this template will be rendered on every page that uses it. The partials and the actual content of the pages reside inside the templates.
Partials are the reusable parts of code, which can be applied to many places on different pages. For example, the footer is the same on every layout, and the sidebar is the same on a few pages with different layouts.
To include a partial in a layout, partial, or email template use the following command:
{% include "partial_name" %}As with the other parts of the portal, layouts and partials also have draft and published states and offer a full version history, with the following features:
- Text editor for the layout template.
- Save draft, publish current version, and revert to the last published state.
- Switch the text editor between the draft and published versions, list the version history, and launch the pop-up editor.
For a complete guide of liquid tags, check the Liquid Reference guide.
1.4. Redirects and changes
The last elements of the Developer Portal are the redirects and changes sections. They are much less complicated than the content section but are still important and provide some custom functionality.
Redirects help you set up redirects from one portal URL to another. This is useful, for example, when you deprecate an old page and don’t want to change all the links. Redirects cannot be used for built-in Developer Portal pages – they are only for pages created by you.
Last but not least is the changes section. It contains a list of all the newly edited and unpublished pages and gives you the choice to publish them individually or all at once.
1.5. Updating local assets
This section provides details on updating local assets for the Developer Portal, based on these points:
-
From 3scale 2.8, all new Developer Portals are created using the
cdn_assettag. -
For existing instances of the Developer Portal, you need to update your assets by using the
cdn_assettag. With this feature, there is not dependence on assets that require downloading from other websites, because all external assets were moved from Content Delivery Networks (CDNs) to our codebase.
Hence, to update an existing Developer Portal instance and use the new local assets, follow these instructions:
- Go to Audience > Developer Portal > Content
From the menu list located on the left side of the window, select Main layout.

Replace
{{ '//netdna.bootstrapcdn.com/font-awesome/4.3.0/css/font-awesome.css' | stylesheet_link_tag }}with
{% cdn_asset /font-awesome/4.3.0/css/font-awesome.css %}Replace
{{ '//ajax.googleapis.com/ajax/libs/jquery/1.7.1/jquery.min.js' | javascript_include_tag }}with
{% cdn_asset /jquery/1.7.1/jquery.min.js %}- Click Publish, and then Save.
- From the menu list located on the left side of the window, select Partials.
Choose stats/chart.
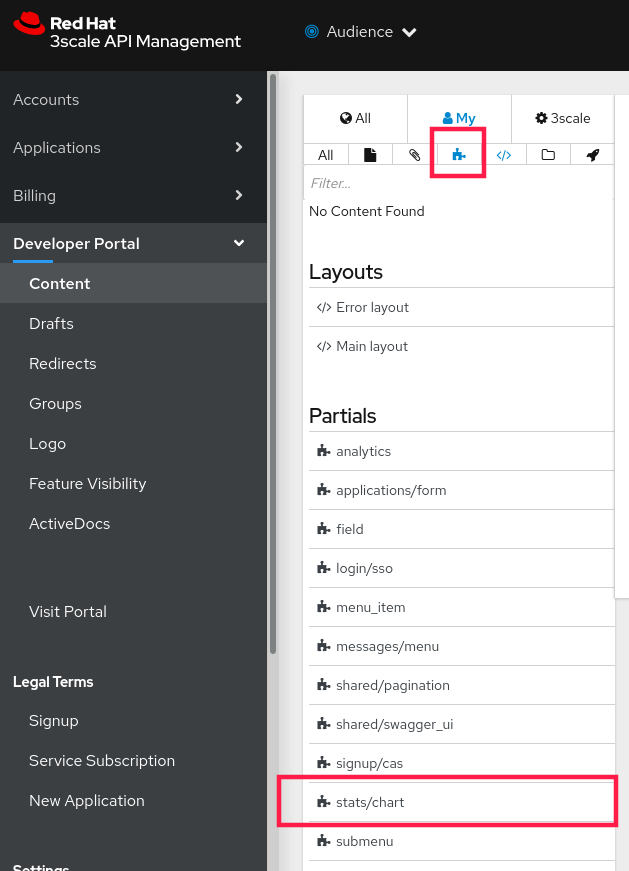
Replace
{{ '//ajax.googleapis.com/ajax/libs/jqueryui/1.11.4/themes/ui-lightness/jquery-ui.css' | stylesheet_link_tag }}with
{% cdn_asset /jquery-ui/1.11.4/jquery-ui.css %}- Click Publish, and then Save.
If you have created other instance files based on the previous ones, such as Main Layout and stats/chart, you will need to update them too. For more information, see the documentation for Liquid tags in porta.
Chapter 2. Custom signup form fields
Learn how to add custom signup fields and the different options around this feature.
By default, 3scale provides commonly used fields at user/account/application signup. You may need to add your own custom fields to these common defaults.
In your Admin Portal, go to Audience > Accounts > Field Definitions where you can see the default form fields and define new ones.
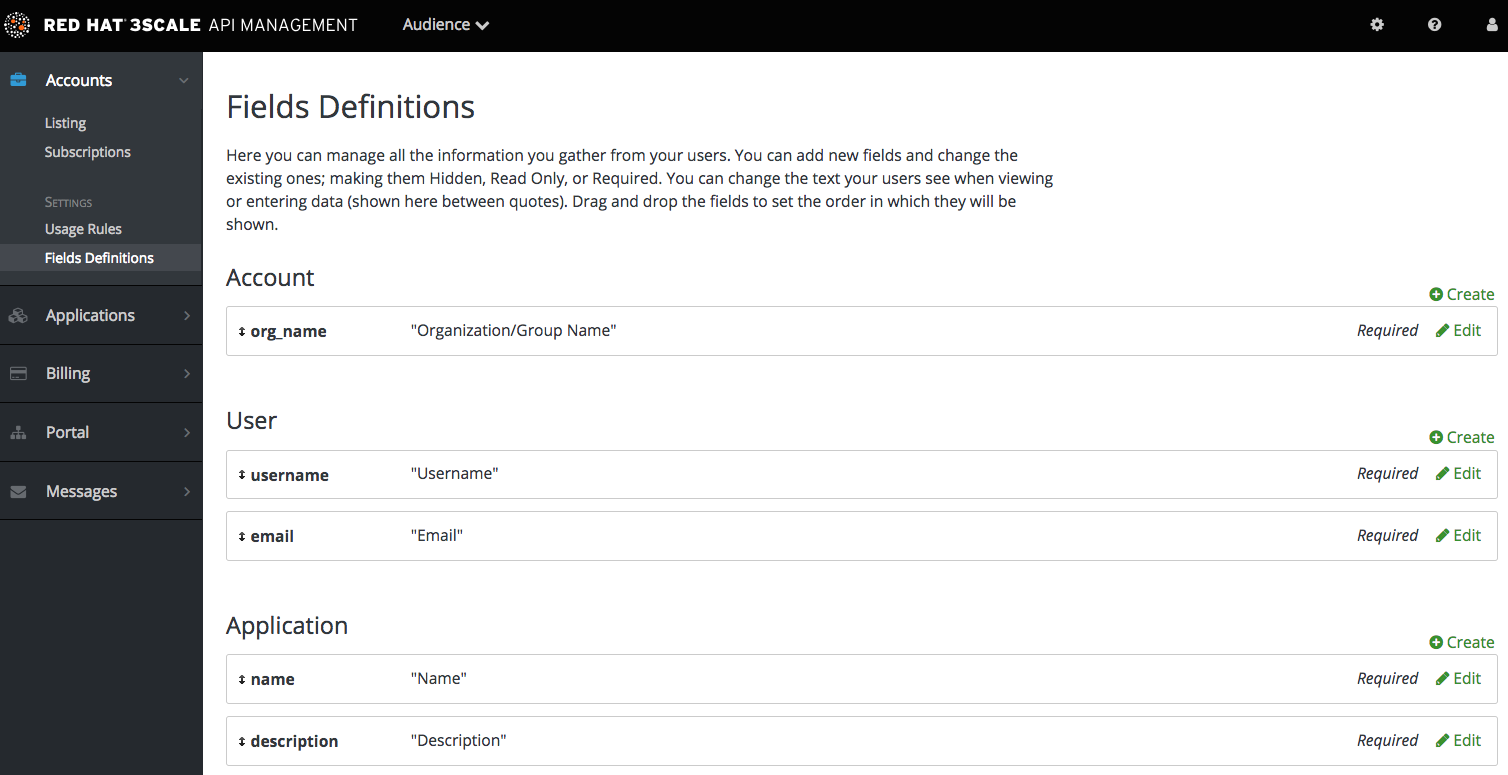
The new account/user signup page is actually an amalgamation of the first two sections. The account fields appear at the top, followed by the user fields, followed by the password fields which don’t need to be configured.

Try adding 3 extra fields, 2 to the user signup section and 1 to the account section. Click create, add the following new field definition and then create it. The required checkbox will, of course, make it mandatory on the signup form. There are also options to make things hidden and read only. A hidden field may be added, for example, when you want new signups to have fields set that you don’t necessarily want to highlight to them, such as access_restricted_areas which would be empty by default. As an admin, you can update this to true later on a per-user basis. Your page logic could read it in to determine what to display. A read-only field might be, for example, browser location, which you could use JavaScript on page load to set.

Now try adding a drop-down to the user signup form. Call it "employment type". Add these comma-separated values into the choices field: full time, part time, contract. The drop-down will be populated with these values.
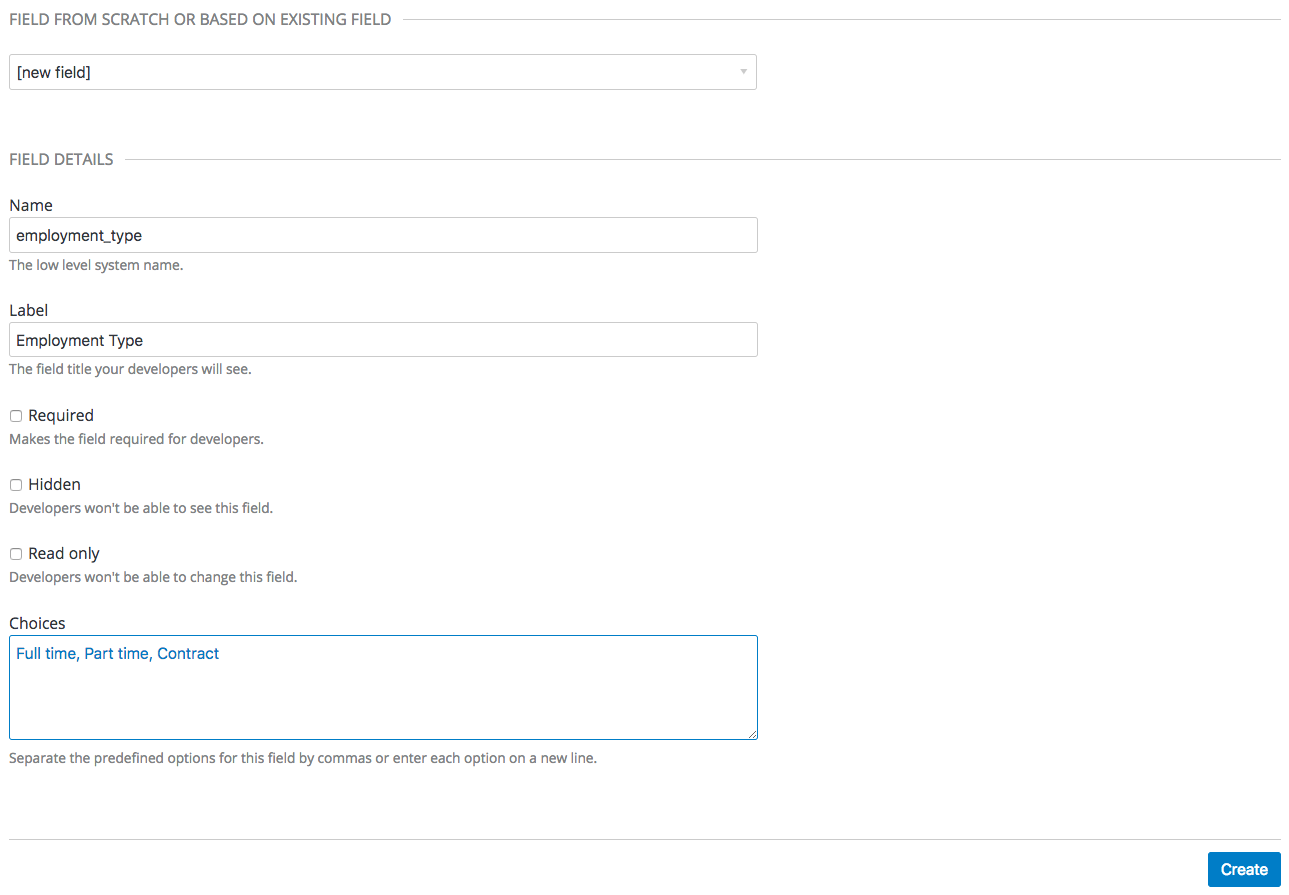
Now add a pre-defined field to the account. Usually the fields you add have no system functionality – they simply hold data that you can access later. (See restricted content.)
Create a field as normal. Then on the drop-down above "name", choose po_number. With this field, a PO number will appear on 3scale-generated invoices sent to this developer account. System-generated fields can be overridden by your admins at any time. Give the field a name – something like "PO number" – and create it.
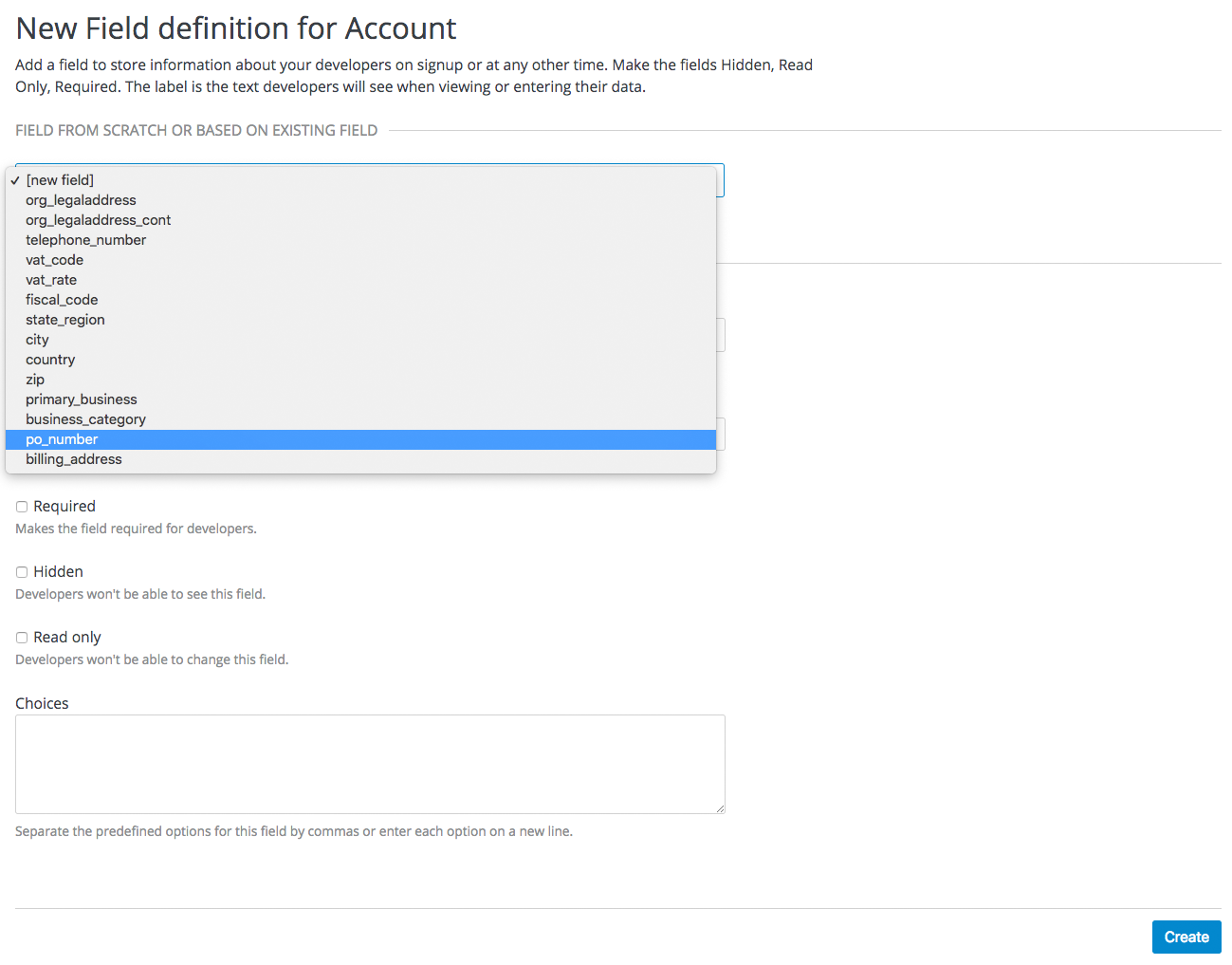
Now take a look at your work. You can see the free text last name and the employment type drop-down have been added to the User section. The PO number system field, also free text, has been added to the Account section.

Finally, these custom fields can be set using the 3scale ActiveDocs; for example, application create.
Chapter 3. Configuring signup flows
In this section, you’ll see which settings to configure to adjust signup workflows.
Signup workflows are a critical aspect of the developer experience you provide through your Developer Portal. The process can range from being completely automatic and self-service to the other extreme of requiring total control over who gains access to what, with various levels of granularity.
The 3scale platform allows you to model your API with a combination of account (optional), service (optional), and application plans. For each of these plans, you can control whether there is an approval gate that you operate. For each one, you also determine whether there is a default, or the developer is required to take the next step and make a choice.
For the extreme of maximum automation and self-service, remove all approval steps and enable all possible default plans. This way, a key can be issued to provide access to your API immediately after signup.
3.1. Removing all approval steps
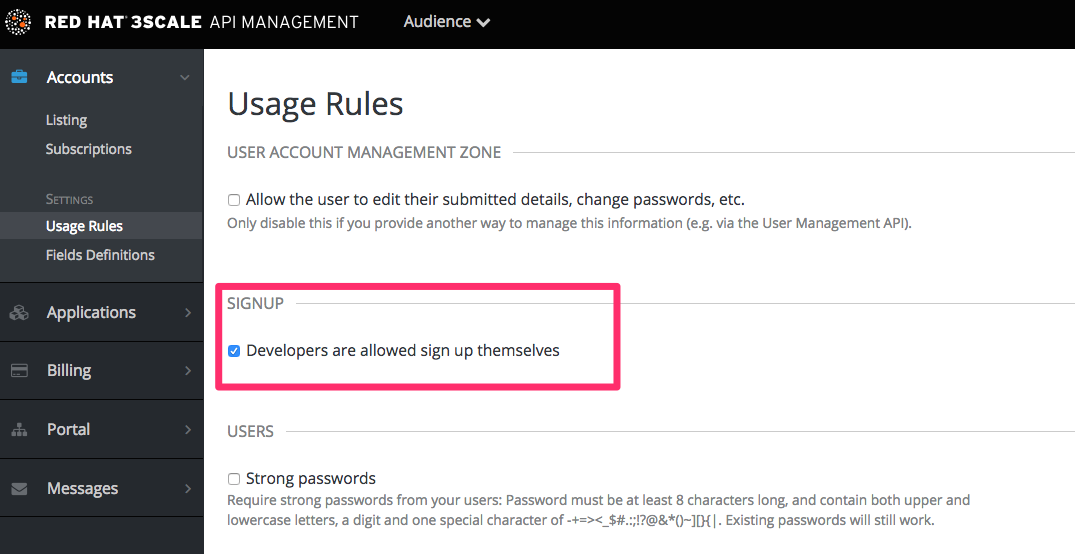
To remove approvals, go to Audience > Accounts > Usage Rules and in the Signup section, make sure the option of Developers are allowed to sign up themselves is checked.
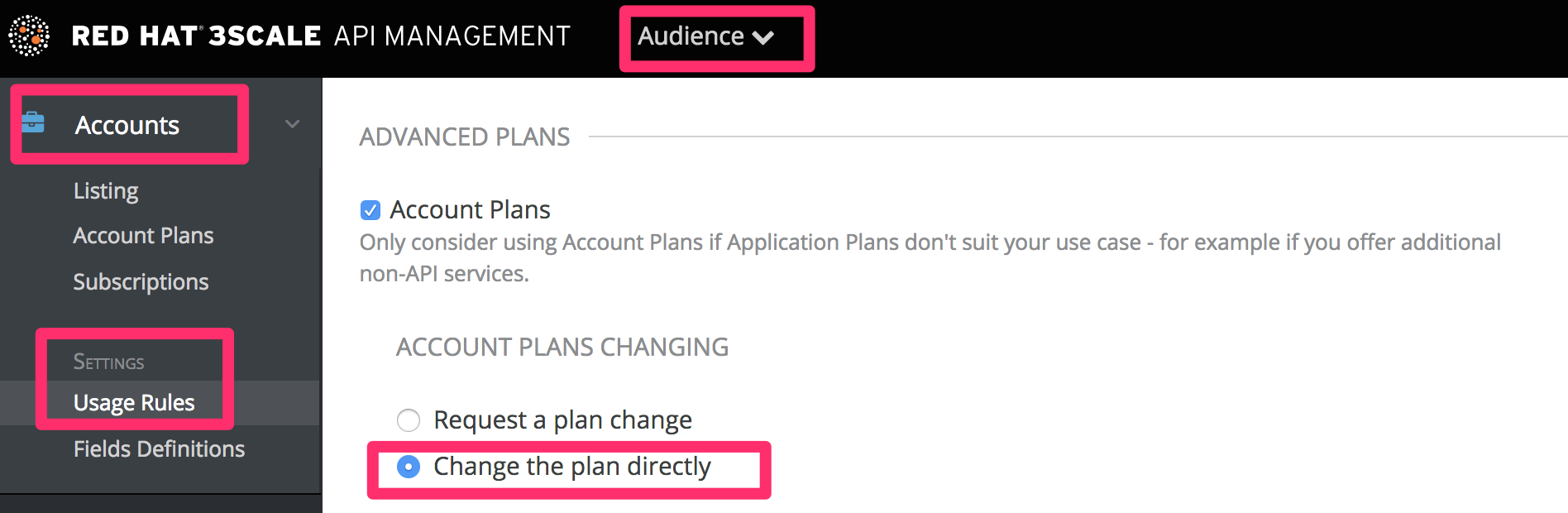
Optionally, if you have account and service plans enabled, scroll down the page and make sure the option Change plan directly is enabled in both cases:
3.2. Enabling all possible default plans
Application plans
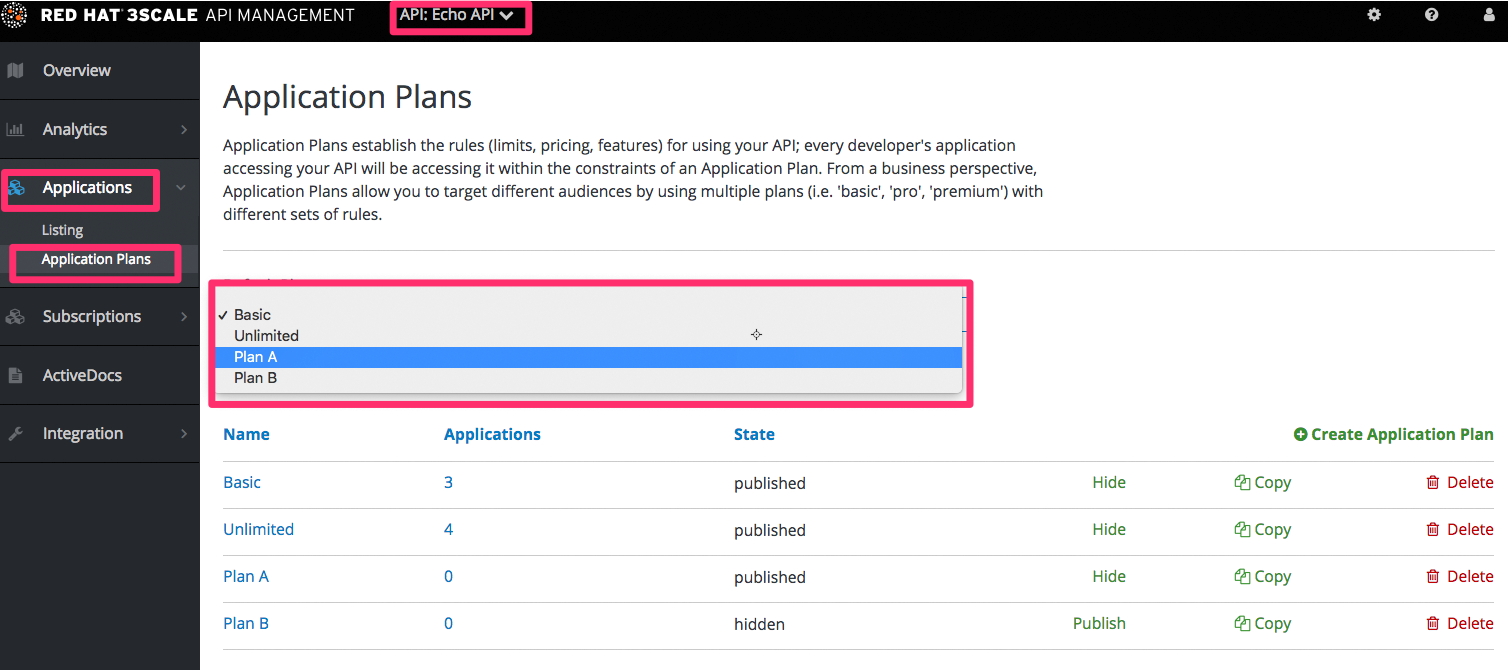
Optionally, if you have account and service plans enabled, choose default plans for those too
Account plans (optional)
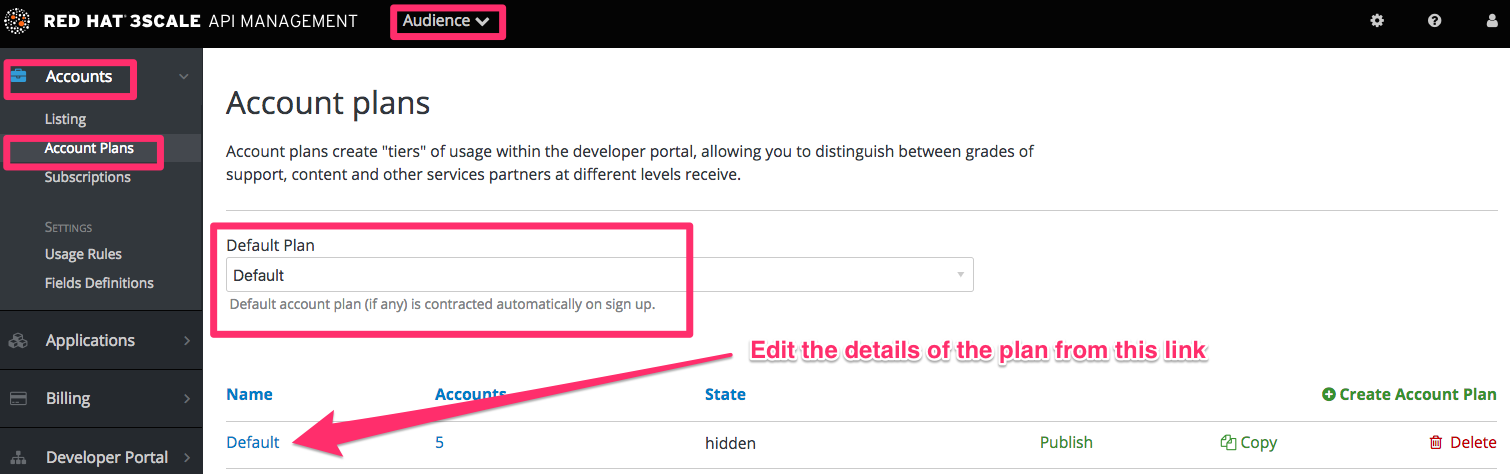
Service plans (optional)
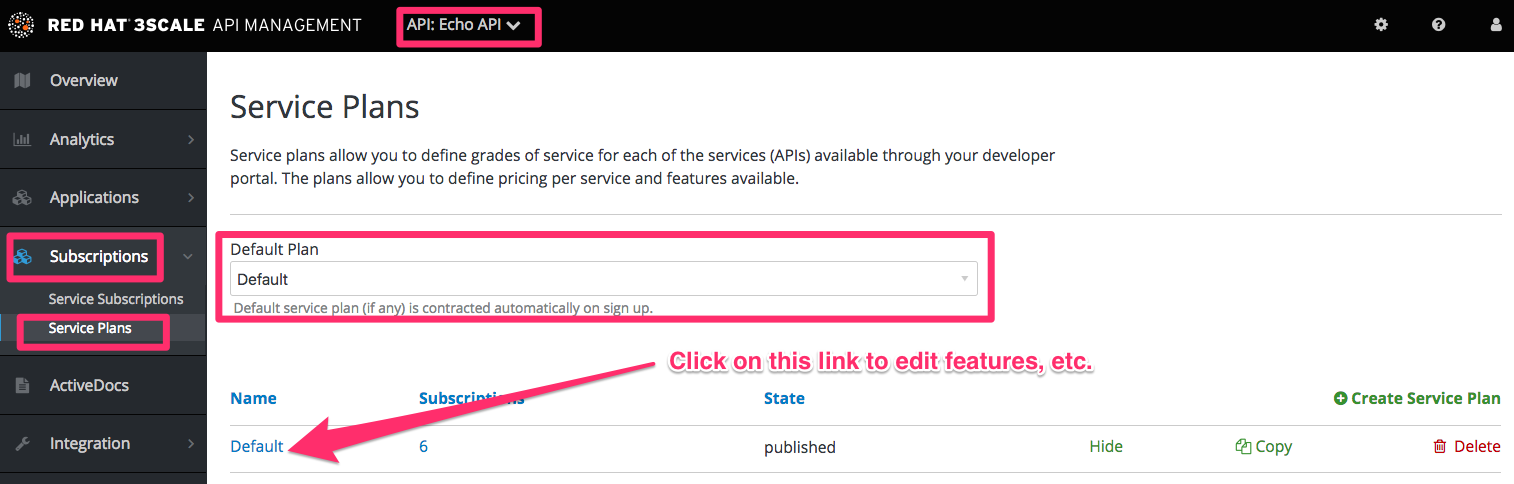
3.3. Testing the workflow
Once you’ve made your desired settings changes, test out the results by going to your Developer Portal and attempting to sign up as a new developer. Experiment and make any necessary adjustments to get exactly the right workflow for your API. When you’re happy with the workflow, it’s a good time to check your email notifications to make sure they provide the right information for your developers.
Chapter 4. Multi-service signup
By the end of this section, you’ll be familiar with the procedure to create and customize a multiple-service signup page.
If you’re using the multiple services functionality, you’re able to customize the signup procedure to allow customers to subscribe to different services.
4.1. Prequisites
You should be familiar with layout and page creation procedures as well as with the basics of Liquid formatting tags. For more details about liquid tags, see Liquid reference. "Multiple Service" functionality must also be enabled on your account (available for Pro plan and up).
It’s strongly recommend that you read about signup workflows, so you’ll have the whole setup prepared and know how it works.
4.2. Introduction
Start the process by creating a new layout, which will serve as the template for your multi-service signup page. Go into the Layouts section of the CMS system, and create the new layout. You can call it multipleservicesignup to be able to easily distinguish it from the other layouts. In the editor, paste the general structure of your standard layout (such as home or main layout). Now delete everything you don’t need – all the containers, sidebars, additional boxes, etc.
Having created the backbone of your layout, proceed to customizing the code for signup.
4.3. Multi-service signup
4.3.1. Retrieving information about services
In order to retrieve all the information about the services that you need to construct the proper signup link, you have to loop through the service objects. Services are a part of the model object.
{% for service in provider.services %}
.
.
.
{% endfor %}4.3.2. Configuring the signup columns
You already have your layout and loop accessing the service objects. Now decide how you want to display information about the service and the signup link. For example, divide them into columns with a service description and a signup link at the bottom. Every column will be a div box with a service-column class to contain all the necessary information.
{% for service in provider.services %}
<div class="service-column">
<p>{{ service.name }}</p>
<p>{{ service.description }}</p>
.
.
.
</div>
{% endfor %}The container inside serves as a custom description field. service.name is the service name, which in this case will be the container’s name.
4.3.3. Configuring the subscription
Now the main part of your custom service signup – to create the signup link, extract the signup URL and the service ID. Take the signup URL from URL’s object and the service ID from your service object on which you iterate in the loop. The final link code will look like this:
<a href="{{ urls.signup }}?{{ service | toparam }}">Signup to {{ service.name }}</a>You also have to take into account that the user may already have signed up for some of your services. Create a conditional block to check.
{% unless service.subscribed? %}
<a href="{{ urls.signup }}?{{ service | toparam }}">Signup to {{ service.name }}</a>
{% endunless %}With this, you can generate the final code:
{% for service in provider.services %}
<div class="service-column">
<p>{{ service.name }}</p>
<p>{{ service.description }}</p>
{% unless service.subscribed? %}
<a href="{{ urls.signup }}?{{ service | to_param }}">Signup to {{ service.name }}</a>
{% endunless %}
</div>
{% endfor %}4.3.4. Styling
Add some final touches to the generated markup, depending on the number of services you have. In the case of this example it’s two, so the CSS code for the service-column div will be:
.service-column {
float: left;
margin-left: 10%;
width: 45%;
}
.service-column:first-child {
margin-left: 0;
}In the example, we’ve used the percentage-based layout to dynamicaly assign the width of the column basic on the containing div’s dimensions.
Now you should have a properly working and good-looking multiple services subscripition page. Congratulations!
If you’d like to display the columns in a specific order, try using conditional expressions (if/else/case) conditioning the service name or another value you know.
Chapter 5. Developer Portal authentication
Follow these steps to configure access to your developer portal.
This article shows how to enable and disable the different types of authentication that can be made available on your developer portal to allow your developers to sign up or sign in.
At the moment, 3scale supports several methods of authenticating to the Developer Portal, which are covered in the following sections:
By default, only one type of authentication will be enabled on your developer portal, two if you signed up on 3scale.net:
- Username/email and password
- Authentication via GitHub (using the 3scale GitHub application) - only enabled by default if you signed up on 3scale.net
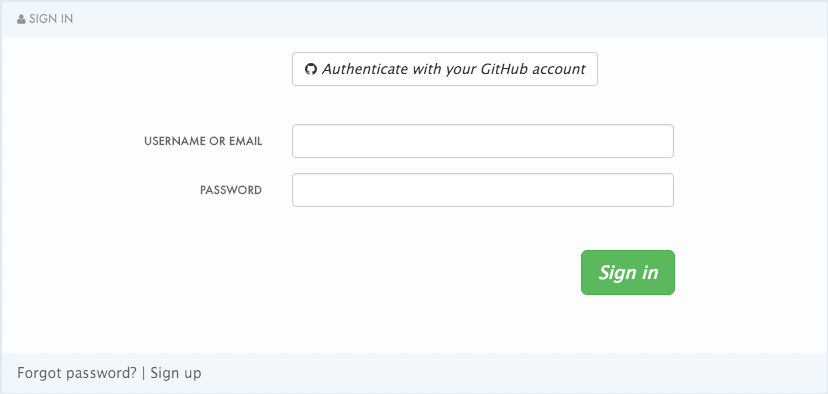
Older 3scale accounts (created prior to December 14th, 2015) might need to follow an extra step in order to enable GitHub and Auth0 authentication.
If this applies to you, you will need to add the following code snippet to the login and signup templates in order to enable this feature in both forms.
{% include 'login/sso' %}5.1. Enabling and disabling username/email and password
By default, the username/email and password authentication is enabled on your developer portal. Usually there is no change to be made here, as this is a standard way for your developers to create an account and to login.
However, in some rare cases you might want to remove this authentication type. To do so, edit the Login > New template as in the screenshot below:
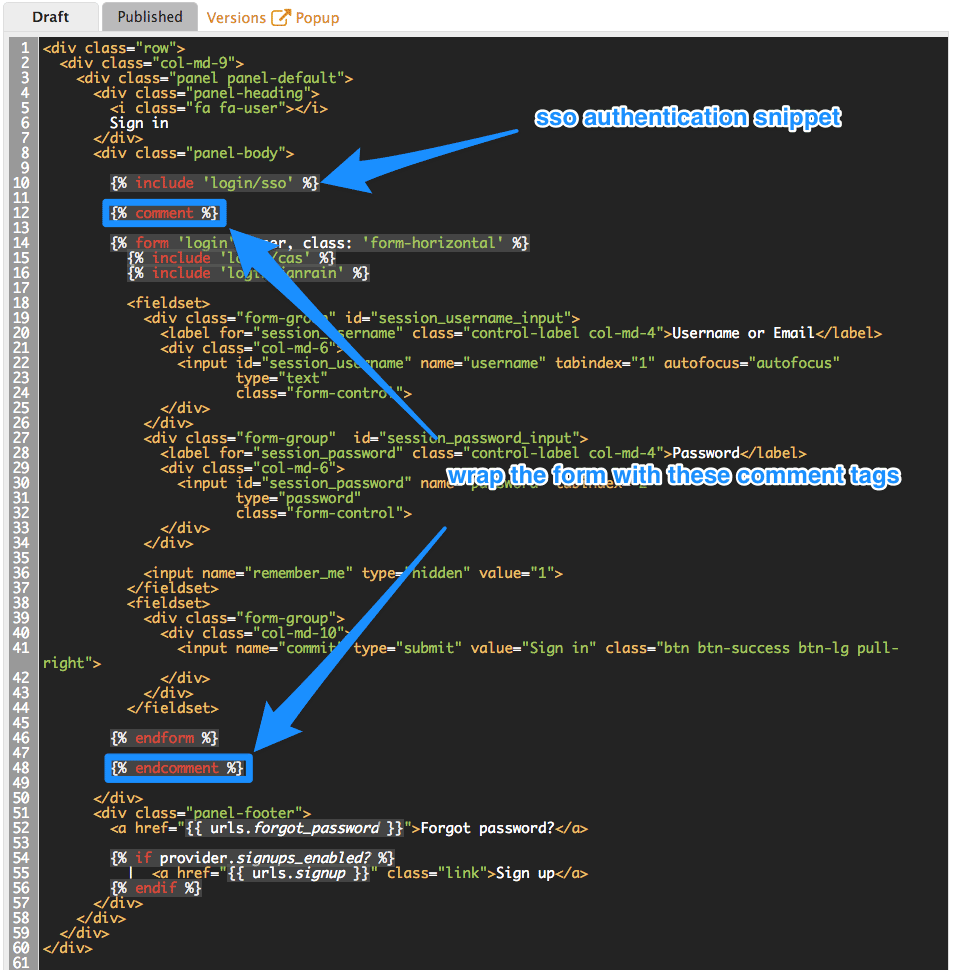
If you need to add back the username/email and password authentication to your developer portal, just remove the liquid comment tags added in the previous step.
5.2. Enabling and disabling authentication via GitHub
In order to enable your own GitHub application, first you will need to create one and retrieve the corresponding credentials.
There are two different ways you can configure authentication via GitHub:
- Using the 3scale GitHub application (enabled by default for hosted 3scale accounts)
- Using your own GitHub application (for on-premises installations)
To make changes to this default configuration, you can go to your 3scale Admin Portal, in Audience > Developer Portal > SSO Integrations you will see the following screen:

Click on GitHub to access the configuration screen:
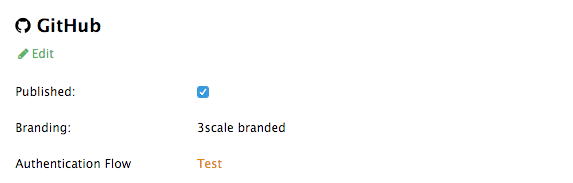
From this screen you can:
- Make the GitHub authentication available or unavailable on your developer portal – to do so, simply check or uncheck the "Published" box.
-
Choose the 3scale branded GitHub application or add your own GitHub application – the 3scale GitHub application is enabled (published) by default. You can configure your own GitHub application by clicking on Edit and entering the details of the OAuth application created in GitHub ("Client" and "Client secret"). Please note that in order to make the integration work properly with your own GitHub application, you should configure the authorization callback URL of your GitHub application using the "Callback URL" that you should see after switching to the "custom branded" option (e.g.
https://yourdomain.3scale.net/auth/github/callback). - Test that the configured authentication flow works as expected.
5.3. Enabling and disabling authentication via Auth0
5.3.1. Note
This feature is only available on the Enterprise plans.
In order to have your developers authenticate using Auth0, you first need to have a valid Auth0 subscription.
Authentication via Auth0 won’t be enabled by default. If you want to use your Auth0 account in conjunction with 3scale to manage the access to your developer portal, you can follow these steps to configure it:
Go to your 3scale Admin Portal, in Audience > Developer Portal > SSO Integrations click on Auth0.

On this configuration screen, you’ll need to add the details of your Auth0 account. Once you’ve entered the client ID, client secret, and site, check the "Published" box and click on Create Auth0 to make it available on your developer portal.
5.4. Enabling and disabling authentication via Red Hat Single Sign-On
This feature is only available on enterprise plans.
Red Hat Single Sign-On (RH-SSO) is an integrated Sign-On solution (SSO) that, when used in conjunction with 3scale, allows you to authenticate your developers using any of the available RH-SSO identity brokering and user federation options.
Refer to the supported configurations page for information on which versions of Red Hat Single Sign-On are compatible with 3scale.
5.4.1. Before You Begin
Before you can integrate Red Hat Single Sign-On with 3scale, you must have a working Red Hat Single Sign-On instance. Refer to the Red Hat Single Sign-On documentation for installation instructions: Installing RH-SSO 7.2
5.4.2. Configuring RH SSO
Perform the following steps to configure Red Hat Single Sign-On:
- Create a realm as described in the Red Hat Single Sign-On documentation.
- Add a client by going to Clients and clicking on Create.
Fill in the form considering the following fields and values:
- Client ID: type the desired name for your client.
-
Enabled: switch to
ON. -
Consent Required: switch to
OFF. - Client Protocol: select openid-connect.
- Access Type: select confidential.
-
Standard Flow Enabled: switch to
ON. -
Root URL: type your 3scale admin portal URL. This should be the URL address that you use to log in into your developer portal, e.g.:
https://yourdomain.3scale.netor your custom URL. Valid Redirect URLs: type your developer portal again by
/*like this:https://yourdomain.3scale.net/*.All the other parameters should be left empty or switched to
OFF.
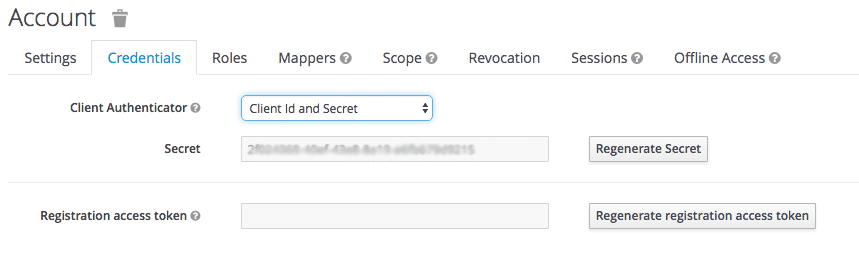
Get the client secret with the following steps:
- Go to the Client you just created.
- Click on Credentials tab.
Select Client Id and Secret in Client Authenticator field.
Configure the
email_verifiedmapper. 3scale requires that theemail_verifiedclaim of the user data is set totrue. In order to map the "Email Verified" user attribute to theemail_verifiedclaim:- Go to the Mappers tab of the client.
Click Add Builtin.
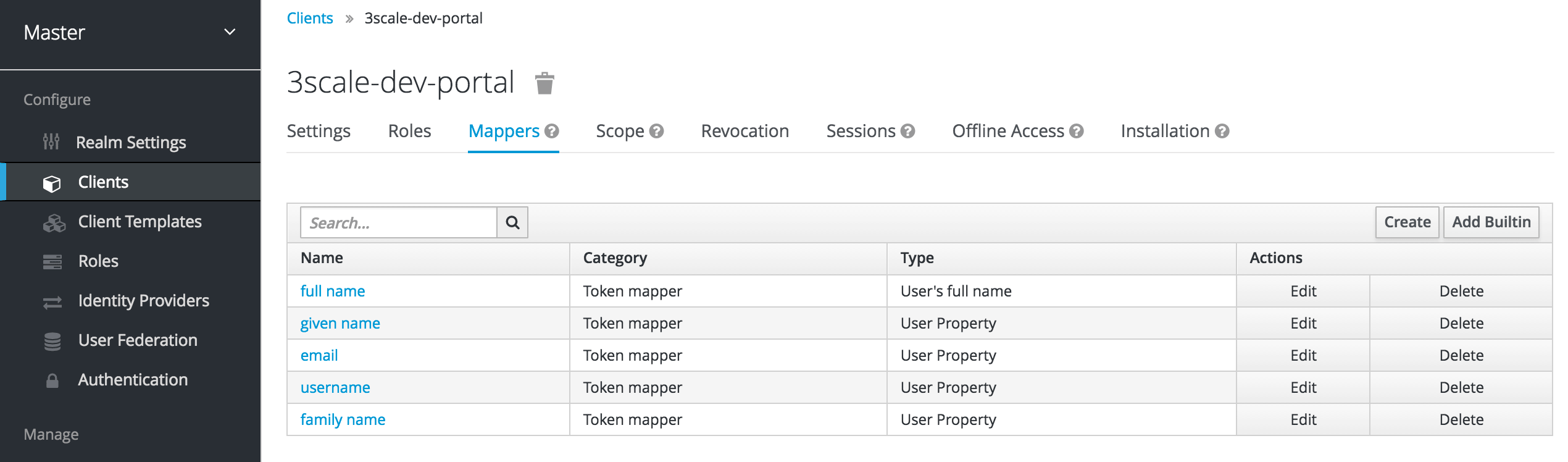
Select the email verified option, and click Add selected to save the changes.
If you manage the users in the Red Hat Single Sign-On local database, make sure that the Email Verified attribute of the user is set to
ON.If you use User Federation, in the client created previously for 3scale SSO integration, you can configure a hardcoded claim by setting the token name to
email_verifiedand the claim value totrue.
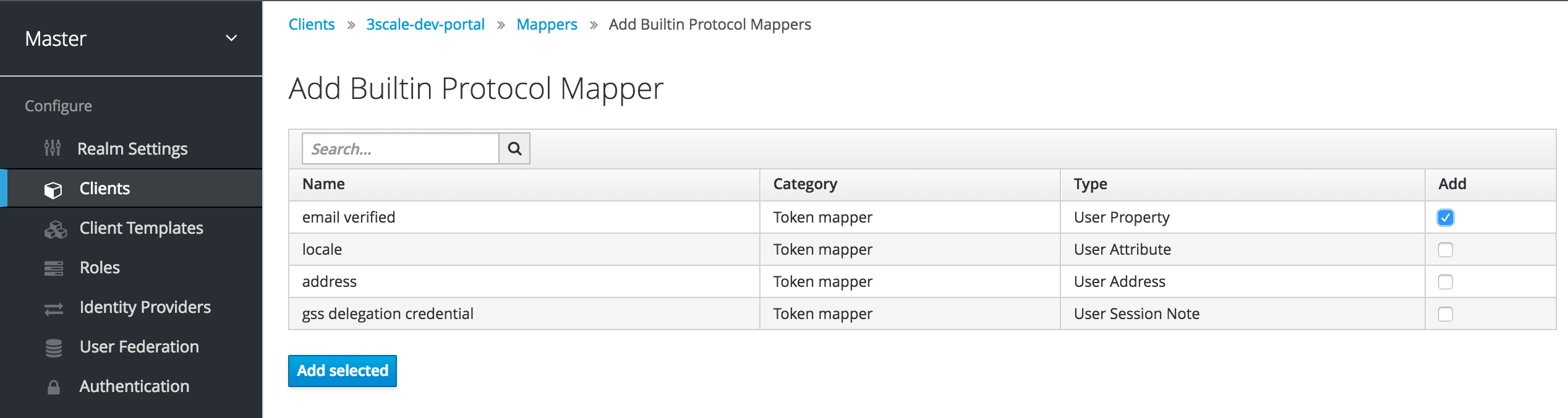
Optionally, configure the
org_namemapper.
When a user signs up in 3scale, the user is requested to fill in the signup form with the Organization Name value. In order to make the signup via Red Hat Single Sign-On transparent for the user by not requiring to fill in the signup form on the developer portal, you need to configure an additionalorg_namemapper:- Go to the Mappers tab of the client.
- Click Create.
Fill the mapper parameters as follows:
-
Name: type any desired name, e.g.
org_name. -
Consent Required: switch to
OFF. - Mapper Type: select User Attribute.
- User Attribute: type org_name.
- Token Claim Name: type org_name.
- Claim JSON Type: select String.
-
Add to ID token: switch to
ON. -
Add to access token: switch to
ON. -
Add to userinfo: switch to
ON. -
Multivalued: switch to
OFF.
-
Name: type any desired name, e.g.
Click Save.
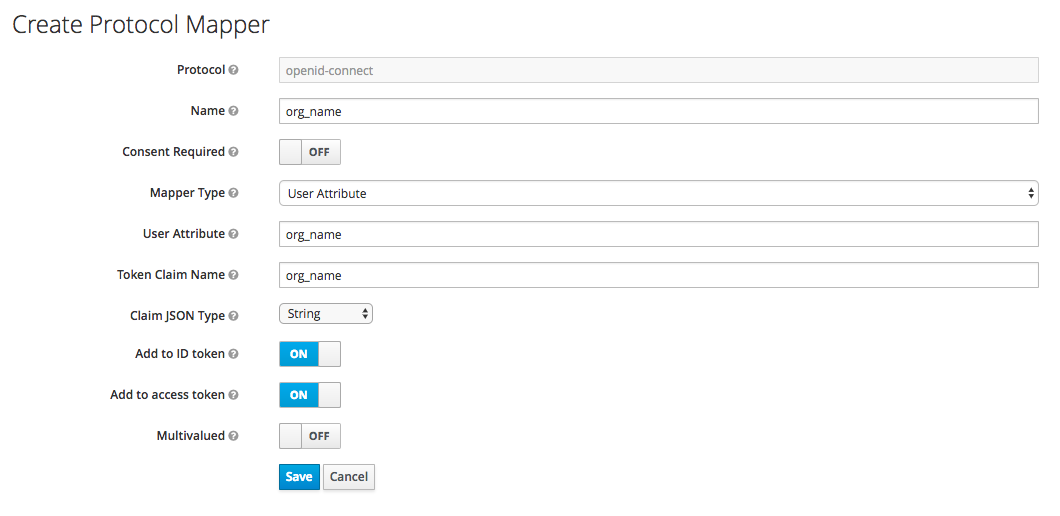
If the users in Red Hat Single Sign-On have the attribute
org_name, 3scale will be able to create an account automatically. If not, then the user will be asked to indicate Organization Name before the account can be created. Alternatively, a mapper of type Hardcoded claim can be created to set the organization name to a hardcoded value for all users signing in with the Red Hat Single Sign-On account.
-
To test the integration, you need to add a user. To achieve this, navigate to Users, click Add user, and fill the required fields. Note that when you create an User in Red Hat Single Sign-On the Email Verified attribute (
email_verified) should be set toON, otherwise the user will not be activated in 3scale.
Using Red Hat Single Sign-On as an identity broker
You can use Red Hat Single Sign-On as an identity broker or configure it to federate external databases. For more information about how to configure these, see the Red Hat Single Sign-On documentation for identity brokering and user federation.
If you decide to use Red Hat Single Sign-On as an identity broker, and if you want your developers to be able to skip both the RH-SSO and 3scale account creation steps, we recommend the following configuration. In the example provided, we are using GitHub as our identity provider.
In Red Hat Single Sign-On, after configuring GitHub in Identity providers, go to the tab called Mappers and click Create.
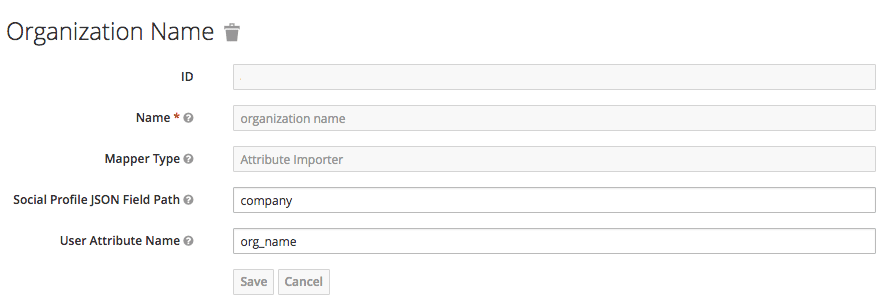
- Give it a name so you can identify it.
- In Mapper Type select Attribute Importer.
- In Social Profile JSON Field Path add company, which is the name of the attribute on GitHub.
In User Attribute Name add org_name, that is how we called the attribute in Red Hat Single Sign-On.
NoteRed Hat Single Sign-On requires first and last name as well as email as mandatory fields. 3scale requires email address, username, and organization name. So in addition to configuring a mapper for the organization name, and for your users to be able to skip both sign up forms, make sure that:
- In the IdP account, they have their first name and last name set.
- In the IdP account, their email address is accessible. E.g. In GitHub, if you set up your email address as private, it won’t be shared.
5.4.3. Configuring 3scale
Authentication via Red Hat Single Sign-On won’t be enabled by default. If you want to use your Red Hat Single Sign-On account in conjunction with 3scale to manage access to your developer portal, you can follow the steps below to configure it.
Go to your 3scale Admin Portal, in Audience > Developer Portal > SSO Integrations click on Red Hat Single Sign-On. (Remember: this is an enterprise only feature so you may have to ask your account manager to enable this for you).
On this configuration screen, you’ll need to add the details of your Red Hat Single Sign-On client that you have configured in the previous step:
- Client: Name of your client in Red Hat Single Sign-On
- Client Secret: Client secret in Red Hat Single Sign-On
- Realm: Realm name and URL address to your Red Hat Single Sign-On
Once you’ve entered those, check the "Published" box and click Create RH-SSO to make it available on your developer portal.
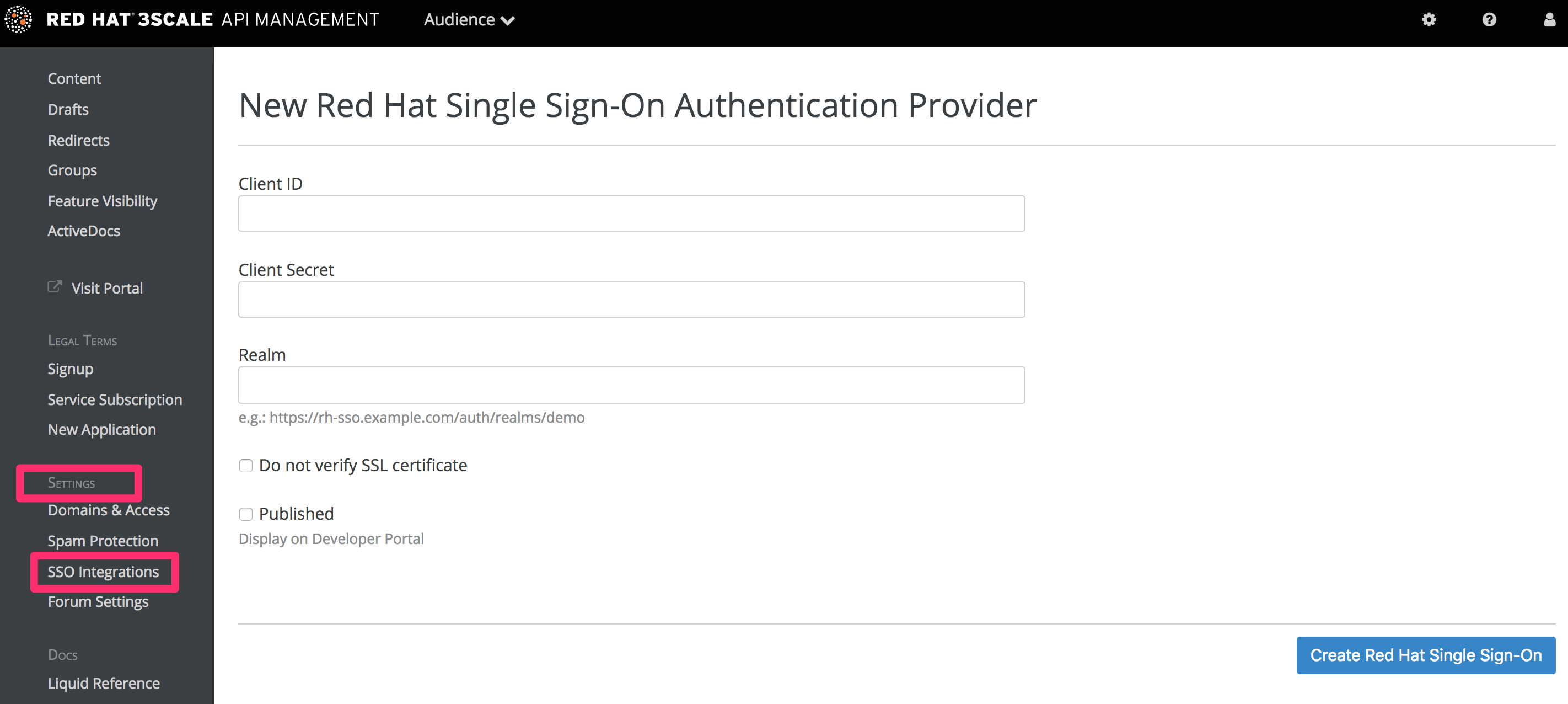
Chapter 6. Red Hat Single Sign On for Developer Portal
Red Hat Single Sign On (RH SSO) allows you to manage access control of multiple independent systems. By following this guide, you’ll be able to allow users that are logged in to your system to log in automatically to your 3scale-powered Developer Portal without being prompted to log in again.
This article shows how existing user credentials of your website can be used to automatically log in to your 3scale-powered Developer Portal.
This feature is meant for API providers that already own the identity of their API consumers (username and password) – such as when the API provider is also the identity provider.
6.1. Creating users in the 3scale platform
First of all, the API consumer must have an account in your Developer Portal. You can import your users to 3scale using the Account Management API or create them manually. Find the Account Management API in the 3scale ActiveDocs, available in your Admin Portal, under the Documentation (question mark icon (?) in the top right corner) → 3scale API Docs section.
6.2. Requesting a login link
Once the user exists, you can use an API request call to generate a URL with a built-in SSO token:
curl -X POST -d "provider_key=YOUR_PROVIDER_KEY&username=USERNAME&expires_in=60" https://YOUR_ADMIN_PORTAL.3scale.net/admin/api/sso_tokens.xml
There are 2 parameters in this call: username to specify who you are requesting the token for and expires_in which is the number of seconds that the token will be valid for (it defaults to 10 minutes).
You can also pass an additional parameter redirect_url with a location to redirect the user after a successful login. This parameter should be percent encoded. The XML response will contain a URL with a secret token included:
<?xml version="1.0" encoding="UTF-8"?> <sso_url> https://YOUR_DEVELOPER_PORTAL/session/create?expires_at=1365087501&token=Q0dNWGtjL2h2MnloR11yWmNwazVZY0NhenlabnBoRUNaNUlyWjZaVG8wMnBGdVNhT0VGN1NUb3FRc1pwSnRrclBZSTIwOUFwRkVTc3NuK1JTbjUrMEE9PS0tY1ZrOGFldzFJNkxna1hrQzQyZ0NGQT09--712f2990ac9248ab4b8962be6467fb149b346000 </sso_url>
You can pass either user_id or username to identify the 3scale user. Typically, the username will be the same for your system and 3scale portal. In that case, using the username should be easy since it does not require any additional information to be stored on your side. However, if you need to do some pairing and machine processes to the URLs anyway, you might be better off with user_id.
6.3. Redirecting users with automatic login
The response contains an RH SSO login URL with a token:
https://YOUR_DEVELOPER_PORTAL/session/create?expires_at=1365087501&token=Q0dNWGtjL2h2MnloR11yWmNwazVZY0NhenlabnBoRUNaNUlyWjZaVG8wMnBGdVNhT0VGN1NUb3FRc1pwSnRrclBZSTIwOUFwRkVTc3NuK1JTbjUrMEE9PS0tY1ZrOGFldzFJNkxna1hrQzQyZ0NGQT09--712f2990ac9248ab4b8962be6467fb149b346000
The URL contains all the required information for the 3scale Developer Portal SSO to log you in. You can embed it directly into web. However, the URL can expire before the user clicks it, so it is recommended to have a generic link on your page that will dynamically request a fresh SSO URL and redirect to it. This way, the user will be seamlessly logged in to the Developer Portal.
The URL address needs to be unescaped. If you want to try it manually in a browser, remember to replace the & with & in your browser. Also any % encodings in the token need to be replaced by their unescaped character.
Chapter 7. Restricted content
Here you can learn how to have content in your Developer Portal that is only visible for some users.
You may need to have some pages of your Developer Portal that are only accessible for a specific group of developers, either part of a page or items in a certain menu. Both goals are achievable through the two techniques introduced below.
7.1. Restricted pages
When creating restricted sections, it is useful to do it so that each section maps to a logical group of users. For this example, assume that there is a group of developers called "partners".
Create a new section in the Developer Portal for every page or group of pages that you want to restrict access to. Uncheck the "public" status field. Then drag and drop any pages you want inside this section.
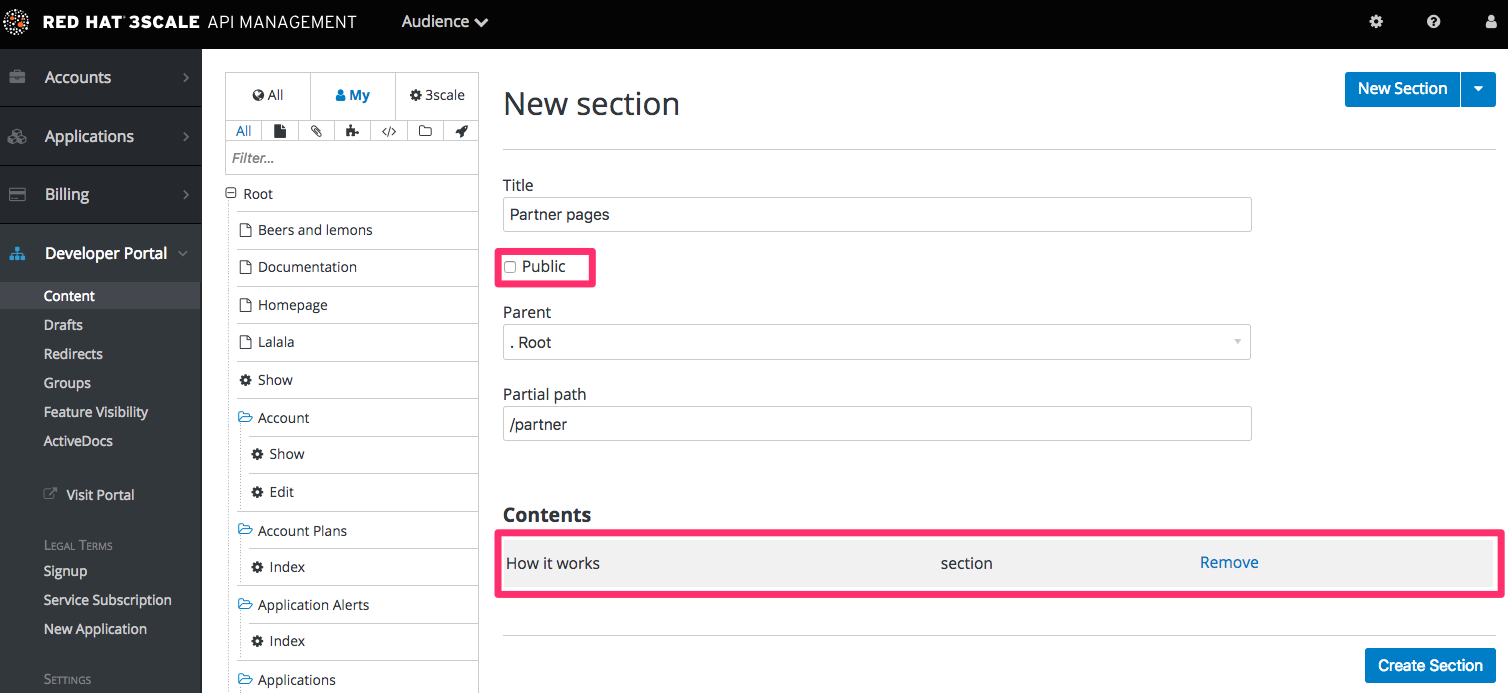
Create a group and give it access to the section you created.
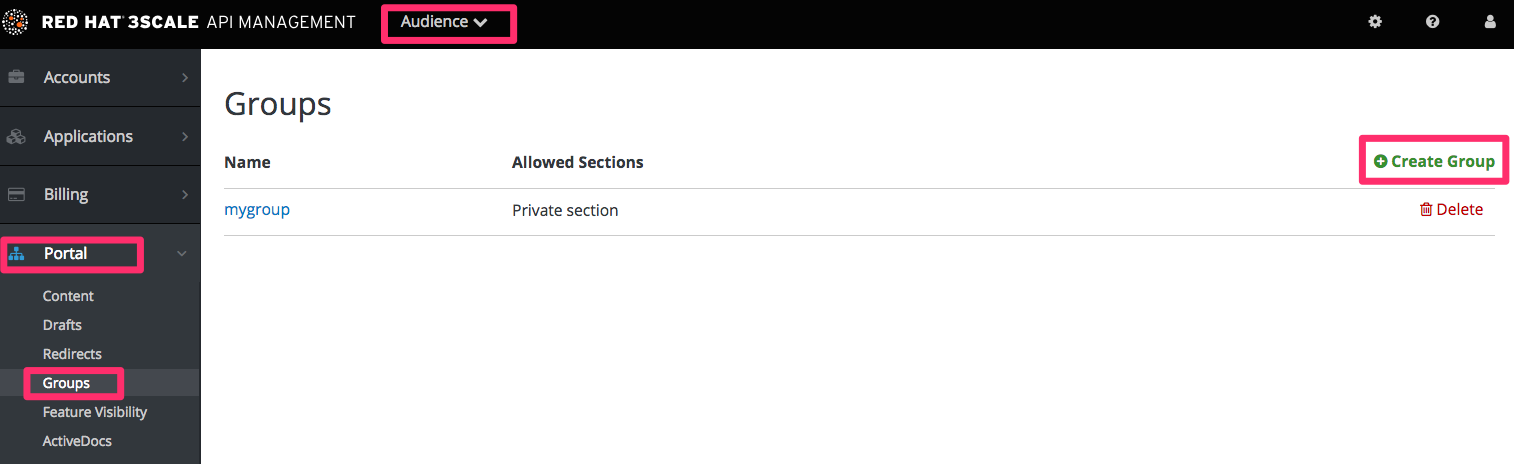
Now every time you have to grant one of your users access to this section, all you have to do is assign them to this group. To do this, go into the corresponding account detail page, then to "Group Permissions." Once there, check the boxes for the sections you want to allow.
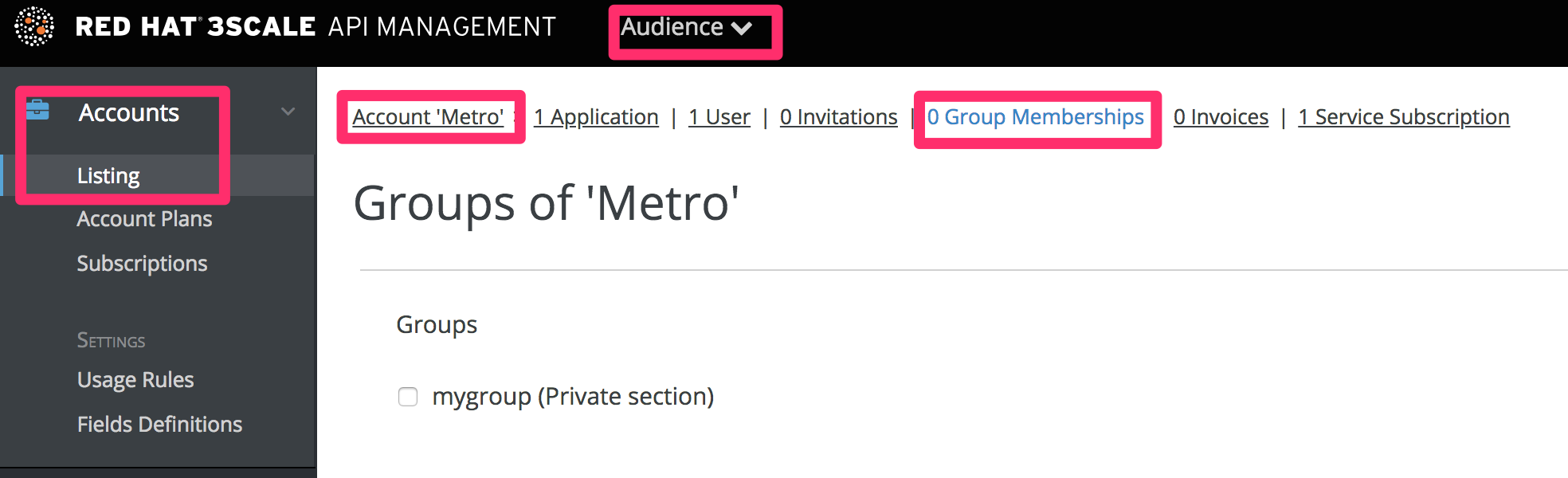
7.2. Restricted blocks of content
Liquid tags are a very powerful way to customize your Developer Portal. Use them here to hide or display parts of a page based on a condition. 3scale allows you to create custom fields for accounts, applications, and users. You can leverage this to store information that is useful for you as the API provider. Here you’ll create an custom field attached to all accounts and use it to indicate whether a given account is a partner or not. You can create this field by going to Audience > Account > Field Definitions. Add a field to the Account section, and mark it as hidden so it will not be displayed on the signup page or anywhere else on the portal.

With the custom field in place, you are now able to show special content to partners by wrapping it in a conditional like in the following snippet:
{{ if current_account.extra_fields.partner == 'true' }}
// content only accessible to partners
{{ endif }}Or use the inverse logic if it suits your case better:
{{ unless current_account.extra_fields.partner == 'true' }}
// content forbidden for partners
{{ endunless }}From here on, whenever you want to show these pieces of hidden content to a user, all you need to do is type in 'true' in the partner field of their account detail page.
7.3. Automating the configuration of extra fields
You can provide access to restricted content to developers based on a change in state. For instance, when they upgrade their application plan.
Streamline the process of access provision by using webhooks together with the Account Management API. The Account Management API is in the 3scale ActiveDocs, available in your Admin Portal:
- Click on Documentation, a question mark icon (?) located in the upper right side of the window.
- Choose 3scale API Docs.
- Get the new plan of the developer who will access the restricted content, by checking the message sent by the webhook request.
- Based on the developer’s new plan, grant access to the private content by calling the API to update the partner field.
7.4. Requiring user login
In addition to the two ways to restrict access to content described above, there is another technique that can be useful: requiring a logged-in user.
This is very easy to achieve using Liquid tags. All you have to do is wrap the content that will be available only for logged-in users inside the following conditional:
{{ if current_user }}
// only visible if the user is logged in
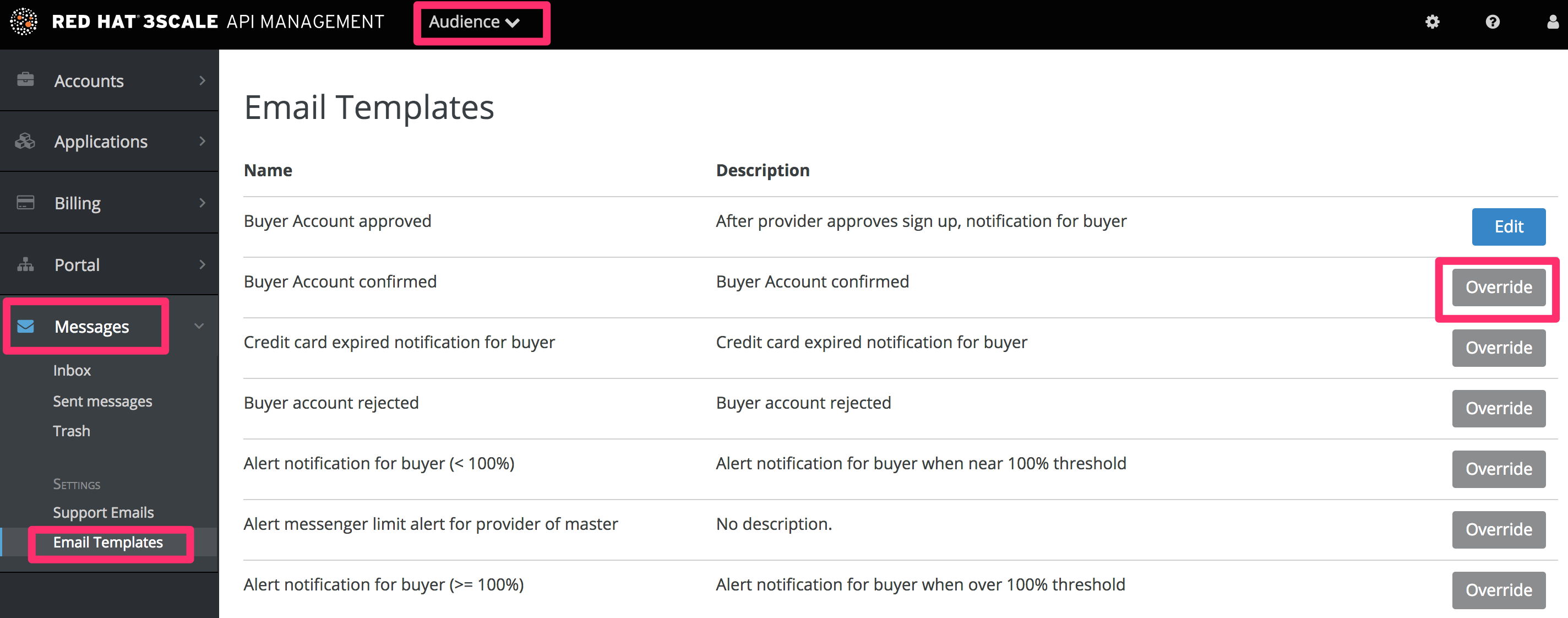
{{ endif }}Chapter 8. Email Templates
By the end of this section, you will have edited and saved a custom email template.
You can completely customize the content of all standard email communication with developers, allowing you to closely match the workflows you’ve set up for your Developer Portal.
8.1. Customizing email templates
8.1.1. Define your workflows before email configuration
There are a lot of email template options, only a subset of which will be relevant for your workflows. Save yourself time by making sure you’re happy with your workflows before beginning to edit the email templates. This way, you’ll only edit the templates that you’ll actually use.
8.1.2. Test your workflow and identify active email templates
Perform a dry run of your finalized workflows, making sure to test all the possible branches (such as approval and rejection). Then, identify each email notification that your test developer account receives to determine what to edit in the next step.
8.1.3. Edit and save your custom template
The first time you edit a template, you’ll actually “create” a custom template. Then in subsequent edits, you’ll save your changes. Warning: there is no version control. We recommend you make a local copy if you want to be able to revert changes.
You can use liquid tags for dynamic content in your email. We especially recommend you make backups when you make changes to the liquid tags.
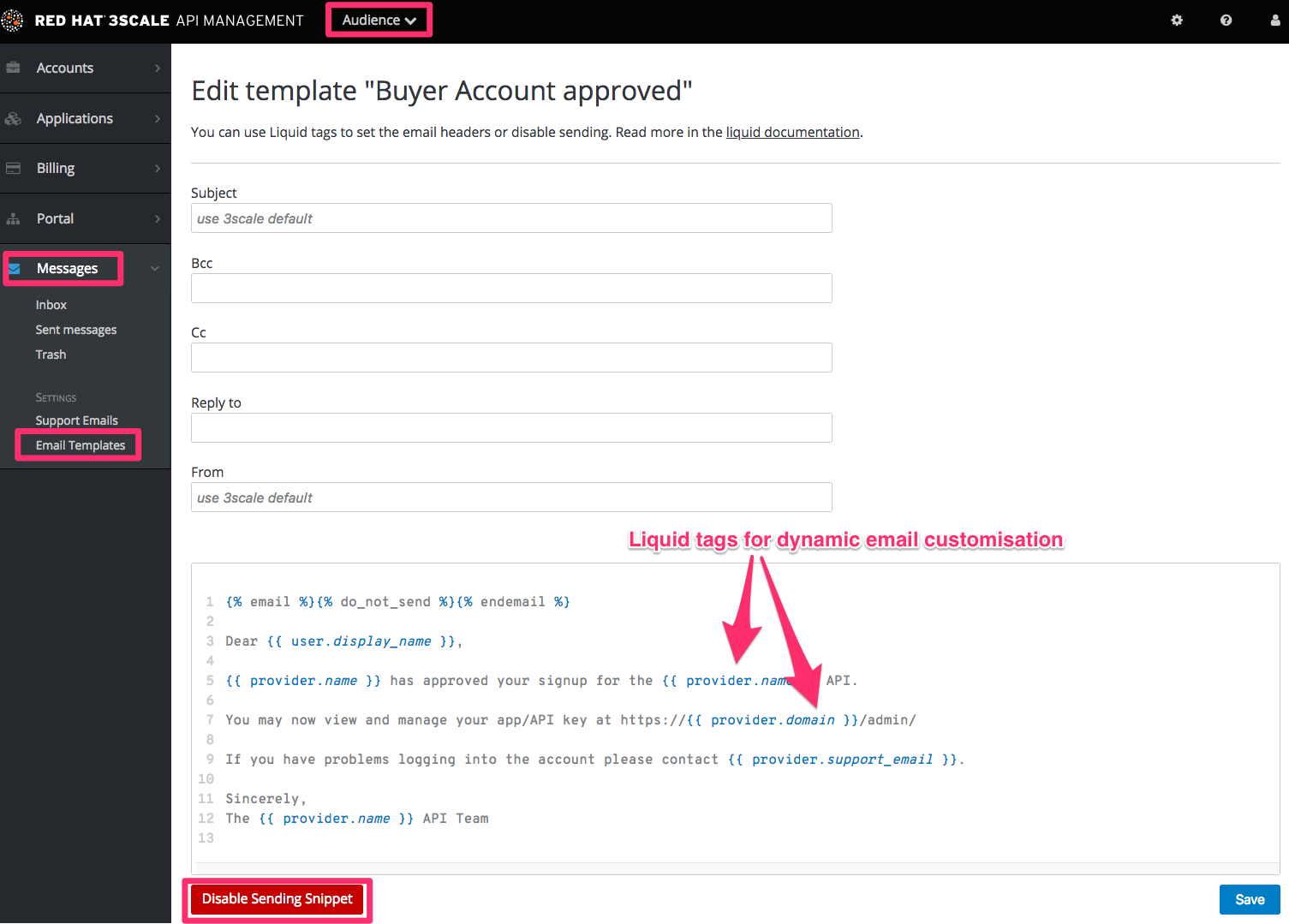
8.1.4. Repeat for all templates in your workflows
Complete these same steps until you’ve covered all possible branches for your workflows.
8.2. More information
- Before customizing your email templates, it’s best to have the signup flows fully finalized and tested.
- If you intend to change any of the liquid tags within the email templates, be sure to read up on the liquid reference documentation.
Chapter 9. Liquids: Developer Portal
This section contains information about Liquid formatting tags and how they work in the 3scale system, including the different elements of the markup, the connections between them, and short examples of how to use them in your Developer Portal.
To learn the basics about Liquids, see the Liquid reference.
9.1. Using Liquids in the Developer Portal
This section explains how to enable liquid markup processing in layouts and pages.
9.1.1. Enabling Liquids
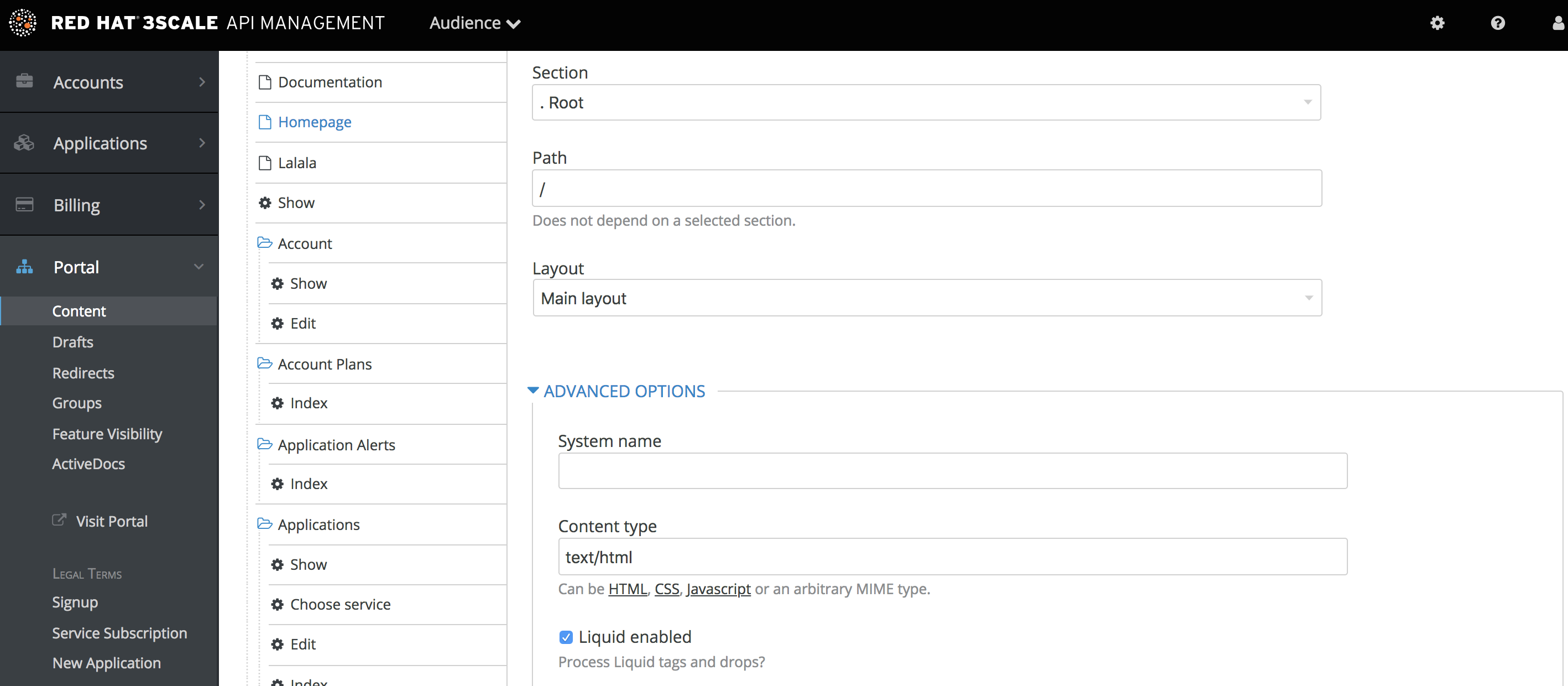
Liquid markup processing is enabled by default for all partials and email templates. Enabling them on layouts is done by ticking the checkbox right under the system_name input field. However, to enable them on pages, you will have to go to the advanced options section of the page.

Just expand the Advanced options section and mark the Liquid enabled checkbox. From now on, all the liquid markup will be processed by the internal engine, and the Developer Portal built-in editor will also add code highlighting for liquid.
9.1.2. Different use on pages, partials, and layouts
The use of liquids usually differs slightly between pages, partials and layouts. Within pages, liquids are single-use elements; while liquids with partials and layouts are the reusable elements of the Developer Portal. This means that instead of applying multiple layouts or partials with small changes to different pages, you can add some logic liquid tags, and alter the layout depending on the page the user is on.
<!-- if we are inside '/documentation' URL -->
<li class="{% if request.request_uri contains "/documentation" %}active{% endif %}"><!-- add the active class to the menu item -->
<a href="/documentation">Documentation</a>
</li>9.1.3. Use with CSS/JS
Liquid markup does not just work with HTML, you can easily combine it with CSS and/or JavaScript code for even more control. To enable liquid in a stylesheet or JS, create them as a page and follow the same steps as if you were enabling it for a normal page. Having done that, you’ll be able to add some conditional markup in CSS or use the server-side data in JavaScript. Just remember to set the content type of the page as CSS or JS.
9.2. Usage of liquids in email templates
This section explains how you can use liquid tags to customize email templates.
9.2.1. Differences from Developer Portal
As previously mentioned, liquid tags can also be used to customize the email templates sent to your users. All the general rules for writing liquid mentioned before also apply to the email templates, with some exceptions:
-
There is no commonly shared list of variables that are available on every template. Instead, you will have to do some testing using the previously mentioned
{% debug:help %}tag. -
Since emails are by nature different from web pages, you will have limited or no access to some tags. For example,
{{ request.request_uri }}will not make sense, as an email does not have a URL.
9.3. Troubleshooting
This troubleshooting section will help you debug and fix typical errors that might occur.
9.3.1. Debugging
If something is not working as intended, but is saved correctly, check the following:
- All the tags are closed correctly
- You are referring to variables available on the current page
- You are not trying to access an array – for example current_account.applications is an array of applications
- The logic is correct
9.3.2. Typical errors and ways to solve them
-
If the document cannot be saved due to a liquid error, it is usually because some tags or drops were not closed correctly. Check that all your
{% %}and{{ }}tags were properly closed and that the logic expressions, for example, if, for and so on, are terminated correctly with endif, enfor. Normally if this is the case, an error will be displayed at the top of the page above the editor with a descriptive error message. -
If everything saved correctly and you do not see any effect, check that you are not referring to an empty element and you are not using a logic tag to display content.
{% %}will never render any content, besides usage in tags which is already an alias of a more complex set of tags and drops. -
If only a
#symbol is displayed, it means that you have tried to display an element that is an array. Check the section on the liquid hierarchy.
9.3.3. Contacting support
If you still have a problem, you can open a new case via the Red Hat Customer Portal.
Chapter 10. Liquids: Email Templates
3scale offers features to customize the email templates with your organization’s own messaging and terminology. You can also take advantage of liquid drops to display personalized information for each of your customers.
Similar to how liquid drops are used in the Developer Portal, every email template has its own context. This means that liquid drops available in one email template may not necessarily be available for other email templates.
This reference outlines which liquid drops are available where, with email templates grouped together by subject matter and the set of liquid drops that they support.
10.1. Account management
These email templates fall under the account management category:
- Buyer Account confirmed
- Buyer Account approved
- Buyer account rejected
For these templates, you can use the following liquid drops:
-
user ⇒ User -
domain ⇒ String -
account ⇒ Account -
provider ⇒ Provider -
support_email ⇒ String
Additionally, the following template:
Password recovery for buyer
has access to the these liquid drops:
-
user ⇒ User -
provider ⇒ Provider -
url ⇒ url
The email to invite additional users to an account:
Invitation
has access to:
-
account ⇒ Account -
provider ⇒ Provider -
url ⇒ url
10.2. Credit card notifications
- Credit card expired notification for provider
- Credit Card expired notification for buyer
You can use the following liquid drops:
-
user_account ⇒ Account -
account ⇒ Account -
provider_account ⇒ Provider -
provider ⇒ Provider
10.3. Limit alerts
- Alert notification for provider (>= 100%)
- Alert notification for buyer (>= 100%)
- Alert notification for provider (< 100%)
- Alert notification for buyer (< 100%)
have access to:
-
application ⇒ Application -
account ⇒ Account -
provider ⇒ Provider -
service ⇒ Service -
alert ⇒ Alert
10.4. Applications
The following email templates all deal with application and application plan notifications.
- Application created for provider
They have access to:
-
url ⇒ url
Application plan change request notification email templates:
- Plan change request for buyer
- Plan change request for provider
They have access to:
-
application ⇒ Application -
provider ⇒ Provider -
account ⇒ Account -
user ⇒ User -
plan ⇒ Plan -
credit_card_url ⇒ credit_card_url
The following email templates contain a number of available drops, such as:
- Application plan changed for buyer
- Application plan changed for provider
- Application trial period expired for buyer
They have access to:
-
provider ⇒ Provider -
account ⇒ Account -
user ⇒ User -
plan ⇒ Plan
As well as all of the above liquid drops, the following application plan messages…
- Application suspended for buyer
- Application accepted for buyer
- Application rejected for buyer
- Application contract cancelled for provider
have the additional liquid drops listed
-
application ⇒ Application -
service ⇒ Service
More liquid drops accumulate for the following email templates for application keys:
- Application key created for buyer
- Application key deleted for buyer
-
key ⇒ key
10.5. Invoicing
The following email template…
- Review invoices prior to charging for provider
has access to:
-
provider ⇒ Provider -
url ⇒ String>
Additionally, the following templates…
- Invoice charge failure for provider without retry
- Invoice upcoming charge for buyer
- Invoice charge failure for provider with retry
- Invoice charge failure for buyer without retry
- Invoice charged successfully for buyer
- Invoice charge failure for buyer with retry
share the following liquids:
-
account ⇒ Account -
provider ⇒ Provider -
cost ⇒ cost -
invoice_url ⇒ invoice_url -
payment_url ⇒ payment_url
10.6. Services
The following email templates:
- Service contract cancelled for provider
- Service trial period expired for buyer
- Service plan changed for provider
- Service contract suspended for buyer
have access to:
-
provider ⇒ Provider -
account ⇒ Account -
user ⇒ User -
plan ⇒ Plan
As well as the above liquid drops, the following service templates…
- Service created for provider
- Service accepted for buyer
- Service rejected for buyer
have the additional liquid drops listed:
-
service ⇒ Service -
service_contract ⇒ Contract -
subscription ⇒ Contract
10.7. Signup
The following email templates…
- Sign-up notification for provider
- Sign-up notification for buyer
have access to:
-
user ⇒ User -
provider ⇒ Provider -
url ⇒ activate_url
Chapter 11. Customizing the Developer Portal layout
You can customize the look and feel of the entire Developer Portal to match your own branding. A standard CSS stylesheet is available to provide an easy starting point for your customizations.
In this tutorial, you’ll add your own CSS customizations to your Developer Portal and reload it to put your new styling changes live.
11.1. Creating a new CSS file
There is a default stylesheet, default.css. It is quite large and complex, so rather than extend it, it’s better to create your own stylesheet for any of your own customizations to overwrite the defaults. You create a new stylesheet the same way you create a page (just remember to choose an appropriate MIME content type in the advanced page settings).
It’s important that the selected layout is blank. Otherwise the page layout HTML will obscure the CSS rules.
11.2. Linking the stylesheet into your page layout
Add the link to your custom CSS in each of your layout templates (or in a partial if you have a common HEAD section) after the link to bootstrap.css. For example:
<link rel="stylesheet" href="/stylesheets/custom.css">
Now enjoy the beauty of your own unique branding!
Chapter 12. Change built-in pages
By the end of this section, you will be able to modify, and configure the visibility of any element in the system-generated pages.
Some elements generated by the system are not possible to modify from the Developer Portal, such as the Signup, Dashboard, and Account pages. This guide shows how to customize with CSS and JavaScript the content on these pages.
The 3scale system-generated pages are subject to change (although infrequently). These changes may break any customizations that you implement following this guide. If you can avoid using these hacks, please do so. Before you continue, please be sure that you’ll be able to monitor for any disruptive changes and do the necessary maintenance work to keep your portal functioning correctly.
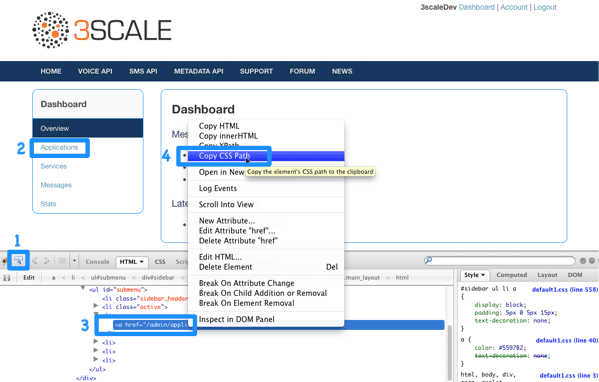
12.1. Identify the elements
The first and most important thing to do is identify what you want to hide. To do that, use Firebug (or any other developer tools such as Chrome Developer tools or Opera Dragonfly). Choose the desired element, and in the console, right click on it and select Copy CSS path. This way you save the exact CSS path to make it easy to manipulate. Remember, if the element is a part of the sidebar navigation widget, you’ll also have to specify which position in the list. For this, you can use either the "+" selector (for example, to choose 3rd li element: ul + li + li + li) or the :nth-child(n) CSS3 pseudoclass.
12.2. Modify or hide the elements
Now, having identified the elements, you can change their display settings. Depending on the type of element, you can choose from two possible methods: CSS manipulation or jQuery script. CSS manipulation is more lightweight and reliable, but doesn’t work well for some kinds of elements that exist on a number of pages (for example, the 3rd element in the sidebar of the Admin Portal’s Dashboard also exists in the Account section but has a different value). Some trickier implementations require use of CSS3 which is not supported by old browsers. In the next two steps, you’ll see both of these approaches.
12.3. Option A: CSS
As an example, try to hide the latest element from the Dashboard page. Following the first step, you have identified its CSS path as:
#three-scale .dashboard_bubble
Keep in mind that it’s the second box with the same path, so you’ll use the "+" selector. Your path will now look like this:
.main_layout #three-scale .dashboard_bubble + .dashboard_bubble /* or */ .main_layout #three-scale .dashboard_bubble:nth-child(1)
Changing display property to none makes that box invisible:
.main_layout #three-scale .dashboard_bubble:nth-child(1) {
display: none;
}12.4. Option B: jQuery
If you have a trickier element to hide such as a sidebar menu element, it’s better to use some jQuery. The CSS path of these elements is identical on the Dashboard and Account sections, and you don’t want to hide elements in both sections. So choose the element based on the CSS path and the content. In this example, assume you want to hide the messages section from the Dashboard’s sidebar. Your CSS path is:
#three-scale #submenu li a
In order to match the content, you’ll use the .text() function. You’ll also include the code inside the document’s head and inside the ready function so it’s executed after all the content has been generated.
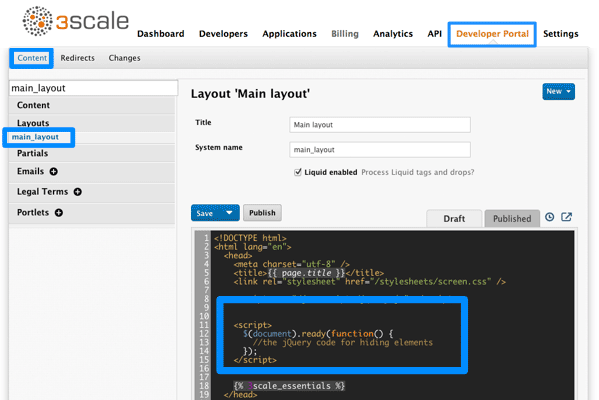
The resulting code snippet will look like this:
$(function() {
$('#three-scale #submenu li a').each(function() {
if ($(this).text() == "Messages")
$(this).parent().css('display', 'none');
});
});This is not the only solution. It just shows one possible way of doing it. The same example could be done using pure CSS with CSS3 selectors basing on the attributes values. For the complete CSS3 selectors specification, take a look here.
Chapter 13. Webhooks
By the end of this section, you will be able to configure and take action on the webhooks in the Developer Portal.
The use of webhooks allows you to tightly integrate 3scale with your back-office workflow. When specified events happen within the 3scale system, your applications will be notified with a webhook message, and you can use the data such as from a new account signup to populate your Developer Portal.
13.1. Introducing webhooks
A webhook is a custom HTTP callback triggered by an event selected from the available ones in the Webhooks configuration window. When one of these events occurs, the 3scale system makes an HTTP or HTTPS request to the URL address specified in the webhooks section. On your end, you can configure the listener to invoke some desired behavior such as event tracking.
To configure webhooks:
- Navigate to Account Settings > Integrate > Webhooks. Account Settings is the gear icon located in the upper right of the window.
Indicate the behavior for webhooks. There are two options:
- Webhooks enabled: Select this checkbox to enable or disable webhooks.
Actions in the admin portal also trigger webhooks: Select this checkbox to trigger a webhook when an event happens. Consider the following:
- When making calls to the internal 3scale APIs configured with the triggering events, use an access token; not a provider key.
- If you leave this checkbox cleared, only actions in the Developer Portal trigger webhooks.
- Specify the URL address for notification of the selected events when they trigger.
- Select the events that will trigger the callback to the indicated URL address.
Once you have configured the settings, click Update webhooks settings to save your changes.
13.2. Webhooks format
The format of the webhook is always the same. It makes a post to the endpoint with an XML document of the following structure:
<?xml version="1.0" encoding="UTF-8"?>
<event>
<type>application</type>
<action>updated</action>
<object>
THE APPLICATION OBJECT AS WOULD BE RETURNED BY A GET ON THE ACCOUNT MANAGEMENT
API
</object>
</event>Each element provides information:
-
<type>: Gives you the subject of the event such as application, account, and so on. -
<action>: Specifies what has been done, by using values such as updated, created, deleted. - `<object>: Constitutes the XML object itself in the same format that is returned by the Account Management API. To check this, you can use our interactive ActiveDocs.
If you need to provide assurance that the webhook was issued by 3scale, expose an HTTPS webhook URL and add a custom parameter to your webhook declaration in 3scale. For example: https://your-webhook-endpoint?someSecretParameterName=someSecretParameterValue. Decide on the parameter name and value. Then, inside your webhook endpoint, check for the presence of this parameter value.
13.3. Troubleshooting
If you experience an outage for your listening endpoint, you can recover failed deliveries. 3scale will consider a webhook delivered if your endpoint responds with a 200 code. Otherwise, it will retry 5 times with a 60 seconds gap. After any recovery from an outage, or periodically, you should run a check and if applicable clean up the queue. You can find more information about the following methods in ActiveDocs:
- Webhooks list failed deliveries
- Webhooks delete failed deliveries
Chapter 14. Setting terms and conditions
When you allow developers to sign up for your API, you will probably want to get them to agree to your Terms and Conditions to make some of your policies clear before you grant them access.
There may be different versions of your Terms and Conditions you want developers to abide by. These are easy to set up at different points throughout the registration process. For example:
- Signup Terms and Conditionss
- Application Terms and Conditions
- Service/subscription Terms and Conditions (only available when you have multiple services)
Additionally, if you are charging for use of your API, you may want to make your credit card policies explicit. 3scale provides an easy way to set up the following kinds of credit card policy URLs:
- Legal Terms
- Privacy
- Refunds
14.1. Terms and conditions
This part of the workflow is easy to set up in the Admin Portal by following the steps below.
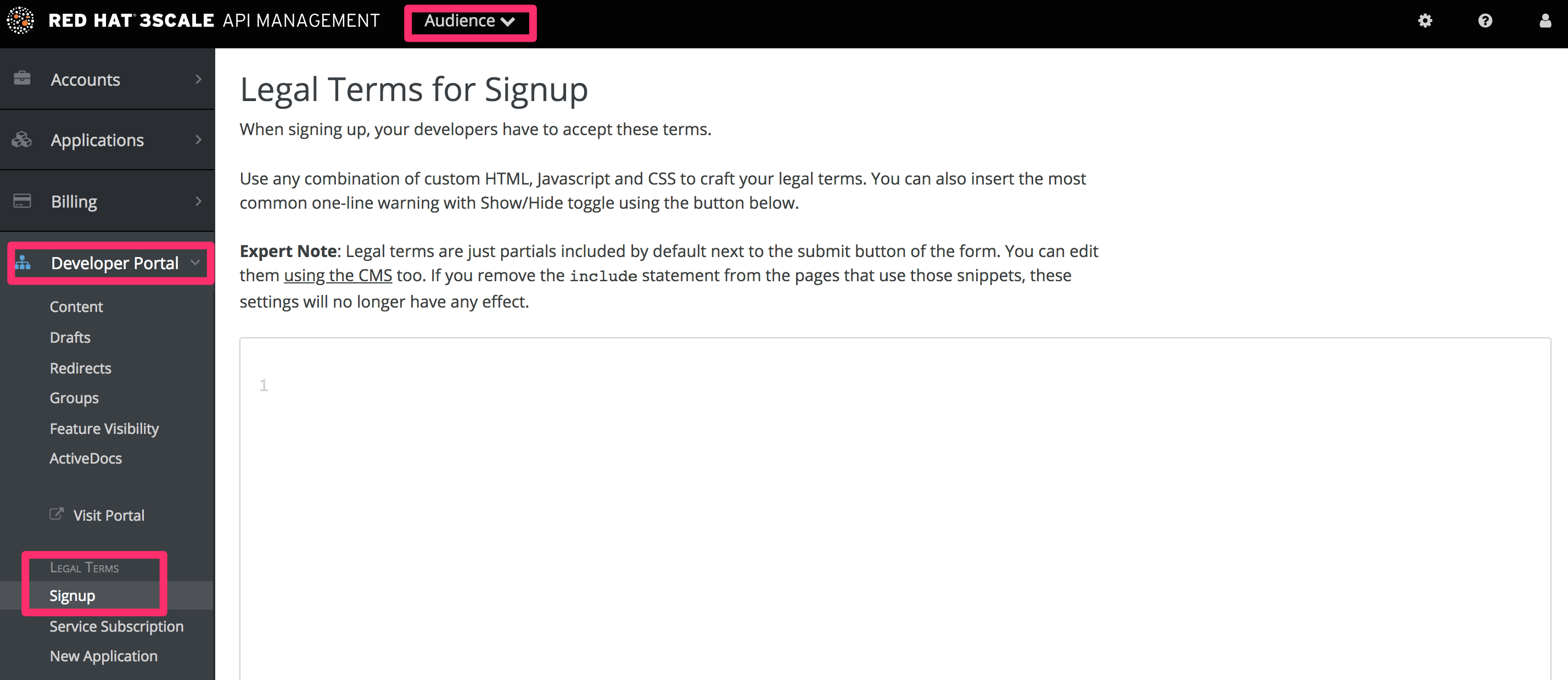
Go to Audience > Developer Portal > Signup, where you will be presented with a blank page to populate with your signup legal terms. You can use any combination of HTML, JavaScript, and CSS. There is also some toggling code provided by clicking Insert toggling code. The content you write in this box will appear just above the Sign Up button on the Signup page of your Developer Portal.
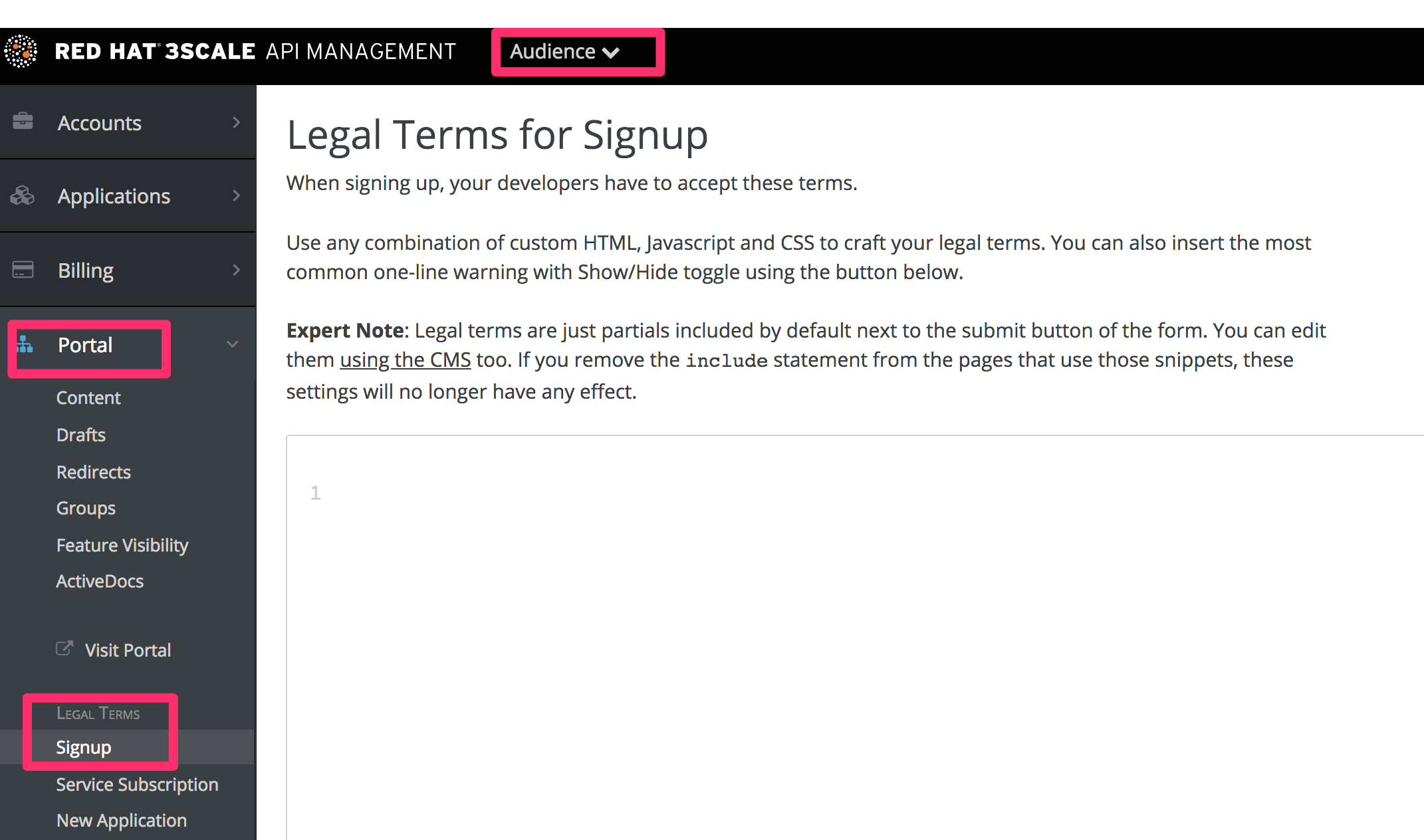
Once you have filled out your Terms and Conditions, save them by clicking Update.
If you have used the toggling code, it will display "By signing up you agree to the following Legal Terms and Conditions" followed by a link that toggles between showing and hiding the Terms and Conditions you specified.
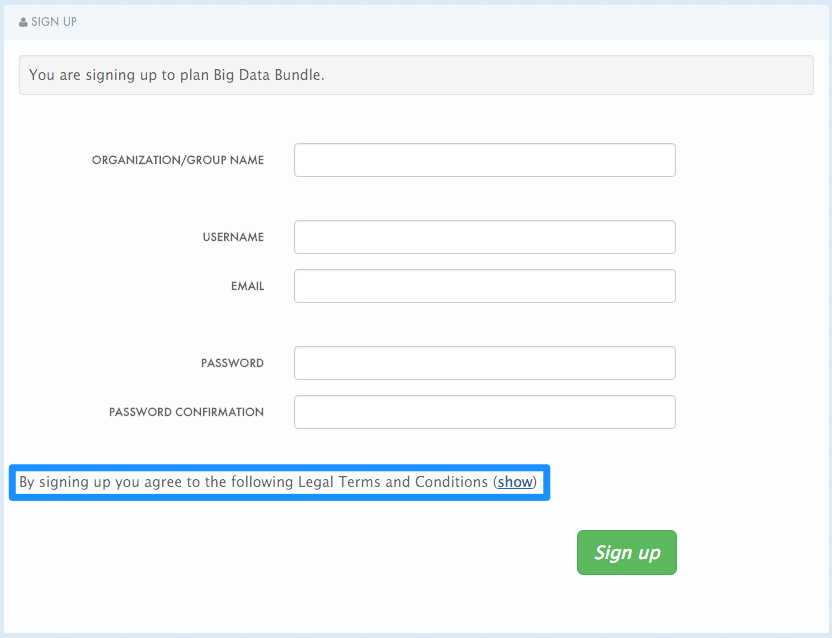
This is placed on the Signup page by default, but it is a partial (signup_licence) that can be included anywhere on your Developer Portal. To remove this from the Signup page, simply remove the {% include 'signup_licence' %} line from the page. Similarly, if you want to include it somewhere else, you can use the same partial by means of the snippet, which can be placed anywhere on your Developer Portal.
You might also want your users to accept another set of Terms and Conditions when they create a new application (new_application_licence partial) and/or when they subscribe to a new service (service_subscription_licence partial). To set these up, you can follow the same procedure outlined above.
14.2. Credit card policies
You can also define other URLs where different policies reside. Set them up by going to Audience > Billing > Credit Card Policies and setting the path where your policy pages will be located.
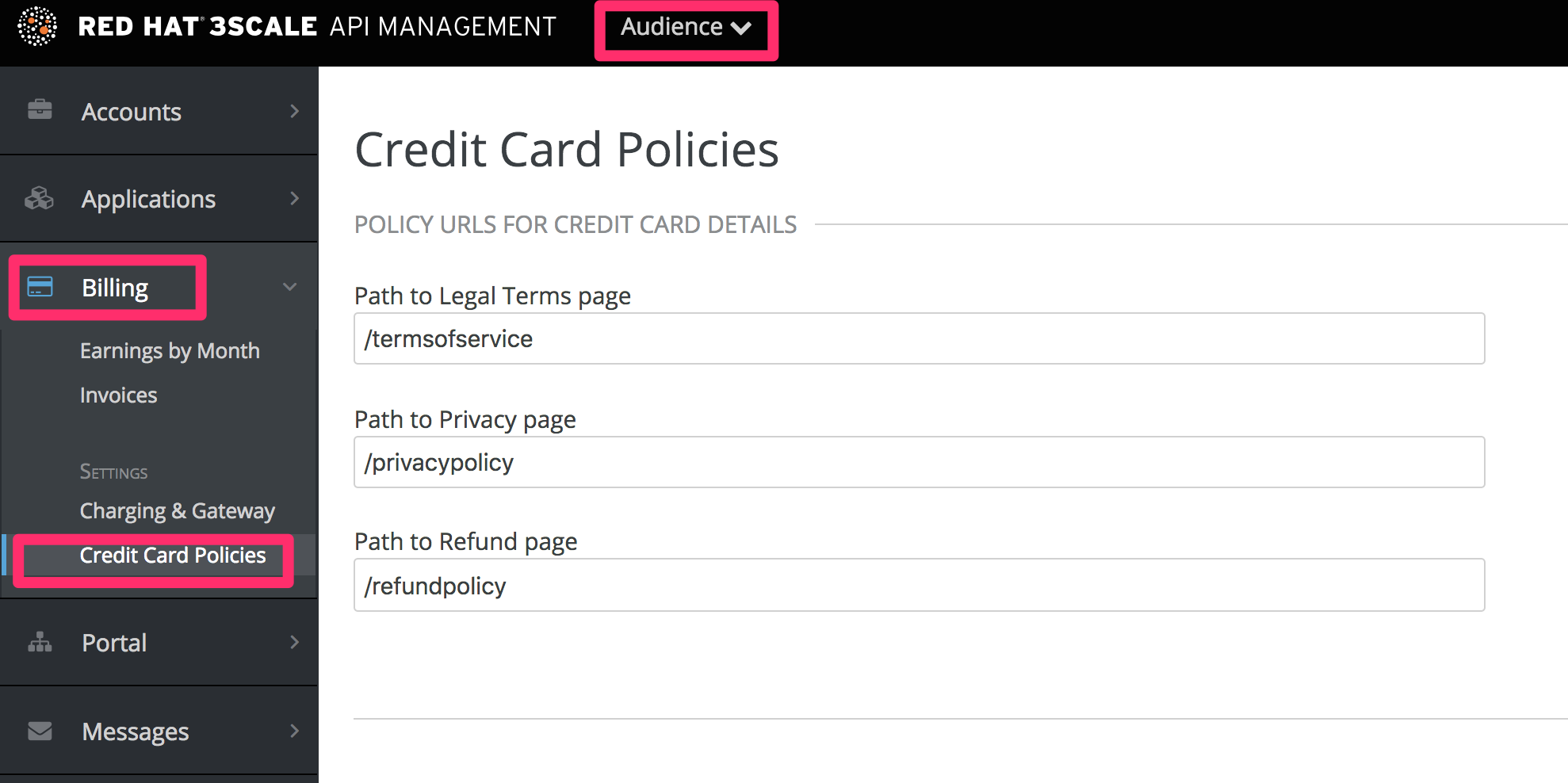
In order for these links to work, you will then need to create new pages in the Developer Portal.
Once that is done, you can reference them using the URL’s liquid drop. For example:
<a href="{{ urls.credit_card_terms }}">Legal Terms</a>
<a href="{{ urls.credit_card_privacy }}">Privacy</a>
<a href="{{ urls.credit_card_refunds }}">Refunds</a>And that’s it!
Chapter 15. Summary: from zero to hero Developer Portal
Most best practice reviews of API deployments agree that a well structured developer portal and great documentation are key elements to assure adoption. Your developer portal is not only a source of documentation. It is also your main hub to manage interactions with developers and for developers to access to their API keys in a secure way.
15.1. Goal
By the end of this tutorial, you will have a Developer Portal up and running to promote your API, allow developers sign up for accounts, and access their API keys.
15.2. Configuring your Developer Portal
15.2.1. Planning your portal concept
From early stages, it is a good idea to plan out the concept for your Developer Portal. The most important elements to consider in your plan include:
- Site map: A skeleton of what the portal structure will be.
- Top menu bar: The navigation that will be repeated on every page.
- Side menu bars: To access to individual pages within each section.
- Page layout guidelines: To give your portal a consistent look and feel.
15.2.2. Setting up the editing environment
The best setup of your editing environment has proven to be:
- A tab showing yourcompany-admin.3scale.net/p/admin/cms logged in with your admin credentials, which gives access to Developer Portal for the portal
- Second tab pointing to yourcompany.3scale.net, the public view of your portal (if you access this though the Site link, you don’t have to worry about the access code)
In the Admin Panel, you can see all your developer portal’s elements in the left sidebar:
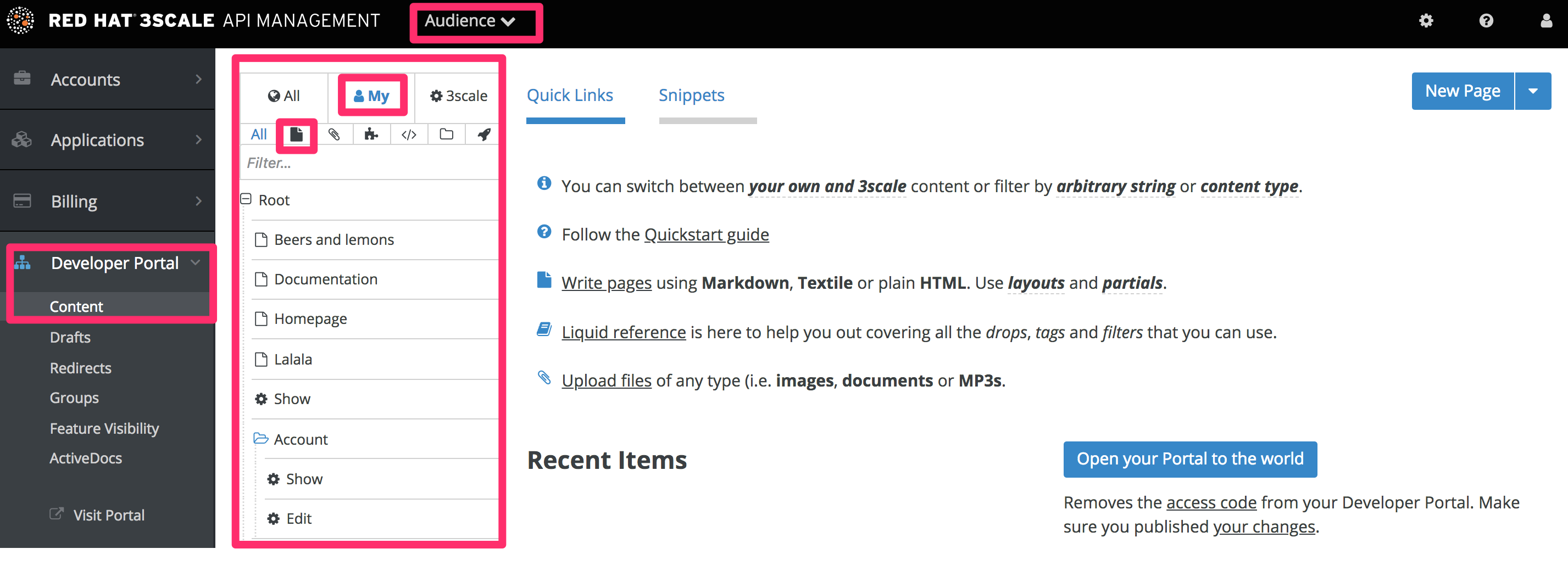
15.2.3. Defining the page layout templates
The general idea is to define a separate layout for each of the different page styles in your portal. There is one standard layout called “main layout” when you start. It’s best not to make any changes to this until you are quite expert at using the Developer Portal because this is used by all the system-generated pages. Usually you’ll want to have a unique style for the home page of your portal.
The main layout template will be a starting point for your customizations. Create a new layout, and copy/paste the content of main layout into it.
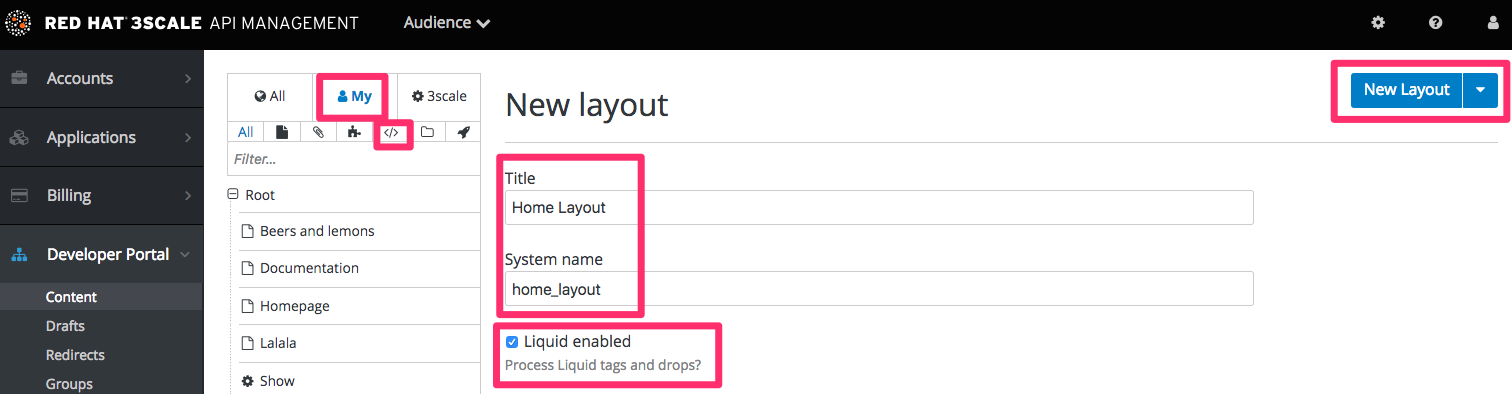
Remove the sidebar menu by deleting this line from your “home layout”:
{% include 'submenu'%}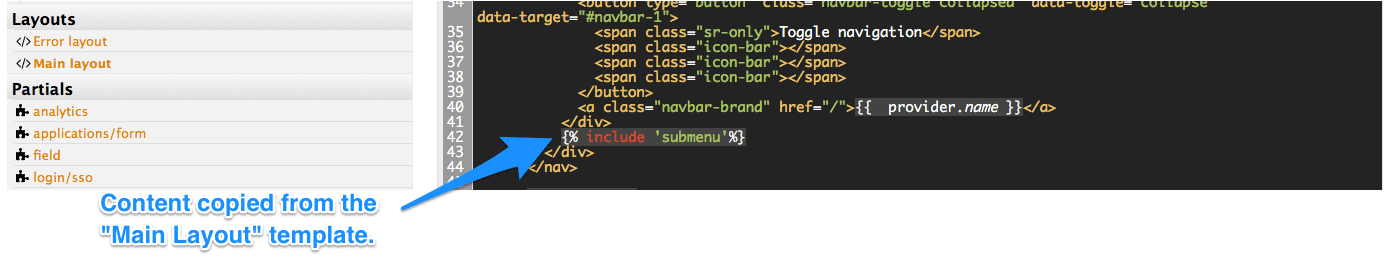
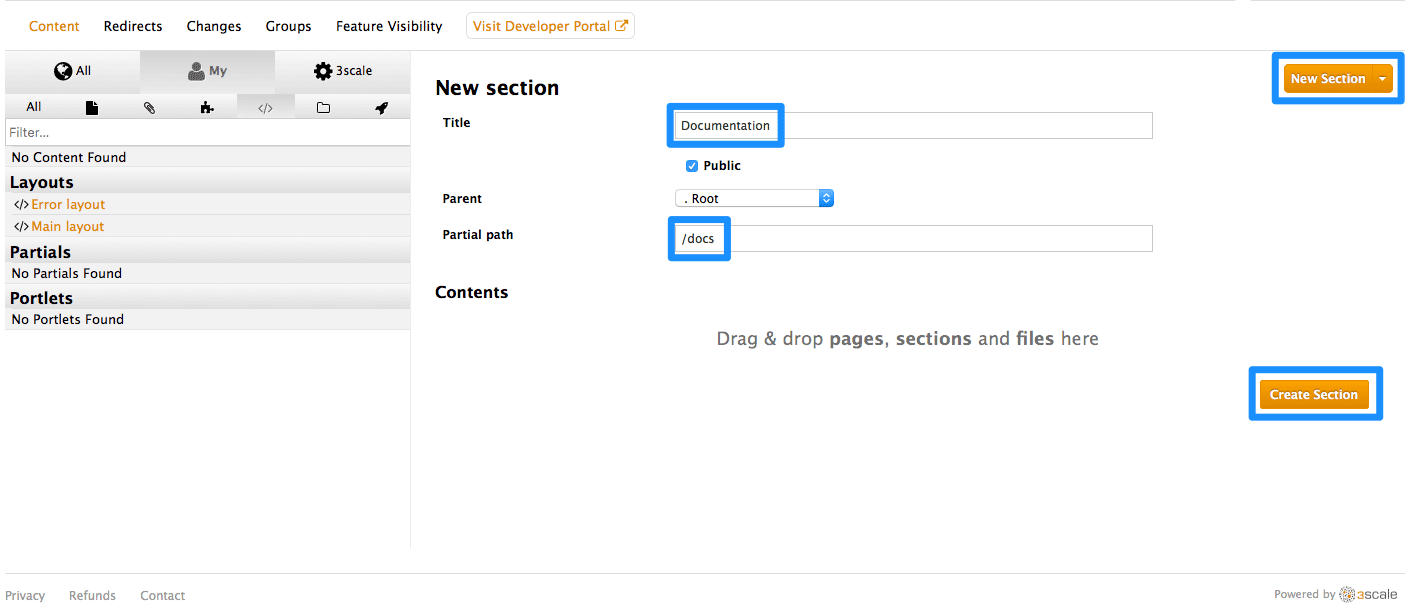
15.2.4. Creating your page hierarchy
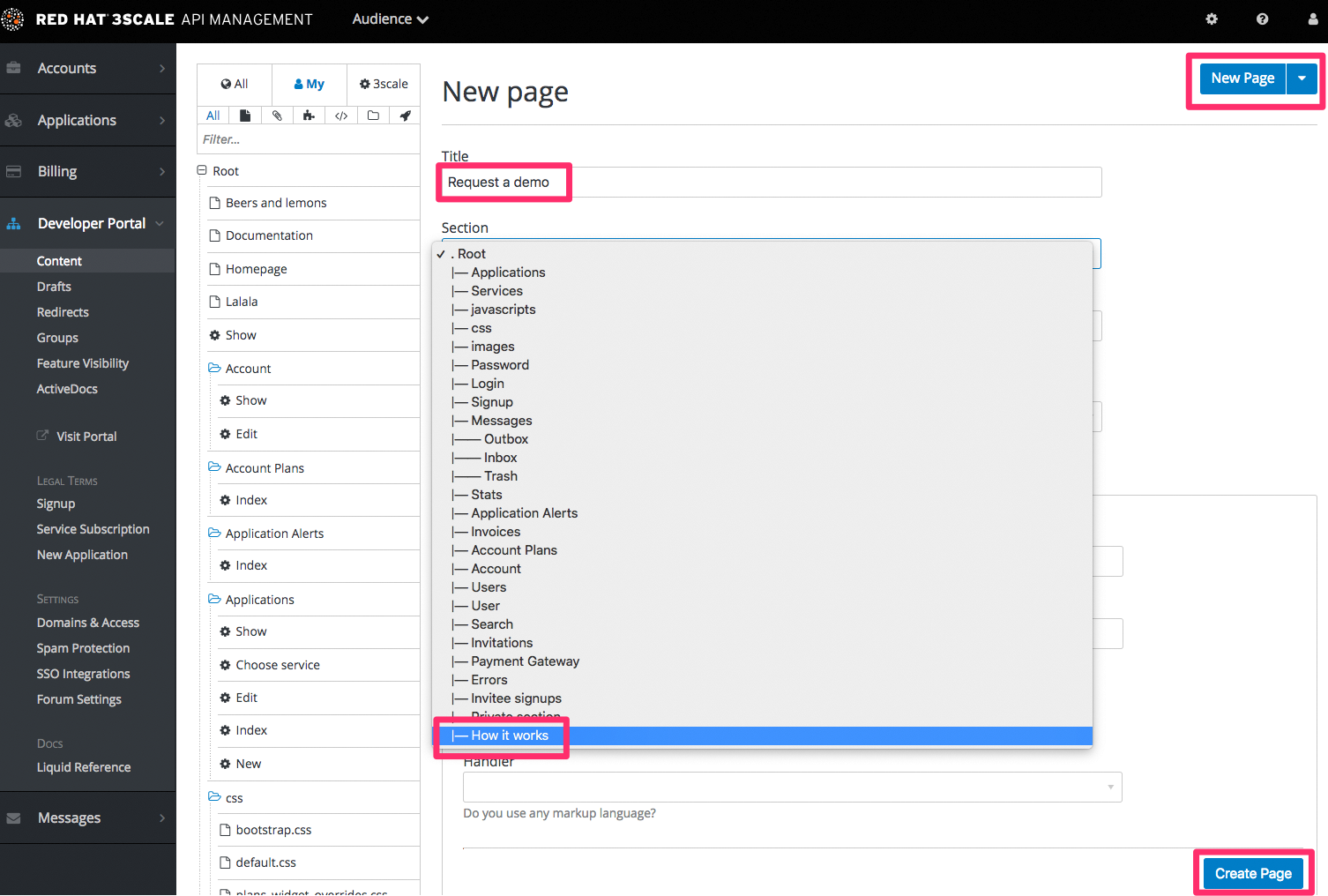
Begin at the root level in the site map, and add a new section for each of your top menu items (add sections by expanding the “new” button on the righthand side). Assign a title, parent section, and the path.
Similar to adding a section, add a page. Choose the desired section in order to structure your URL paths consistently. Next, select the layout that the page will be using. After completing the page content, hit “create page”. If you are writing a lot of content, you may prefer to use a markup language like Textile or Markdown, which you can select in the advanced page settings.
View the draft preview and refine the page content until you are happy and ready to publish it.
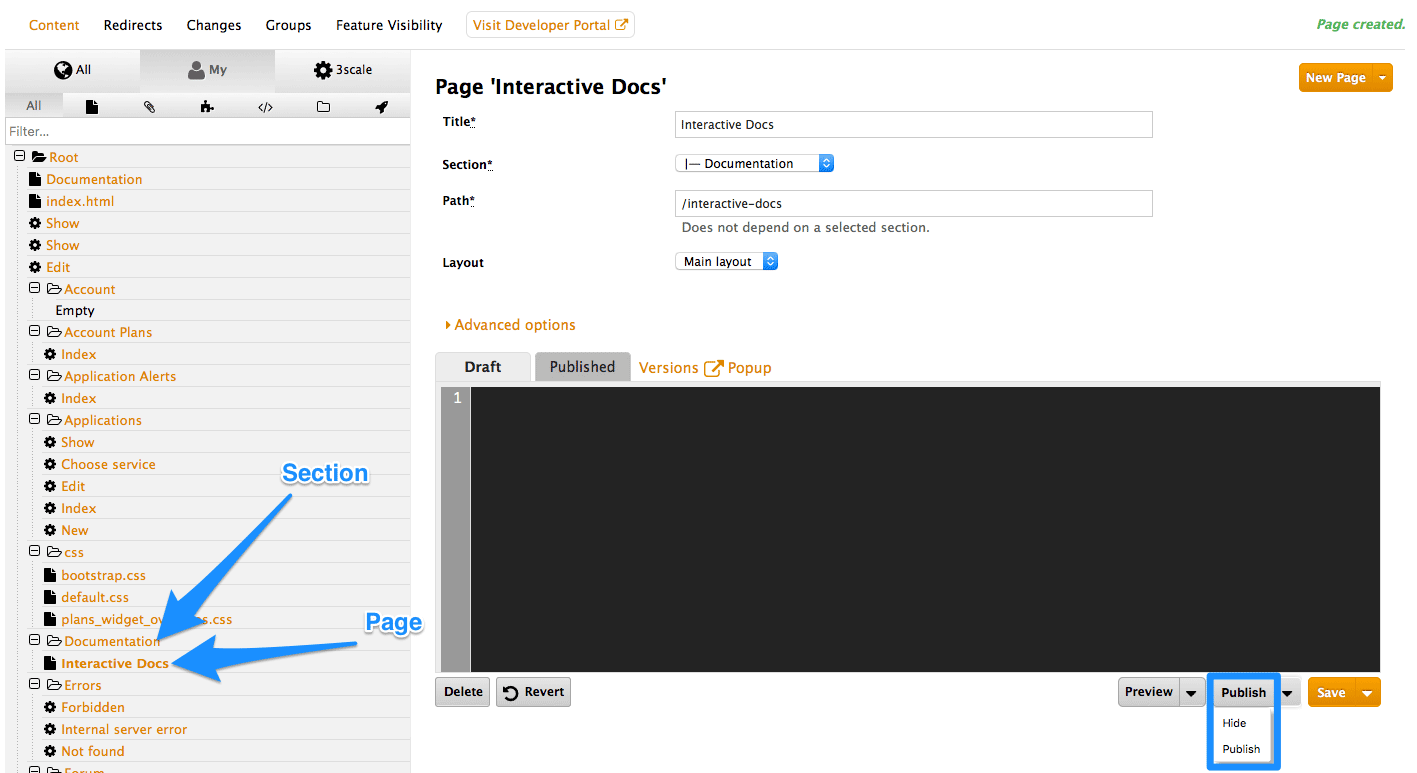
- Repeat for all pages in the section.
- Then repeat for all sections in the site.
15.2.5. Editing your page headers
All repetitive page elements such as headers and footers are defined in the portal Developer Portal section called “partials”. If you have only one layout, or very few of them, you can omit this step and include the header and footer inside the layouts code. However, remember to customize these elements in the layout. For example, the default “menu” partial should be edited to reflect your site map.

15.2.6. Adding images and other assets
For images or other files, first load the files into the content library, then insert a link into your text content.
- Select New File in order to choose your file, and identify where you will save it on your site.
- Copy the URL to the image
- Now you can add your HTML or <a> tag, and paste in the URL for your image.
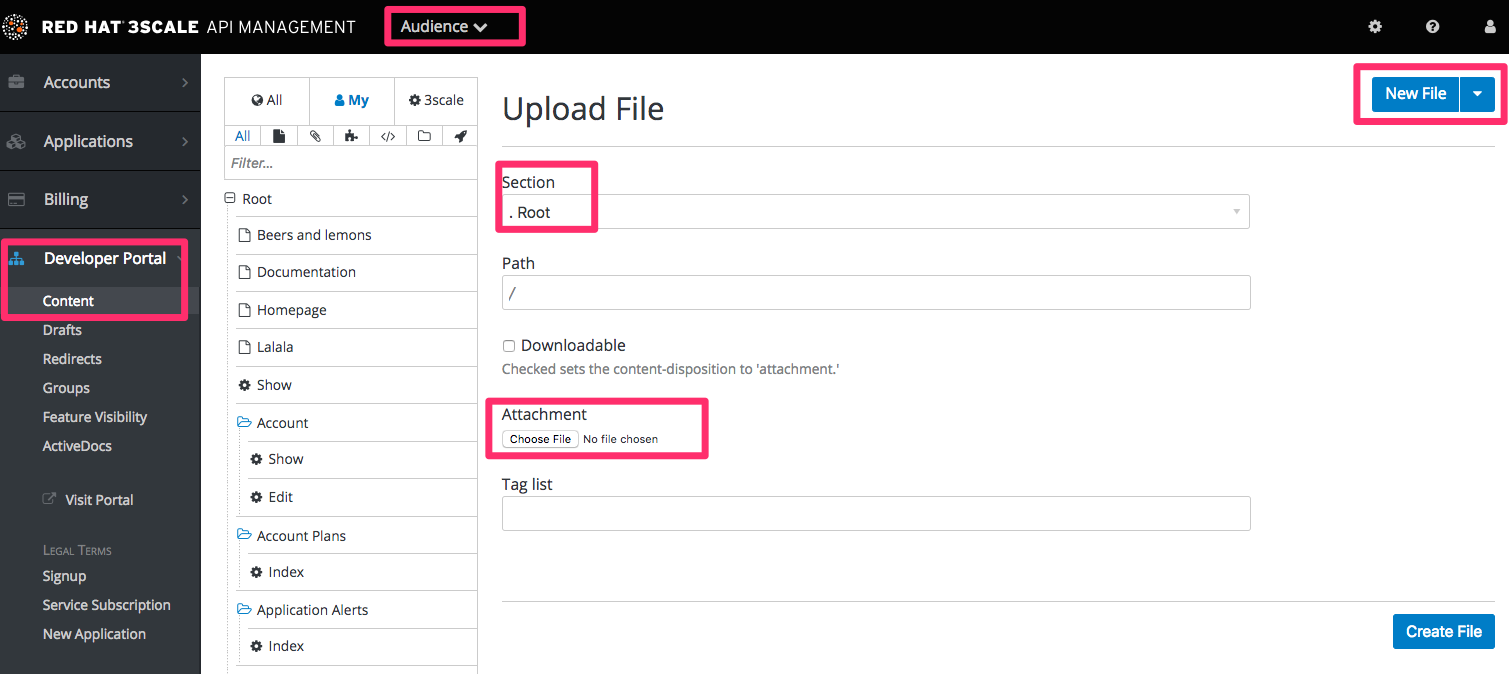
15.2.7. Customizing with your branding
There is a default stylesheet called default.css, which is quite large and complex. Rather than extend this, it is better to create your own stylesheet with your own customizations to overwrite the defaults.
You can create a new stylesheet the same way you create a page – just remember to choose an appropriate MIME content type in the advanced page settings. Then add the link to your custom CSS in your layout templates after the link to default.css, for example:
<link rel="stylesheet" href="/stylesheets/custom.css" />
15.2.8. Going live
The final task is to view the entire portal site and check all the workflows. You can publish each page or all of the pages in the Changes section. Once you’re happy with everything, make a final check that all pages have been published.
Now you’re ready to remove any access code for the portal:
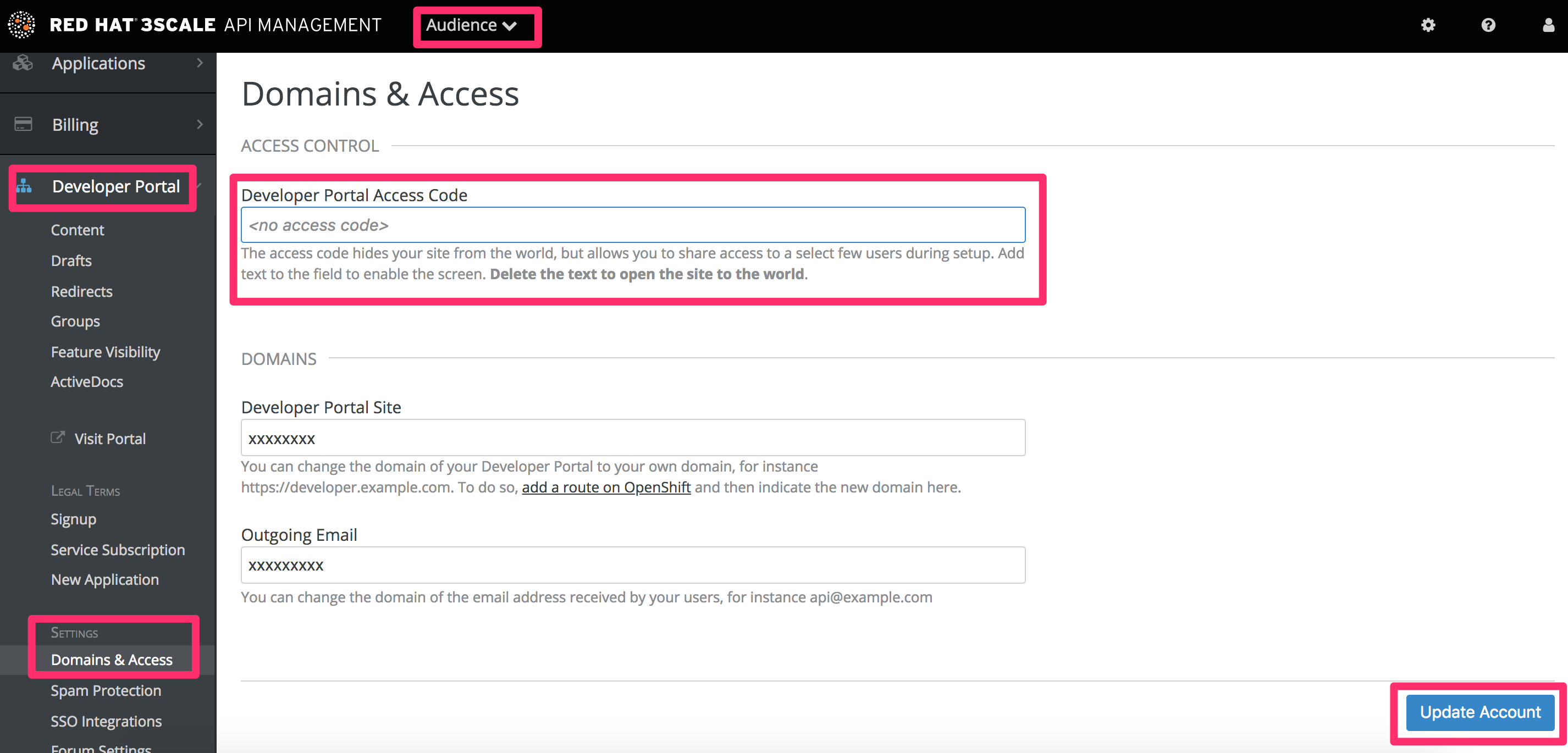
Congratulations! Your Developer Portal is now live and ready to help build your developer community.
15.3. Additional configuration options for your Developer Portal
There are additional areas interacting with your Developer Portal that you can configure:
- Set up your application plans: With these plans, you have the access rights configured for the API keys that you will issue.
- Configure your developer signup flows: These flows can be anywhere on the range from self-service, to approval required, or invite only with signups disabled.

