Red Hat Training
A Red Hat training course is available for Red Hat Enterprise Linux
30.6. Modifying sudo Rules
Modifying sudo Rules in the Web UI
- Under the Policy tab, click Sudo → Sudo Rules.
- Click the name of the rule to display its configuration page.
- Change the settings as required. On some configuration pages, the Save button is available at the top of the page. On these pages, click the button to confirm the changes.
The
sudo rule configuration page includes several configuration areas:
- The General area
- In this area, you can modify the rule's description and
sudo order. Thesudo orderfield accepts integers and defines the order in which IdM evaluates the rules. The rule with the highestsudo ordervalue is evaluated first. - The Options area
- In this area, you can add
sudoersoptions to the rule.- Click Add above the options list.
Figure 30.5. Adding a
sudoOption
- Enter the
sudoersoption. For example, to specify thatsudowill not prompt the user to authenticate, add the!authenticateoption:Figure 30.6. Entering a
sudoersOption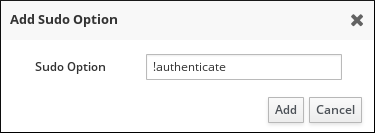 For more information on
For more information onsudoersoptions, see the sudoers(5) man page. - Click Add.
- The Who area
- In this area, you can select the users or user groups to which the
sudorule will be applied. These users will be entitled to usesudoas defined in the rule.To specify that all system users will be able to usesudoas defined in the rule, select Anyone.To apply the rule to specific users or groups only, select Specified Users and Groups and then follow these steps:- Click Add above the users or user groups list.
Figure 30.7. Adding Users to a
sudoRule
- Select the users or user groups to add to the rule, and click the > arrow button to move them to the Prospective column. To add an external user, specify the user in the External field, and then click the > arrow button.
Figure 30.8. Selecting Users for a
sudoRule
- Click Add.
- The Access This Host area
- In this area, you can select the hosts on which the
sudorule will be in effect. These are the hosts where the users will be grantedsudopermissions.To specify that the rule will be in effect on all hosts, select Anyone.To apply the rule to specific hosts or host groups only, select Specified Hosts and Groups and then follow these steps:- Click Add above the hosts list.
Figure 30.9. Adding Hosts to a
sudoRule
- Select the hosts or host groups to include with the rule, and click the > arrow button to move them to the Prospective column. To add an external host, specify the host in the External field, and then click the > arrow button.
Figure 30.10. Selecting Hosts for a
sudoRule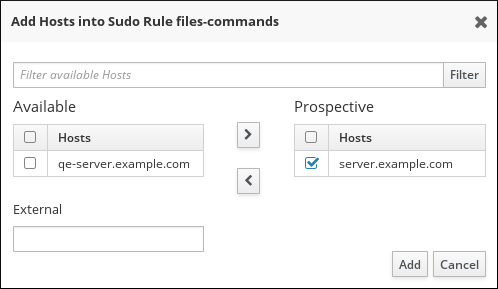
- Click Add.
- The Run Commands area
- In this area, you can select the commands to be included in the
sudorule. You can specify that users will be either allowed or denied to use specific commands.To specify that users will be allowed to use any command withsudo, select Any Command.To associate the rule with specific commands or command groups, select Specified Commands and Groups and then follow these steps:- Click one of the Add buttons to add a command or a command group.To specify allowed commands or command groups, use the Allow area. To specify denied commands or command groups, use the Deny area.
Figure 30.11. Adding Commands to a
sudoRule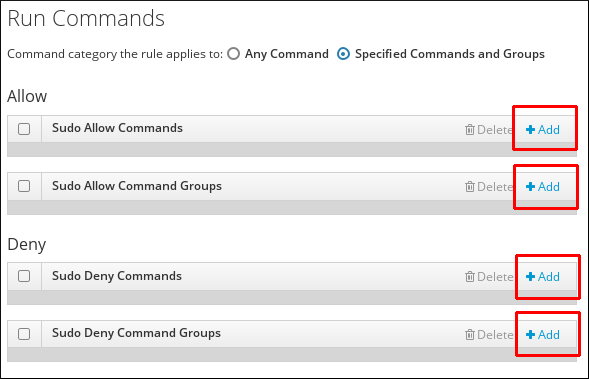
- Select the commands or command groups to include with the rule, and click the > arrow button to move them to the Prospective column.
Figure 30.12. Selecting Commands for a
sudoRule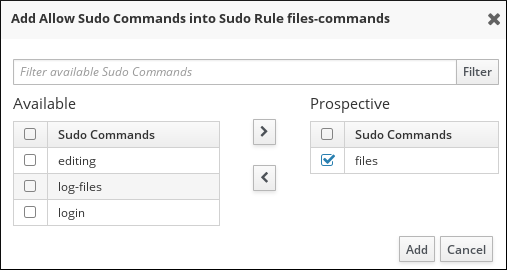
- Click Add.
- The As Whom area
- In this area, you can configure the
sudorule to run the given commands as a specific, non-root user.Note that if you add a group of RunAs users, UIDs of the members of the group will be used to run the command. If you add a RunAs group, the GID of the group will be used to run the command.To specify that the rule will be run as any user on the system, select Anyone. To specify that the rule will be run as any group on the system, select Any Group.- Click Add above the users list.
Figure 30.13. Configuring
sudoRules to Execute Commands as a Specific User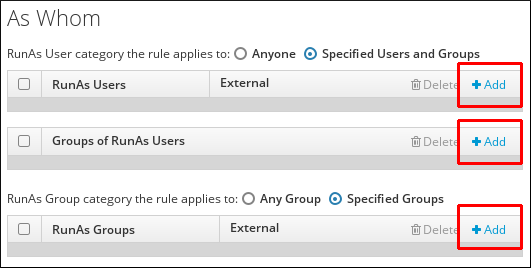
- Select the required users or groups, and use the > arrow button to move them to the Prospective column. To add an external entity, specify it in the External field, and then click the > arrow button.
Figure 30.14. Selecting Users for the Command
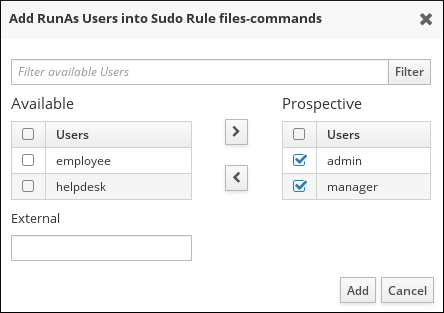
- Click Add.
Modifying sudo Rules from the Command Line
The IdM command-line utilities allow you to configure several
sudo rule areas:
- General
sudorules management - To change the general configuration for a
sudorule, use the ipa sudorule-mod command. The most common options accepted by the command are:- The
--descoption to change thesudorule description. For example:$ ipa sudorule-mod sudo_rule_name --desc="sudo_rule_description"
- The
--orderoption to define the order of the specified rule. For example:$ ipa sudorule-mod sudo_rule_name --order=3
- Options to specify a category of entities:
--usercat(user category),--hostcat(host category),--cmdcat(command category),--runasusercat(run-as user category), and--runasgroupcat(run-as group category). These options only accept theallvalue that associates the rule with all users, hosts, commands, run-as users, or run-as groups.For example, to specify that all users will be able to usesudoas defined in thesudo_rulerule:$ ipa sudorule-mod sudo_rule --usercat=all
Note that if the rule is already associated with a specific entity, you must remove it before defining the correspondingallcategory. For example, ifsudo_rulewas previously associated with a specific user using the ipa sudorule-add-user command, you must first use the ipa sudorule-remove-user command to remove the user.
For more details and a complete list of options accepted by ipa sudorule-mod, run the command with the--helpoption added. - Managing
sudooptions - To add a
sudoersoption, use the ipa sudorule-add-option command.For example, to specify that users usingsudobased on thefiles-commandsrule will not be required to authenticate, add the!authenticateoption:$ ipa sudorule-add-option files-commands Sudo Option: !authenticate --------------------------------------------------------- Added option "!authenticate" to Sudo Rule "files-commands" ---------------------------------------------------------
For more information onsudoersoptions, see the sudoers(5) man page.To remove asudoersoption, use the ipa sudorule-remove-option command. For example:$ ipa sudorule-remove-option files-commands Sudo Option: authenticate ------------------------------------------------------------- Removed option "authenticate" from Sudo Rule "files-commands" -------------------------------------------------------------
- Managing who is granted the permission to use
sudo - To specify an individual user, add the
--usersoption to the ipa sudorule-add-user command. To specify a user group, add the--groupsoption to ipa sudorule-add-user.For example, to adduseranduser_groupto thefiles-commandsrule:$ ipa sudorule-add-user files-commands --users=user --groups=user_group ... ------------------------- Number of members added 2 -------------------------
To remove an individual user or group, use the ipa sudorule-remove-user. For example, to remove a user:$ ipa sudorule-remove-user files-commands [member user]: user [member group]: ... --------------------------- Number of members removed 1 ---------------------------
- Managing where the users are granted the
sudopermissions - To specify a host, add the
--hostsoption to the ipa sudorule-add-host command. To specify a host group, add the--hostgroupsoption to ipa sudorule-add-host.For example, to addexample.comandhost_groupto thefiles-commandsrule:$ ipa sudorule-add-host files-commands --hosts=example.com --hostgroups=host_group ... ------------------------- Number of members added 2 -------------------------
To remove a host or host group, use the ipa sudorule-remove-host command. For example:$ ipa sudorule-remove-host files-commands [member host]: example.com [member host group]: ... --------------------------- Number of members removed 1 ---------------------------
- Managing what commands can be used with
sudo - You can specify that users will be either allowed or denied to use specific commands.To specify an allowed command or command group, add the
--sudocmdsor--sudocmdgroupsoption to the ipa sudorule-add-allow-command. To specify a denied command or command group, add the--sudocmdsor--sudocmdgroupsoption to the ipa sudorule-add-deny-command command.For example, to add the/usr/bin/lesscommand and thefilescommand group as allowed to thefiles-commandsrule:$ ipa sudorule-add-allow-command files-commands --sudocmds=/usr/bin/less --sudocmdgroups=files ... ------------------------- Number of members added 2 -------------------------
To remove a command or command group from a rule, use the ipa sudorule-remove-allow-command or ipa sudorule-remove-deny-command commands. For example:$ ipa sudorule-remove-allow-command files-commands [member sudo command]: /usr/bin/less [member sudo command group]: ... --------------------------- Number of members removed 1 ---------------------------
Note that the--sudocmdsoption only accepts commands added to IdM, as described in Section 30.4.1, “AddingsudoCommands”. - Managing as whom the
sudocommands are run - To use the UIDs of an individual user or users in a group as the identity under which the commands are run, use the
--usersor--groupsoptions with the ipa sudorule-add-runasuser command.To use the GID of a user group as the identity for the commands, use the ipa sudorule-add-runasgroup --groups command.If you specify no user or group,sudocommands will be run as root.For example, to specify that the identity ofuserwill be used to execute the commands in thesudorule:$ ipa sudorule-add-runasuser files-commands --users=user ... RunAs Users: user ...
For more information on the ipa sudorule-* commands, see the output of the ipa help sudorule command or run a particular command with the
--help option added.
Example 30.1. Adding and Modifying a New sudo Rule from the Command Line
To allow a specific user group to use
sudo with any command on selected servers:
- Obtain a Kerberos ticket for the
adminuser or any other user allowed to managesudorules.$ kinit admin Password for admin@EXAMPLE.COM:
- Add a new
sudorule to IdM.$ ipa sudorule-add new_sudo_rule --desc="Rule for user_group" --------------------------------- Added Sudo Rule "new_sudo_rule" --------------------------------- Rule name: new_sudo_rule Description: Rule for user_group Enabled: TRUE
- Define the who: specify the group of users who will be entitled to use the
sudorule.$ ipa sudorule-add-user new_sudo_rule --groups=user_group Rule name: new_sudo_rule Description: Rule for user_group Enabled: TRUE User Groups: user_group ------------------------- Number of members added 1 -------------------------
- Define the where: specify the group of hosts where the users will be granted the
sudopermissions.$ ipa sudorule-add-host new_sudo_rule --hostgroups=host_group Rule name: new_sudo_rule Description: Rule for user_group Enabled: TRUE User Groups: user_group Host Groups: host_group ------------------------- Number of members added 1 -------------------------
- Define the what: to allow the users to run any
sudocommand, add theallcommand category to the rule.$ ipa sudorule-mod new_sudo_rule --cmdcat=all ------------------------------ Modified Sudo Rule "new_sudo_rule" ------------------------------ Rule name: new_sudo_rule Description: Rule for user_group Enabled: TRUE Command category: all User Groups: user_group Host Groups: host_group
- To let the
sudocommands be executed as root, do not specify any run-as users or groups. - Add the
!authenticatesudoersoption to specify that the users will not be required to authenticate when using thesudocommand.$ ipa sudorule-add-option new_sudo_rule Sudo Option: !authenticate ----------------------------------------------------- Added option "!authenticate" to Sudo Rule "new_sudo_rule" ----------------------------------------------------- Rule name: new_sudo_rule Description: Rule for user_group Enabled: TRUE Command category: all User Groups: user_group Host Groups: host_group Sudo Option: !authenticate
- Display the new
sudorule configuration to verify it is correct.$ ipa sudorule-show new_sudo_rule Rule name: new_sudo_rule Description: Rule for user_group Enabled: TRUE Command category: all User Groups: user_group Host Groups: host_group Sudo Option: !authenticate

