-
Language:
English
-
Language:
English
Red Hat Training
A Red Hat training course is available for JBoss Enterprise Application Platform Common Criteria Certification
Chapter 4. The JBoss Security Extension Architecture
The preceding discussion of the general JBoss security layer has stated that the JBoss Security Extension framework (JBossSX) is an implementation of the security layer interfaces. This is the primary purpose of the JBossSX framework. The framework offers a great deal of customization possibilities for integration into existing security infrastructures. A security infrastructure can be anything from a database or LDAP server to a sophisticated security software suite. The integration flexibility is achieved using the Pluggable Authentication Model (PAM) available in the JAAS framework.
The heart of the JBossSX framework is
org.jboss.security.plugins.JaasSecurityManager. This is the default implementation of the AuthenticationManager and RealmMapping interfaces. Figure 4.1, “Relationship between <security-domain> deployment descriptor value, component container, and JaasSecurityManager.” shows how the JaasSecurityManager integrates into the EJB and web container layers based on the <security-domain> element of the corresponding component deployment descriptor.
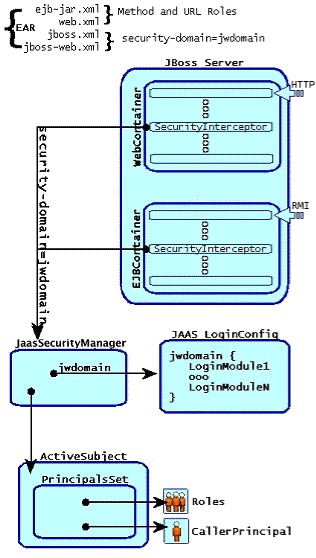
Figure 4.1. Relationship between <security-domain> deployment descriptor value, component container, and JaasSecurityManager.
Figure 4.1, “Relationship between <security-domain> deployment descriptor value, component container, and JaasSecurityManager.” depicts an enterprise application that contains both EJBs and web content secured under the security domain
jwdomain. The EJB and web containers have a request interceptor architecture that includes a security interceptor, which enforces the container security model. At deployment time, the <security-domain> element value in the jboss.xml and jboss-web.xml descriptors is used to obtain the security manager instance associated with the container. The security interceptor then uses the security manager to perform its role. When a secured component is requested, the security interceptor delegates security checks to the security manager instance associated with the container.
The JBossSX
JaasSecurityManager implementation performs security checks based on the information associated with the Subject instance that results from executing the JAAS login modules configured under the name matching the <security-domain> element value. We will drill into the JaasSecurityManager implementation and its use of JAAS in the following section.
4.1. How the JaasSecurityManager Uses JAAS
The
JaasSecurityManager uses the JAAS packages to implement the AuthenticationManager and RealmMapping interface behavior. In particular, its behavior derives from the execution of the login module instances that are configured under the name that matches the security domain to which the JaasSecurityManager has been assigned. The login modules implement the security domain's principal authentication and role-mapping behavior. Thus, you can use the JaasSecurityManager across different security domains simply by plugging in different login module configurations for the domains.
To illustrate the details of the
JaasSecurityManager's usage of the JAAS authentication process, you will walk through a client invocation of an EJB home method invocation. The prerequisite setting is that the EJB has been deployed in the JBoss server and its home interface methods have been secured using <method-permission> elements in the ejb-jar.xml descriptor, and it has been assigned a security domain named jwdomain using the jboss.xml descriptor <security-domain> element.

Figure 4.2. Secured EJB Home Method Authentication and Authorization Invocation Steps.
Figure 4.2, “Secured EJB Home Method Authentication and Authorization Invocation Steps.” provides a view of the client to server communication. The numbered steps shown are:
- The client must perform a JAAS login to establish the principal and credentials for authentication, and this is labeled Client Side Login in the figure. This is how clients establish their login identities in JBoss. Support for presenting the login information via JNDI
InitialContextproperties is provided via an alternate configuration.A JAAS login entails creating aLoginContextinstance and passing in the name of the configuration to use. The configuration name isother. This one-time login associates the login principal and credentials with all subsequent EJB method invocations. Note that the process might not authenticate the user. The nature of the client-side login depends on the login module configuration that the client uses. In this example, theotherclient-side login configuration entry is set up to use theClientLoginModulemodule (anorg.jboss.security.ClientLoginModule). This is the default client side module that simply binds the user name and password to the JBoss EJB invocation layer for later authentication on the server. The identity of the client is not authenticated on the client. - The client obtains the EJB home interface and attempts to create a bean. This event is labeled as Home Method Invocation. This results in a home interface method invocation being sent to the JBoss server. The invocation includes the method arguments passed by the client, along with the user identity and credentials from the client-side JAAS login performed in Step 1.
- On the server side, the security interceptor first requires authentication of the user invoking the call, which, as on the client side, involves a JAAS login.
- The security domain under which the EJB is secured determines the choice of login modules. The security domain name is used as the login configuration entry name passed to the
LoginContextconstructor. The EJB security domain isjwdomain. If the JAAS login authenticates the user, a JAASSubjectis created that contains the following in itsPrincipalsSet:- A
java.security.Principalthat corresponds to the client identity as known in the deployment security environment. - A
java.security.acl.GroupnamedRolesthat contains the role names from the application domain to which the user has been assigned.org.jboss.security.SimplePrincipalobjects are used to represent the role names;SimplePrincipalis a simple string-based implementation ofPrincipal. These roles are used to validate the roles assigned to methods inejb-jar.xmland theEJBContext.isCallerInRole(String)method implementation. - An optional
java.security.acl.GroupnamedCallerPrincipal, which contains a singleorg.jboss.security.SimplePrincipalthat corresponds to the identity of the application domain's caller. TheCallerPrincipalsole group member will be the value returned by theEJBContext.getCallerPrincipal()method. The purpose of this mapping is to allow aPrincipalas known in the operational security environment to map to aPrincipalwith a name known to the application. In the absence of aCallerPrincipalmapping the deployment security environment principal is used as thegetCallerPrincipalmethod value. That is, the operational principal is the same as the application domain principal.
- The final step of the security interceptor check is to verify that the authenticated user has permission to invoke the requested method. This is labeled as Server Side Authorization in Figure 4.2, “Secured EJB Home Method Authentication and Authorization Invocation Steps.”. Performing the authorization this entails the following steps:
- Obtain the names of the roles allowed to access the EJB method from the EJB container. The role names are determined by
ejb-jar.xmldescriptor <role-name> elements of all <method-permission> elements containing the invoked method. - If no roles have been assigned, or the method is specified in an exclude-list element, then access to the method is denied. Otherwise, the
doesUserHaveRolemethod is invoked on the security manager by the security interceptor to see if the caller has one of the assigned role names. This method iterates through the role names and checks if the authenticated user's SubjectRolesgroup contains aSimplePrincipalwith the assigned role name. Access is allowed if any role name is a member of theRolesgroup. Access is denied if none of the role names are members. - If the EJB was configured with a custom security proxy, the method invocation is delegated to it. If the security proxy wants to deny access to the caller, it will throw a
java.lang.SecurityException. If noSecurityExceptionis thrown, access to the EJB method is allowed and the method invocation passes to the next container interceptor. Note that theSecurityProxyInterceptorhandles this check and this interceptor is not shown. - For JBoss Web connections, Tomcat manages elements of security constraint, and role verification.When a request is received for a web connection, Tomcat checks the security constraints defined in
web.xmlthat match the requested resource and the accessed HTTP method.If a constraint exists for the request, Tomcat calls the JaasSecurityManager to perform the principal authentication, which in turn ensures the user roles are associated with that principal object.Role verification is performed solely by Tomcat, including checks on parameters such asallRoles, and whetherSTRICT_MODEis used.
Every secured EJB method invocation, or secured web content access, requires the authentication and authorization of the caller because security information is handled as a stateless attribute of the request that must be presented and validated on each request. This can be an expensive operation if the JAAS login involves client-to-server communication. Because of this, the
JaasSecurityManager supports the notion of an authentication cache that is used to store principal and credential information from previous successful logins. You can specify the authentication cache instance to use as part of the JaasSecurityManager configuration as you will see when the associated MBean service is discussed in following section. In the absence of any user-defined cache, a default cache that maintains credential information for a configurable period of time is used.

