Red Hat Training
A Red Hat training course is available for Red Hat Enterprise Linux
24.4. Certificate Profiles
A certificate profile defines the content of certificates belonging to the particular profile, as well as constraints for issuing the certificates, enrollment method, and input and output forms for enrollment. A single certificate profile is associated with issuing a particular type of certificate. Different certificate profiles can be defined for users, services, and hosts in IdM.
The CA uses certificate profiles in signing of certificates to determine:
- whether the CA can accept a certificate signing request (CSR)
- what features and extensions should be present on the certificate
IdM includes the following two certificate profiles by default:
caIPAserviceCert and IECUserRoles. In addition, custom profiles can be imported.
Custom certificate profiles allow issuing certificates for specific, unrelated purposes. For example, it is possible to restrict use of a particular profile to only one user or one group, preventing other users and groups from using that profile to issue a certificate for authentication.
For details on supported certificate profile configuration, see Defaults Reference and Constraints Reference in the Red Hat Certificate System Administration Guide.
Note
By combining certificate profiles and CA ACLs, Section 24.5, “Certificate Authority ACL Rules”, the administrator can define and control access to custom certificate profiles. For a description of using profiles and CA ACLs to issue user certificates, see Section 24.6, “Using Certificate Profiles and ACLs to Issue User Certificates with the IdM CAs”.
24.4.1. Creating a Certificate Profile
For details about creating a certificate profile, see the following documentation in the Red Hat Certificate System 9 Administration Guide:
- The Setting up Certificate Profiles section explains how to create new certificate profiles and how they are constructed.
- The Defaults, Constraints, and Extensions for Certificates and CRLs appendix lists the object identifiers (OID) other fields you can use in a certificate profile.
24.4.2. Certificate Profile Management from the Command Line
The
certprofile plug-in for management of IdM profiles allows privileged users to import, modify, or remove IdM certificate profiles. To display all commands supported by the plug-in, run the ipa certprofile command:
$ ipa certprofile
Manage Certificate Profiles
...
EXAMPLES:
Import a profile that will not store issued certificates:
ipa certprofile-import ShortLivedUserCert \
--file UserCert.profile --desc "User Certificates" \
--store=false
Delete a certificate profile:
ipa certprofile-del ShortLivedUserCert
...
Note that to perform the
certprofile operations, you must be operating as a user who has the required permissions. IdM includes the following certificate profile-related permissions by default:
- System: Read Certificate Profiles
- Enables users to read all profile attributes.
- System: Import Certificate Profile
- Enables users to import a certificate profile into IdM.
- System: Delete Certificate Profile
- Enables users to delete an existing certificate profile.
- System: Modify Certificate Profile
- Enables users to modify the profile attributes and to disable or enable the profile.
All these permissions are included in the default
CA Administrator privilege. For more information on IdM role-based access controls and managing permissions, see Section 10.4, “Defining Role-Based Access Controls”.
Note
When requesting a certificate, the
--profile-id option can be added to the ipa cert-request command to specify which profile to use. If no profile ID is specified, the default caIPAserviceCert profile is used for the certificate.
This section only describes the most important aspects of using the ipa certprofile commands for profile management. For complete information about a command, run it with the
--help option added, for example:
$ ipa certprofile-mod --help Usage: ipa [global-options] certprofile-mod ID [options] Modify Certificate Profile configuration. Options: -h, --help show this help message and exit --desc=STR Brief description of this profile --store=BOOL Whether to store certs issued using this profile ...
Importing Certificate Profiles
To import a new certificate profile to IdM, use the ipa certprofile-import command. Running the command without any options starts an interactive session in which the
certprofile-import script prompts your for the information required to import the certificate.
$ ipa certprofile-import Profile ID: smime Profile description: S/MIME certificates Store issued certificates [True]: TRUE Filename of a raw profile. The XML format is not supported.: smime.cfg ------------------------ Imported profile "smime" ------------------------ Profile ID: smime Profile description: S/MIME certificates Store issued certificates: TRUE
The ipa certprofile-import command accepts several command-line options. Most notably:
--file- This option passes the file containing the profile configuration directly to ipa certprofile-import. For example:
$ ipa certprofile-import --file=smime.cfg
--store- This option sets the
Store issued certificatesattribute. It accepts two values:True, which delivers the issued certificates to the client and stores them in the target IdM principal'suserCertificateattribute.False, which delivers the issued certificates to the client, but does not store them in IdM. This option is most commonly-used when issuing multiple short-term certificates is required.
Import fails if the profile ID specified with ipa certprofile-import is already in use or if the profile content is incorrect. For example, the import fails if a required attribute is missing or if the profile ID value defined in the supplied file does not match the profile ID specified with ipa certprofile-import.
To obtain a template for a new profile, you can run the ipa certprofile-show command with the
--out option, which exports a specified existing profile to a file. For example:
$ ipa certprofile-show caIPAserviceCert --out=file_name
You can then edit the exported file as required and import it as a new profile.
Displaying Certificate Profiles
To display all certificate profiles currently stored in IdM, use the ipa certprofile-find command:
$ ipa certprofile-find ------------------ 3 profiles matched ------------------ Profile ID: caIPAserviceCert Profile description: Standard profile for network services Store issued certificates: TRUE Profile ID: IECUserRoles ...
To display information about a particular profile, use the ipa certprofile-show command:
$ ipa certprofile-show profile_ID Profile ID: profile_ID Profile description: S/MIME certificates Store issued certificates: TRUE
Modifying Certificate Profiles
To modify an existing certificate profile, use the ipa certprofile-mod command. Pass the required modifications with the command using the command-line options accepted by ipa certprofile-mod. For example, to modify the description of a profile and change whether IdM stores the issued certificates:
$ ipa certprofile-mod profile_ID --desc="New description" --store=False ------------------------------------ Modified Certificate Profile "profile_ID" ------------------------------------ Profile ID: profile_ID Profile description: New description Store issued certificates: FALSE
To update the certificate profile configuration, import the file containing the updated configuration using the
--file option. For example:
$ ipa certprofile-mod profile_ID --file=new_configuration.cfg
Deleting Certificate Profiles
To remove an existing certificate profile from IdM, use the ipa certprofile-del command:
$ ipa certprofile-del profile_ID ----------------------- Deleted profile "profile_ID" -----------------------
24.4.3. Certificate Profile Management from the Web UI
To manage certificate profiles from the IdM web UI:
- Open the Authentication tab and the Certificates subtab.
- Open the Certificate Profiles section.
Figure 24.7. Certificate Profile Management in the Web UI

In the Certificate Profiles section, you can display information about existing profiles, modify their attributes, or delete selected profiles.
For example, to modify an existing certificate profile:
- Click on the name of the profile to open the profile configuration page.
- In the profile configuration page, fill in the required information.
- Click Save to confirm the new configuration.
Figure 24.8. Modifying a Certificate Profile in the Web UI
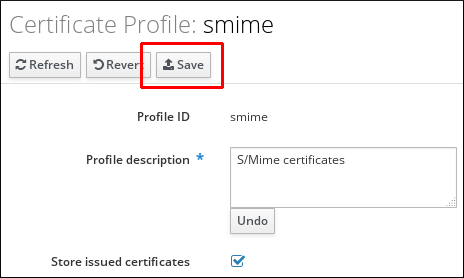
If you enable the
Store issued certificates option, the issued certificates are delivered to the client as well as stored in the target IdM principal's userCertificate attribute. If the option is disabled, the issued certificates are delivered to the client, but not stored in IdM. Storing certificates is often disabled when issuing multiple short-lived certificates is required.
Note that some certificate profile management operations are currently unavailable in the web UI:
- It is not possible to import a certificate profile in the web UI. To import a certificate, use the ipa certprofile-import command.
- It is not possible to set, add, or delete attribute and value pairs. To modify the attribute and value pairs, use the ipa certprofile-mod command.
- It is not possible to import updated certificate profile configuration. To import a file containing updated profile configuration, use the ipa certprofile-mod --file=file_name command.
For more information about the commands used to manage certificate profiles, see Section 24.4.2, “Certificate Profile Management from the Command Line”.
24.4.4. Upgrading IdM Servers with Certificate Profiles
When upgrading an IdM server, the profiles included in the server are all imported and enabled.
If you upgrade multiple server replicas, the profiles of the first upgraded replica are imported. On the other replicas, IdM detects the presence of other profiles and does not import them or resolve any conflicts between the two sets of profiles. If you have custom profiles defined on replicas, make sure the profiles on all replicas are consistent before upgrading.

