Red Hat Product Security Risk Report 2016
At Red Hat, our dedicated Product Security team analyzes threats and vulnerabilities against all our products and provides relevant advice and updates through the Red Hat Customer Portal. Customers can rely on this expertise to help them quickly address the issues that can cause high risks and avoid wasting time or effort on those that don’t.
Red Hat delivers certified, signed, supported versions of the open source solutions that enable cost-effective innovation for the enterprise. This is the Red Hat value chain.
This report explores the state of security risk for Red HatⓇ products for calendar year 2016. We look at key metrics, specific vulnerabilities, and the most common ways that security issues affected users of Red Hat products.
Among our findings:
-
Looking only at issues affecting base Red Hat Enterprise LinuxⓇ releases, we released 38 Critical security advisories addressing 50 Critical vulnerabilities. Of those issues, 100% had fixes the same or next day after the issue was public.
-
During that same timeframe, across the whole Red Hat portfolio, 76% of Critical issues had updates to address them the same or next day after the issue was public with 98% addressed within a week of the issue being public.
-
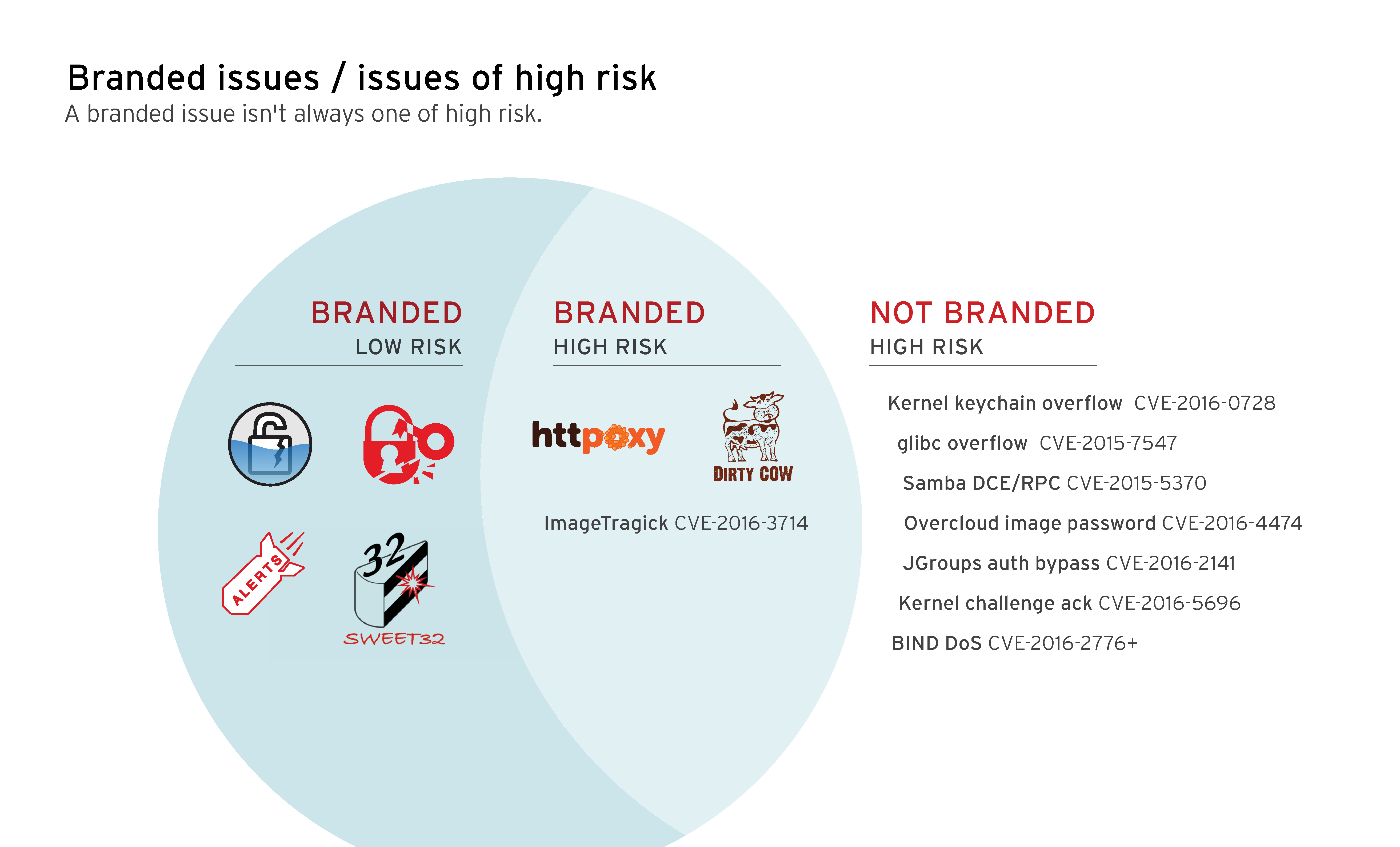
A catchy name or a flashy headline for a vulnerability doesn't tell much about its risk. The Red Hat Product Security Team helps customers determine a vulnerability’s actual impact. Most 2016 issues that mattered were not branded.
Vulnerabilities
Across all Red Hat products, and for all issue severities, we fixed more than 1,300 vulnerabilities1 by releasing more than 600 security advisories in 2016. Critical2 vulnerabilities pose the most risk to an organization. Most Critical vulnerabilities occur in browser or browser components, so Red Hat Enterprise Linux server installations will generally be affected by far fewer critical vulnerabilities. One way customers can reduce risk when using our modular products is to make sure they install the right variant and review the package set to remove packages they don’t need.
The Red Hat value chain
Red Hat products are based on open source software. Some Red Hat products contain several thousand individual packages, each of which is based on separate, third-party software from upstream projects.
Red Hat engineers play a part in many upstream components, but handling and managing vulnerabilities across thousands of third-party components is a significant task. Red Hat has a dedicated Product Security team that monitors issues affecting Red Hat products and works closely with upstream projects.
For more than 15 years, Red Hat Product Security has been a recognized leader in fixing security flaws across the Linux stack. In 2016, we investigated more than 2,600 vulnerabilities that potentially affected parts of our products, leading to fixes for 1,346 vulnerabilities. That’s a 30% increase over 2015, when the team investigated 2,000.
Vulnerabilities known to Red Hat in advance of being made public are known as “under embargo.” Unlike companies shipping proprietary software, Red Hat is not in sole control of the date each flaw is made public. This is a good thing, as it leads to much shorter times between when a flaw is first reported and when it becomes public. Shorter embargo periods make flaws much less valuable to attackers. They know a flaw in open source is likely to get fixed quickly, shortening their window of opportunity to exploit it.
For 2016, across all products, we knew about 394 (29%) of the vulnerabilities we addressed before making them public, down slightly from 32% in 2015. We expect this figure to vary from year to year. Across all products and vulnerabilities of all severities known to us in advance, the median embargo was seven days. This is much lower than 2015, when the median embargo was 13 days.
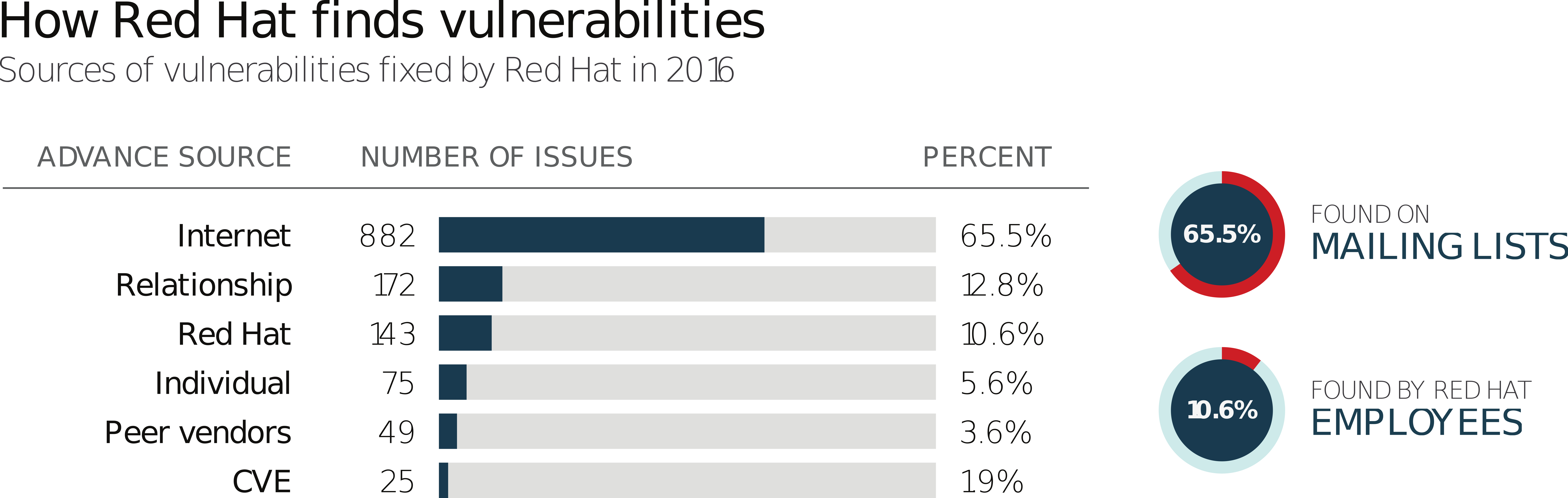
Figure 2: Red Hat Product Security monitors multiple sources to identify vulnerabilities. The value of your Red Hat subscription at work.
The full report is available for download.
-
Red Hat Product Security assigns a Common Vulnerabilities and Exposures (CVE) name to every security issue we fix. In this report, we equate vulnerabilities to CVEs. ↩︎
-
Red Hat rates vulnerabilities on a four-point scale that shows at a glance how much concern Red Hat has about each security issue. The scale rates vulnerabilities as Low, Moderate, Important, or Critical. By definition, a Critical vulnerability is one that could be exploited remotely and automatically by a worm. However we, like other vendors, also stretch the definition to include those flaws that affect web browsers or plug-ins where a user only needs to visit a malicious (or compromised) website to be exploited. ↩︎


Comments